



Various hacktivist groups have targeted critical infrastructure, government agencies, and organizations in both Israel and Palestine. The attacks include Distributed Denial of Service (DDoS) attacks, defacement attacks and data breaches. As other countries take a stand on the war, the conflict has also spread beyond the immediate region, affecting several other countries. This report provides a concise overview of the escalating cyber conflict in the Middle East, stemming from recent geopolitical events. Notably, we engaged directly with threat actors from hacktivist groups to gain a deeper understanding of their motivations and forthcoming targets.
As cyber conflict advances, the concept of ‘hybrid warfare’ emerges, blending kinetic and non-kinetic (i.e. digital) operations on the modern battlefield. While traditionally cyber operations have been non-kinetic, a paradigm shift is looming, as cyber-attacks on vital infrastructure – like power plants – have the potential to yield tangible, kinetic outcomes that disrupt local operations, and can lead to extensive chaos and collateral damage. This type of event has precedent: the Russian invasion of Ukraine was proceeded by a synchronized disruption of Viasat nodes by a GRU-initiated DDoS attack, underlining the intertwined nature of modern warfare. With non-state actors increasingly engaging in disruptive operations, we are observing a similar pattern in the ongoing conflict between Israel and Gaza.
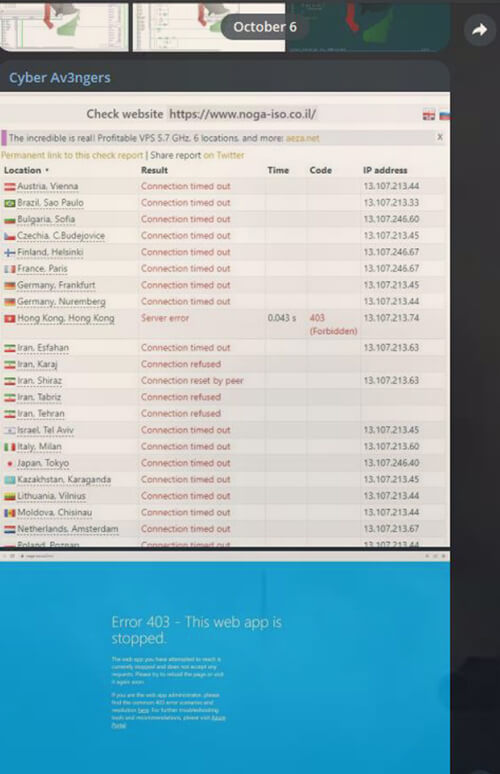
October 6, 2023: Cyber Av3ngers, a hacktivist group, claims responsibility for hacking the Noga Independent Systems Operator and launching Distributed Denial of Service (DDoS) attacks. This event marks the beginning of cyber activity related to the ongoing conflict.
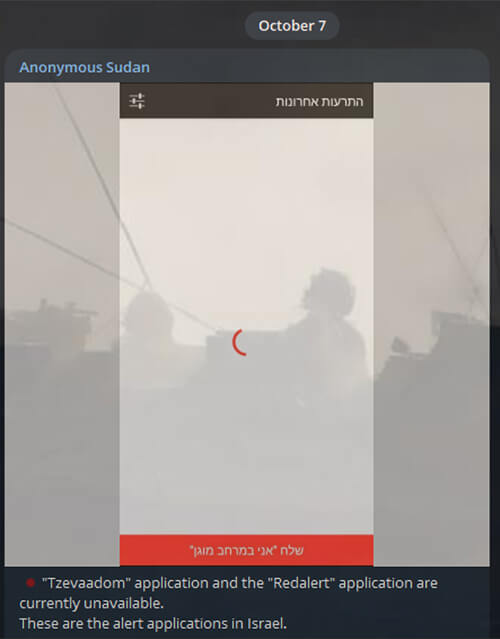
October 7, 2023: Within an hour of the 5000+ missile attack on Israel by Hamas, hacktivist group Anonymous Sudan (suspected to be of Russian origin) launched DDOS attacks on all the alert applications used for notifying citizens about incoming rockets.
