



In this report, we discuss the recently observed XSSLite Stealer that is being discussed within multiple hacking communities. It was released as part of a malware development competition (XSSWare) hosted by the infamous Russian hacking community; XSS. The developer of the stealer has shared the source code of the project and hinted that he is moving on to another project. After the launch of XSSLite on a Russian forum, we have also seen the stealer being distributed on Chinese hacking communities. We will explore the capabilities of this infostealer along with more details on how these competitions urge financially motivated malware developers to create and distribute different types of malwares.
The CYFIRMA research team has observed a sharp rise in malware being distributed on a Russian hacking forum at no cost. The forum administrators had announced a malware development competition on 1st November 2023.

Since then, we have seen 20+ malware developers post under the topic, contending for the prize money. Amongst these entries, we have observed that a user has come up with 3 different malware – an infostealer, a crypto seed phrase checker and a Metamask wallet bruter. For the sake of this report, we will take a look at the infostealer, XSSLite.
XSSLite:
Sandbox Evasion and Anti-Debugging
The stealer evades sandbox analysis by looking for VMware and Hyper-V related infrastructure.

Additionally, the malware uses WMI to query device information to detect if its running on a VM. It also uses Windows memory manager to maintain a “write watch” on allocations for debugging and profiling purposes.



The web panel for XSSLite (which can be hosted on a private server) can be used to receive the stealer logs on an open port of the attacker’s choice.

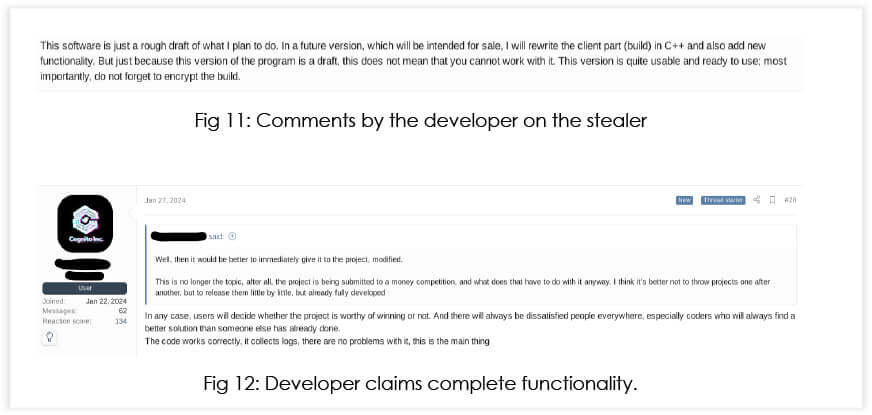
In the last week of January 2024, we noticed a post by a user on XSS; a Russian hacking forum. The post was created under the thread for “XSSWare competition”.

The developer claims that the project was initially meant to be a malware with infostealer and RAT capabilities. However, looking at the competition, the developer decided to rewrite the stealer in C++, while making the C# project accessible to everyone.
More malware, FOR FREE!
The malware development competition has motivated multiple contenders to create functional malware and post them at no cost on the forum. We have seen crypto brute force software, spyware, botnets and information stealers being disseminated for free.

The developer of XSSLite has shared a seed phrase checker for crypto wallets and a META wallet bruter. A seed phrase is a sequence of 12, 18 or 24 random words that provide the information required to recover (or in this case, takeover) a cryptocurrency wallet.

This can help attackers hijack cryptocurrency wallets of unsuspecting users. It supports BTC, LTC, DASH and DOGECOIN.
This report sheds light on the escalating risk landscape fuelled by underground malware development competitions — motivating malicious actors to create and share potent tools freely. A hefty prize pool shows just how much these administrators earn by running the cybercriminal forum. Competitions attract a larger audience, fostering increased participation and engagement within the forum. This comradeship can lead to more sustained and meaningful interactions, contributing to the overall health of the forum. With another month to go, we expect the number of malwares seen in the competition to experience a steep rise, likely resulting in increased campaigns by threat actors using those respective tools.
Strategic:
Management:
Tactical:
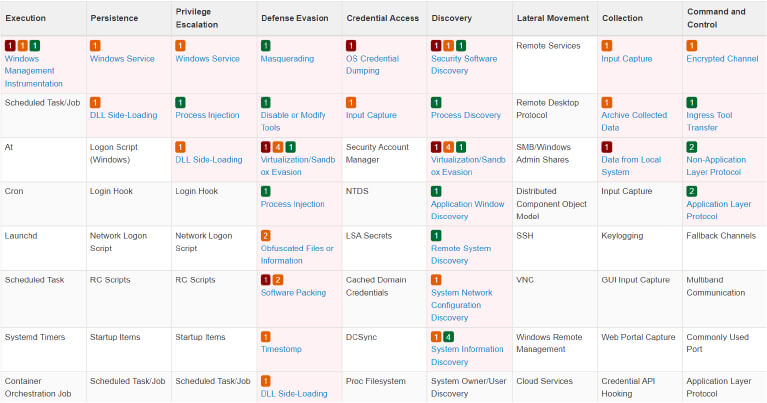
MITRE Mapping
| No | Indicator | Remarks |
|---|---|---|
| 1 | c6a7145f6756ab116b5811bce9d8af81 | MD5 |
| 2 | 6d43f8dae033320866f7c70198bfa85a37ae16aa | SHA1 |
| 3 | 15be0030e75fc12a27fa778f7fedaac338c1b26f9c238100fab649b1fa77dd34 | SHA256 |