



Helldown Ransomware is a fast-evolving cyber threat targeting critical industries globally. With advanced cross-platform capabilities, including Windows and Linux, it disrupts systems by encrypting files and exploiting vulnerabilities. Its modular design and anti-detection techniques signal active development.
Helldown ransomware was first identified in August 2024 by CYFIRMA. The ransomware encrypts the files, appends random extensions to filenames, and creates a ransom note (“Readme.[random_string].txt”).
# Windows Platform:
File name: Hellenc.exe
File size: 653.50 KB (669184 bytes)
MD5: 5e7f5bb24a7cdaabcf3d2e77ed31fa4e
SHA-256: 0bfe25de8c46834e9a7c216f99057d855e272eafafdfef98a6012cecbbdcfabf
Compiler-stamp: Fri Aug 02 06:48:50 2024 | UTC
The specimen is a 32-bit GUI-based Windows executable. It drops two files, 1.bat and xx.ico, in the C: ProgramData directory.
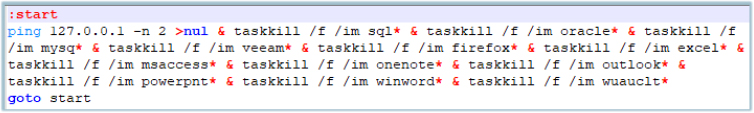
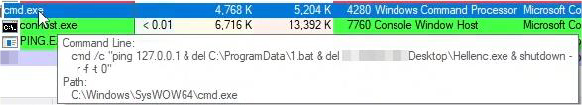
The dropped batch script initially pings the localhost and discards its result, which is used to create a small delay in execution, before forcefully terminating the process mentioned in the script:
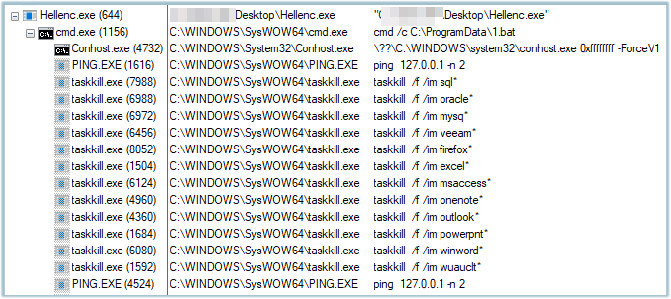
The below process tree shows the initial actions of the Helldown ransomware:
The malware checks for an analysis environment, such as the processor feature to detect a virtual machine:
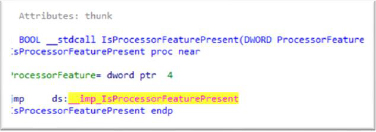
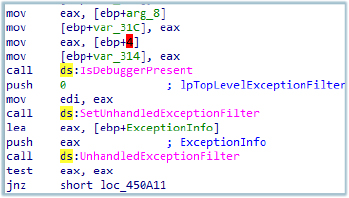
It also verifies if it is running under the debugger and calls UnhandledExceptionFilter as an anti-debugging measure to exit the debugger or terminate the process:
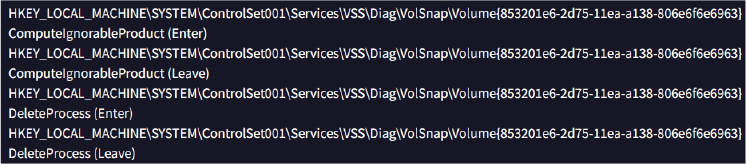
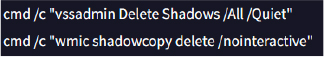
Helldown ransomware manipulates the Windows registries to alter the Volume Shadow Copy Service (VSS) settings, potentially to delete or alter shadow copies and hinder recovery efforts:
It encrypts the system files, including documents and images. It also changes the file extension of the encrypted ones to “.FGqogsxF” and the icon of the file using the icon file it dropped in ProgramData in the earlier stage of execution.
The Ransomware then deletes the dropped script and itself, and other artifacts, such as created registries, and restarts the compromised system:
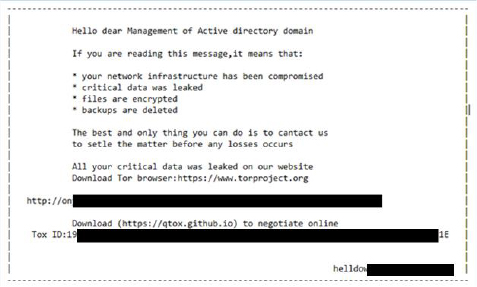
It drops a ransom note in the form of a text file:
Linux Platform:
File name: e.dat
File size: 237.30 KB (242999 bytes)
MD5: 64cc86931bab241dcc08db03e659bcc5
SHA-256: 6ef9a0b6301d737763f6c59ae6d5b3be4cf38941a69517be0f069d0a35f394dd
This specimen of Helldown ransomware is a 64-bit ELF executable. It loads hardcoded configuration data at the initial stage of execution, which includes tags associated with the malware’s actions:
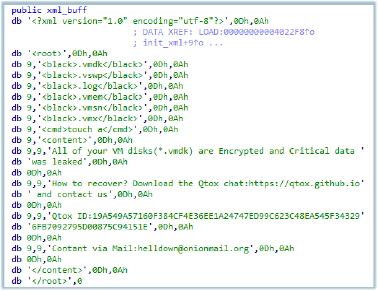
The ransomware executes commands using the shell command-line interpreter, leveraging the touch command to create and modify time stamps. It can evade sandbox detection by utilizing the sleep function from the standard C library.
