


CYFIRMA analyzed the September 2, 2025, Jaguar Land Rover (JLR) cyber incident, which caused widespread disruption by shutting down global IT systems and halting manufacturing and retail operations, including at Halewood, while employees were sent home. The attack coincided with the UK’s “New Plate Day,” intensifying financial losses as dealers could not register or deliver vehicles. Although some customer data breaches have been confirmed, the exposure of internal systems by Scattered Spider Lapsus$ Hunters group on the Telegram channel and prior HELLCAT attacks highlight IT and operational risks.
On September 16th, Jaguar announced that the forensic investigation of the cyber incident is still ongoing. As a result, the company has extended the suspension of production until Wednesday, September 24, 2025, and communicated the same update to its supplier partners.
While JLR has not shared details on the scope or nature of the breach till now, the incident appears to align with a wider trend of advanced cyberattacks on the automotive sector. Notably, earlier this year, the HELLCAT ransomware group targeted JLR in separate attacks, exfiltrating hundreds of internal documents and compromising employee data through stolen Jira credentials.
Earlier, Jaguar Land Rover was Breached by HELLCAT Ransomware Group Using the Infostealer Playbook
The HELLCAT ransomware group claimed responsibility for a major data breach against Jaguar Land Rover (JLR), in which gigabytes of sensitive information were leaked, including proprietary documents, source code, and employee and partner data. The attack, attributed to a threat actor known as “Rey” [identified by breach tracking platforms as an active member of HELLCAT] on a dark forum, on March 10, 2025, posted roughly 700 internal JLR documents that were compromised. The breach was enabled through stolen Jira credentials harvested via Infostealer malware, a known hallmark of HELLCAT’s operations. The exposed data includes development logs, tracking information, source code, and a large employee dataset with usernames, email addresses, display names, and time zones. The presence of verified employee information from JLR’s global workforce raises significant concerns about identity theft and targeted phishing campaigns.
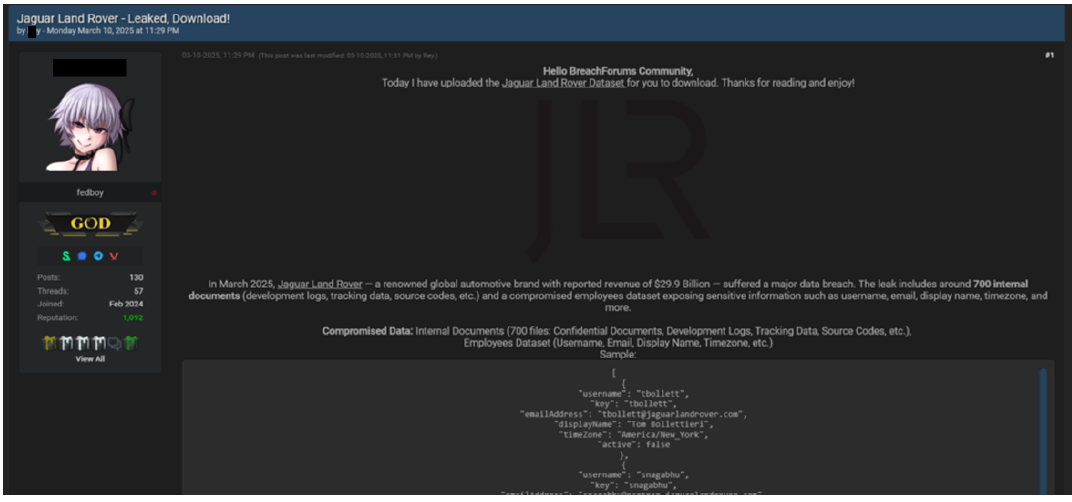
HELLCAT’s attack on Jaguar Land Rover (JLR) followed its known tactic of exploiting stolen Jira credentials, a method seen in attacks on other organizations earlier. Emerging in mid-2024, HELLCAT has rapidly developed into a sophisticated ransomware group, using spear-phishing or public-facing application exploits for initial access, followed by PowerShell-based persistence, AMSI bypasses, and reflective code loading. The final payload typically delivers SliverC2, providing persistent remote access. The leaked JLR data, including source code, tracking information, and potentially cloud credentials, poses serious risks, from intellectual property exposure to potential targeting of individual customers.
