


CYFIRMA’s research team discovered Lyrix Ransomware while monitoring underground forums as part of our Threat Discovery Process. Developed in Python and compiled with PyInstaller — allowing it to run as a standalone executable with all dependencies—Lyrix targets Windows systems using strong encryption and appends a unique file extension to encrypted files. Its advanced evasion techniques and persistence mechanisms make it challenging to detect and remove. This discovery underscores the need for proactive cybersecurity measures and a robust incident response strategy to safeguard data and reduce the risk of breaches.
| Target Technologies | Windows Operating System |
| Written In | Python |
| Encrypted file extension | Original file names appended with ‘.02dq34jROu’ extension |
| Observed First | 2025-04-20 |
Lyrix Ransomware targets Windows operating systems using advanced evasion and anti-analysis techniques to reduce the likelihood of detection. Its tactics include obfuscating malicious behavior, bypassing rule-based detection systems, employing strong encryption, issuing ransom demands, and threatening to leak stolen data on underground forums.
| Filename | Encryptor.exe |
| Size | 20.43 MB |
| Signed | Not signed |
| File Type | Win32 EXE |
| Timestamp | Sun Apr 20 09:04:34 2025 (UTC) |
| SHA 256 Hash | fcfa43ecb55ba6a46d8351257a491025022f85e9ae9d5e93d945073f612c877b |
MZ Header: Starts with the ASCII characters “MZ” (0x4D 0x5A), indicating it’s an executable file.
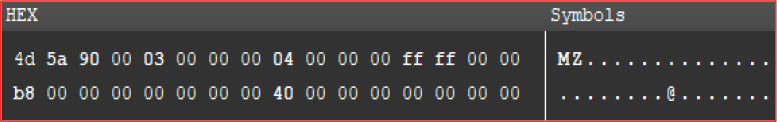
The Windows API function VirtualProtect is used as an anti-virtualization technique to detect whether the malware is running in a virtual environment.
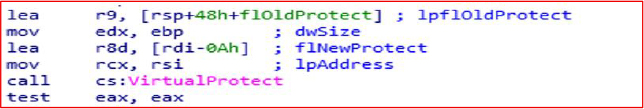
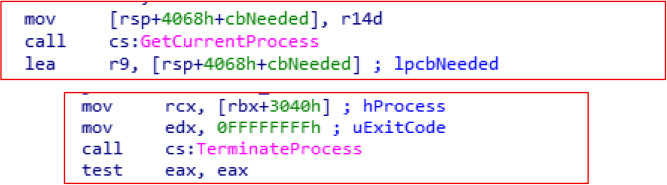
GetCurrentProcess and TerminateProcess functions for process manipulation. Attackers use this function to monitor and control the execution of their own processes, privilege escalation, Inject malicious code into other processes, and anti-malware tools.
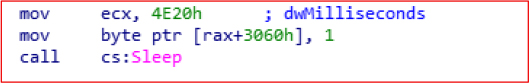
The Sleep function is used to evade sandbox analysis and delay the execution of malicious behavior.
GetStartupInfoW retrieves startup configuration details for the current process.
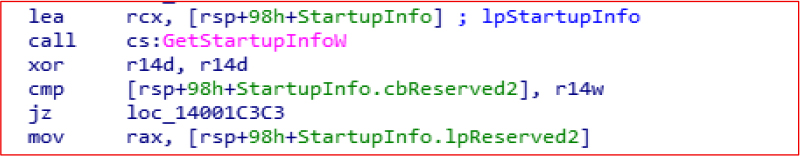
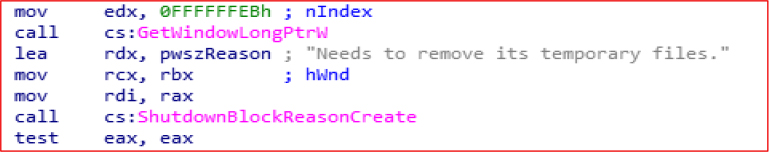
GetWindowLongPtrW is used to hide the taskbar, while ShutdownBlockReasonCreate prevents Windows from shutting down until a specific application explicitly allows it or clears the block.