October 8, 2023: The Israeli government’s official website becomes unreachable worldwide, and the Russian hacker group ‘Killnet’ claims responsibility for the attack. They accuse the Israeli government of supporting the “terrorist regime” in Ukraine and announce that they will target Israeli government systems.
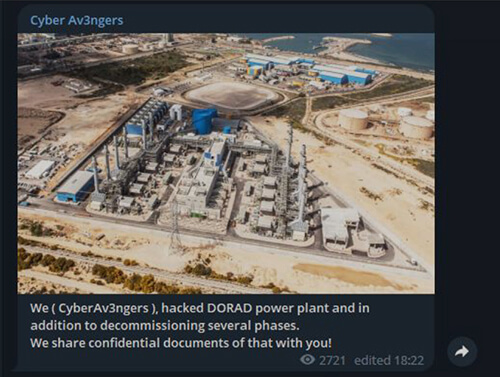
Anonymous Sudan attacks The Jerusalem Post’s website, causing it to go offline for over 2 days. Threat actor Ares Leaks announces that they are willing to purchase data related to Hamas military group. Furthermore, Cyber Aveng3rs claimed responsibility of hacking into the DORAD power plant, and ThreatSec claimed to have breached and shut down Alfanet, Palestine’s largest ISP provider.
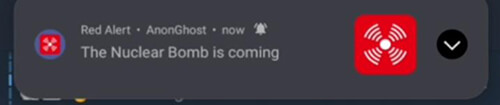
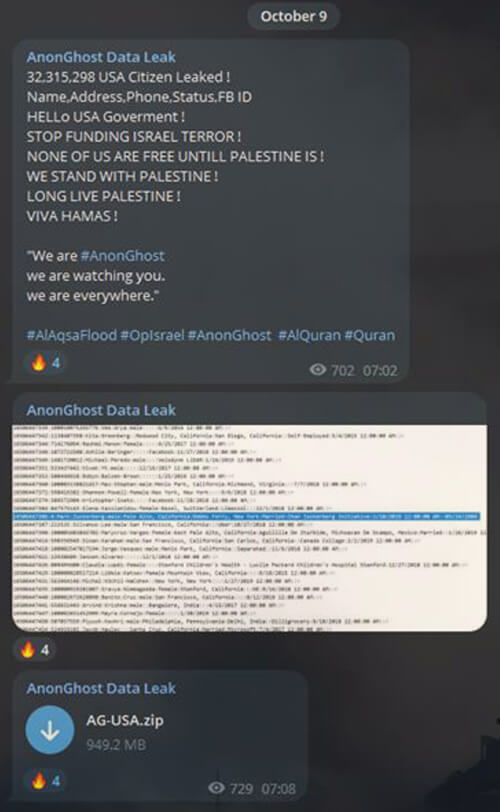
October 9, 2023: Hacktivist group; AnonGhost, compromised Israel’s Alert App and sent threatening notifications by exploiting an API vulnerability in the application. On the other hand, the cyber branch of the Israel Police’s Lahav 433 unit, along with the help of Binance, freezes cryptocurrency accounts belonging to Hamas.
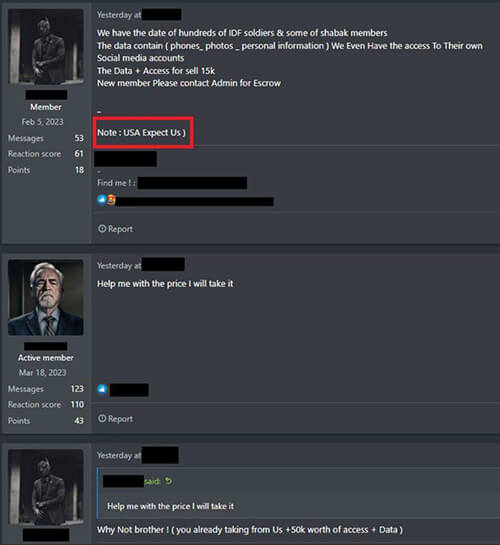
October 10, 2023: A threat actor known as “blackfield” announces on a Russian-speaking forum that they possess data belonging to hundreds of IDF soldiers and Shabak members, including phone numbers, photos, and personal information. They may use this data for further targeted attacks and disinformation campaigns. Blackfield also hints at targeting the US in the near future.
