



CVE-2024-4577 is a critical PHP CGI vulnerability that allows for argument injection leading to remote code execution. The vulnerability is particularly concerning due to the ease of exploitation and the widespread use of PHP in web applications. If left unpatched, it could enable attackers to gain unauthorized access and control over affected servers. Immediate action is required to patch affected systems and mitigate potential threats. Organizations must prioritize this issue to protect their web environments from malicious activities.
The CYFIRMA Research team conducted an in-depth analysis of CVE-2024-4577, analyzing this critical vulnerability affecting the Common Gateway Interface (CGI) component in PHP versions. This vulnerability allows for argument injection, which can lead to remote code execution (RCE). Given PHP’s widespread use in web development, particularly for server-side scripting, this vulnerability has far-reaching implications. The vulnerability primarily affects environments where PHP is configured to run in CGI mode, often found in shared hosting scenarios. Organizations utilizing PHP in their technology stacks must be aware of this vulnerability and take immediate action to secure their systems.
Key Takeaways:
Acknowledgements:
CYFIRMA Research acknowledges the collaborative efforts of security researchers and the cybersecurity community in identifying and addressing the CVE-2024-4577 vulnerability.
Vulnerability Type: Unauthenticated Remote Code Execution (RCE)
CVE ID: CVE-2024-4577
CVSS Severity Score: 9.8 (Critical)
Application: PHP (configured in CGI mode)
Impact: Allows unauthenticated attackers to execute arbitrary code, posing a significant risk of remote code execution.
Severity: Critical
Affected Versions: Check here
Patch Available: Yes
Mitigation: Organizations are strongly advised to upgrade to PHP version 8.3 or later, and to apply the latest security updates and patches promptly to mitigate the risk of exploitation. Additionally, ensure PHP is not unnecessarily configured to run in CGI mode.
CVE-2024-4577 is a critical security flaw in PHP, specifically targeting its CGI component. This vulnerability arises when PHP is configured to run in CGI mode, allowing attackers to inject malicious arguments. By crafting special HTTP requests, an attacker can exploit this flaw to execute arbitrary code on the server. This type of vulnerability is particularly dangerous because it can be exploited remotely without authentication, making it a prime target for attackers.
The impact of CVE-2024-4577 is substantial, given its ability to allow remote code execution on vulnerable servers. Exploitation can lead to:
CVE-2024-4577 affects PHP versions prior to 8.3. Any environment running these versions with PHP configured in CGI mode is vulnerable to this critical security flaw. Check here.
Is there already an exploit tool to attack this vulnerability?
As of the latest available information, there are some known public exploit tools specifically targeting CVE-2024-4577 affecting PHP installations configured in CGI mode.
Has this vulnerability already been used in an attack?
Regarding exploitation, while CVE-2024-4577 poses a critical risk, there is no specific information confirming active exploitation of this vulnerability at present. However, due to its critical nature and ease of exploitation, it is being closely monitored.
Are hackers discussing this vulnerability in the Deep/Dark Web?
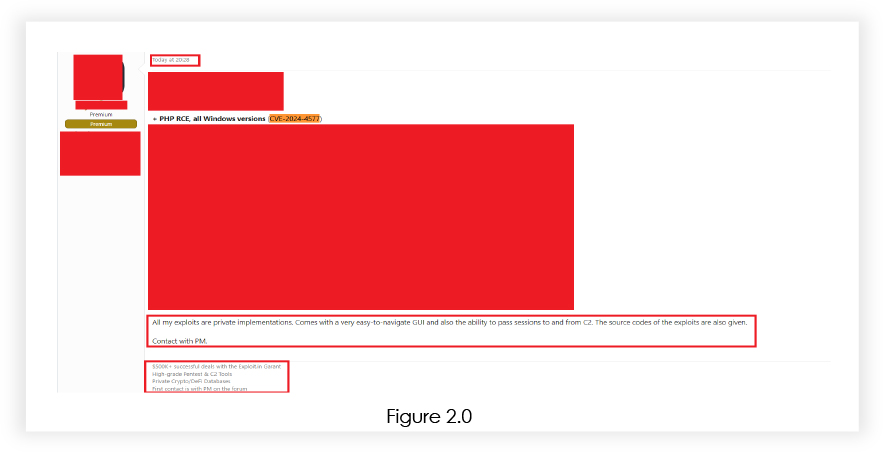
Discussions related to the potential exploitation and sale of exploit for CVE-2024-4577 have been observed in the Deep/Dark Web, indicating the potential for malicious actors to exploit the vulnerability. Cybersecurity teams should be vigilant and monitor these channels for any emerging threats.
What is the attack complexity level?
The attack complexity level for CVE-2024-4577 in PHP CGI is assessed as LOW. This means that exploiting this vulnerability does not require advanced technical skills, increasing the risk of widespread exploitation.
Historical Trends and Known Exploits
There is a known public exploit tool specifically targeting CVE-2024-4577, affecting PHP installations. However, discussions related to potential exploitation concept demonstrations have been observed in the Deep/Dark Web, indicating the potential for malicious actors to exploit the vulnerability. Organizations should remain vigilant and ensure that appropriate mitigation measures are in place.