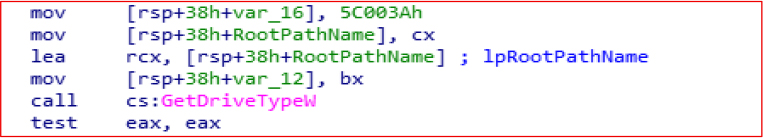
GetDriveTypeW is used to determine the type of drive (such as removable, fixed, CD-ROM, etc.)
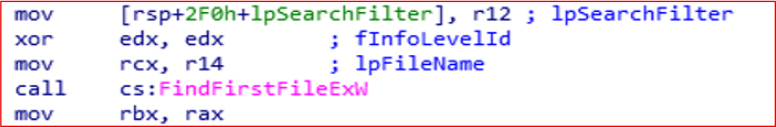
FindNextFileExW is used to search the files in the directory by ransomware to enumerate targets specific extensions like .docx, .pdf, .xls and .jpg, etc.
FileNextFilew is used to continue the files enumeration started by FindFirstFileExW
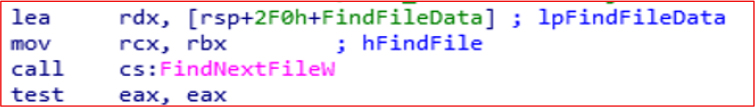
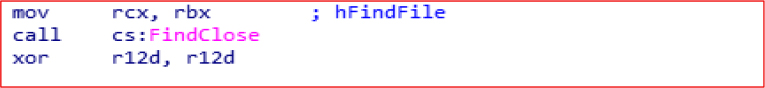
FileClose is used to release the handle from FindFirstFileExW.
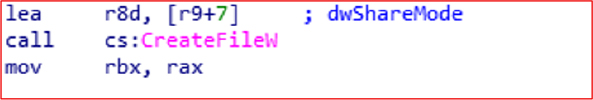
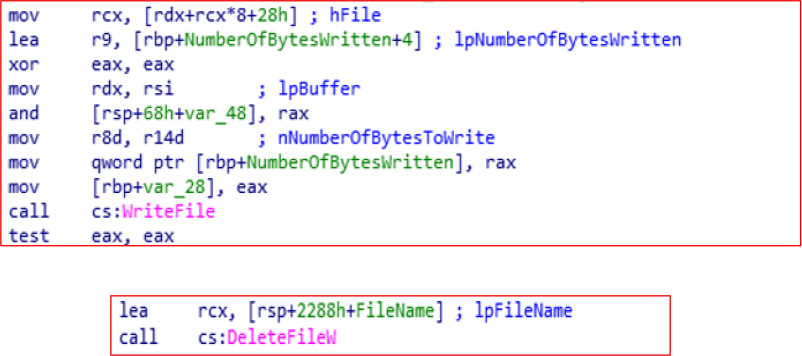
It uses CreateFileW to open user files, encrypt data, and writes it back using WriteFileW.
DeleteFileW is used to delete files from the filesystem. It’s often abused for destructive purposes.
Once it infects a system, it generates a secure 256-bit AES encryption key, which it then encrypts using a hardcoded RSA public key.
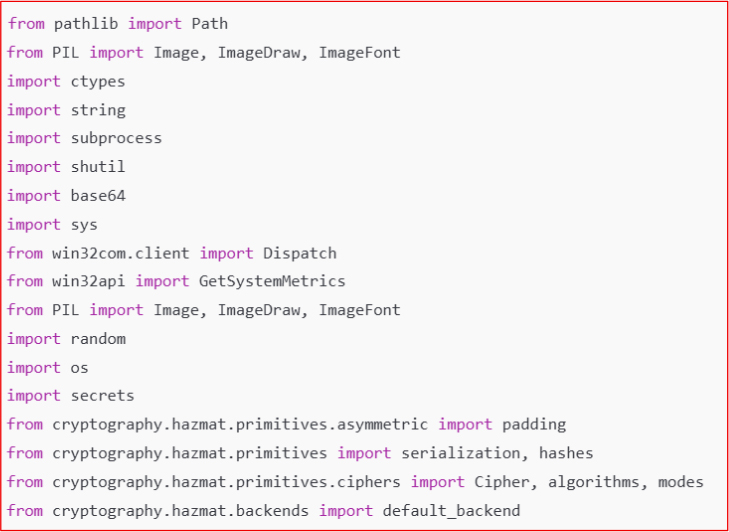
This encrypted AES key is saved in the “ProgramData” folder with the file name ‘02dq34jR0u.key’ to prevent the victim from decrypting files without the attacker’s private key.