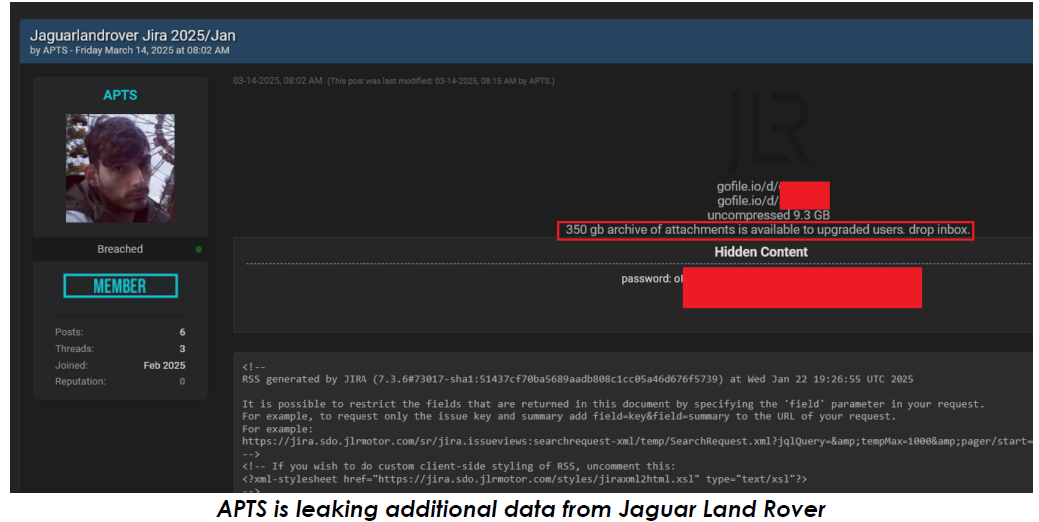
Just days after Rey’s initial disclosure, the JLR breach escalated when a second threat actor, “APTS,” appeared on DarkForums on March 14, 2025. APTS claimed to have exploited Infostealer credentials dating back to 2021, belonging to an employee who held third-party access to JLR’s Jira server. Using these compromised credentials, the actor gained entry and shared a screenshot of a Jira dashboard as proof. APTS also leaked an additional tranche of sensitive data, estimated at around 350 GB, which contained information not included in Rey’s original dump, further amplifying the scale and severity of the breach.
A Telegram channel calling itself Scattered Lapsus$ Hunters has claimed responsibility for Jaguar Land Rover’s cybersecurity incident, sharing a screenshot of Jaguar Land Rover’s internal IT systems. The channel’s name merges three English-speaking hacker collectives: Scattered Spider, Lapsus$, and ShinyHunters. Shinyhunters Collective has previously been linked to cyber-attacks on UK retailers. Jaguar Land Rover, however, has not yet confirmed the specifics or nature of the attack.
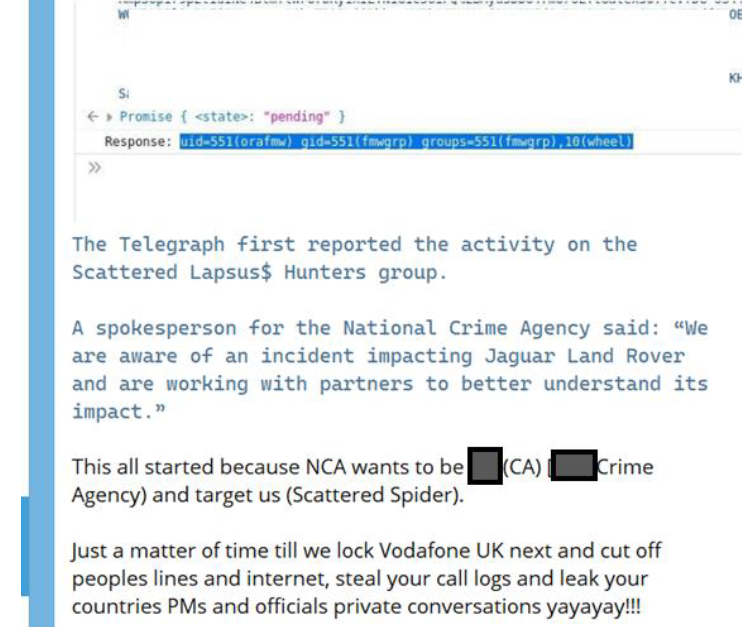
On September 3, 2025, while sharing news links related to the Jaguar Land Rover recent cyber incident, the Scattered Spider Lapsus$ Hunter Group also posted the following screenshot alongside.
