Risk Score: 8.
Confidence Level: High.
Suspected Malware: Trojan.Win64.STEALTHVECTOR.SMZTID-B
MD5: b3f3de10b3c1c15491c53223f1b5979f
SHA256: 91aa05e3666c7e2443fc1f0f0142f1829f5ec51e289c95b10811531da50eb2b3
File Details: As shown in Figure1, following are the details related to the malware.
File Type: Windows PE-64 Executable
Subsystem: GUI
Compilation Time: Oct 2020.
Figure 1
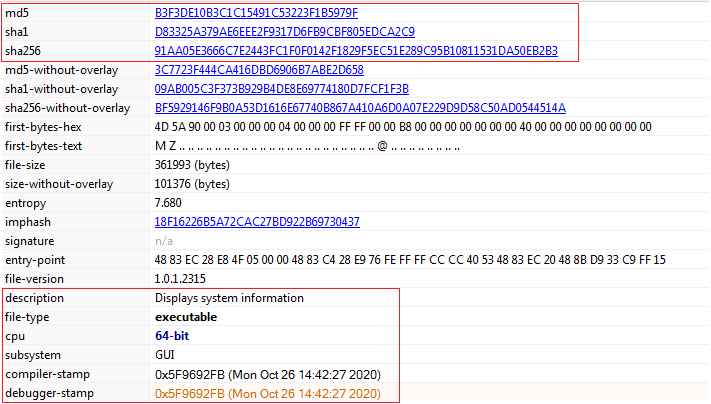
Figure 2
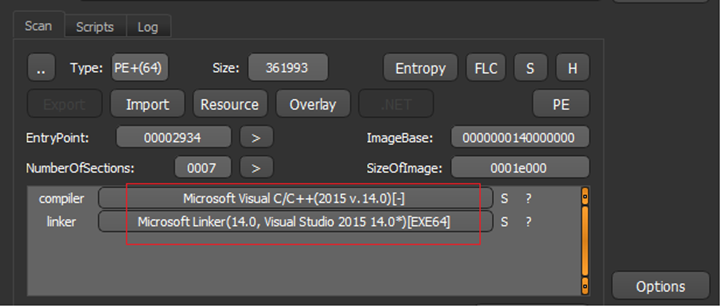
As shown in Figure1 and Figure2, the malicious sample is Visual C/C++ based. It is 64-bit Windows PE executable having GUI subsystem and compile stamp of Oct 2020. The corresponding hashes are also mentioned in Figure1 which may act as IOCs for the malware. Further high entropy indicates that malware may be packed.
Figure 3
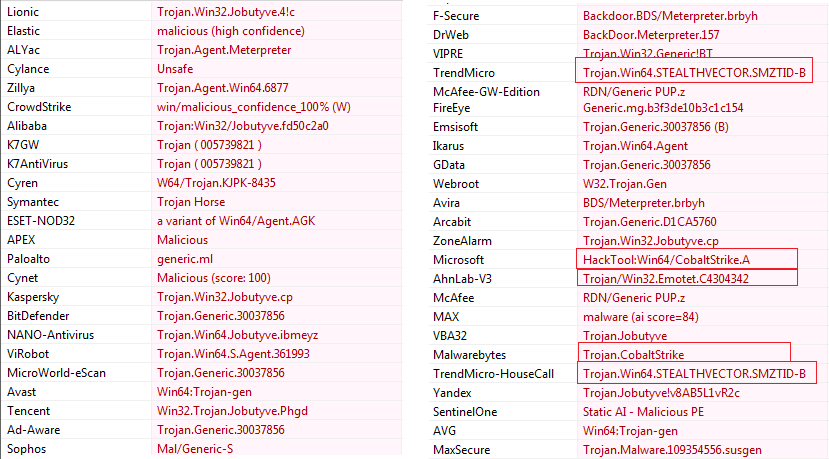
When we analyzed the file through different anti-virus engines, they detected the file as malicious and generally suggest that it has trojan capability. Some anti-viruses specifically categorized it related to STEALTHVECTOR.SMZTIB, CobaltStrike, Emotet indicates that this malicious file may be used by these malware campaigns also.