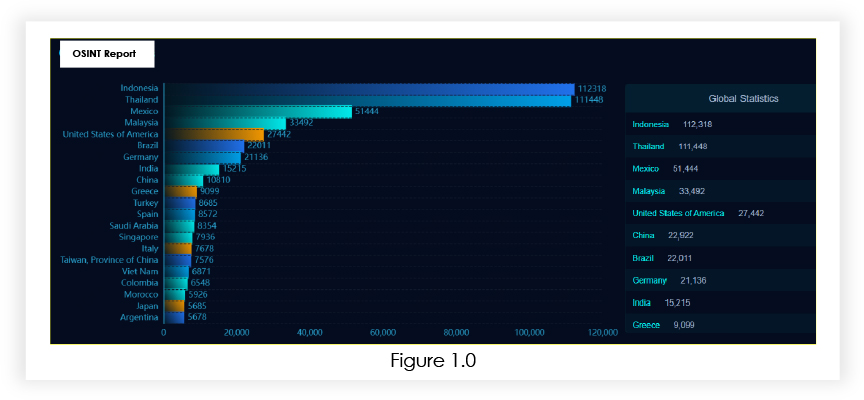
Our analysis found that more than 5,92,498+ PHP in CGI mode are public, which can be vulnerable to CVE-2024-4577.
PHP installations configured to run in CGI mode may be vulnerable due to a specific aspect of PHP’s Unicode handling. In certain locale settings, such as Chinese or Japanese, PHP’s Unicode best-fit conversion can unexpectedly interpret a soft hyphen (0xAD) as a dash (0x2D). This issue allows attackers to manipulate CGI arguments intended for PHP scripts, injecting malicious commands into the execution flow. This circumvents normal security measures and facilitates unauthorized remote code execution on the server.
Attackers begin by identifying potential targets through scanning methods. They seek out PHP installations configured in CGI mode and running versions of PHP that are susceptible to the Unicode conversion issue. This reconnaissance involves automated tools or manual inspection to pinpoint vulnerable endpoints across networks or the internet. For example, attackers might use scripts that send test requests to PHP CGI endpoints, appending -d allow_url_include=1 to URLs to check for vulnerability. Successful responses indicate exploitable instances, enabling attackers to proceed with crafted payloads for malicious execution.
Once a vulnerable PHP instance is identified, attackers craft exploit payloads designed to leverage the CGI argument injection vulnerability. These payloads are meticulously constructed to evade detection, often using techniques like base64 encoding to obscure malicious commands. For example, the payload might include encoded commands such as base64_encode(“echo ‘[S]’; system(‘$cmd’); echo ‘[E]’;”), which are decoded and executed by the PHP server. These instructions enable attackers to execute system-level operations or gain unauthorized access to sensitive data stored on the server. The payload’s sophistication allows it to bypass security measures and exploit the Unicode conversion flaw, thereby granting attackers the capability to compromise the server’s integrity and perform malicious actions remotely.
With the payload prepared, attackers initiate exploitation by sending HTTP requests to the vulnerable PHP endpoint. These requests contain manipulated CGI arguments designed to exploit the vulnerability. For example, they might include arguments like -d allow_url_include=1 or -d auto_prepend_file=php://input, which are part of the PHP configuration that can be abused to execute arbitrary code. The PHP server, interpreting these arguments as legitimate due to the Unicode conversion issue, unwittingly executes the injected payload. This grants attackers remote access and control over the server, enabling them to carry out actions such as data theft, installation of malware, or further compromise of the system’s integrity. Understanding these attack vectors underscores the importance of securing PHP installations promptly.
To mitigate the risks associated with CVE-2024-4577, the following steps should be taken:
Timely implementation of these measures is crucial to safeguard against potential exploits and ensure the security of web environments.
Target Geography: The impact of CVE-2024-4577 extends globally, affecting organizations worldwide utilizing PHP in CGI mode for web application development and hosting. Geographically, the vulnerability impacts regions across North America, Thailand, Europe, Asia, and beyond, where PHP is extensively deployed in various web hosting environments. Organizations in diverse geographical locations, irrespective of their specific region, are vulnerable to the potential exploitation of this critical security flaw.
Target Industry: CVE-2024-4577 poses a threat across various industries, including Technology, Banking, Financial Services and Insurance, healthcare, government, and e-commerce, relying on PHP for server-side scripting and web application functionalities. Threat actors may target industries based on the value of the data or services hosted on vulnerable PHP instances. Industries handling sensitive information or those heavily reliant on PHP-based web applications may face heightened risks.
Target Technology: This vulnerability affects PHP versions prior to 8.3, specifically when configured in CGI mode, a common setup in shared hosting and certain web server configurations. Given the widespread adoption of PHP across various technological ecosystems, the impact of this vulnerability can extend to interconnected systems, applications, and services, highlighting the need for comprehensive mitigation strategies.
Understanding the global impact, cross-industry implications, and technological dependencies of CVE-2024-4577 is crucial for organizations to accurately assess their risk exposure. Swift action, including patching, implementing security controls, and monitoring for suspicious activities, is essential to mitigate the potential risks associated with this critical vulnerability.
Threat actors are actively selling exploits for CVE-2024-4577 in dark web forums, posing significant risks to organizations using PHP in CGI mode.
In conclusion, CVE-2024-4577 presents a critical threat to organizations globally utilizing PHP configured in CGI mode for web application development and hosting. Collaboration, proactive monitoring, and a swift response guided by CYFIRMA’s insights are essential for defending against potential exploitation and safeguarding critical assets. It is crucial for organizations to remain vigilant about emerging threats, apply security patches promptly, and enhance their security posture to effectively mitigate the risks associated with CVE-2024-4577.