



At CYFIRMA, we are committed to offering up-to-date insights into prevalent threats and tactics employed by malicious actors, targeting both organizations and individuals. This thorough examination delves into the widespread adoption of ‘Nikki Stealer’, a malicious tool available for purchase on Discord or Telegram. The developer, who has a history as a defacer, now sells this stealer, designed to steal Discord tokens, browser cookies, and credentials, with numerous users utilizing the tool. Our research explores the various evasion techniques utilized by threat actors to avoid detection, while also shedding light on the intricate processes involved in creating resilient malware payloads.
Nikki Stealer v1 was initially discovered on Telegram, where the developer showcased its undetectable capabilities. We managed to gather details about the older version of Nikki Stealer. The malware’s developer, Sk4yx, operates primarily from Discord, where he shares the latest insights and recent developments of the stealer, primarily in Portuguese. The latest version (v9) is now available for purchase: this version is capable of stealing browser cookies, credentials, and other sensitive data, and is developed using the Electron framework by GitHub. Interestingly, we have observed similarities in source code between Nikki Stealer and Fewer Stealer.
Nikki Stealer drops PE (Portable Executable) files into the startup folder, ensuring it runs automatically every time the system starts up.
The malware attempts to harvest and steal browser information, including browsing history, and passwords.
Nikki Stealer tries to load missing Dynamic Link Libraries (DLLs), which could be necessary for its proper functioning or to extend its capabilities.
The malware is built using the Electron framework, enabling the development of cross-platform desktop applications using web technologies like JavaScript, HTML, and CSS.
| File Name | Cum3d_Setup.exe, nikki 1.1.4 (1).exe |
| File Size | 66.47 Mb |
| Signed | Not Signed |
| MD5 Hash | a4317a8d4595f181c56efa6b3be6c14b |
| SHA-256 Hash | 0fa64d5ad4c84011bef6e838d0f70121a3af53df5dbc3b5f5f0c16a8fb495244 |
| First Seen in the Wild | October 2023 |
At the time of analysis, i.e. March 10th, 2024, the stealer is flagged as malicious by only 2 vendors.
Note: The two detections by the antivirus engine are based on heuristics.
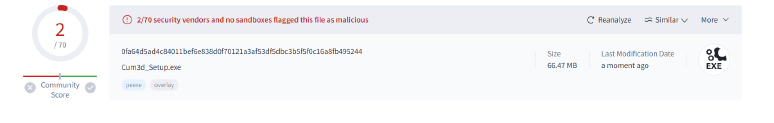
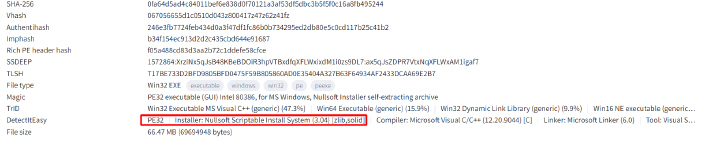
Upon analysis, it’s determined that the file is packed using the Nullsoft packer, which can be unpacked using 7zip.
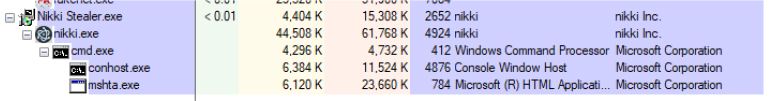
Once executed, the Nikki stealer drops a second payload named nikki.exe inside the temp folder, which is the main executable file.
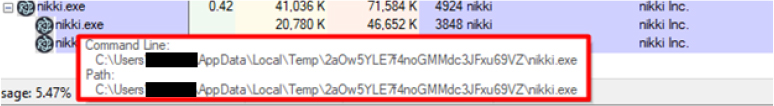
The below snippet shows the folder where the executable is stored.
Modifying process features and prefetch settings could be used to manipulate system behavior or evade detection by security software. For example, disabling certain features might help the malware to avoid detection or hinder analysis by security tools.