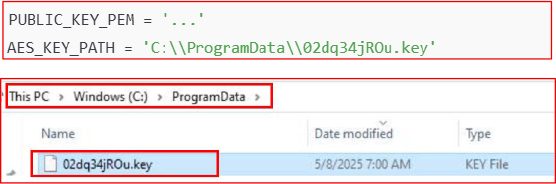
It scans specific user directories such as Download, Music, Documents, Desktop, Video, and Pictures for encrypting the data.
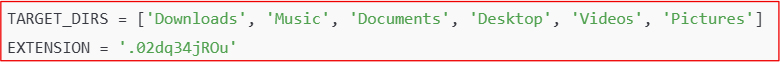
It encrypts files and appends ‘.02dq34jROu’ custom extensions to each file indicating a specific, possibly private ransomware.
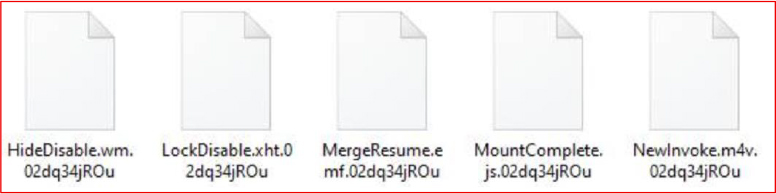
It skips ‘.exe’, ‘.dll’, and ‘.lnk’ files for encryption to avoid damaging system functionality.
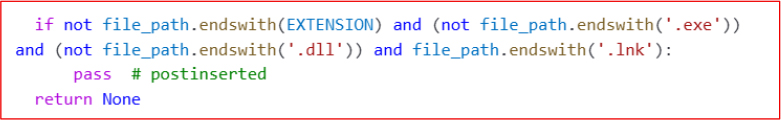
It also drops a ransom note file in every directory with the name “Readme.txt” and provides victims with instructions for file recovery and ransom payment.
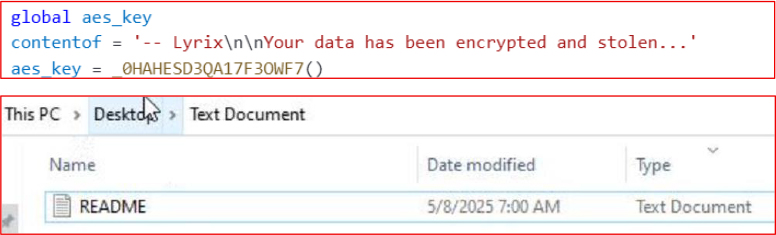
The ransom note says the victim’s data has been encrypted and stolen. The attackers claim the only way to recover the files is by contacting them. They warn against using third-party recovery tools, stating it could cause permanent damage. To prove they can decrypt files, they offer to decrypt two random files for free. They threaten to publicly release a portion of the stolen data if payment is not made. Contact information and a victim ID are also provided. The motive behind ransomware attacks is financial gain.
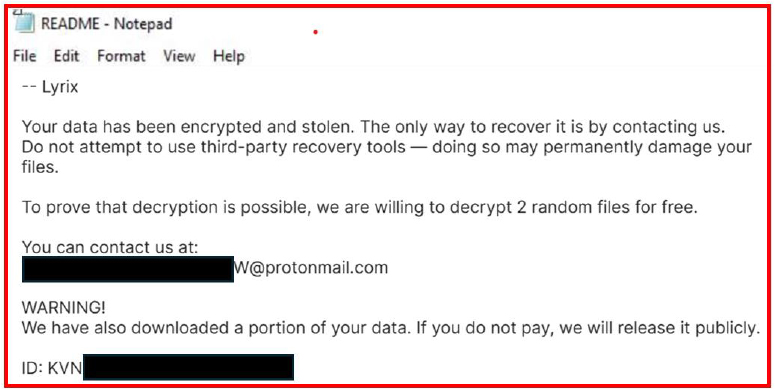
Additionally, the script executes system commands to delete all Volume Shadow Copies using vssadmin delete shadows /all /quiet, which removes any backup snapshots that Windows creates automatically, often used for system restore or file history recovery. Then it uses wmic shadowcopy delete as a backup method to ensure all shadow copies are removed, even if the first command fails. After that, it modifies the system’s boot configuration using bcdedit /set {default} bootstatuspolicy ignoreallfailures, which tells Windows to suppress startup failure messages and skip recovery prompts. Finally, it disables the Windows Recovery Environment (WinRE) using bcdedit /set {default} recoveryenabled no, completely blocking access to system recovery tools during boot. Together, these commands are intended to cripple the system’s built-in recovery features, forcing the user to either pay the ransom or lose access to their encrypted files permanently.
