



The team at CYFIRMA recently intercepted Android malware suspected to have been delivered by a Pakistan-based APT group targeting Indian defense personnel. Surprisingly, the campaign has been active for over a year. The unidentified threat actor possibly utilized Spynote, or its modified version known by Craxs Rat, obfuscating the app with a high level of complexity, making it difficult to understand.
The team at CYFIRMA collected an Android sample that was delivered via WhatsApp Messenger to target Indian defense personnel. The payload was possibly generated by the Spynote Android remote administration tool, or a modified version known by the name ‘Craxs Rat’. Based on the target region, industry, and method of communication observed as part of social engineering, we attribute this threat actor to the region of Pakistan with a medium degree of confidence.
Further investigation by the team at CYFIRMA revealed the delivered payload was part of a campaign that has been running for a year and has similarities with a payload flagged on VirusTotal, communicating with the same C2 server.
The threat actor attempted social engineering by impersonating a senior officer and attempting to deliver the app directly on WhatsApp. The delivered apps were named “MNS NH Contact.apk” and “Posted out off.apk”. The threat actor attempted to make the files appear defense-related, however, when installed, the app names were different from what they were named when clicked. The default app that was built using Craxs Rat was modified according to the threat actors’ objectives, which seem to be gaining access to victims’ contact lists, call logs, and SMSs. We also observed a screen monitoring feature, but this is only activated when the victim turns on accessibility access for the installed malicious app: this app didn’t oblige the victim to do so, indicating that they intended to gather information and follow maximum security evasion tactics.
The team tried to install the app on an Android emulator, but the app crashed, hinting at the use of an anti-emulator feature, the same feature is available in Craxs RAT.
The screenshot shows the installation of MNS NH Contact.apk but when installation progressed, the app revealed its real name – cleverly disguising itself as the “Contacts” app.
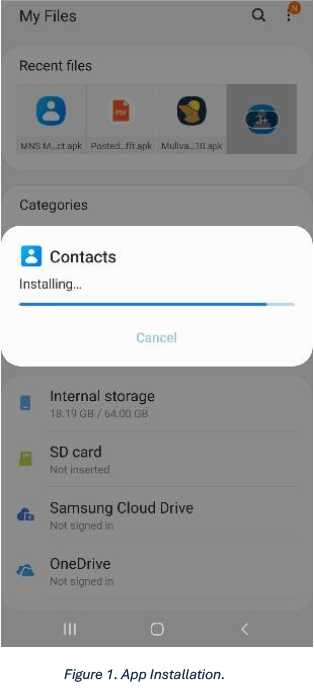
Upon opening the app, it directs the victim to a one-time click permission page, which, once clicked, takes the victim to a bogus page. The app then disappears from the menu.
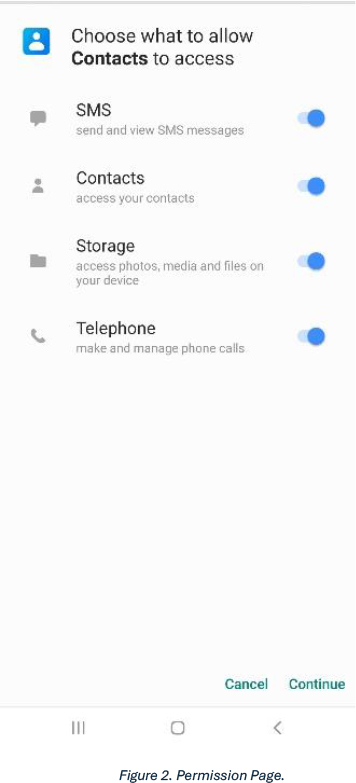
The team learned the app was highly modified and obfuscated to evade Android security measures and antivirus software. The team found a module to fetch the location of the victim, however, there was no request for this on the one-time click permission page, and permission for the location was not found in the Android Manifest file either.
Screenshot of Android Manifest File associated with the MNS NH Contact.apk.
