



AtomSilo is a new Ransomware recently seen in September 2021 during one of their attacks by exploiting a recently revealed vulnerability (CVE-2021-26084) in Atlassian’s Confluence Collaboration Software for initial access. The Ransomware used the double extortion method which is gaining popularity among ransomware threat actors where they first, exfiltrate the confidential information and as a second step encrypt the system files.
The attackers after gaining initial access to the above-specified software group server were installed a stealthier backdoor by using DLL side loading technique on legitimate third-party software. This backdoor can connect to its command-and-control server and is able to execute Windows shell commands through the Windows Management Interface (WMI). During lateral movement, the attackers trying to exploit more servers and install additional backdoors by compromising administrative accounts and at last drop AtomSilo Ransomware to the compromised server.
Risk Score: 8
Confidence Level: High
Suspected Malware: AtomSilo Malware.
Function: Ransomware.
Tactic Used: Double Extortion includes Data Exfiltration and Data Encryption.
Threat actor Associations: Unknown
Other Malware related to AtomSilo: Similarities in code with LockFile.
First Seen: September 2021
Target Industry: Multiple.
Target Countries: Multiple
In the initial analysis, it is a little bit difficult to understand the AtomSilo in terms of its relation to a particular ransomware or threat group as it copied different parts from different ransomware or threat groups as specified below and in Fig 1:
Atomsilo has similarities with the code of Lockfile which in-turn copied the ransom note page of Lockbit.
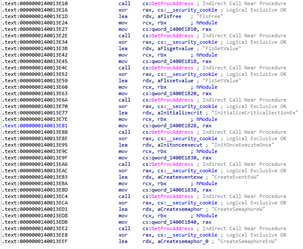
Fig 1:
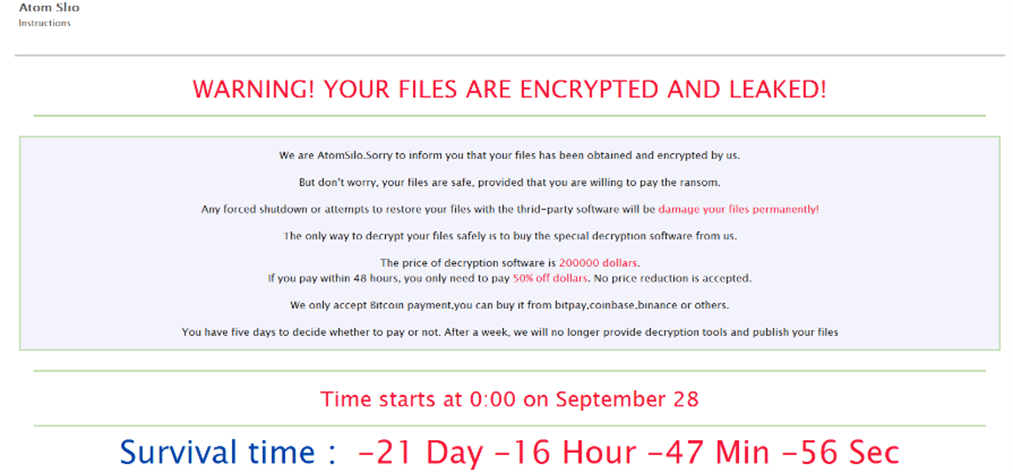
AtomSilo used the ransom notepage of Cerber version6. (Figure2)
AtomSilo copied the BlackMatter’s site contents. (Fig 3)
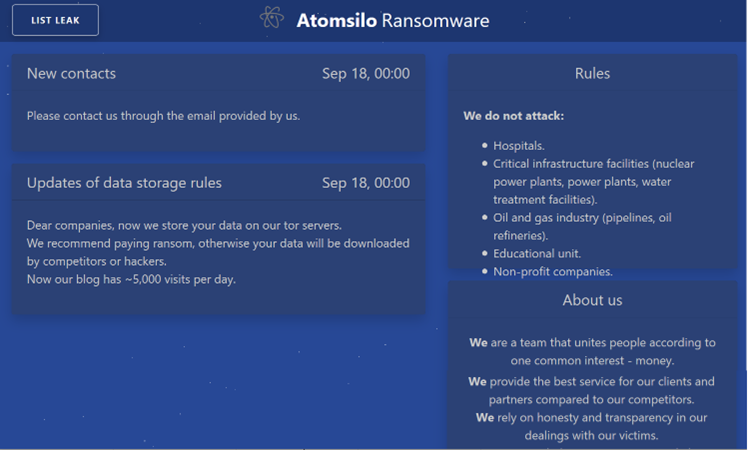
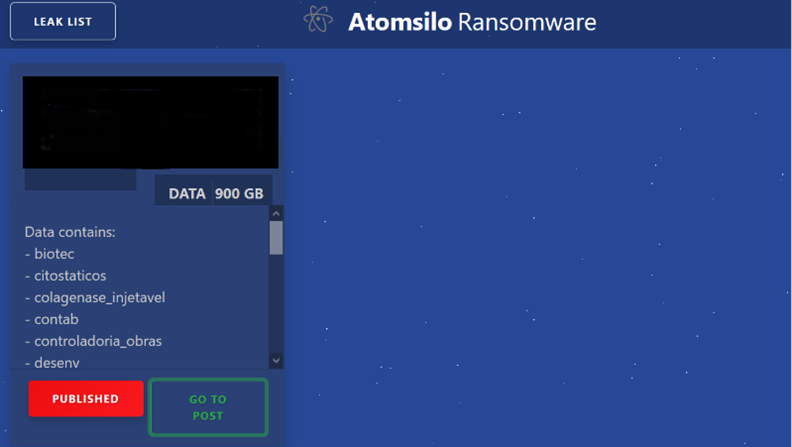
As per the information provided on their dark website, AtomSilo group followed the same policy of BlackMatter ransomware group to not attack the following industries/organizations:
Broadly we can say that the AtomSilo is up to some extent identical to LockFile specifically in terms of functionality as both have similarities in coding part but the AtomSilo has its own novel tactics and techniques like DLL side-loading technique.
Initial Access: The initial point of compromise in this attack was a vulnerability that was only public for about three weeks at the time. In particular, the ransomware operators were observed targeting a recently patched and actively exploited Confluence Server and Data Centre vulnerability to deploy their ransomware payloads.
Compromise and lateral movement: After gaining initial access through a Confluence server via an Object-Graph Navigation Language (OGNL) injection attack, this code injection on the Confluence server provided a backdoor, via which the attacker was able to drop and execute files for another, stealthy backdoor. The payload dropped for the second backdoor consisted of three files. One of them was a legitimate, signed executable from a third-party software provider that is vulnerable to an unsigned DLL sideload attack.
Defense Evasion: Atom Silo made significant efforts to evade detection before launching the ransomware, which included well-worn techniques used in new ways. Other than the backdoors themselves, the attackers used only native Windows tools and resources to move within the network until they deployed the ransomware.
Impact (Data Encryption, Exfiltration): The ransomware actors begin their own discovery and exfiltration efforts, checking the local volumes attached to an important server and then checking its history of Remote Desktop sessions. Using RDP, the ransomware gang then went hands-on-keyboard, dropping and executing the RClone utility to copy data off the server to a Dropbox account from several directories. The process was repeated on another server. Soon after the exfiltration was complete, the intruders connected to the domain controller and dropped their all-in-one attack executable.
The ransomware starts encrypting files in a similar fashion to LockFile, adding a .ATOMSILO extension to encrypted files. The ransomware dropped a ransom note formatted in HTML, with instructions on how to contact Atom Silo’s operators.
The AtomSilo malicious file is Windows-PE 64-bit executable as shown in Fig 4 and in Fig 5 we have mentioned different hash values for the malware and these values could also act as IOCs.
