



CVE-2024-6387, known as regreSSHion, is a high-severity vulnerability in OpenSSH’s server (sshd) that involves a sophisticated race condition during the authentication phase, allowing unauthenticated remote code execution with root privileges. This flaw impacts most Linux distributions due to their default OpenSSH installation, with older versions being particularly vulnerable. The severity is rated at CVSS 8.1, indicating significant risk. The vulnerability is actively discussed on the Deep/Dark Web, and reports suggest that affected device IP addresses are being circulated in underground forums. It is currently being exploited in the wild, as documented by CISA’s Known Exploited Vulnerabilities Catalog. Immediate action is essential to address this critical threat.
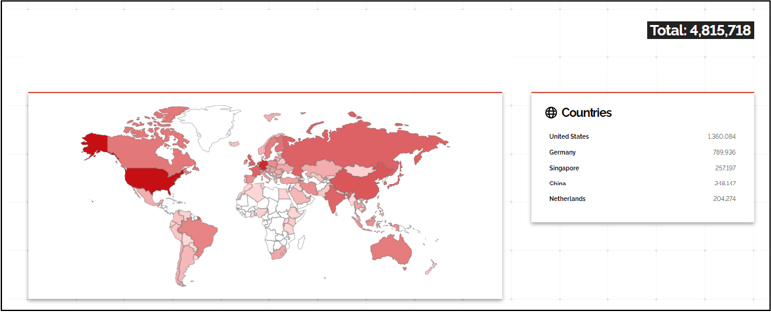
CVE-2024-6387 is a critical vulnerability in OpenSSH’s server (sshd) that allows unauthenticated remote code execution with root access. Affecting over 4.8 million internet-exposed instances of OpenSSH servers, this flaw poses a significant risk across various industries and geographies. It reintroduces an issue that had been previously patched, making it a notable security concern. The vulnerability enables attackers to execute malicious code without authentication, potentially compromising sensitive systems and data. Immediate patching and enhanced security measures are essential to mitigate the risks associated with this severe exploit.
Key Takeaways:
Acknowledgements:
The CYFIRMA Research team acknowledges security researchers who responsibly disclosed this vulnerability.
Vulnerability Type: Remote unauthenticated code
CVE ID: CVE-2024-6387
CVSS Severity Score: 8.1 (High)
Application: OpenSSH
Impact: Allowing remote unauthenticated code execution
Severity: High
Affected Versions: OpenSSH versions between 8.5p1 and 9.8p1
Patch Available: Yes
CVE-2024-6387, known as regreSSHion, is a critical vulnerability in OpenSSH’s server (sshd) that allows unauthenticated remote code execution, granting full root access. This vulnerability arises from a race condition in how sshd handles signals, which can be triggered by a remote attacker failing to authenticate within a specific time frame. The issue affects OpenSSH’s default configuration and does not require user interaction, making it a significant exploit risk. Unlike OpenBSD, which deals with the exploitable signal path differently, most modern systems have mitigations that reduce the likelihood of successful exploitation. While the exploit is technically possible, its success depends on various factors, and not all security controls are effective against this vulnerability.
CVE-2024-6387 has significant impacts, including unauthorized access where attackers can gain root-level privileges if successful. This access can lead to the exposure of sensitive information stored on compromised systems, such as user credentials, private keys, and confidential files. Additionally, attackers can manipulate system configurations, install backdoors, or alter critical files, disrupting normal operations and compromising system integrity. With root access, they can further escalate privileges, potentially gaining complete control over the affected systems.
The CVE-2024-6387 vulnerability affects specific versions of OpenSSH. Versions earlier than 4.4p1 are susceptible to this signal handler race condition unless they have been patched. Versions from 4.4p1 up to, but not including, 8.5p1 are not vulnerable due to a transformative patch, which made a previously unsafe function secure. However, the vulnerability resurfaces in versions from 8.5p1 up to, but not including, 9.8p1 due to the accidental removal of a critical component in a function.
Is there already an exploit tool to attack this vulnerability?
Yes, exploit tools for CVE-2024-6387 are already circulating. These tools highlight the seriousness of the vulnerability and emphasize the critical need for users to promptly address it to prevent potential exploitation and compromise of their systems.
Has this vulnerability already been used in an attack?
Yes, there is evidence that the CVE-2024-6387 OpenSSH vulnerability has been exploited in the wild. Malicious scripts and files have been used in attacks leveraging this vulnerability. These attacks have allowed threat actors to gain unauthorized root access to affected systems, enabling them to install malware, manipulate data, create persistent backdoors, and propagate through networks.
Are hackers discussing this vulnerability in the Deep/Dark Web?

