



At CYFIRMA, we provide timely insights into prevalent threats and malicious tactics affecting organizations and individuals. Our research team recently identified a zip archive in the wild containing a malicious SFX executable that can infiltrate systems and execute malicious actions.
Subsequent analysis reveals similar instances associated with the campaign that exhibit consistent characteristics. These samples embed the malicious “uuid.exe” binary and decoy PDF file, suggesting a deliberate and targeted approach by the threat actors.
Moreover, our open-source intelligence (OSINT) investigations and analysis hint at collaboration with Russian cybercriminals for hosting C2 infrastructure targeting individuals in South Asia. This report delves into the details of the malware campaign, shedding light on the tactics and techniques involved.
When the malicious binary “New Oil License.exe” is executed, it drops a secondary payload named “uuid.exe”. This operates covertly in the background, while presenting the user with a decoy PDF document masquerading as legitimate regulatory documentation related to food item licenses in Delhi, India. This serves as a front for the malware’s underlying malicious activities, which include executing various commands and scripts and establishing connections with the Command and Control (C2) server. The exact initial attack vector remains unknown, but it is conceivable that the distribution mechanism may involve phishing or spear-phishing emails.
The commands are indicative of typical malware behaviour, such as collecting system information, concealing directories, duplicating potentially harmful files, running scripts, and gathering information about system volumes.
The CYFIRMA research team continuously investigates evolving threats, malware, and the Tactics, Techniques, and Procedures (TTPs) utilized by malicious actors. We engage in active surveillance of current threats, monitor persistent campaigns, evaluate their evolution, and remain alert to any new developments within this dynamic environment. Expanding upon these ongoing endeavors, we have uncovered the malicious file “New Oil License.exe” which upon execution drops another malicious payload “uuid.exe” on the system which runs in the background, executes various commands and also establishes a connection with the C2 server IP “176[.]56[.]237[.]126” at port 443, presenting the user with the decoy PDF as shown below:

It appears to be a legitimate document outlining requirements to obtain food-related licenses in Delhi, India.
To obtain the license, the applicant has to send the documentation to the following;“Addl. Commissioner (Food), Block, Vikas Bhawan, I.P.Estate, New Delhi-110 002”. The inclusion of specific references to the Delhi address potentially indicates a geographic focus or targeting strategy by the threat actor. The use of decoy documents like this is a common tactic employed by threat actors to evade suspicion and potentially delay detection.
Additionally, our research team has identified similar samples associated with the campaign, which have been observed exclusively since April 23rd.
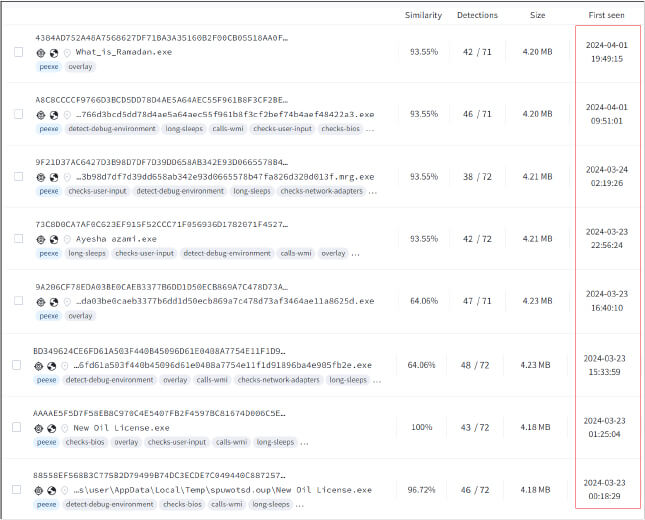
These samples also have similar PDF files as well as the malicious binary “uuid.exe” embedded within them. One PDF claims to be the CV of an individual named “Ayesha Azami” – listing a Delhi education – a second masquerades as a diet chart, and another presents the Ramadan schedule and timings for 2014, referencing Karachi, Pakistan. The mention of the year 2014 is strange, however, and the compilation time stamps of all binaries are also of the year 2013, though the binary is visible since April 2024 only.