![]()
Fig. 4
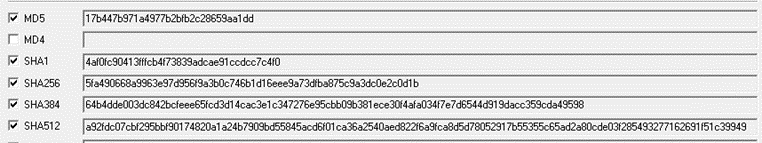
Fig. 5
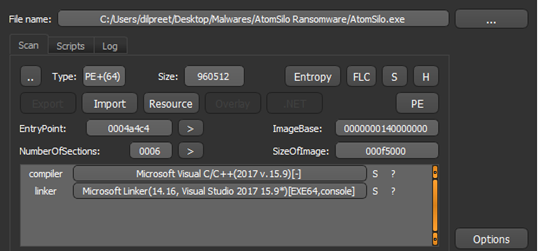
Fig 6
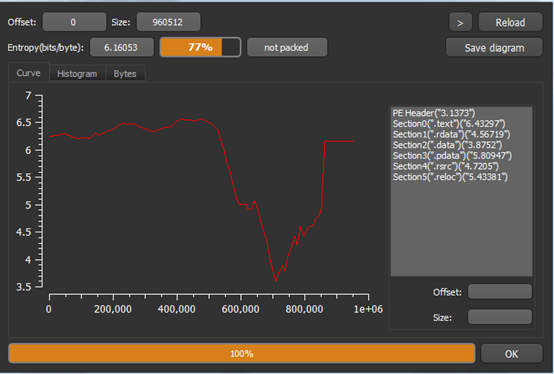
Fig 7
Fig 6 brief us that the compiler and linker for the malware sample are Microsoft Visual Studio with their version and Fig 8 shows the entropy of the malware and tells us that the malware is not packed.
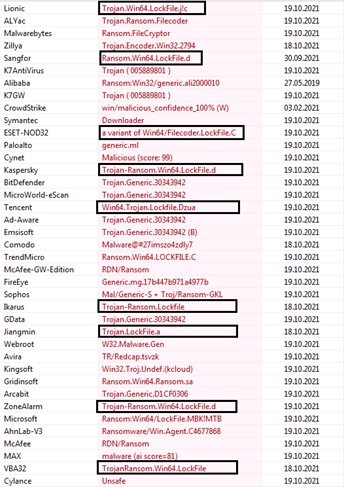
Fig 8
As shown in Fig 8 above, we have checked our sample file through various Anti-viruses Engines and what we observe has strengthened our initial analysis that most antivirus detects it as malicious in nature and ransomware. Further many anti-viruses also detect it as a variant of LockFile ransomware (boxed out in Fig 8) as we have mentioned in the beginning also that there are code similarities between AtomSilo and LockFile ransomware.
Fig 9 below confirms that our sample is PE-64bit executable having compile time of 24-Sep 2021 which is quite recent.
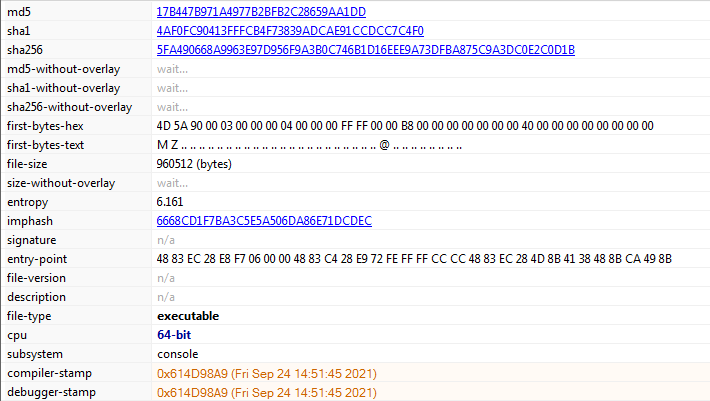
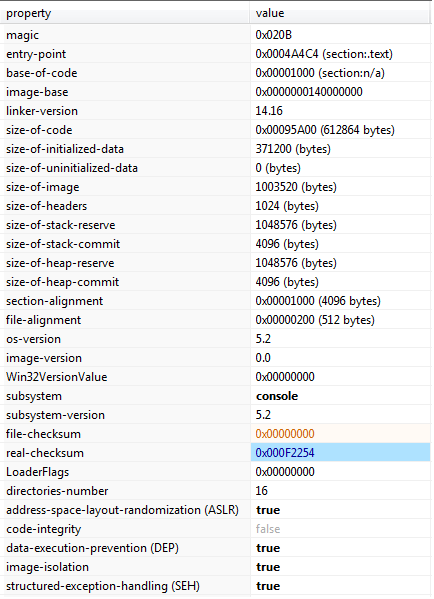
Fig 10
Fig 10 shown above indicates that the malware has a subsystem console i.e., it does not have any GUI. Further, it implements techniques like ASLR and DEP which help in preventing any other security program to predict its addresses and execute code in certain areas. It also makes it difficult for a malware researcher to analyze it. Such techniques are not added specifically but now are part of the compiler and other low-level programs like OS while we code and compile any program but definitely makes sense while we analyze or revere-engineer any executable whether it is a malicious program or a legitimate one.