Figure4
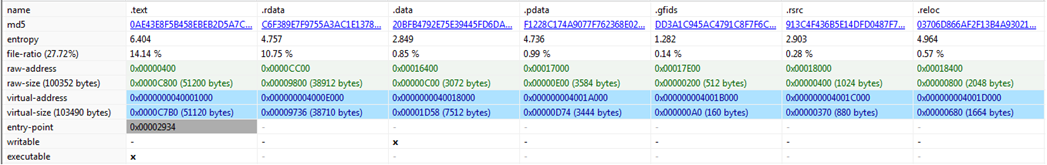
Figure 5
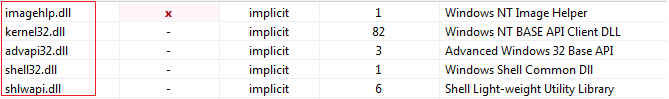
Figure4 above shows different sections present in the malware and looking quite normal and Figure5 shows the libraries imported by the malware. All are important and indicate the functionality possessed by the malware. kernel32.dll is a common library and its presence points towards the fact that the malware may access and manipulate memory, files, or hardware. advapi32.dll is used to access and manipulate registry entries, shell32.dll is used to open webpages, shlwapi.dll is also important and used to handle URLs. Furtherimagehlp.dll is also significant as it can be used by malware to access data contained in any PE file.
Figure6
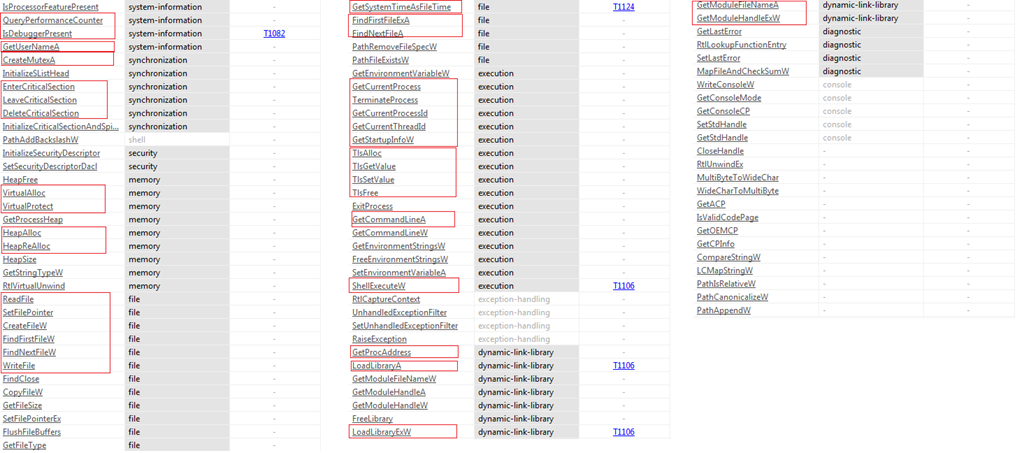
Figure7

Figure6 shows the various APIs used by the malware and Figure7 shows the strings extracted from the malware. The APIs and strings mentioned in Figure6 and Figure7 indicate the following capabilities possessed by the malware.
Figure8
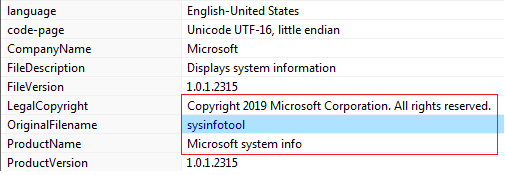
Figure9
![]()
Figure8 above shows the original name of the malware that is “sysinfotool” and related to Microsoft. Further, when we executed it, the highlighted part in Figure9 mentioned that the malware/application is of Microsoft which indicates that the malware disguised as a legitimate application to hide its presence and thwart detection from anti-malware solutions.