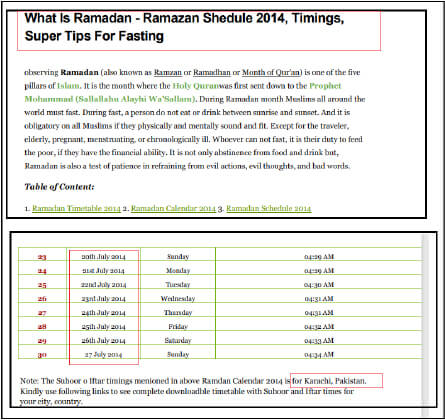
As per public community reporting, some of the researchers have attributed the campaign with “patchworks”, which Confucius APT has identified as pro-India threat groups.
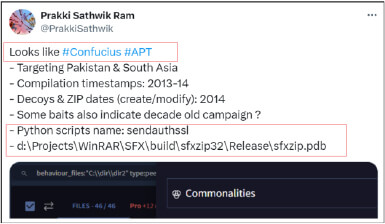
In another instance, another threat intel researcher “@h2jazi”, linked the samples with “Transparent Tribe”, a suspected Pakistan-based threat group.
The specific association cannot be properly confirmed, however, during our OSINT investigation, we were able to identify the email address linked with the C2 IP address “176[.]56[.]237[.]126” which acts as a server and could be used to deploy other payloads on the system, grant remote access, and commit data exfiltration.
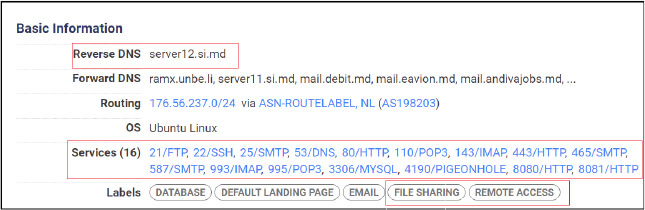
The IP address linked to the email “krasay4ik2211@tutanota[.]com” is connected to an individual of Russian origin.
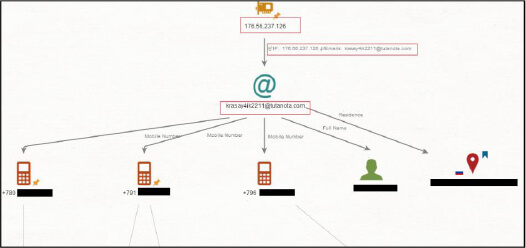
The investigation uncovered additional details, including associated phone numbers and addresses which were compromised in a data breach incident in 2022.
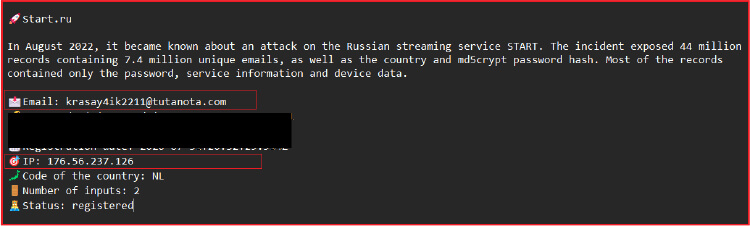
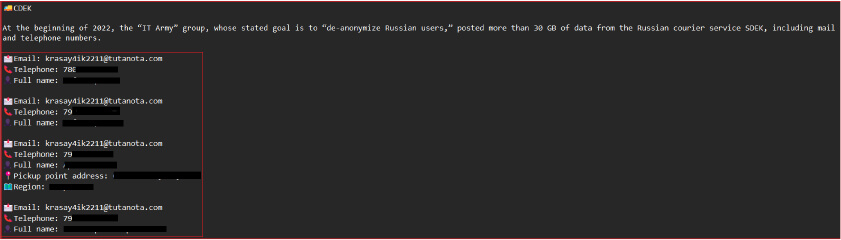
Our analysis indicates that the threat group behind this is targeting individuals in South Asia. It appears that they are utilizing the services of Russian cybercriminals to host their Command and Control (C2) server, potentially indicating, leveraging the expertise of different cybercrime communities for their malicious activities.