Fig 11
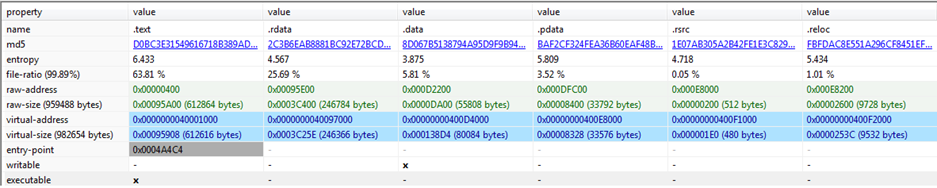
Fig 12
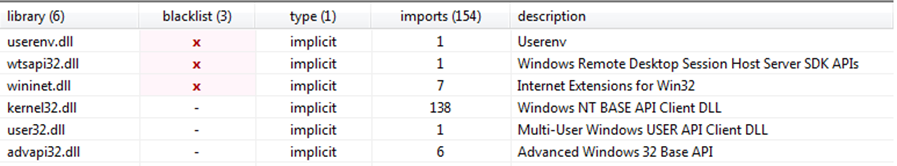
Fig 11 and Fig 12 above give us information about different sections present and the libraries imported by the malware. Both pieces of information are very important from point of view of analysis. .text section contains mainly the executable code of the malware. The imported libraries/DLLs are also important like Kernel32.dll used for low level or kernel level functioning while advapi32.dll presence indicates that the malware in some way must be accessing system and registry information or may try to manipulate it. Wininet.dll is also important as it is used to interact with FTP and HTTP protocols or broadly for internet/network connections which signify that malware may try to make outside connection. Wtsapi32.dll is important for making remote connections. Similarly, userenv.dll could be used to manipulate user profiles.