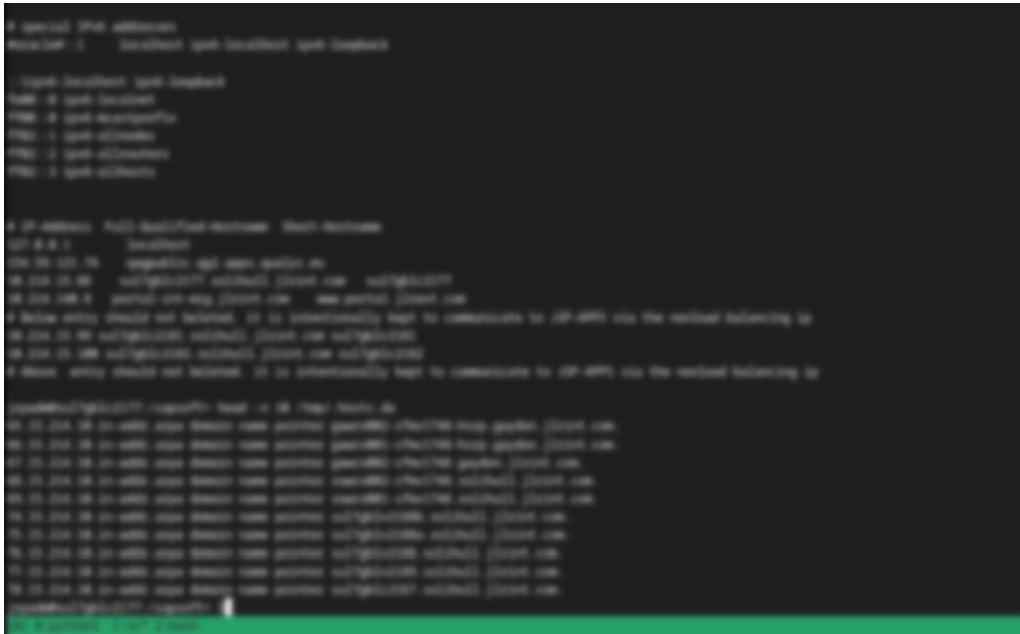
It was shared by the group Shinyhunters Collective, likely as proof they accessed internal JLR systems or proprietary data.
While the log itself may not be harmful, it is potentially part of a larger breach, making its exposure concerning.
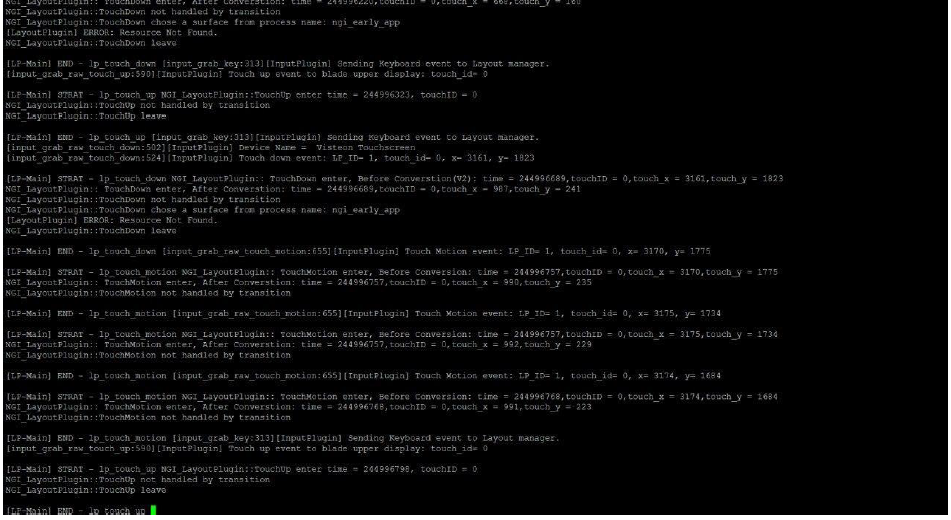

Based on the screenshots, leaked backend code, debug logs, and internal host/DNS entries shared by ShinyHunters Collectives, we can map possible MITRE ATT&CK TTPs.