This acknowledgment underscores the dedication of the CYFIRMA Research team to proactively anticipate and thoroughly analyze emerging cyber threats, delivering invaluable insights to bolster the resilience of the cybersecurity landscape.
Basic Details:
MD5: 0D808D30525CF9BF822E2F695D8E1F83
SHA256: ec1981fa58e90a06efeb35537a45744756552b852eb298ca2b96929d21b0ca91
File Type: ZIP
MD5: 6CB2D35E9FE00765F83BCC771579D653
SHA256: 88558ef568b3c775b2d79499b74dc3ecde7c049440c8872573fc6622433eec17
File Type: Win32 EXE (SFX archive)
Our CYFIRMA research team identifies a zip archive in the wild containing WIN32 PE 32-bit executable with a GUI subsystem. The compile and debugger time stamp is old (December 2013); however, this looks suspicious. The sample file is an SFX archive executable file named “New Oil License.exe” that on execution drops multiple files on the system.
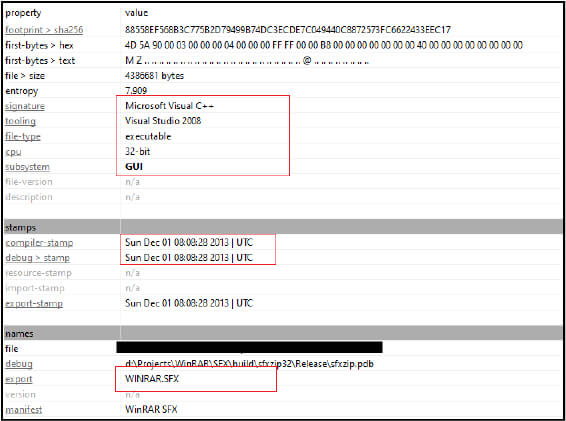
SFX is a little application that contains compressed files. It is the same as a .ZIP or .RAR archive, the only difference being that, when you execute, it will automatically extract the files. However, if you add some parameters, you can execute them after extraction or execute a shell command before extraction. So, this feature has been exploited many times by malware authors.
The overlay section of the binary “New Oil License.exe” contains a zip archive that we extracted that contains two files, one being the PDF file with name “NewOil_and_Gas_secures_license_extension.PDF” (0F30778FB27E4F8ADB00906F163385FE) and the other the binary “uuid.exe” (A225651AB45BC8ABEF10E1DC1C03E786).
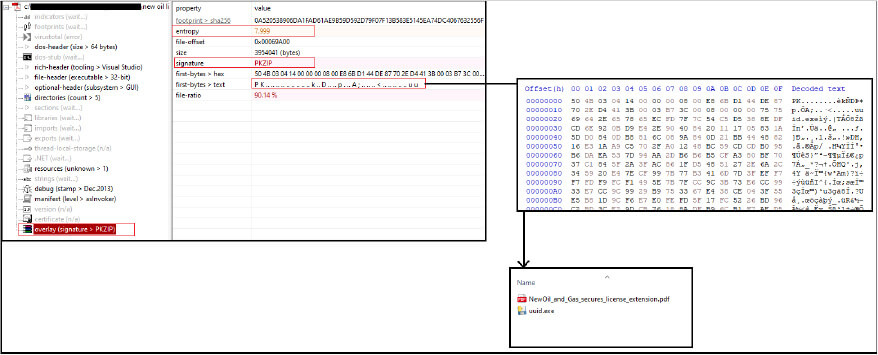
Upon execution, “New Oil License.exe”, drops “uuid.exe” into the “C:\Users\Username\AppData\Local\Temp” directory, and displays the PDF file as the decoy document, while executing the binary “uuid.exe” in the background which further runs several commands, creates directories, and drops, executes, and deletes .vbs file, and copies itself into the “C:\dir\dir2” directory.
Below is the process tree corresponding to the execution of the binary “New Oil License.exe” and the dropped binary “uuid.exe”. The malicious binary “uuid.exe” on execution, creates the process with the same name. Then it spawns a child process of the same name, where the packed malware has to run, unpack itself, and create new processes.
