



This report provides a high-level overview of the most notable cybersecurity threats facing the Philippines. It examines a range of threats that are ever present and pose the most significant risks, such as financial, reputational, and national security. The report highlights the significant impacts of malware, ransomware extortion methods, DDoS attacks, credential stealing, and state-sponsored espionage.
The Philippines faces significant cybersecurity challenges, making it highly susceptible to cyberattacks. Factors contributing to this vulnerability include widespread internet usage, a lack of cybersecurity awareness, and underdeveloped cybersecurity infrastructure. Notably, the country is a prime target for cyber espionage activities conducted by nations like China, North Korea, and Russia. The looming potential conflict over Taiwan adds an element of unpredictability to the regional security landscape, with cyber warfare being a significant concern.
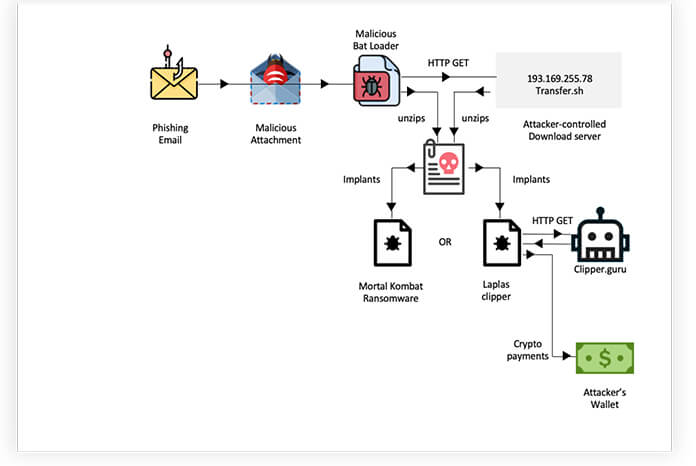
Recent trends indicate a surge in ransomware attacks within the Philippines, with sectors like finance, government, healthcare, education, and retail being primary targets. Over the past three months, the Medusa ransomware strain has inflicted severe damage globally, with the Philippines amongst the hardest-hit nations. Additionally, other malware variants, such as RedEnergy Stealer-as-a-Ransomware and MortalKombat ransomware, have been actively targeting the country.
In April 2023, a major data breach exposed the personal information of millions of Filipinos, including records from crucial institutions like the Philippine National Police (PNP), National Bureau of Investigation (NBI), Bureau of Internal Revenue (BIR), and Special Action Force (SAF). Furthermore, the Russian market has witnessed the illicit sale of stolen data logs from compromised Philippine government subdomains.
Cyber espionage remains a substantial threat, with groups like Earth Estries and FamousSparrow focusing their efforts on infiltrating government and technology sectors within the Philippines. This report offers a concise overview of the prevailing threat landscape, highlighting significant breaches and advanced persistent threats (APTs) that pose imminent risks to the country.
As widely reported, on September 22, PhilHealth experienced a Medusa ransomware attack, accompanied by a $300,000 ransom demand. In addition to the above, the following have also been observed around the Philippines Threat Landscape:
Ransomware operators are continuously improving their techniques with the intent to intimidate and force victims to pay the ransom. At present, ransomware operators are suspected to follow a 4-layer approach to target organizations which includes:
This type of malware encrypts data and demands a ransom for the decryption key. Financial institutions are particularly attractive targets because of their need for constant access to data.

The financial sector is the most targeted industry by ransomware in the Philippines. This is because financial institutions store a large amount of sensitive financial data, which is valuable to cybercriminals.

The government sector is also a prime target for ransomware attacks. Government agencies control critical infrastructure and store a large amount of sensitive data, such as personal information and national security secrets.

The healthcare sector is vulnerable to ransomware attacks because it stores a large amount of sensitive patient data, such as medical records and financial information.

The education sector is also a target for ransomware attacks. Educational institutions store a large amount of student data and intellectual property, which is valuable to cybercriminals.

The retail sector is vulnerable to ransomware attacks because it processes a large volume of credit card transactions. Cybercriminals can use ransomware to encrypt credit card data and then demand a ransom payment in exchange for the decryption key.