Figure10
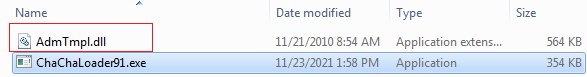
When we execute the malicious sample which has the name “ChaChaLoader.exe” as shown in Figure10. It drops the DLL AdmTmpl.dll in the same folder and we analyzed and explore it, it was found to be a valid system file and generally used to create new records/entries in the registry. So, the purpose here is either to hook this valid legitimate file by process injection or hollowing or simply used its functionality to create new records in the registry for malicious and persistence objectives.
Figure11
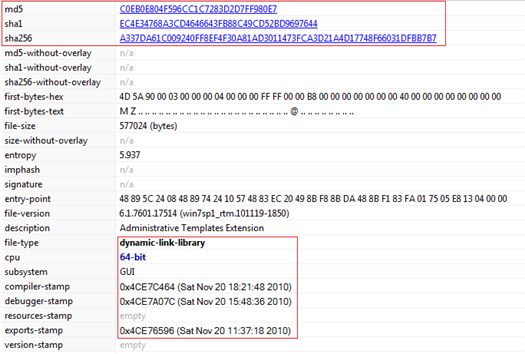
Figure12
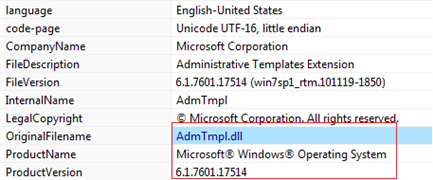
Figure11 and Figure12 show details about the suspicious “AdmTmpl.dll” file, It is a 64-bit DLL having compile time of Nov 2010 which matches with other valid system files on the system and is related to Microsoft.
Figure13
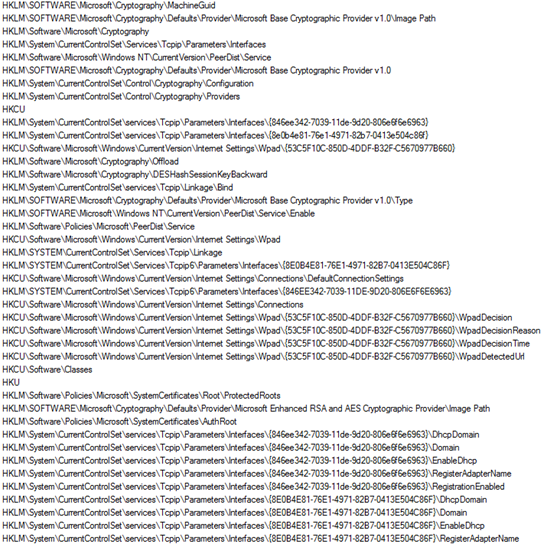
Figure13 above shows some of the registry entries the malware is accessing. Further Figure14 and Figure 15 shows all the different system, browser and other files accessed by the malware during execution.