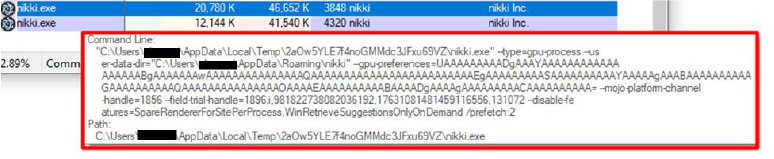
To achieve persistence, the Nikki Stealer first drops itself into the startup folder.
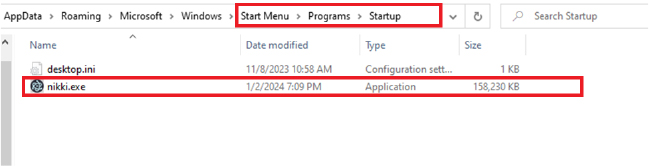
This creates an entry into a start menu, commonly used by adversaries for persistence purposes. Adversaries often place their malicious binaries or shortcuts in these folders to ensure their malware continues to run even after system reboots or other disruptions.
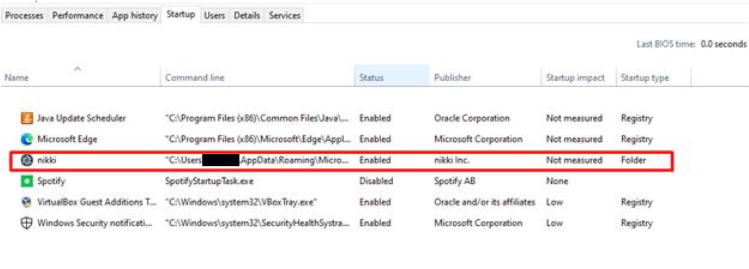
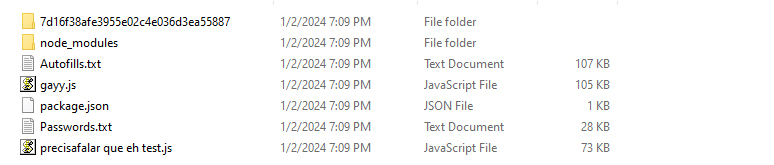
After executing the initial payload, the Nikki Stealer malware places a second payload in the system’s temp folder. In the provided snippet, the primary executable, which is the Nikki Stealer, is accompanied by various DLL files, as well as autofill.txt and password.txt files. These text files are filled with fake data by the malware author for testing purposes. Our focus here will be on the executable file.
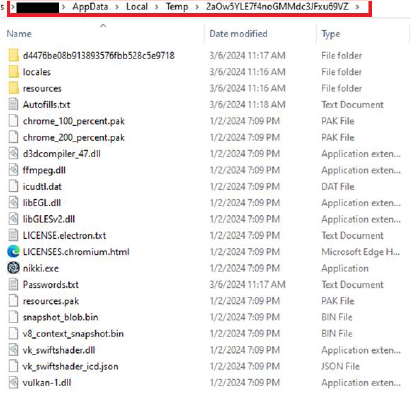
The main executable is a 64-bit file, sized at over 160 megabytes. Additionally, the screenshot displays information about the version and name of the stealer.
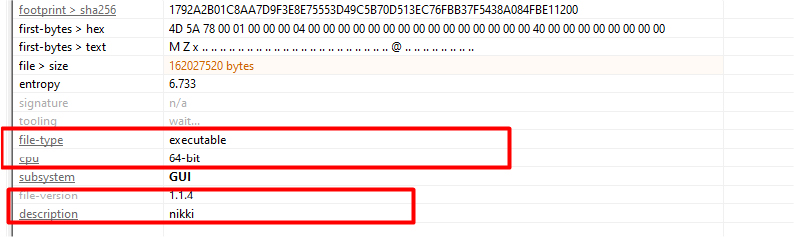
The primary executable file i.e. ‘nikki.exe’ is built using the Electron framework.
