HEALTHCARE Q1 I 2026 : INDUSTRY REPORT
EXECUTIVE SUMMARY The CYFIRMA Industry Report delivers original cybersecurity insights and telemetry-driven


EXECUTIVE SUMMARY The CYFIRMA Industry Report delivers original cybersecurity insights and telemetry-driven

EXECUTIVE SUMMARY At CYFIRMA, we continuously monitor emerging threat techniques that abuse trusted

EXECUTIVE SUMMARY The CYFIRMA Industry Report delivers original cybersecurity insights and telemetry-driven

INTRODUCTION CYFIRMA assesses that Mamba 2FA is a representative of a broader class of adversary-in-the-middle
EXECUTIVE SUMMARY SolyxImmortal is a Python-based Windows information-stealing malware that combines

Kimsuki, an advanced persistent threat (APT) group active since at least 2012, is suspected to be

EXECUTIVE SUMMARY The CYFIRMA Industries Report provides cutting-edge cybersecurity insights and telemetry-driven
EXECUTIVE SUMMARY Ransomware activity in December 2025 highlights an evolution toward cartel-style,

EXECUTIVE SUMMARY Multi-Factor Authentication (MFA) has long been positioned as a definitive control

EXECUTIVE SUMMARY The CYFIRMA Industries Report provides cutting-edge cybersecurity insights and telemetry-driven
Executive Summary: Recent monitoring of underground forums and Telegram communities has identified
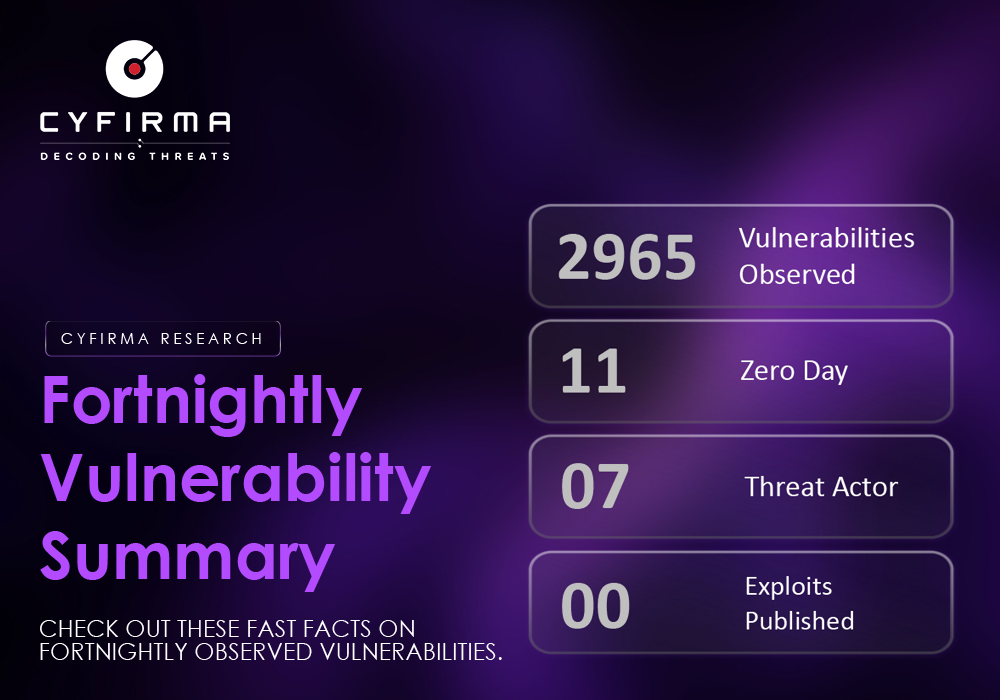
Fortnightly Vulnerability Summary CHECK OUT THESE FAST FACTS ON FORTNIGHTLY OBSERVED VULNERABILITIES.

EXECUTIVE SUMMARY The CYFIRMA Industries Report provides cutting-edge cybersecurity insights and telemetry-driven

EXECUTIVE SUMMARY The CYFIRMA Industries Report provides cutting-edge cybersecurity insights and telemetry-driven

EXECUTIVE SUMMARY CYFIRMA has identified a targeted malware campaign attributed to APT36 (Transparent

EXECUTIVE SUMMARY Hacktivist Proxy Operations describe a class of deniable cyber pressure activities

EXECUTIVE SUMMARY CYFIRMA is dedicated to providing advanced warning and strategic analysis of the

EXECUTIVE SUMMARY CYFIRMA examines a sophisticated phishing campaign that leverages QR-code-based

Fortnightly Vulnerability Summary CHECK OUT THESE FAST FACTS ON FORTNIGHTLY OBSERVED VULNERABILITIES.

EXECUTIVE SUMMARY The CYFIRMA Industry Report delivers original cybersecurity insights and telemetry-driven