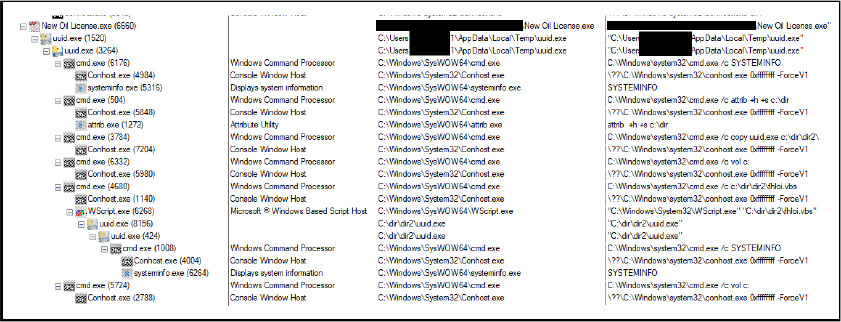
The executed commands perform a series of actions consistent with malware behavior, including gathering system information, hiding directories, copying potentially malicious files, executing scripts, and manipulating system volumes.
The cmd.exe from the system directory C:\Windows\system32\ is used to execute command-line operations, often a preferred method for malware to interact with the system. The commands are executed using the /c switch, indicating the provided string should be treated as a command.
The first command “C:\Windows\system32\cmd.exe /c SYSTEMINFO” aims to gather detailed system information, which could be leveraged by an attacker to tailor subsequent malicious actions or to profile the target system.
The command “C:\Windows\system32\cmd.exe /c attrib +h +s c:\dir” seeks to hide the directory specified (c:\dir) by setting the hidden (+h) and system (+s) attributes. This is a common tactic employed by malware to obfuscate its presence from users and security tools.
The command “C:\Windows\system32\cmd.exe /c copy uuid.exe c:\dir\dir2\” copies the file “uuid.exe” to the directory c:\dir\dir2\. The use of generic filenames like “uuid.exe” is typical of malware to disguise its malicious nature, potentially indicating the propagation of malware or additional payload delivery.
Further, the command “C:\Windows\system32\cmd.exe /c vol c:” retrieves volume information for the specified drive. Malware often collects this type of information to understand the target environment better or for encryption-related operations.
The command “C:\Windows\system32\cmd.exe /c c:\dir\dir2\fhloi.vbs” initiates the execution of a Visual Basic Script named “fhloi.vbs”, situated within the directory c:\dir\dir2. This .vbs file, which is dynamically generated, and its name varies with each instance of execution, is typically deployed by malware onto the system. Upon execution, the script fulfills its intended malicious function and is later deleted from the system, potentially to evade detection.
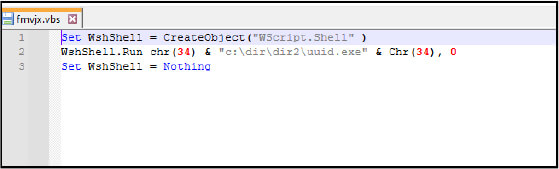
Following is the code for the .vbs script executed by the malware:
Set WshShell = CreateObject(“WScript.Shell” )
WshShell.Run chr(34) & “c:\dir\dir2\uuid.exe” & Chr(34), 0
Set WshShell = Nothing
The provided Visual Basic Script (VBS) code initiates a sequence of potentially malicious actions within a malware campaign. The script begins by creating a WScript.Shell object, enabling the execution of system commands. Subsequently, it invokes the execution of a file “uuid.exe” from a different location “C:\dir\dir2”. The parameter ‘0’ passed to the Run method implies that the executed command should be hidden from the user interface. Finally, the script releases system resources by setting the WshShell object to Nothing.
The VBS code demonstrates a common tactic employed by malware to execute arbitrary executables (in this case, “uuid.exe”). This instance of the binary “uuid.exe” execution also collects system and volume information of the system and later process terminates.
The main malicious binary (uuid.exe) later establishes the connection to the C2 server at IP address 176[.]56[.]237[.]126 on port 443. Connection employs TLS version 1.0 and lists various cipher suites supported by the client, which indicate the encryption methods used to secure data transmission between the compromised host and the C2 server.