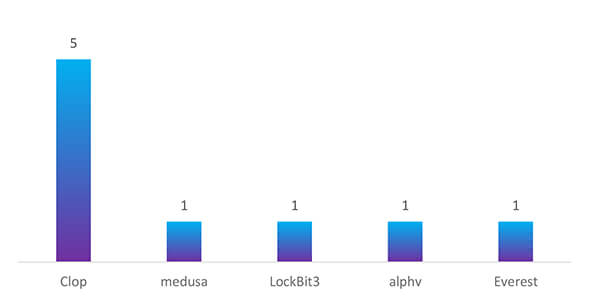
In the past 90 days, the Philippines has experienced ransomware attacks from various groups, including Cl0p, Medusa, LockBit3, ALPHV, and Everest. These incidents highlight the ongoing and diverse cyber threats faced by organizations in the region, emphasizing the critical need for robust cybersecurity measures and vigilance to protect against ransomware attacks.
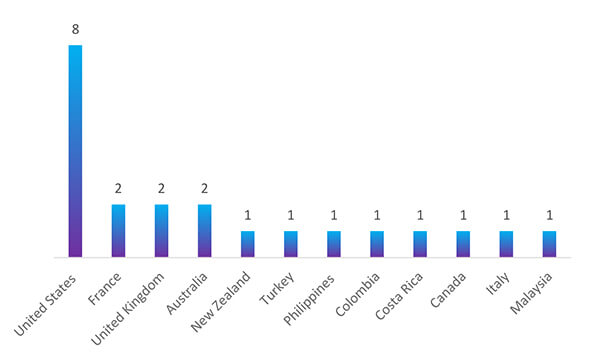
In the past 90 days, Medusa ransomware has targeted victims across the globe, with the United States being the hardest hit, totaling 8 incidents. France, the United Kingdom, Australia, and New Zealand have also suffered attacks, with 2 incidents each. This widespread campaign may be attributed to several factors, including the lure of valuable data, the lack of robust cybersecurity measures, and the ever-evolving tactics of ransomware operators. Organizations worldwide need to prioritize cybersecurity to mitigate the risk of falling victim to such attacks and protect sensitive data.
Screenshots (below) from the Dark Web of a recent ransomware attack targeting the Philippines’ health sector:
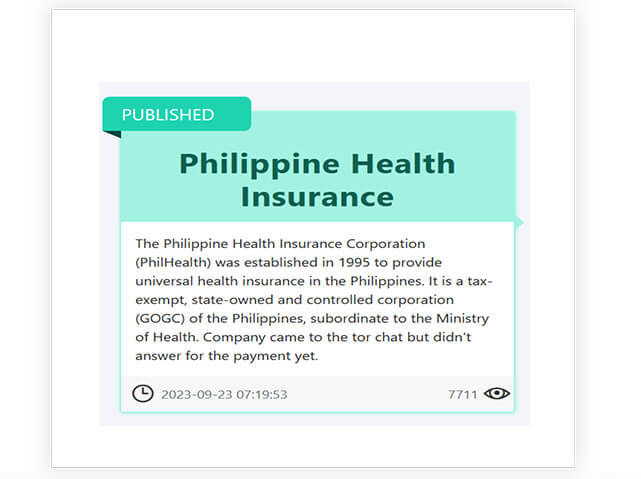

On September 22, PhilHealth experienced a Medusa ransomware attack, accompanied by a $300,000 ransom demand. This led to the temporary suspension of the online systems of the state health insurer. Subsequent to the ransom payment deadline passing, the responsible group uploaded more than 600 gigabytes of files to a leak site and a Telegram channel. The leaked information encompassed photos, bank cards, transaction receipts, and other sensitive data belonging to the victims.