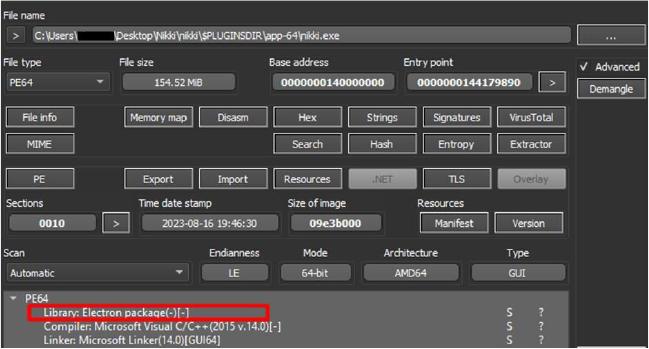
To provide context, Electron is a software framework made by GitHub, used for creating desktop applications that work on different operating systems, like Windows, macOS, and Linux.
Electron lets developers use web technologies like JavaScript, HTML, and CSS to build their applications. Under the hood, it uses two main components: Chromium, which is responsible for displaying web content, and Node.js, which runs the backend code.
Attackers like to use Electron because it enables them to create malicious software that can run on many different types of computers and develop code that works on multiple platforms without needing individual rewrites.
Meanwhile, in the background, these applications can secretly access important functions of the operating system, allowing attackers to perform malicious activities without the user’s knowledge.
The app built with Electron stores its source code and essential files within a resource file. Inside this resource file, you’ll typically find an “app.asar” file, which serves as the main file containing all the source code and important resources.
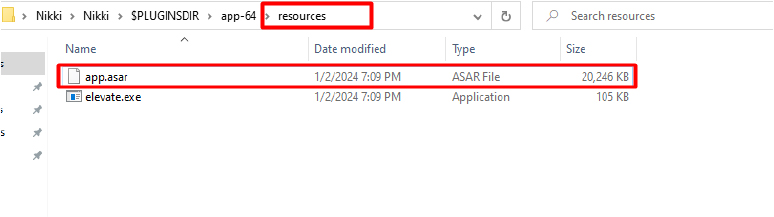
To extract the file with ‘.asar’ extension, we can use a plugin designed for 7-Zip, available on the internet. Once extracted, we’ll have access to the complete source code of this sample application.
The file “precisafalar que eh test” translates to “I need to say that it’s a test.” This file contains the source code for Nikki Stealer. Additionally, within the password text file, there are numerous fake credentials provided. These credentials are used to test the capabilities of the stealer.
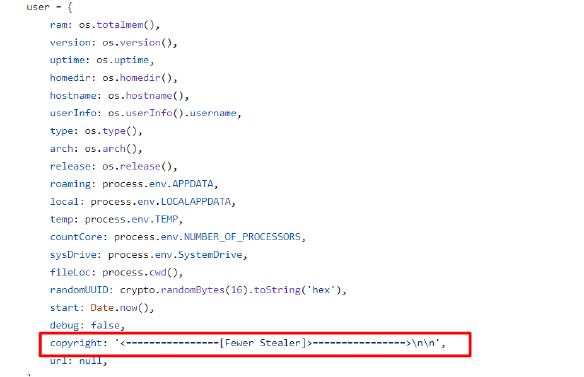
The below screenshot highlights the Nikki Stealer source code which looks similar to the Fewer Stealer source code.