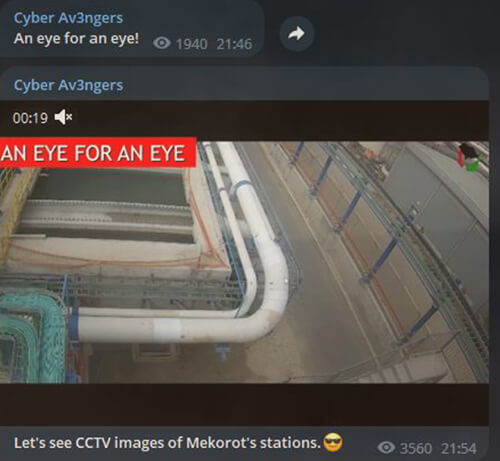
Various pro-Israel and pro-Hamas hacker groups engage in cyber activities, shutting down websites and targeting infrastructure. Cyber Av3ngers claims to have CCTV access to Mekorot, the national water company of Israel, adding to the list of attacks on industrial control systems.

October 11 – October 13, 2023: Individuals from various hacktivist groups are looking up stealer logs added to a central public lookup repository, trying to find valid credentials to compromise their targets of interest. Hacktivists are interested in servers belonging to:
And more.
October 14, 2023: Cyber Av3ngers announce that they have compromised ORPAK, a company that provides payment and management solutions for fuel, retail and fleet businesses in Israel. This was followed by them leaking CCTV footage and data from multiple gas stations and screenshots of the internal panels using SiteOmat.
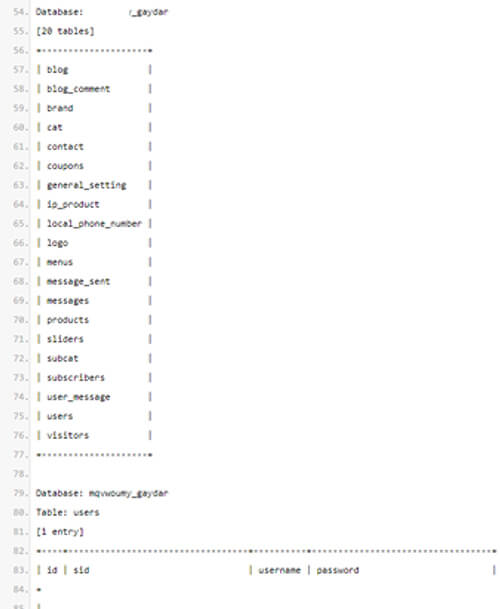
October 15, 2023: Hacktivist group AnonGhost Indonesia claims to leak the database of a dating and consolidation project for the Israeli LGBTQ community – “The Gaydar” on Pastebin.
October 16, 2023: Amidst other attacks, Israeli news websites “All Israel News” and “Abu Ali Express” were targeted by hacktivist “YourAnon T13x”. “All Israel News” took countermeasures that resulted in the web requests from the hacktivist group initially getting blocked, however, the threat actors were able to DDOS the website again.
October 17, 2023: Hacktivist group AnonGhost dumped a list of Israeli targets vulnerable to CVE-2023-29489 along with the exploit. The vulnerability affects cPanel application hosted commonly on websites. It’s a reflected cross-site scripting vulnerability that could be exploited without any authentication by an attacker.
In September 2022, Spid3r and the Kromsec group emerged as significant threats to Iran, both in the digital and real World. They initiated a cyber offensive as part of Anonymous’s #OpIran campaign, responding to the tragic death of Mahsa Amini, which has placed considerable pressure on the Tehran regime. Spid3r, who was previously involved in #OpRussia and contributed to the disruption of critical Russian targets, shared insights on the ongoing war. As stated by Spid3r in previous conversations, “Turning off unimportant targets for 5 minutes doesn’t work at all – But DDoS can be effective if you lock a specific target for a long time. For example, let’s say that the money transfer system of a country’s central bank does not work for 6 hours. Loss is unpredictable”.
