



CVE-2024-21894 unveils a critical vulnerability within Ivanti’s Connect Secure and Policy Secure gateways, posing a severe threat of remote code execution (RCE). This vulnerability extends its impact to a wide range of Ivanti’s products, potentially compromising security across approximately 391,480 exposed VPN gateways globally. Addressing this risk necessitates urgent attention from organizations, mandating the application of patches promptly issued by Ivanti. Additionally, bolstering network defenses with heightened security measures becomes imperative to thwart potential exploitation attempts effectively.
In this comprehensive analysis, CYFIRMA’s Research team has scrutinized CVE-2024-21894, a significant vulnerability sending ripples through cybersecurity spheres and posing a critical risk to global organizations. This vulnerability takes aim at Ivanti’s Connect Secure and Policy Secure gateways, pivotal elements in remote access security. Its exploitation allows for remote code execution (RCE), opening pathways for unauthorized access to sensitive networks by malicious actors. This emphasizes the urgent need for organizations to fortify their cybersecurity frameworks with proactive measures and informed threat intelligence to effectively counter evolving cyber threats.
Key Takeaways:
Acknowledgements:
CYFIRMA Research acknowledges the collaborative efforts of security researchers and the cybersecurity community in identifying and addressing the CVE-2024-21894 vulnerability.
Vulnerability Type: Unauthenticated Remote Code Execution (RCE)
CVE ID: CVE-2024-21894
CVSS Severity Score: 8.2 (High)
Application: Ivanti’s Connect Secure and Policy Secure gateways
Impact: Enables unauthenticated attackers to execute arbitrary code, posing a significant risk of remote code execution.
Severity: High
Affected Versions: Multiple versions of Ivanti’s Connect Secure and Policy Secure gateways are affected. Refer to vendor advisories for details. Check here
Patch Available: Yes
Mitigation: Organizations are strongly advised to apply the latest security updates and patches promptly to mitigate the risk of exploitation.
CVE-2024-21894 is a high-severity vulnerability in Ivanti Connect Secure and Policy Secure gateways, allowing attackers to execute arbitrary code, trigger denial of service conditions, and exploit heap overflow vulnerabilities. Attackers can exploit this vulnerability by sending specially crafted requests to the affected gateways, potentially compromising sensitive data, and disrupting business operations.
The exploitation of CVE-2024-21894 could result in severe consequences, including unauthorized access to sensitive information, disruption of business operations, financial losses, and damage to organizational reputation. Prompt mitigation is essential to safeguard against these risks.
CVE-2024-21894 affects specific versions of Ivanti Connect Secure and Policy Secure gateways. Organizations should refer to Ivanti’s security advisories for details on affected versions and apply the necessary security updates.
Check here.
Is there already an exploit tool to attack this vulnerability?
As of the latest available information, there is a known public exploit tool for CVE-2024-21894 targeting Ivanti’s Connect Secure and Policy Secure gateways.
Has this vulnerability already been used in an attack?
Regarding exploitation, while CVE-2024-21894 poses a critical risk, there is no specific information confirming active exploitation of this vulnerability at present. However, organizations should remain vigilant and prioritize applying patches promptly.
Are hackers discussing this vulnerability in the Deep/Dark Web?
CYFIRMA’s observations have identified some current discussions or potential exploitation of CVE-2024-21894 in the Deep/Dark Web.
What is the attack complexity level?
The attack complexity level for CVE-2024-21894 in Ivanti’s Connect Secure and Policy Secure gateways is assessed as LOW. While there are no known public exploit tools, the severity of the vulnerability underscores the urgency for mitigation efforts and the implementation of robust security measures.
Historical Trends and Known Exploits:
There are some known exploits or historical trends for CVE-2024-21894 in Ivanti’s products. Organizations must acknowledge the significant risks associated with this vulnerability and take proactive steps to apply updates and enhance security measures, ensuring protection against potential threats. Regular updates and proactive security measures are crucial to defend against evolving cyber threats.
Our analysis found that more than 391,480+ Ivanti’s Connect Secure and Policy Secure gateways are public, which can be vulnerable to CVE-2024-21894.
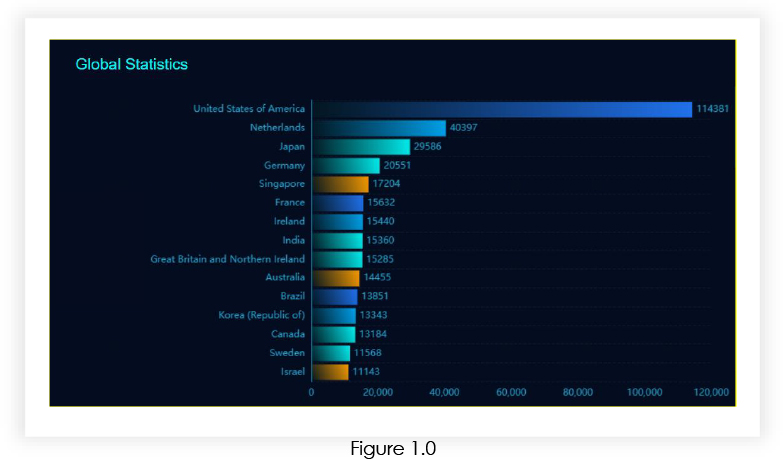
CVE-2024-21894 unveils a critical flaw in Ivanti’s Connect Secure and Policy Secure gateways, stemming from a boundary error within the IPSec component. This error occurs due to inadequate input validation mechanisms during the processing of IPSec packets.