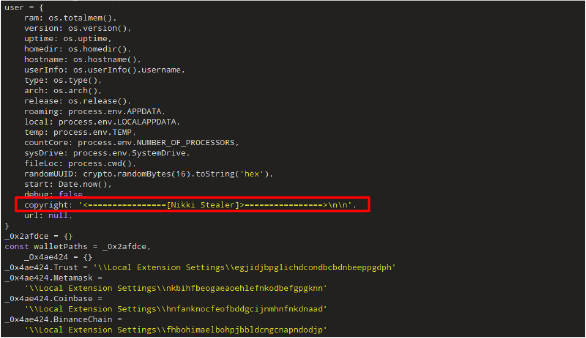
The Fewer stealer source code found on GitHub, has similarities with the Nikki Stealer source code:
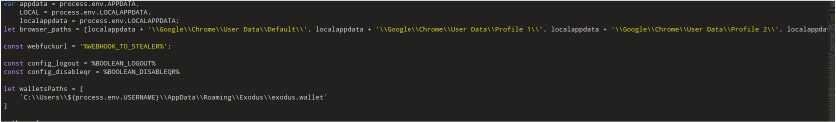
This malware’s main aim is to steal saved passwords and session cookies from web browsers like Chrome, Opera, Microsoft Edge, and Brave. For each browser, the malware locates where sensitive user data is stored, such as cookies and login credentials for different websites.
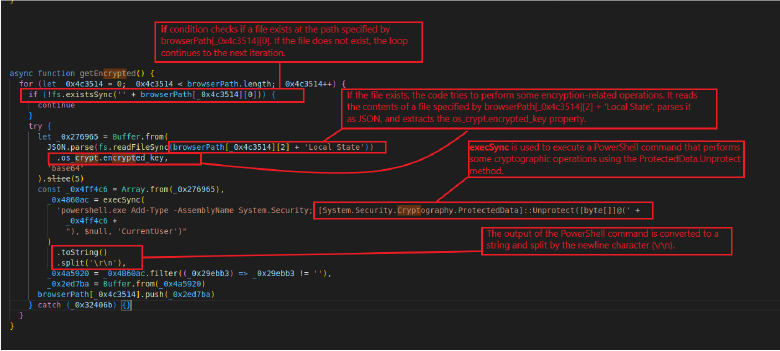
This JavaScript code seems to be designed to gather encrypted data, possibly related to browsers. It goes through an array called “browserPath” that holds possible paths to browser data.
Nikki Stealer v9 has been launched on their Discord channel with various subscription plans available. This new version has a more efficient injector, making it even more effective at stealing sensitive information from target systems.
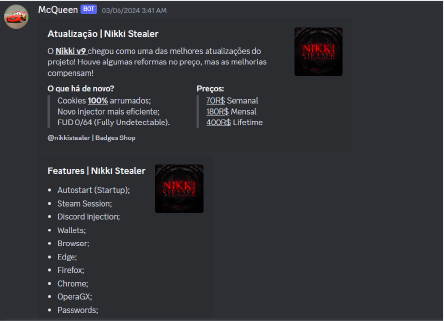
The Nikki Stealer channel was established on Telegram on October 23, 2023. During our investigation, we discovered similarities in the descriptions of both the Nikki Stealer and Crow Stealer channels. This suggests that Sk4yx; the developer associated with the Nikki Stealer code, is also the creator of the Crow Stealer malware. Additionally, past findings indicate that the Crow Stealer channel promoted the Nikki Stealer channel, further supporting the connection between the two projects and their common developer, Sk4yx.
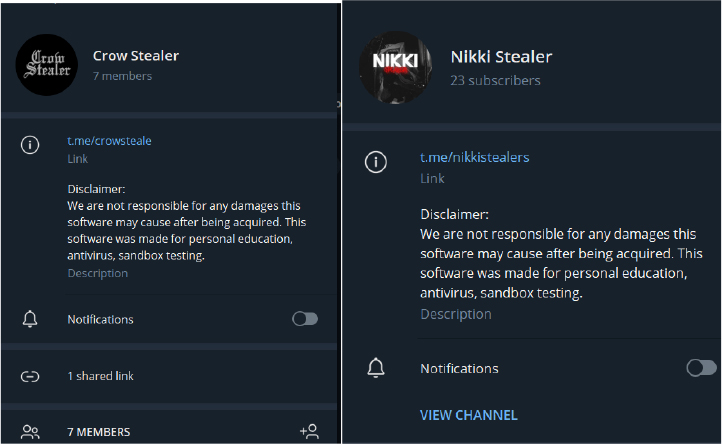
While the Telegram channel appears to have low activity, it’s noteworthy that Sk4yx and associated individuals are predominantly active on Discord, boasting a user base of over 136 members. Within this Discord community, they promote not only malicious activities but also engage in illegal behavior, such as sharing photographs of drugs.