(CYFIRMA): Can you please introduce yourself and describe your group’s political stance?
Spid3r (KromSec): Certainly. We are KromSec, a collective of hacktivists. Our primary goal is to respond to global events and issues through hacktivism. We operate from a democratic standpoint, firmly against censorship, corruption, human rights violations, and various modern-day problems. Our group comprises not only hackers but also activists, writers, and journalists. However, the individuals taking responsibility for our actions are mostly hacktivist hackers with a background linked to Anonymous.
We were notably involved in Anonymous’ OpRussia, and later, we initiated OpIran. Our activities have targeted various entities, including universities, ministries, national assemblies, and government systems.
After the protests in France, we hacked the French Ministry of Justice and disclosed information about hundreds of judges. Unfortunately, our Twitter account and Telegram channel were suspended due to the French Government’s intervention.
You can expect to see more data related to the French Ministry and an important government system on our channel soon. I hope that gives you a good overview. Feel free to ask further questions.
CYFIRMA: Can you confirm your group’s involvement in the recent cyber-attacks on the Palestinian Ministry of Foreign Affairs?
Spid3r (KromSec): Yes, it is true that we gained access to their systems. However, we want to clarify that our intentions are not malicious. We believe that wars are tragic and should not be supported by any side.
CYFIRMA: What do you plan to do with the data you obtained from the Palestinian Ministry of Foreign Affairs?
Spid3r (KromSec): Our intention is to reveal any hidden information when we deem it necessary.
CYFIRMA: Are you acting independently, or are you affiliated with a specific organization or group?
Spid3r (KromSec): We operate independently.
CYFIRMA: Do you believe that cyber-attacks will extend beyond the Middle East? There has been significant attention to this issue.
Spid3r (KromSec): In today’s world, technology connects everything, including people. Cyber actions can have a far-reaching impact, and we should consider their potential consequences.
CYFIRMA: Given the recent Hamas/Israel confrontation, have you heard of any major actions on the horizon?
Spid3r (KromSec): The media attention on unnecessary DDoS attacks makes us question their significance. We are monitoring an Israeli group closely, and they have targeted various .edu.ps websites. Pro-Palestinian Arab groups tend to focus on DDoS attacks on vulnerable systems or exploit WordPress vulnerabilities or compromised admin accounts. We respect genuine hacks, but DDoS attacks on insignificant sites for bragging rights are questionable.
CYFIRMA: How does your group view the ongoing conflict between Palestinian militant groups and Israel?
Spid3r (KromSec): We believe that the Israeli intelligence services are aware of such attacks, and it’s thought-provoking that they coincide with a time when Netanyahu lost support from his own people.
CYFIRMA: Do you have a longer-term strategy?
Spid3r (KromSec): It’s too early to discuss long-term strategies. The future is uncertain, and events can change rapidly.
CYFIRMA: What specific targets have you focused on in your cyber-attacks?
Spid3r (KromSec): We always act with consideration for potential consequences on civilians and critical infrastructure. We don’t aim to harm the public.
CYFIRMA: Are there specific demands or conditions your group aims to convey through these cyber-attacks?
Spid3r (KromSec): We usually communicate our intentions through attack messages or by contacting the affected system.
CYFIRMA: How do you see your cyber actions fitting into the overall strategy of your organization or group in this conflict?
Spid3r (KromSec): Our primary focus is on positive intentions. We targeted two universities, which are prominent in their country and have students who oppose the current regime. Our goal was to establish a constructive dialogue to prevent the potential misuse of information by others. Unfortunately, the situation didn’t unfold as we had hoped.
CYFIRMA: Would your group consider engaging in dialogue or negotiations with relevant parties in the Israel/Hamas conflict to address your concerns without resorting to cyber-attacks?