Fig 13.1
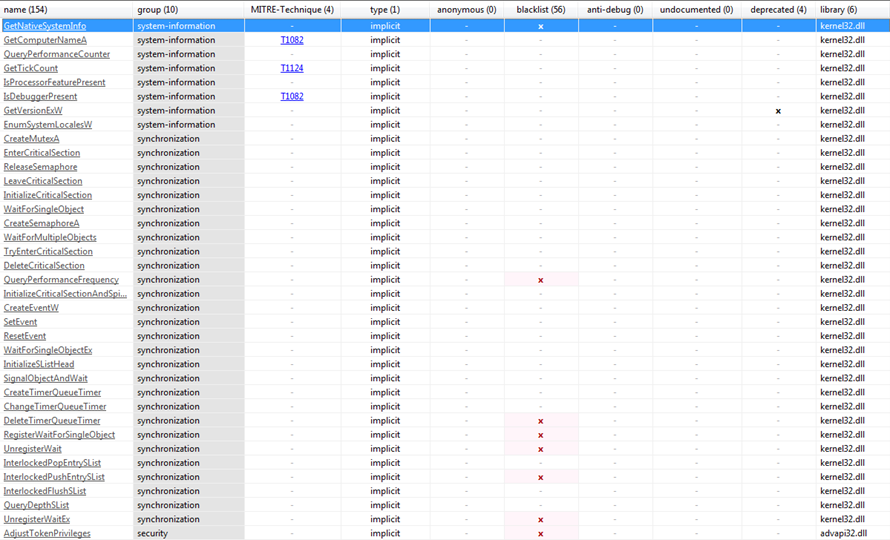
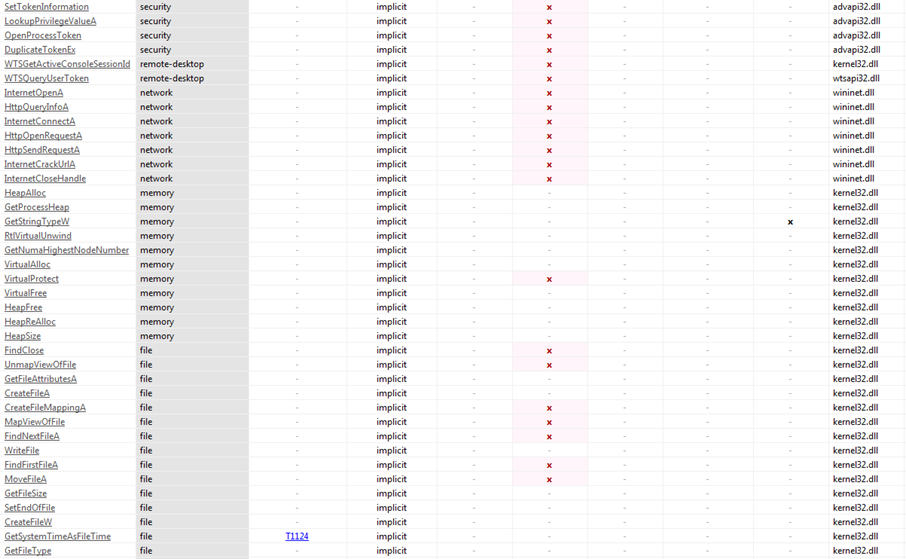
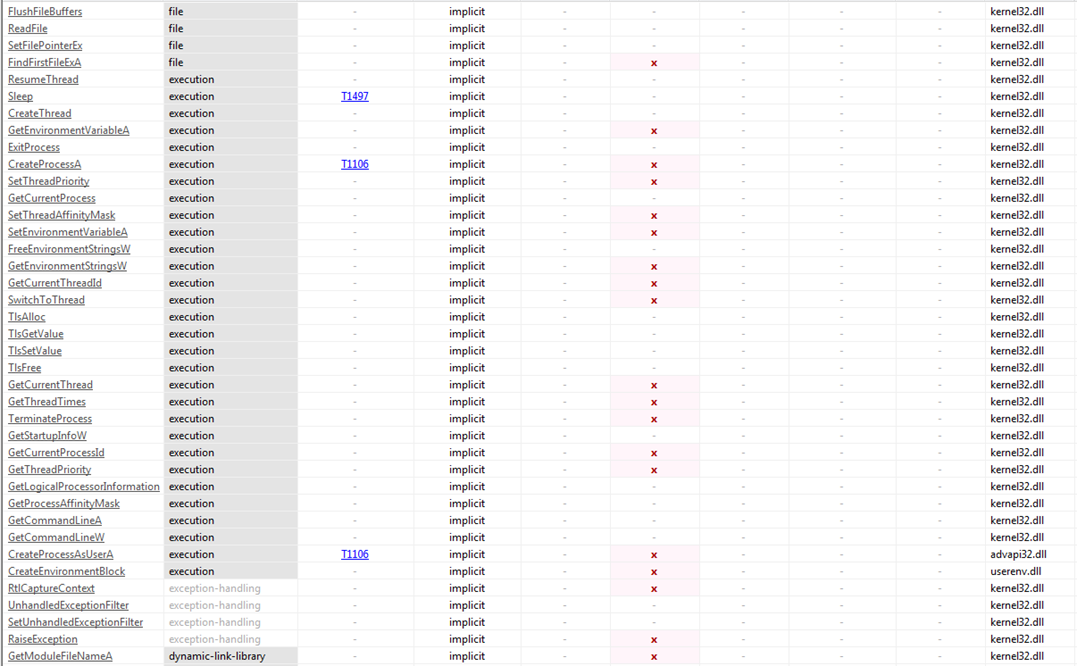
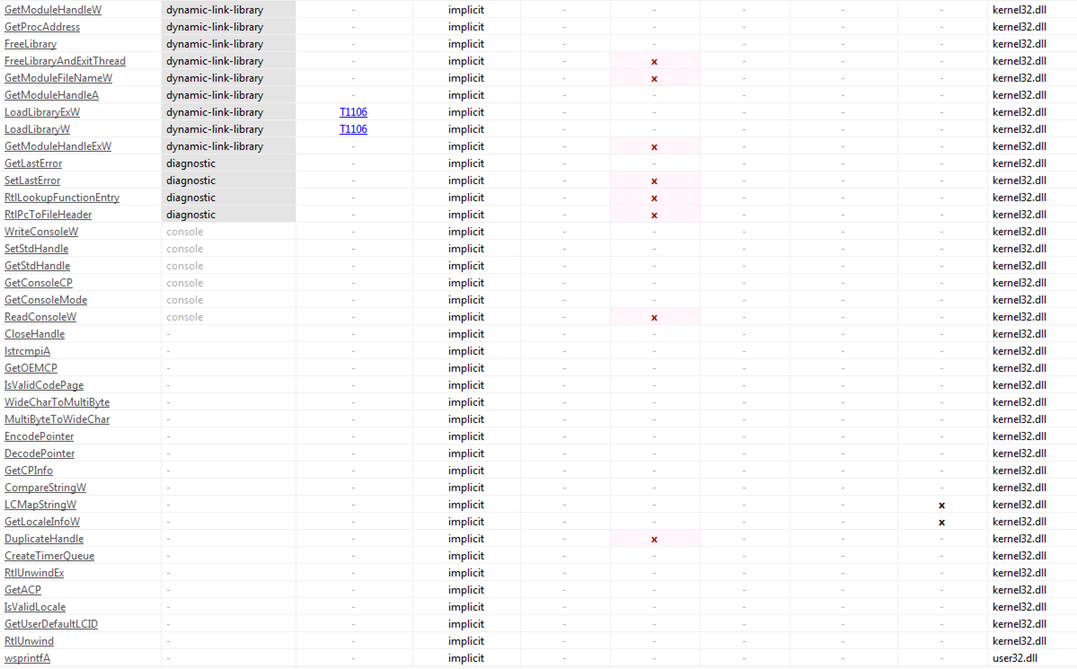
The figures above show various API functions part of different libraries. With analysis of all the above functions, we