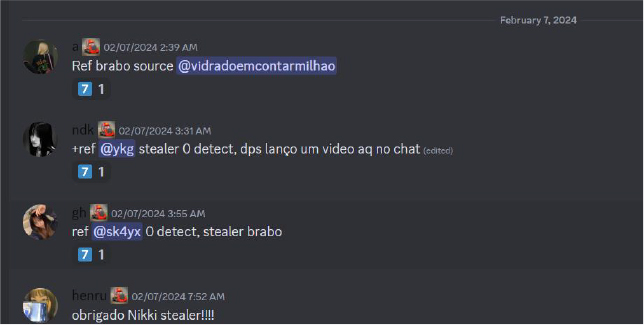
Users who have purchased Nikki Stealer are praising its effectiveness, claiming that it is fully undetectable (FUD) and has a zero detection rate.
During our analysis, we discovered the Instagram profile of Sk4yx, where he mentioned the Nikki Stealer website.
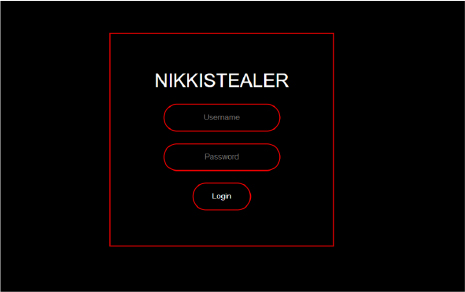
Upon further investigation, we found evidence in the web archive indicating the existence of a login panel for Nikki Stealer, although it is currently inactive.
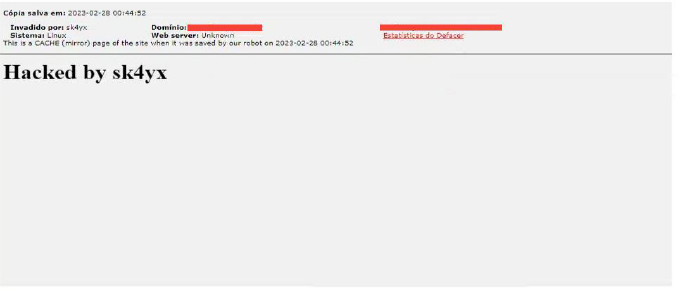
It has been noted that Sk4yx has referred to themselves as an ex-defacer, and evidence suggests that they have defaced websites belonging to organizations in Brazil in the past. Additionally, Sk4yx maintains an account on PyPI, but there has been no activity observed from this account from an extended period.
Based on our analysis of the chat conversations within the Discord platform, we have medium confidence to suggest that Sk4yx/Sk4yxx, is a developer based in either Brazil or Portugal, and is the creator of the Nikki Stealer. This conclusion is further supported by references to their name within the source code.
Below is a screenshot from Sk4yx showcasing drugs they have access to.