Spid3r (KromSec): I don’t anticipate such an offer. As for the pro-Israeli group we are monitoring, we are open to dialogue.
CYFIRMA: Please share your thoughts on the Hamas/Israel conflict and how you think things will unfold, both on the ground and in cyberspace.
Spid3r (KromSec): The ongoing conflict raises many questions. Is Hamas doing more harm to Israel or to their own people? The actions taken by Hamas, such as dismantling pipes from international organizations for infrastructure and repurposing them for missiles, are concerning. What Hamas is doing is unacceptable, and all Palestinians suffer as a result. However, this doesn’t justify Israel’s use of phosphorus gas. The lack of international response is baffling.
The situation is shrouded in uncertainty. We are closely watching the Middle East, where complex political games are played behind closed doors. True peace in this region will only be possible when both Israeli and Palestinian children can sleep without fear. We believe that diplomacy, rather than escalating tensions through attacks, is the key to a resolution.
CYFIRMA: You mentioned that your group has some background with Anonymous. Would you like to share a little about your technical capabilities?
Spid3r (KromSec): While I prefer not to boast about my technical skills, I can confirm that I am not new to the realm of cybersecurity. Anonymous has provided us with valuable knowledge and resources.
CYFIRMA: Is there a specific reason you don’t want to discuss your skills in detail?
Spid3r (KromSec): I believe that actions speak louder than words, and I prefer to let our activities demonstrate our skills.
The conversation below is an excerpt from that interview.
Note: The responses have been slightly modified to improve readability as English is not their native language
CYFIRMA: We appreciate you taking the time to speak with us. Can you begin by telling us more about your group, DeltaBoys, and your role within it?
DeltaBoys: We are a group with a long history, and I’m referred to as “anony.” We’ve had different names in the past, but our recent one is DeltaBoys. We’ve been involved in various activities, including penetrating government organizations and exposing their information.
CYFIRMA: What prompted you to communicate with the media directly?
DeltaBoys: We are regular people who are interested in communication, and we decided to engage with the media.
CYFIRMA: To introduce you properly, how would you describe your group’s activities? Are you primarily access brokers or involved in other aspects of cyber operations?
DeltaBoys: Our activities were initially in the underground, but about a year ago, we rebranded as DeltaBoys. We focus on infiltrating government organizations and disclosing their information.
CYFIRMA: What is your group’s technical specialty or passion?
DeltaBoys: For nearly 20 years, we have specialized in penetration and vulnerability detection.
CYFIRMA: Could you share the origins of your group and what motivates your activities?
DeltaBoys: Initially, our focus was on exposing corrupt governments, governmental crimes, and corruption. We were driven by a desire to hold such entities accountable and make people happier through our actions.
CYFIRMA: Have you collaborated with other groups or formed any affiliations?
DeltaBoys: Yes, we have worked with many groups, although our group’s rules often didn’t align with those of other groups. Unfortunately, most well-known groups have affiliations with security organizations, and it’s interesting to note that many hacker groups have been victims of our actions, resulting in us obtaining and publishing information about them.
CYFIRMA: Can you tell us about your targets, particularly those related to Israeli infrastructure, and the ideological reasons behind your attacks?
DeltaBoys: The Israeli government has a history of what we view as wrongdoing and violence worldwide. Hacking and disclosing their information are a way for us to express our opposition to their actions. We have targeted many cyber groups from Israel, identifying their information and operational weaknesses. Their primary goal often revolves around financial control.
CYFIRMA: We’ve noticed an increase in web defacement attacks. Can you explain this and whether it’s due to a growth in your group or an increase in sophistication?
DeltaBoys: We are a small but secretive group. Some of our intrusions occur after thorough information checks on organizations, while others involve sensitive information and documents. The public hacks typically relate to our older targets.
CYFIRMA: How do you select your targets, and what vulnerabilities or criteria attract your attention?
DeltaBoys: We have a vulnerability testing lab and identify the latest vulnerabilities. We also gather information on government targets through our members and by assessing the level of corruption. Occasionally, we hack ordinary people for fun, particularly if they are involved in fraud and corruption.