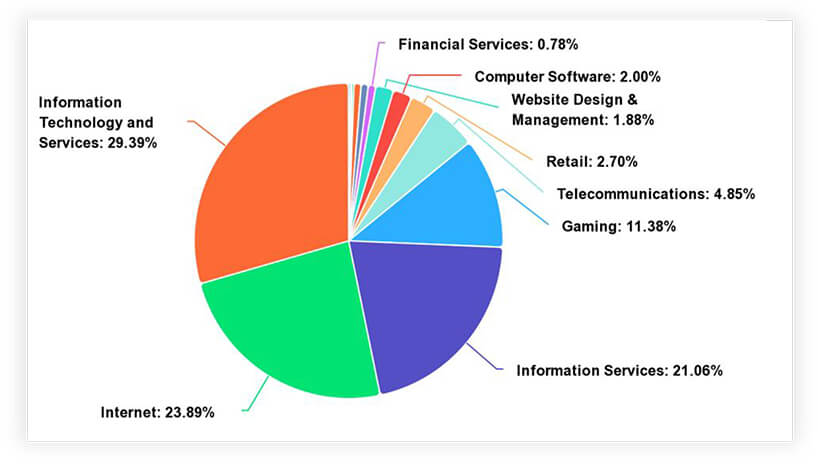
Over the last six months, the Philippines has confronted a dynamic landscape of distributed denial-of-service (DDoS) attacks, revealing a nuanced distribution of threats across industries. The Information Technology and Services sector emerged as the primary target, facing a substantial 29.39% of attacks, signifying a heightened and specific risk. Close behind were Internet-based services and Information Services, each with significant percentages, underlining a noteworthy impact on entities involved in data management and online platforms. Noteworthy percentages in the gaming, telecommunications, and Internet sectors emphasize the breadth of the threat, necessitating heightened cybersecurity measures. Although facing comparatively lower percentages, sectors like banking and financial services underscore the critical need for robust cybersecurity practices to protect sensitive data. This multifaceted distribution highlights the diverse industries grappling with DDoS challenges in the Philippines, demanding tailored and vigilant cybersecurity strategies.
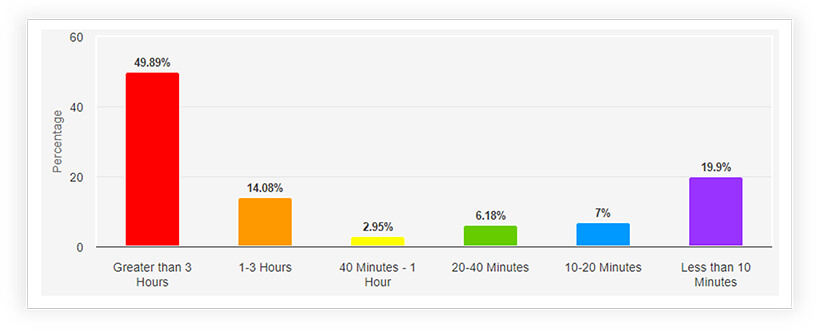
The DDoS attack landscape in the Philippines over the last six months reveals distinctive patterns in terms of attack durations. Notably, a substantial 49.89% of attacks persisted for durations exceeding three hours, indicating a prolonged and impactful threat. Attacks lasting between one to three hours accounted for 14.08%, while those lasting 40 minutes to an hour constituted 2.95%. A noteworthy 6.18% of attacks persisted for durations between 20 to 40 minutes, and 7% for 10 to 20 minutes. Attacks of shorter durations, ranging from less than 10 minutes, accounted for 19.90% of incidents. This breakdown underscores the diversity in attack durations, with nearly half of the attacks being protracted, potentially causing significant disruptions and emphasizing the need for sustained cybersecurity measures.