| Tactic | Technique ID | Technique |
| Initial Access | T1566 | Phishing (Spear phishing to obtain credentials for internal systems) |
| Initial Access | T1078 | Valid Accounts (using stolen Jira/employee credentials) |
| Execution | T1059.001 | Command and Scripting Interpreter: PowerShell (if scripts were used to deploy malware in JLR systems) |
| Persistence | T1547.001 | Boot or Logon Autostart Execution: Registry Run Keys / Startup Folder (if scripts modified registry for persistence) |
| Privilege Escalation | T1068 | Exploitation for Privilege Escalation (leveraging misconfigured host entries) |
| Defense Evasion | T1027 | Obfuscated Files or Information (screenshots/code indicate obfuscation of activity) |
| Credential Access | T1555.003 | Credentials from Password Stores: Credentials from Web Browsers (Jira credentials) |
| Discovery | T1083 | File and Directory Discovery (screenshots show system paths, debug logs) |
| Discovery | T1046 | Network Service Discovery (internal DNS and host resolution entries) |
| Collection | T1005 | Data from Local System (debug logs, source code, backend files) |
| Collection | T1114 | Email Collection (if internal communication/data harvested) |
| Exfiltration | T1041 | Exfiltration over C2 Channel (sensitive code, Jira issues, debug logs) |
| Command and Control (C2) | T1071.001 | Application Layer Protocol (C2 over HTTPS/HTTP for persistence) |
| Impact | T1499 | Endpoint Denial of Service (threat of disruption to operational systems) |
| Impact | T1489 | Service Stop (shutdown of IT/retail systems as part of attack strategy) |
Based on the shared information, Shinyhunters Collective’s motives appear to be a mix of reputational and strategic rather than purely financial. By posting internal screenshots, backend code, and debug logs from Jaguar Land Rover systems, they are signaling technical prowess and gaining notoriety within the cybercriminal community. The targeting of operational systems, critical infrastructure, and connected vehicle modules suggests an interest in demonstrating control and influence, possibly to intimidate the company and its partners. While there is no direct evidence of ransom demands, the group could leverage the data for future exploitation or sell it, indicating potential financial incentives. Their references to geopolitical narratives in other posts hint at occasional ideological signaling, but the primary motive seems to revolve around recognition, influence, and potential leverage over the organization.
Based on the evidence and posts shared by the ShinyHunters Collective, the actor’s perceived impact of the Jaguar Land Rover incident appears to be significant and multi-dimensional:
The analysis suggests that the Jaguar Land Rover cyber incident not only disrupted operations but also exposed weaknesses across both IT and OT environments. Although no direct compromise of customer data has been confirmed, past breaches and leaked internal information increase the risks of credential theft, intellectual property exposure, and follow-on targeted attacks.
As the forensic investigation is still ongoing, the exact tactics used by the threat actors and their attribution remain unverified. Researchers, media outlets, and our own assessment indicate with medium confidence that the group ShinHhunters Collective may be responsible. However, we will await the official findings before making a definitive attribution.
Strategic Recommendations: Implement a comprehensive cyber resilience framework across IT and OT environments, ensuring regular risk assessments, supplier audits, and integration of lessons learned from industry incidents like JLR and Mitsubishi Electric SCADA vulnerabilities.
Technical Recommendations: Strengthen access controls by enforcing multi-factor authentication, regular credential rotation, and monitoring for compromised accounts; deploy advanced endpoint and network detection solutions to detect lateral movement or abnormal activity early.
Operational Recommendations: Develop and test incident response and business continuity plans that account for operational downtime, supply chain disruptions, and critical production halts; conduct employee training and simulations for cyber-attack scenarios.
Tactical Recommendations: Regularly perform tabletop exercises and red-team simulations targeting both IT and OT environments to test response procedures, validate detection capabilities, and ensure teams can quickly contain and remediate incidents similar to JLR or HELLCAT-style attacks