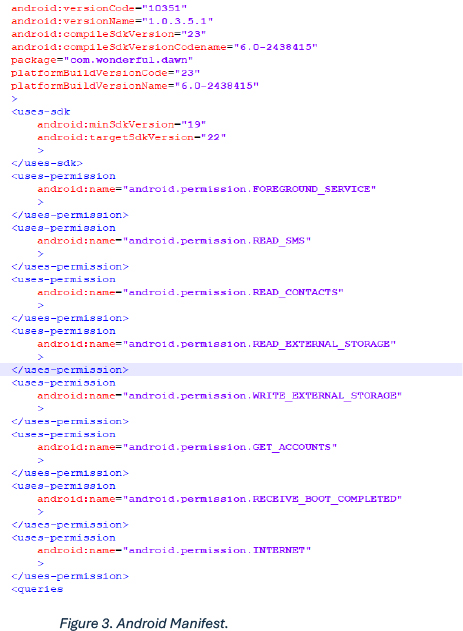
Below are major permissions that the app is exploiting to fetch the information from victims’ phones:
| Sr no. | Permission | Description |
| 1 | READ_SMS | Helps threat actors to fetch SMSs. |
| 2 | READ_CONTACTS | With this permission threat actor can fetch an updated contact list of the victim. |
| 3 | READ_EXTERNAL_STORAGE | With this permission, the threat actor can interact with the file manager of the mobile. |
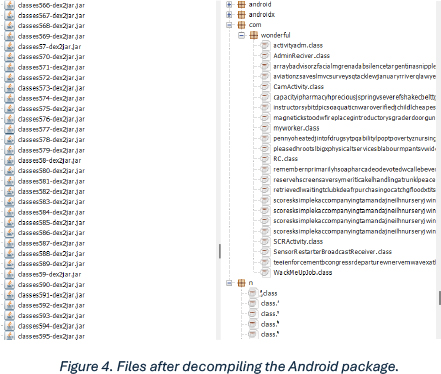
The screenshot below reveals that the threat actor split a dex file into 600 parts, which were later converted into .jar files by the team. Splitting the dex file into 600 parts was part of the obfuscation technique:
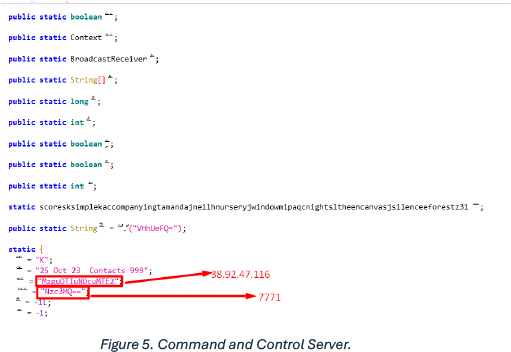
The screenshot below reveals the command-and-control server encrypted with base64 encryption, which is also seen in the payload generated by Spynote and Craxs Rat:
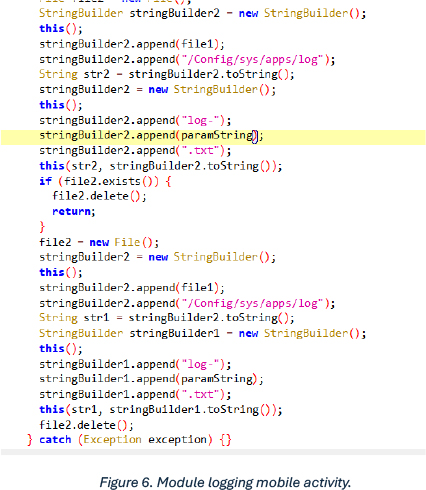
The below shows part of a module that stores the activity of mobile phones in a .txt file:
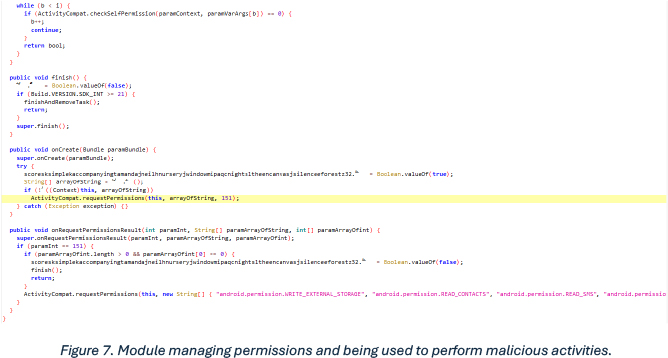
This snippet is part of a module that is responsible for managing the permissions:
During our analysis, we discovered that the threat actor is utilizing Spynote or its customized variant known as Crax Rat. Spynote, along with its updated version – developed by the threat actor EVLF – is highly sought after by threat actors engaged in various fraudulent and criminal activities. It is noteworthy that an unidentified actor has already leveraged it for cyber espionage, targeting defense personnel to gather intelligence from the neighboring country. Considering the tool’s widespread availability, it is intriguing that this unknown APT group from Pakistan has chosen to utilize it for cyber espionage purposes. The tool’s appeal to APT groups lies in its wide range of features, and the option to modify it to suit their specific objectives, with the possibility to utilize the tool more with some further, more malicious modifications.
| Indicator | Type | Remarks |
| 78625E72074EEE611866AB04AE1935F2152ED695D3ADCD68061D10386170668B | SHA256 | MNS NH Contact.apk |
| 6C9A7E15D666FD61F62F1802D79782753BA25AAA76ECC86401658807F5D41503 | SHA256 | Posted out off.apk |
| 38[.]92[.]47[.]116 | IP address | Command Control |
| Tactics | Technique ID | Description |
| TA0030- Defense Evasion | T1406- Obfuscated Files or Information | Obfuscated code to increase chances of bypassing security measures. |
| TA0035-Collection | T1636. 003-Contact List | The threat actor fetches the contact list when compromised. |
| TA0035-Collection | T1636. 002-Call Log | The threat actor gets access to the victims’ call list. |
| TA0035-Collection | T1636. 004-SMS Messages | The threat can fetch ‘Sent’ and ‘received SMS’ once the device is compromised. |
| TA0032-Discovery | T1420- File and Directory Discovery | The threat actor can access the storage. |
An unknown espionage group based in Pakistan is utilizing a readily available Android RAT to target sensitive entities: while the tool may offer cost-effectiveness for their operations, their delivery techniques appear poor, resorting to dissemination over WhatsApp. These tactics suggest the emergence of a new APT group currently relying on accessible resources, however, as they establish a stronger foothold, they may eventually employ more sophisticated techniques.