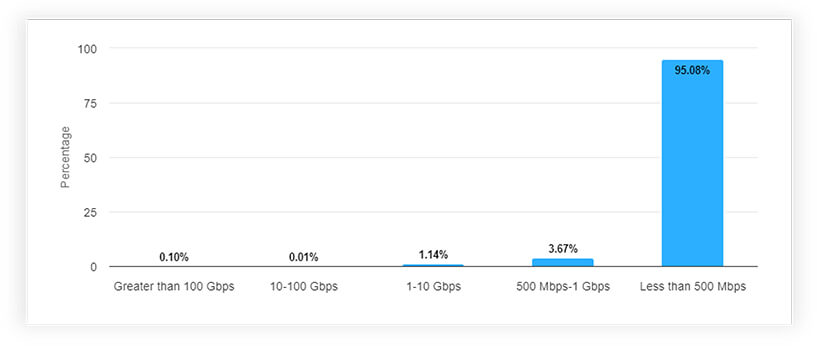
The distribution of DDoS attacks in the Philippines over the last six months can be categorized by their varying levels of intensity based on bitrate. A negligible fraction, just 0.1%, exceeded an exceptionally high threshold, surpassing 100 Gbps. Likewise, a minimal 0.007% fell within the range of 10-100 Gbps. A more noticeable 1.14% of attacks operated within the 1-10 Gbps range, signifying a moderate level of intensity. Significantly, 3.67% of attacks fell within the bandwidth of 500 Mbps to 1 Gbps. The vast majority, comprising 95.08%, were of lower intensity, registering at less than 500 Mbps. This diverse bitrate distribution highlights the importance of a flexible and adaptive cybersecurity strategy capable of effectively addressing both lower and higher-intensity DDoS threats in the Philippines.
The predominant sources of traffic in the analyzed DDoS attacks are identified in several key regions, namely the United States, Singapore, China, Denmark, Great Britain, Russia, Japan, France, and Canada. These countries contribute significantly to the observed DDoS activity, underscoring the global nature of the threat landscape.
A massive data hack in April 2023, which exposed 817.54 gigabytes of both applicant and employee records under multiple state agencies, including the Philippine National Police (PNP), National Bureau of Investigation (NBI), Bureau of Internal Revenue (BIR), and Special Action Force (SAF), has put the personal information of millions of Filipinos at risk.


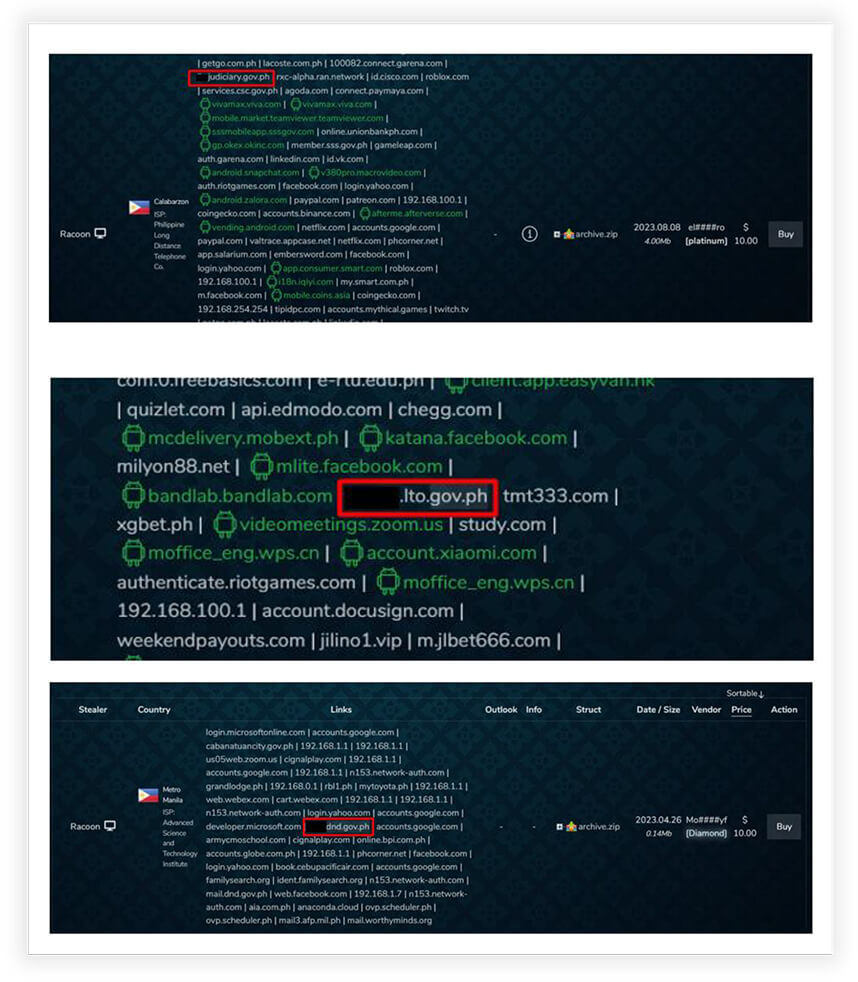
Stealer logs are a serious threat to computer users, as they can be used to steal personal and sensitive data, such as login credentials, financial information, and cryptocurrency. Stealer logs are created by malware that is installed on a victim’s computer, typically through a phishing email or malicious website. Once installed, the malware will scan the victim’s computer for valuable data and then exfiltrate it to a server controlled by the threat actor.