CYFIRMA: Can you share some insights into your tactics and techniques that set you apart from other threat actor groups?
DeltaBoys: Unfortunately, we cannot disclose our work method, but we achieve significant results by leveraging zero-day vulnerabilities and exploiting human error. A single human error in a security organization, for instance, can provide us with access to the entire organization, including emails, passwords, VPNs, files, virtual networks, and social networks.
CYFIRMA: Let’s discuss the financial aspect. How do you monetize your operations, and what brings in the most income for your group?
DeltaBoys: We primarily make money through the sale of data and government and financial access, generating approximately $40,000 per month. This income supports our operations, but it’s important to distinguish between hackers and financial fraudsters who steal from ordinary people’s databases. We are not thieves.
CYFIRMA: What are your near-term and long-term ambitions as a group?
DeltaBoys: Our goal is to create a powerful group that transcends sect, religion, and racism. We aim to fight against corrupt politics, racism, and corruption while defending human rights. We believe that all human beings have equal rights, and we strive to uphold them.
(CYFIRMA): Can you please introduce yourself? How would you describe yourself in terms of political stance?
fqw (Owner of GlorySec): My handle is fqw, I am the owner of GlorySec, and I would also like to state before we get started that most, if not all hacktivist groups have no idea about the current geopolitics other than what they hear from the media/press. We aren’t black hats like GhostSec or SiegedSec; we actually stand up for what’s right, we attack everybody with a particular reason.
CYFIRMA: Are you acting independently, or are you affiliated with a specific organization or group?
fqw: GlorySec is a subgroup of a particular darknet cult that we can’t go into any further detail about. However, yes – GlorySec is affiliated with another group.
CYFIRMA: Ok, thanks. Can you confirm your involvement in the recent cyber-attacks on the Palestinian territory?
fqw: We are currently prioritizing our involvement within the Israel-Palestine conflict, but we can’t go into operational details.
CYFIRMA: How does your group view the ongoing conflict between Palestinian militant groups and Israel?
fqw: GlorySec members have left, and the owner has left as well to start a new operation. We have an entirely new team with the same political agenda. We will be more radical towards terrorists and extremists and those who threaten humanity without justification. We support Israel in the Israeli-Palestinian conflict and Azerbaijan in the Azerbaijan-Armenia war. We have worked on #OPArmenia and #OPPalestine and taken over websites. We have attacked educational institutions in response to attacks on the innocent.
CYFIRMA: So far, we have seen several cyber groups becoming involved in the recent Hamas/Israel confrontation. Are you aware of any major actions that may take place?
fqw: We feel that both countries will be severely attacked, but we can’t provide operational details or those of our affiliates.
CYFIRMA: I understand you can’t go into too much operational detail about what you are planning, but can you give us an idea of your group’s capabilities or what you have previously done?
fqw: Our new team is very advanced, with skills ranging from reverse engineering to network penetration. However, we primarily focus on web penetration testing.
CYFIRMA: Is what you are planning solely a response to recent events in the Gaza Strip, or does it represent a longer-term strategy?
fqw: It’s most likely a longer-term strategy, but our first motivation was the Gaza Strip attacks.
CYFIRMA: Do you think cyber-attacks will extend beyond the Middle East?
fqw: It depends on the group and the country.
CYFIRMA: Have you considered the potential consequences of your actions on civilians or critical infrastructure in the affected regions?
fqw: Yes, we have, but we always have a purpose, so we don’t take it into critical consideration.
CYFIRMA: Are there any specific demands or conditions that your group is trying to convey through these cyber-attacks?
fqw: It depends on the issue. For example, in the Palestine situation, we are trying to push Palestine out of Israel, although they likely won’t listen. Many hacktivist groups are attacking both sides.