may say that the AtomSilo Ransomware must have the following capabilities:
Fig 14
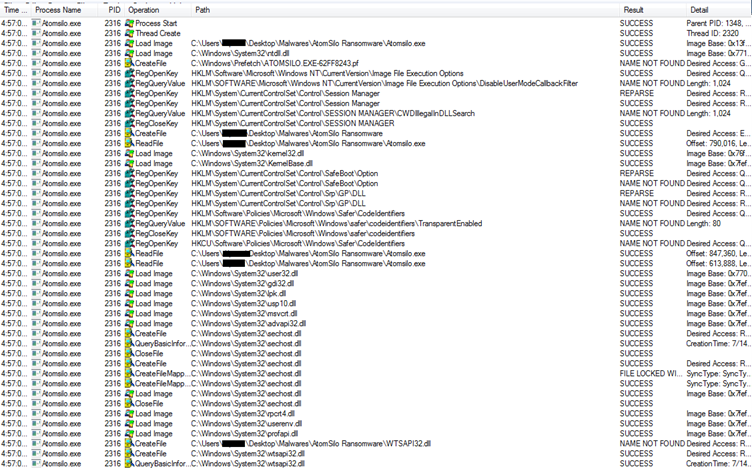
Fig 14 above shows the start of the execution of AtomSilo ransomware, creating threads, Loading images of various DLLs, and accessing many registry entries.