Stealer logs are often sold on criminal marketplaces, where they can be used by cybercriminals to commit a variety of crimes, such as identity theft, fraud, and cyber espionage.
The below three examples show compromised Stealer logs from Filipino Government agencies, for sale on the Dark Web.
Cyber espionage is a growing threat to all organizations, including businesses, governments, and critical infrastructure. It is the use of computers and networks to steal sensitive information, such as trade secrets, government secrets, and personal information.
Cyber espionage can be used to advance geopolitical goals, steal intellectual property, or commit financial crimes. It is often carried out by sophisticated actors with high-level resources and skills.
One specific area where cyber espionage is increasing is in the Philippines. Cyfirma has identified two advanced persistent threat (APT) groups that have targeted the Philippines, namely, Earth Estries and FamousSparrow:
Earth Estries, a well-known hacking group, has become a major player in a cyber espionage campaign that targets government and technology sectors in multiple countries. The campaign was discovered in August, and its primary focus is on two regions: Asia (Philippines, Taiwan, and Malaysia) and Germany and the United States. Earth Estries has been linked to a highly sophisticated operation with extensive experience in cyber espionage and illicit activities. The campaign has been active since at least 2020 and has global implications.
Interestingly, there are overlaps in tactics, techniques, and procedures (TTPs) between Earth Estries and FamousSparrow.
Earth Estries demonstrates a high level of sophistication, using advanced skills and experience in cyberespionage and illicit activities. Their arsenal includes various backdoors and hacking tools, with a focus on evading detection. They use PowerShell downgrade attacks to bypass security measures and exploit public services such as GitHub, Gmail, AnonFiles, and File.io for communication and data transfer.
FamousSparrow is a cyber-espionage entity with connections to APT groups like SparklingGoblin and Metasploit, which have been associated with activities originating from China and has been targeting government and technology sectors in the Philippines, as well as other countries in Asia, South Africa, Germany, and the United States.
In conclusion, the Philippines faces a complex and multifaceted cybersecurity landscape that demands immediate attention and concerted efforts to safeguard its digital infrastructure and sensitive data. The geopolitical overview underscores the country’s vulnerability, situated in a region marred by geopolitical tensions and the potential for unforeseen cyber repercussions in the event of a conflict over Taiwan. The Philippines’ strategic significance and close ties to the United States make it a prime target for cyberattacks, particularly from China, North Korea, and Russia.
Ransomware, a pervasive threat, continues to evolve in sophistication, employing tactics like double extortion and ransomware-as-a-service to maximize financial gains. The top five targeted industries, including finance, government, healthcare, education, and retail, face significant risks, not only in terms of financial loss but also potential data breaches and business disruptions.
Recent ransomware incidents, such as those involving Medusa ransomware, highlight the urgent need for robust cybersecurity practices. Moreover, the massive data breach in April 2023, exposing sensitive information from key government agencies, underscores the severity of the threat and the importance of data protection.
Additionally, the sale of compromised Philippine government subdomains further exacerbates cybersecurity concerns, potentially leading to various criminal activities. Notably, cyber espionage groups like Earth Estries and FamousSparrow targeting government and technology sectors within the Philippines pose a significant threat to national security and the protection of sensitive information.
Considering these challenges, it is imperative for the Philippines to prioritize the enhancement of network security standards and cybersecurity practices across all sectors. Collaboration, information sharing, and investments in cutting-edge cybersecurity technologies are vital steps to mitigate the ever-evolving cyber threats and ensure the nation’s digital resilience in an increasingly interconnected world.