Hackers are actively discussing the CVE-2024-6387 vulnerability on the Deep/Dark Web, with reports of affected device IP addresses being shared in underground forums.
What is the attack complexity level?
The attack complexity level for CVE-2024-6387 in OpenSSH is assessed as High.
Our analysis discovered more than 4.8 million internet-exposed instances of OpenSSH servers vulnerable to the RegreSSHion exploit (CVE-2024-6387). This critical flaw allows remote unauthenticated code execution, potentially compromising entire systems. Attackers can install malware, manipulate data, create backdoors, and propagate within networks. While executing the exploit is challenging, the risk remains high, especially for enterprises relying on OpenSSH for remote management.
The provided code is a sophisticated proof-of-concept (PoC) exploit for CVE-2024-6387, an exploit targeting a race condition vulnerability in OpenSSH’s sshd server on glibc-based Linux systems. Authored by 7etsuo and dated July 1, 2024, the exploit aims to achieve remote code execution (RCE) as root by leveraging a vulnerability where the SIGALRM handler in sshd calls async-signal-unsafe functions, leading to a race condition that can be exploited.
The exploit starts by setting up a connection to a specified target IP and port. It then performs an SSH handshake, which involves sending and receiving version strings and KEX_INIT (key exchange initialization) packets. This handshake ensures that the connection is correctly established and prepared for further interactions.
The core of the exploit involves manipulating the heap layout on the target system. The exploit sends a series of carefully crafted packets designed to create specific memory allocations and deallocations. This process includes allocating and freeing tcache chunks, creating large and small holes in memory, and setting up fake file structures within these holes. These fake structures are intended to overwrite critical areas in memory when the race condition is triggered.
Timing is a crucial aspect of this exploit, which measures the parsing time of packets by sending error packets and records the response times. This timing information is used to adjust the precise moment when the final packet (containing the shellcode and fake structures) is sent. The goal is to hit the narrow window, where the race condition can be exploited.
The final packet is sent in two stages: first, all but the last byte of the packet is sent, and then, at the precise calculated moment, the last byte is sent to trigger the race condition. If successful, the exploit leads to arbitrary code execution with root privileges on the target system.
The exploit iterates over multiple possible base addresses for glibc to bypass Address Space Layout Randomization (ASLR). For each base address, it attempts exploitation up to 20,000 times, adjusting timing parameters based on feedback from previous attempts. If successful, it prints a message indicating the potential success of the exploitation.
This exploit demonstrates advanced techniques in heap manipulation, precise timing for race condition exploitation, and iterative strategies to bypass ASLR, all aimed at achieving remote code execution on a vulnerable OpenSSH server.
To mitigate CVE-2024-6387, update your OpenSSH server to the latest version and apply all relevant security patches. If SSH agent forwarding is not needed, disable it to reduce the risk. Restrict SSH access by allowing only trusted IP addresses or networks and use firewall rules or TCP wrappers for control. Regularly monitor SSH logs for suspicious activity, including failed login attempts or unexpected commands. Additionally, implement network segmentation to isolate critical systems from less critical ones, thereby limiting the potential impact of an attack
Target Geography:
CVE-2024-6387, known as regreSSHion, is a critical vulnerability in OpenSSH’s server (sshd) that allows unauthenticated remote code execution, granting full root access. This vulnerability impacts regions across North America, Europe, and Asia. For effective external threat landscape management, focus on understanding the worldwide threat environment. Stay informed by monitoring international security news, reports, and alerts, and collaborate with global cybersecurity organizations and government agencies. Identify and analyze threat actors operating across different regions, including nation-state actors, cybercriminal groups, hacktivists, and insider threats, by examining their tactics, techniques, and procedures (TTPs). This comprehensive global awareness will enhance your ability to anticipate and defend against threats that span multiple regions
Target Industry:
CVE-2024-6387 is a critical vulnerability in OpenSSH that poses significant risks to various industries. Financial institutions might be targeted for monetary gains, while energy and critical infrastructure sectors could face threats from nation-state actors. Healthcare organizations are also at risk, particularly due to geopolitical tensions. As threat actors may choose targets based on the value of data or services managed through this vulnerability, industries handling sensitive information or relying heavily on OpenSSH for operational continuity should be particularly vigilant. The external threat landscape management should involve monitoring and assessing these sector-specific risks to better protect against potential exploits.
Target Technology:
CVE-2024-6387, known as regreSSHion, is a severe vulnerability in OpenSSH that impacts a wide range of technologies. Organizations leveraging OpenSSH for secure remote access should be particularly aware of the external threat landscape. As this vulnerability affects systems worldwide, external threat landscape management should focus on assessing the risks associated with OpenSSH deployments. This includes monitoring for emerging threats, applying timely patches, and understanding how attackers might exploit the vulnerability in various technology stacks. By staying informed about potential attack vectors and maintaining robust security measures, organizations can better defend against the exploitation of CVE-2024-6387.

In underground forums, threat actors are actively focusing on the exploitation of the recently discovered CVE-2024-6387 vulnerability in OpenSSH. Malicious actors are sharing and analyzing exploits related to this vulnerability, including technical details and potential impacts of associated proof-of-concepts (PoCs). This level of attention highlights the serious concern within the cybercriminal community about the severity and potential consequences of this vulnerability.
In conclusion, CVE-2024-6387, known as regreSSHion, represents a critical vulnerability in OpenSSH that exposes systems to unauthorized remote code execution with root access. Affecting a wide range of industries and technologies, including those using OpenSSH for operational continuity, this vulnerability underscores the need for heightened vigilance and proactive security measures. Organizations must stay informed about the external threat landscape, apply security patches promptly, and adopt best practices to mitigate risks. By addressing these concerns, businesses can protect their systems from potential exploitation and safeguard sensitive information against evolving cyber threats.