Exploiting this vulnerability involves crafting specially tailored IPSec packets, designed to exploit the boundary error. Upon transmission to the vulnerable gateway, these packets trigger a heap-based buffer overflow within the IPSec component. This overflow condition allows the attacker to manipulate the memory space beyond its allocated boundaries, paving the way for arbitrary code execution.
Technically, the attacker gains control over the vulnerable system’s execution flow, enabling the execution of malicious code with the privileges of the affected software. This could lead to a range of detrimental outcomes, including unauthorized access to sensitive data, system manipulation, or disruption of network functionality.
Mitigating CVE-2024-21894 requires the prompt installation of updates provided by Ivanti. Organizations must apply patches from the vendor’s website to rectify the vulnerability and prevent exploitation. Failure to do so exposes systems to potential compromise and exploitation by threat actors.
The impacted software versions encompass Ivanti Connect Secure (formerly Pulse Connect Secure) versions 9.0R1 through 22.6R2.2 and Ivanti Policy Secure (formerly Pulse Policy Secure) versions 9.0R1 through 22.6. It is imperative for organizations relying on these versions to expedite patching efforts and bolster their network security posture against CVE-2024-21894.
Organizations utilizing Ivanti Connect Secure and Policy Secure gateways should promptly apply the security updates released by Ivanti to mitigate the risks associated with CVE-2024-21894. Additionally, implementing robust security measures, such as network segmentation and access controls, can help prevent the exploitation of this vulnerability. Regular security assessments and patch management practices are essential to ensure ongoing protection against emerging threats.
Target Geography:
Organizations worldwide relying on Ivanti’s Connect Secure and Policy Secure gateways are affected by CVE-2024-21894. The geographical impact spans regions such as North America, Europe, Asia, and beyond, where Ivanti’s products are extensively deployed. Regardless of location, organizations utilizing Ivanti’s gateways, particularly the affected versions, are susceptible to potential exploitation of this critical vulnerability.
Target Industry:
The vulnerability in Ivanti’s Connect Secure and Policy Secure gateways poses a threat across various industries, including healthcare, finance, government, telecommunications, and others relying on Ivanti’s products for secure remote access. Threat actors may target industries based on the perceived value of the data or services protected by Ivanti’s gateways. Industries handling sensitive information or those heavily dependent on secure remote access solutions may face heightened risks.
Target Technology:
CVE-2024-21894 specifically impacts Ivanti’s Connect Secure and Policy Secure gateways, crucial components of remote access infrastructure. Successful exploitation of this vulnerability may compromise sensitive networks and jeopardize interconnected systems, applications, and devices within the organization’s network. This underscores the potential ripple effect on an organization’s technological ecosystem, necessitating comprehensive mitigation strategies.
Understanding the global impact, cross-industry ramifications, and technological implications of CVE-2024-21894 is essential for organizations to assess their exposure accurately. Swift action through patching, proactive security measures, and vigilant monitoring is imperative to mitigate the risks associated with this critical vulnerability.
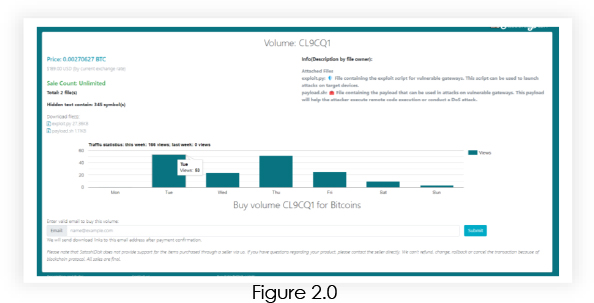
One GitHub user has been discovered selling an exploit for CVE-2024-21894 for the exchange of a few cryptos.
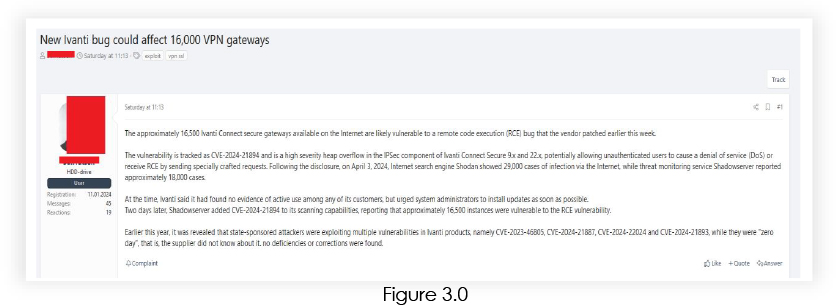
We have also found active discussion about the vulnerability on a dark web forum.
In conclusion, CVE-2024-21894 poses a critical threat to organizations worldwide relying on Ivanti’s Connect Secure and Policy Secure gateways. Immediate action through patching and enhanced security measures is essential to mitigate the risk of remote code execution. Collaboration, proactive monitoring, and prompt response guided by CYFIRMA’s insights are vital for defending against potential exploitation and safeguarding critical assets.