Fig 15 given below shows multiple threads running of AtomSilo.exe and native API usage.
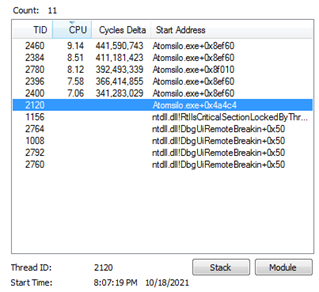
Fig 16
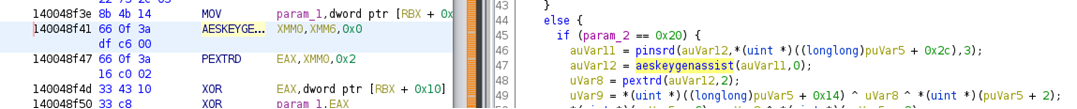
Fig 16 above and Fig 17 given below also give us sign about the cryptography/encryption algos used for encryption. AtomSilo use XOR and AES Encryption algorithms for encryption and it generates AES keys by using “aeskeygenassist” function as shown above in Figure 16.
Here in Fig 17 below, we have compared two files. The file on the right-hand side is the normal text file having some contents while on the left side is the hexdump of the same file after encrypted by the AtomSilo Ransomware. The main thing we observe here is that the ransomware can’t encrypt the whole contents of the file but encrypt some parts as highlighted in yellow rectangles in Figure17 and the other remaining part is a normal text readable as before. It is like it encrypts the first 16 bytes, then no change in the next 32 bits, and again encrypts the next 16 bits, and so on. At the end of the file (highlighted in green rectangle), is other data or encryption keys encrypted and append at the end of the file.
Fig 17
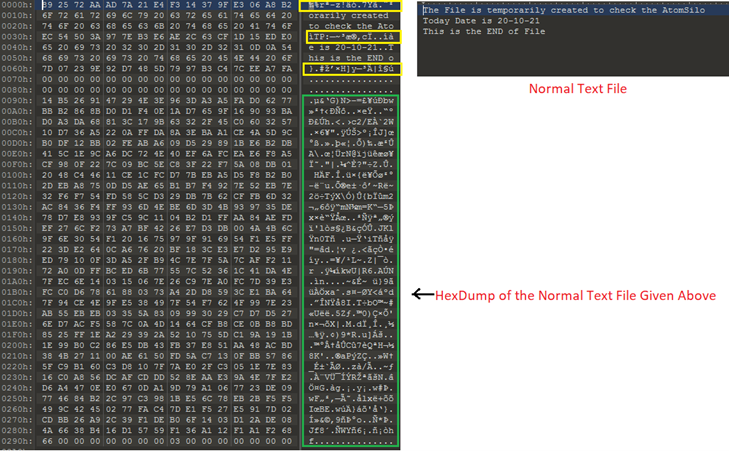
Fig 18
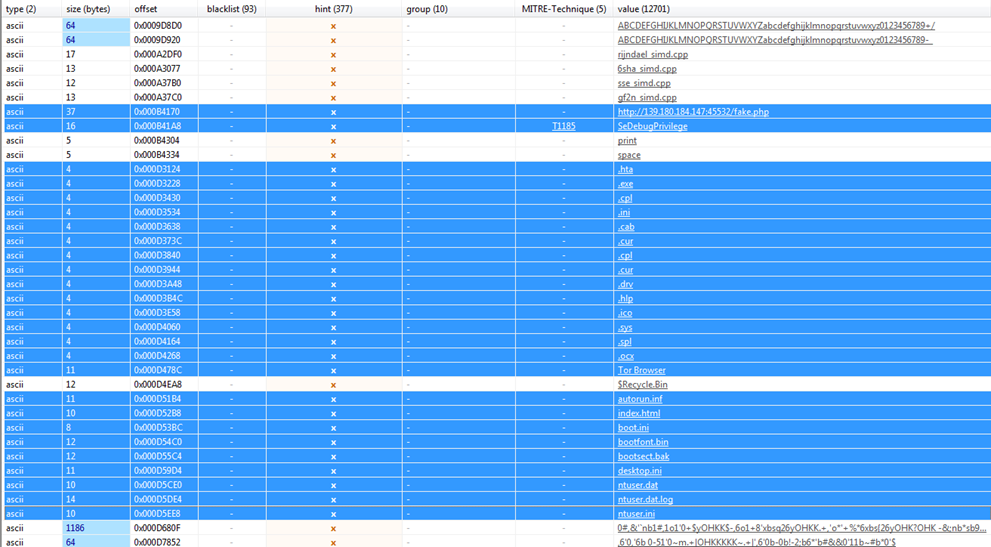
Fig 18 above provides us with two main IOCs for the AtomSilo ransomware that is a url: http://139.180.184.147:45532/fake.php and IP address: 139.180.184.147. Further, AtomSilo tries to access each file on the system and encrypt all files and folders except following:
autorun.inf, index.html, boot.ini, bootfont.bin, bootsect.bak, desktop.ini, ntuser.dat, ntuser.dat.log, ntuser.ini as highlighted in Figure18.