Figure14
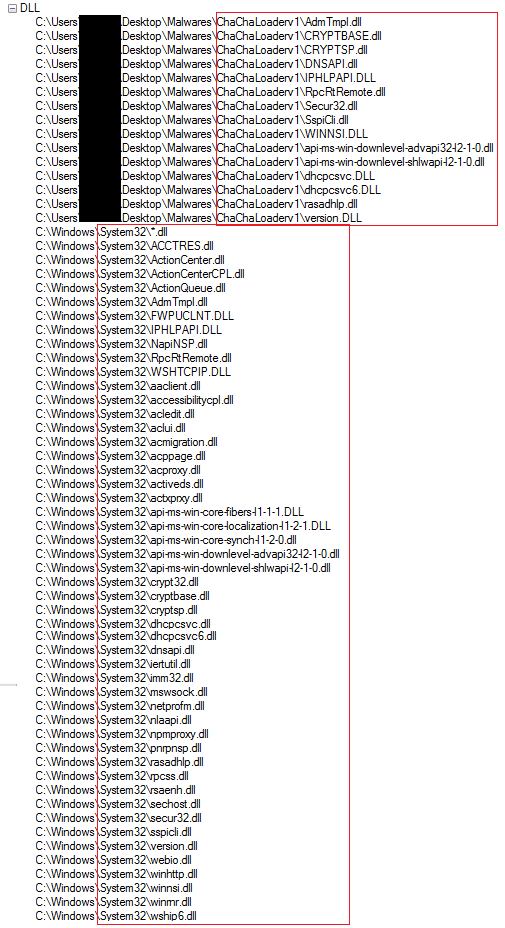
Figure15
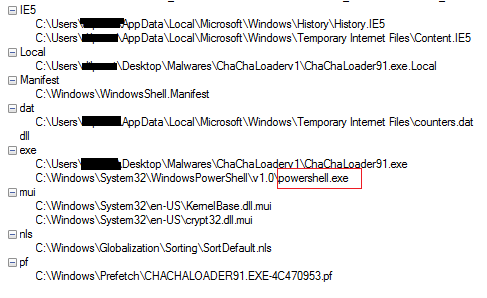
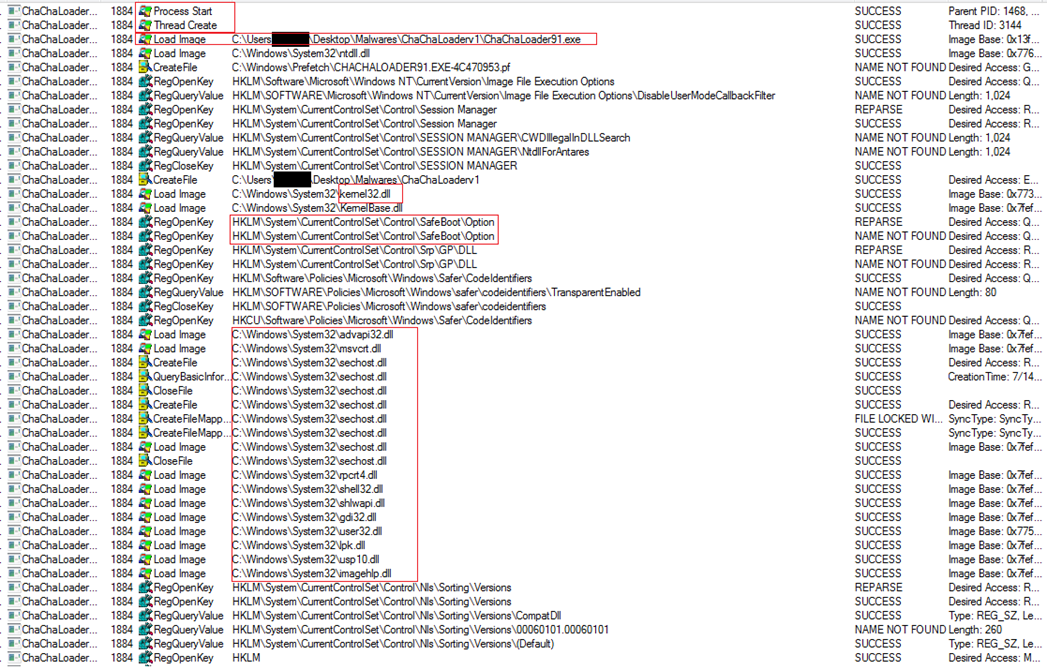
As shown in Figure14, the malware accesses many system DLLs from the folder where it resides but in actual those files are not there, so it indicates that the malware accessing the system32 folder where these files reside, copies them in hidden mode in the folder where it resides, use them or hook them for its own purpose and later on delete them. Figure14 also shows that how the malware accesses many files under the System32 folder. Further, see the highlighted part in Figure15 where it is accessing powershell.exe and could be used it to run any Powershell script. Figure16 shown below mentioned one IP and one Url accessed used by the malware. When we check online they appear to be clean, only one vendor signifies the IP to be linked to a malicious file. Figure17 below shows how the malware starts the process and creates a new thread of execution and accessing various registries, files and folders during execution and also Loading many system DLLs into memory.
Figure16

Figure17