Translation from Portuguese to English: to muitondoido virado > I am very crazy turned

Another member of the Nikki Stealer group, known by the alias YKG, has a YouTube channel to promote their activities.
| No. | Indicator (SHA-256) | Remarks |
|---|---|---|
| 1 | 0fa64d5ad4c84011bef6e838d0f70121a3af53df5dbc3b5f5f0c16a8fb495244 | Nikki Stealer 1st Payload |
| 2 | 01ae1b2996a35fb5a3eb40c33763058b01b892253458fb6c9a8b0efc6b98d0a0 | JS file |
| 3 | 7a32c14d724c8904511ccb4eca27cf62aaa31d85a05a0e443d28ad95d35b363c | JS file |
| 4 | 1792a2b01c8aa7d9f3e8e75553d49c5b70d513ec76fbb37f5438a084fbe11200 | Nikki Stealer 2nd Payload |
| No. | Tactics | Technique |
|---|---|---|
| 1 | Execution (TA0002) | T1047: Windows Management Instrumentation T1059: Command and Scripting Interpreter |
| 2 | Persistence (TA0003) | T1547.001: Registry Run Keys / Startup Folder T1574.002: DLL Side-Loading |
| 3 | Privilege Escalation (TA0004) | T1055: Process Injection T1547.001: Registry Run Keys / Startup Folder |
| 4 | Defense Evasion (TA0005) | T1036: Masquerading T1055: Process Injection T1574.002: DLL Side-Loading |
| 5 | Credential Access (TA0006) | T1003: OS Credential Dumping |
| 6 | Discovery (TA0007) | T1012: Query Registry T1057: Process Discovery T1018: Remote System Discovery T1082: System Information Discovery |
| 7 | Collection (TA0009) | T1005: Data from Local System |
| 8 | Command and Control (TA0011) | T1573: Encrypted Channel T1071: Application Layer Protocol |
Investigation into the Nikki Stealer reveals a sophisticated and actively developed malware tool. Operated primarily through Discord and previously discovered on Telegram, Nikki Stealer demonstrates a high level of stealth and persistence, dropping PE files into the startup folder for automatic execution. Its primary function revolves around harvesting sensitive browser information, including browsing history and passwords, with attempts to mitigate missing dependencies by loading DLLs as needed. Built on the Electron framework, Nikki Stealer leverages modern web technologies for its development, enhancing its cross-platform capabilities. Overall, the presence of Nikki Stealer underscores the evolving landscape of cyber threats and the importance of robust security measures to mitigate its impact.
Implement Defense-in-Depth Strategy: Develop a comprehensive defense strategy that combines network segmentation, robust perimeter defenses, and endpoint security to create multiple layers of protection against such threats.
Invest in Threat Intelligence: Engage with threat intelligence services to stay informed about the evolving tactics, techniques, and procedures employed by malware operators. Regularly update defenses based on the latest threat intelligence to enhance proactive detection capabilities.
Enhance Employee Training: Conduct regular cybersecurity training programs to educate employees about phishing threats, social engineering, and safe browsing practices. Building a security-aware culture can significantly reduce the likelihood of successful infostealer infections.
Develop an Incident Response Plan: Establish a robust incident response plan that outlines clear procedures for identifying, containing, eradicating, and recovering from a Nikki Stealer infection. Regularly test and update the plan to ensure effectiveness.
Conduct Regular Security Audits: Perform periodic security audits to assess the effectiveness of existing security controls, identify potential weaknesses, and validate the organization’s overall security posture. Use the findings to make informed adjustments and improvements.
Collaborate with Industry Peers: Engage in information sharing and collaboration with industry peers, cybersecurity communities, and relevant authorities. Sharing threat intelligence and best practices can enhance collective resilience against emerging threats like Nikki Stealer.
Update and Patch Systems: Regularly update and patch operating systems, software, and applications to address vulnerabilities that malware like Nikki stealer exploits. Automated patch management tools can streamline this process and minimize the attack surface.
Utilize Advanced Endpoint Protection: Deploy advanced endpoint protection solutions that incorporate behavioural analysis, heuristic detection, and threat intelligence to identify and mitigate the specific techniques employed by Nikki stealer. Ensure these solutions are regularly updated with the latest detection rules such as the one given in the report.
Implement Application Whitelisting: Restrict the execution of unauthorized applications by implementing application whitelisting. This helps prevent the execution of unknown or malicious binaries, hindering Nikki’s stealer ability to run on endpoints.