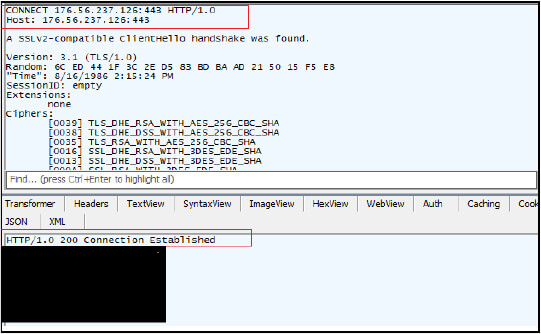
The malicious binary exhibits the behavior of a Trojan, collecting information of the system and establishing a connection with the C2 server possibly to download a more sophisticated payload, exfiltrate information and provide remote access.
At CYFIRMA, our commitment is to provide timely insights into prevalent threats and malicious tactics. Our recent identification of a malicious campaign underscores the multifaceted threat landscape. Our investigation into the malicious campaign surrounding the distribution of the “New Oil License.exe” malware emphasizes the complexity and sophistication of modern cyber threats. The campaign involves the deployment of a Trojan dropper, with the primary executable delivering a secondary payload named “uuid.exe” upon execution.
This secondary binary operates covertly in the background, executing a series of commands and scripts aimed at carrying out malicious activities. These actions include the gathering of detailed system information, the concealment of directories, and the copying of potentially harmful files. Furthermore, the use of decoy PDF documents – which appear to be legitimate regulatory documentation related to food item licenses – showcases the adeptness of threat actors in evading detection and extending the longevity of their malicious operations. Additionally, the campaign demonstrates collaboration with Russian cybercriminals for hosting Command and Control (C2) infrastructure, highlighting the complex web of global cybercrime networks.
As organizations and individuals navigate the increasingly complex threat landscape, it is imperative to remain vigilant and adopt proactive defense strategies informed by technical insights and analysis. Our ongoing research aims to provide timely intelligence and technical expertise to empower defenders in their efforts to safeguard against evolving cyber threats.
| Sr No. | Indicator | Type | Remarks |
| 1 | 0D808D30525CF9BF822E2F695D8E1F83 | MD5 File Hash | Zip File |
| 2 | 6CB2D35E9FE00765F83BCC771579D653 | MD5 File Hash | New Oil License.exe (SFX Archive) |
| 3 | 0F30778FB27E4F8ADB00906F163385FE | MD5 File Hash | NewOil_and_Gas_secures_license_extension.PDF |
| 4 | A225651AB45BC8ABEF10E1DC1C03E786 | MD5 File Hash | uuid.exe |
| 5 | 97b1e5ba1857d12d9f5f6e845622961a | MD5 File Hash | fmvjx.vbs |
| 6 | 176[.]56[.]237[.]126 | IP | C2 |
| 7 | 5c62c1c3856dc45060c50bf1f6bb6cd7 | MD5 File Hash | Other Similar Sample |
| 8 | 6eaab68919b851e402b5fb46b8b37b18 | MD5 File Hash | Other Similar Sample |
| 9 | e0541d63ac8093f1e472e63b96227844 | MD5 File Hash | Other Similar Sample |
| 10 | fd3c5ff86016fe626ad8a23befe38bec | MD5 File Hash | Other Similar Sample |
| 11 | 39bcff51ad0c4491bea74c100240c86c | MD5 File Hash | Other Similar Sample |
| 12 | dc001bad7f38cdb3bfe2f5ac08c5f3f5 | MD5 File Hash | Other Similar Sample |
| No. | Tactic | Technique |
| 1 | Initial Access (TA0001) | T1566: Phishing |
| T1566.001: Spear phishing Attachment | ||
| 2 | Execution (TA0002) | T1204: User Execution |
| T1059.005: Visual Basic | ||
| 4 | Defense Evasion (TA0005) | T1055: Process Injection |
| T1027: Obfuscated Files or Information | ||
| 5 | Discovery (TA0007) | T1082: System Information Discovery |
| 6 | Collection (TA0009) | T1005: Data from Local System |
| 7 | Exfiltration (TA0010) | T1041 – Exfiltration Over Command-and-Control Channel |
| T1071: Application Layer Protocol |