CYFIRMA: How do you anticipate what you are planning will affect the situation on the ground or the broader conflict? How impactful is it going to be? We’ve heard some industrial control systems being attacked; is it in that vein?
fqw: GlorySec isn’t like other hacktivist groups that claim they are grey hats, but they are actually black hats. We always have a purpose when we hack, and we do it to push a cause. Our actions will likely impact Palestine financially, making them realize they need to back out. There have been some attacks on industrial control systems.
CYFIRMA: What are your views on Iran, who are widely known to fund Hamas? Isn’t that an attractive target?
fqw: We have looked into Iran, and that is our next operation after Palestine. We also have a few people already working on Iran, but it’s mainly focused on Palestine.
CYFIRMA: Before we wrap up, could you give us an idea of the background of your group? What makes you all so motivated?
fqw: GlorySec is made up of average citizens, such as cashiers or lawn mowers, everyday people like you. Our motivation comes from tragedies and events caused by companies and countries, like the wrongful invasion of Palestine. We are fighting for justice.
CYFIRMA: Thanks for chatting. If you want to say anything else, always feel free to reach out!
Cybercriminals, Hacktivists, APTs
Private botnets, Bulletproof VPS, Booters/Stressers, Compromised RDPs/VNCs
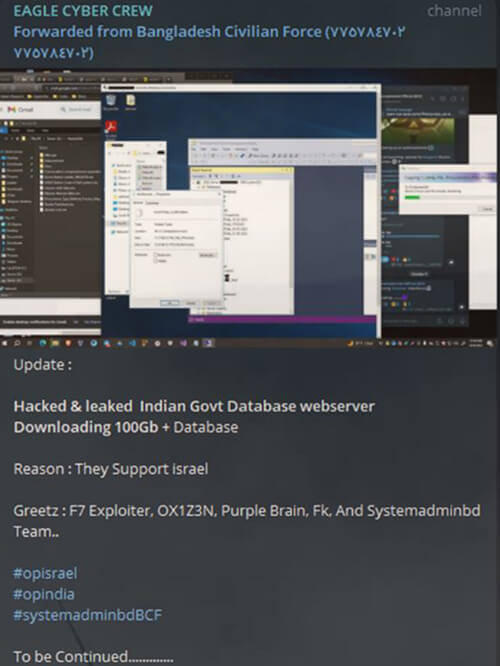
Pro-Gaza hacktivists are collectively targeting countries such as India, Egypt, Kenya, France, Germany, Italy, United Kingdom, and the United States (other than Israel). On the other hand, Pro-Israel hacktivists are targeting Iran, Iraq, Saudi Arabia, Lebanon and Qatar (other than Palestine and Gaza).
Most of these groups are disorganized and are looking to spread their propaganda using DDOS and defacement attacks. However, there are a few groups on either side that can execute more sophisticated attacks.
Throughout this period, CYFIRMA has observed an increasing number of cybercriminal groups entering the conflict, targeting infrastructure on both sides.
Note: This information is subject to change due to the dynamic nature of events.
Given how APT groups usually operate, we have not observed any confirmed activity yet. However, it is highly likely that they will attempt to take advantage of the situation to carry out more sophisticated attacks than we have seen so far from other groups. Below is a list of groups that have a history of targeting Israel:
Since the initial attack by Hamas, CISA is “in very close contact” with the Israeli National Cyber Directorate to share intelligence. US President Joe Biden is scheduled to embark on a trip to Israel, followed by Jordan, where he will engage with both Israeli and Arab leaders. On the other hand, Iran’s Foreign Minister, Abdollahian, has issued a warning about the possibility of Iran and its allies taking “preemptive action” in the near future in response to Israel’s attacks on Gaza. The Israeli-Palestinian conflict saw a significant escalation in cyber attacks by hacktivist groups and threat actors from various regions, targeting government websites, education and media sector, billboards, power plants, alert systems, and even sensitive military information. The involvement of these cyber actors added a new dimension to the ongoing conflict, highlighting the vulnerability of nations to cyberattacks in times of elevated tensions. As the situation began to unfold, it became clear that cybersecurity would play a critical role in this complex and long-standing conflict. The ongoing war has cost a lot of innocent lives on both sides.