Fig 18 also highlighted following file types: .hta, .exe, .cpl, .ini, .cab, .cur, .cpl, .cur, .drv, .hlp, .ico, .sys, .spl, .ocx, the AtomSilo ransomware does not encrypt the files having these extensions.
Fig 19, Fig 20 below show the AtomSilo ransomware when it executes, enumerates each drive and folder, encrypts the files, and drops a ransom note as shown above in Figure2 in each folder with extension .hta. The format of the ransom note .hta file is README-FILE-{Name of the Computer}-{Random Number}.hta.
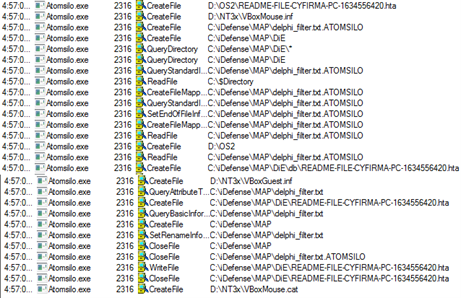
Fig 19

Fig 20
Further, each encrypted file ends with the extension .ATOMSILO as shown in Fig 20 above and Fig 21 below.

Fig 21
| # | Indicator | Type | Remarks |
| 1 | 17b447b971a4977b2bfb2c28659aa1dd | File Hash | MD5 |
| 2 | 5fa490668a9963e97d956f9a3b0c746b1d16eee9a73dfba875c9a3dc0e2c0d1b | File Hash | SHA256 |
| 3 | a92fdc07cbf295bbf90174820a1a24b7909bd55845acd6f01ca36a2540aed822f6a9fca8d5d78052917b55355c65ad
2a80cde03f285493277162691f51c39949 |
File Hash | SHA512 |
| 4 | http://139.180.184.147:45532/fake.php | URL | |
| 5 | 139.180.184.147 | IP Address |
| # | Tactic | Technique |
| 1 | Initial Access (TA0001) | Phishing |
| 2 | Execution (TA0002) | Malicious File |
| 3 | Persistence (TA0003) | Registry Keys |
| 4 | Defense Evasion (TA0005) | DLL Side Loading Technique |
| 5 | Discovery (TA0007) | Process Discovery |
| System Information Discovery | ||
| 6 | Lateral Movement (T1210) | Exploitation of Remote Services |
| 7 | Command and Control (TA0011) | Execute Windows Shell Commands |
| 8 | Impact (TA0040) | Data Encrypted |