Lyrix Ransomware presents a serious cybersecurity threat, as individuals or organizations may unknowingly download malicious files, resulting in infections that could lead to data breaches, system compromise, or serve as a gateway for further attacks. Addressing this threat involves identifying the locations of these malicious files, analyzing the specific malware variants and their impacts, and promptly notifying relevant parties—such as internal security teams, external partners, and hosting providers—so the content can be swiftly removed.
To reduce the risk of these files being executed on systems, organizations should focus on ongoing user education about the dangers of downloading executables from untrusted sources. In addition, implementing robust endpoint protection solutions and maintaining up-to-date systems with the latest security patches are essential for effective defense.
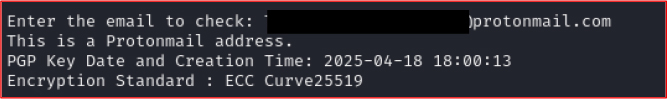
Additionally, during the investigation, we examined the ProtonMail address mentioned in the ransom note and found that the account was created in April 2025. This indicates that the threat actor has been active since at least that time.
| MITRE FRAMEWORK | ||
| Tactic | ID | Technique Name |
| Execution | T1059 | Command and Scripting Interpreter |
| T1129 | Shared Modules | |
| Persistence | T1542.003 | Pre-OS Boot: Bootkit |
| Privilege Escalation | T1574 | Hijack Execution Flow |
| T1055 | Process Injection | |
|
Defense Evasion |
T1014 | Rootkit |
| T1027.002 | Obfuscated Files or Information: Software Packing | |
| T1036 | Masquerading | |
| T1070.006 | Indicator Removal: Timestomp | |
| T1202 | Indirect Command Execution | |
| T1497 | Virtualization/Sandbox Evasion: System Checks | |
| T1564.001 | Hide Artifacts: Hidden Files and Directories | |
| T1564.003 | Hide Artifacts: Hidden Files and Directories | |
| Credential Access | T1003 | OS Credential Dumping |
| T1552.001 | Unsecured Credentials: Credentials In Files | |
|
Discovery |
T1057 | Process Discovery |
| T1082 | System Information Discovery | |
| T1083 | File and Directory Discovery | |
| T1518.001 | Software Discovery: Security Software Discovery | |
YARA Rules
rule Lyrix_Ransomware_Hashes
{
meta:
author = “Cyfirma Research”
description = “Detects presence of hardcoded indicators from Lyrix ransomware”
date = “2025-05-06”
strings:
$hash1 = “d298fb4197d65eabf1ef427c2eb737f1”
$hash2 = “fcfa43ecb55ba6a46d8351257a491025022f85e9ae9d5e93d945073f612c877b”
$hash3 = “72a8f2c6e5628f5e8e3c4dc7dcdb93cb”
$hash4 = “77706303f801496d82f83189beff412d83a362f017cadecc7a3e349a699ce458”
condition:
any of ($hash*)
}
Implementing the following mitigations recommended by CYFIRMA can help to block ransomware’s installation, prevent infiltration, and reduce the overall attack surface:
To reduce the risks associated with Lyrix and strengthen defenses against similar threats, the following recommendations are proposed:
Implementing the following mitigations can help block the ransomware’s installation.
Indicators of Compromise
Kindly refer to the IOCs section to exercise controls on your security systems.
| Indicators of Compromise | Remark |
| d298fb4197d65eabf1ef427c2eb737f1 | Block |
| fcfa43ecb55ba6a46d8351257a491025022f85e9ae9d5e93d945073f612c877b | Block |
| 72a8f2c6e5628f5e8e3c4dc7dcdb93cb | Block |
| 77706303f801496d82f83189beff412d83a362f017cadecc7a3e349a699ce458 | Block |