The ransomware scans the path provided as an argument to the program, targeting files with extensions specified in the XML file’s excluded tags. When the ransomware identifies a file with a specified extension, it encrypts the file and a ransom note is generated on the infected machine using details from the XML file.
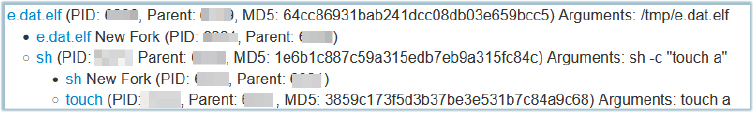
It is equipped with functionality to kill the VM (virtual instances) before encryption to get write access to the system files, but it is not executed during the execution. We also didn’t notice any network connection attempt to malicious IP/domain.
Researchers observed that threat actors are actively exploiting vulnerabilities in Zyxel firewalls to gain initial access to targeted systems. These firewalls, commonly used as IPSec VPN access points, were identified in at least eight breaches, with some victims replacing their devices following the incidents.
A critical vulnerability, CVE-2024-42057 with CVSS 8.1, which allows unauthenticated code execution, is believed to be a significant attack vector. During the breaches, attackers created unauthorized accounts, such as “SUPPOR87” and uploaded malicious files like “zzz1.conf,” which contained encoded payloads for exploitation. Reports of similar activity, including compromised devices running older firmware, further corroborate these findings.
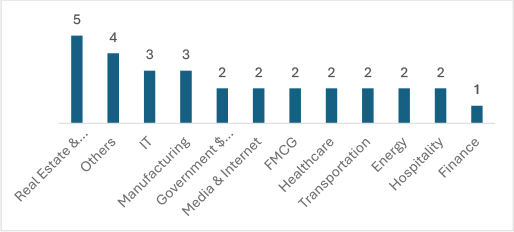
Helldown ransomware, which emerged just three months ago, has swiftly targeted diverse industries. Real Estate & Construction leads with five victims, followed by IT and Manufacturing with three each. Critical sectors like Healthcare, Energy, and Transportation are also affected, highlighting its broad scope and significant threat across essential services and businesses.
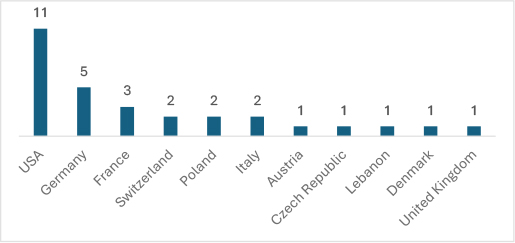
The Helldown ransomware, active for only three months, has already demonstrated a global impact, affecting victims in 11 countries. The USA has reported the highest number of cases (11), followed by Germany with five. France and Switzerland are also notably impacted, highlighting the ransomware’s extensive reach across Europe. Based on this trend, there is medium confidence that Helldown is likely to continue spreading globally rather than focusing on specific regions.
| MITRE FRAMEWORK | ||
| Tactic | ID | Technique/Sub Technique |
| Initial Access | T1190 | Exploit Public Facing Application |
| Execution | T1047 | Windows Management Instrumentation |
| Execution | T1129 | Shared Modules |
| Persistence | T1543.003 | Create or Modify System Process: Windows Service |
| Persistence | T1574.002 | Hijack Execution Flow: DLL Side-Loading |
| Privilege Escalation | T1055 | Process Injection |
| Privilege Escalation | T1543.003 | Create or Modify System Process: Windows Service |
| Privilege Escalation | T1548 | Abuse Elevation Control Mechanism |
| Privilege Escalation | T1574.002 | Hijack Execution Flow: DLL Side-Loading |
| Defense Evasion | T1027.002 | Obfuscated Files or Information: Software Packing |
| Defense Evasion | T1027.005 | Obfuscated Files or Information: Indicator Removal from Tools |
| Defense Evasion | T1036 | Masquerading |
| Defense Evasion | T1055 | Process Injection |
| Defense Evasion | T1070.004 | Indicator Removal: File Deletion |
| Defense Evasion | T1140 | Deobfuscate/Decode Files or Information |
| Defense Evasion | T1202 | Indirect Command Execution |
| Defense Evasion | T1497 | Virtualization/Sandbox Evasion |
| Defense Evasion | T1548 | Abuse Elevation Control Mechanism |
| Defense Evasion | T1562.001 | Impair Defenses: Disable or Modify Tools |
| Defense Evasion | T1574.002 | Hijack Execution Flow: DLL Side-Loading |
| Credential Access | T1003 | OS Credential Dumping |
| Credential Access | T1056 | Input Capture |
| Credential Access | T1552.001 | Unsecured Credentials: Credentials in Files |
| Discovery | T1007 | System Service Discovery |
| Discovery | T1010 | Application Window Discovery |
| Discovery | T1016 | System Network Configuration Discovery |
| Discovery | T1018 | Remote System Discovery |
| Discovery | T1057 | Process Discovery |
| Discovery | T1082 | System Information Discovery |
| Discovery | T1083 | File and Directory Discovery |
| Discovery | T1135 | Network Share Discovery |
| Discovery | T1497 | Virtualization/Sandbox Evasion |
| Collection | T1005 | Data from Local System |
| Collection | T1056 | Input Capture |
| Collection | T1114 | Email Collection |
| Collection | T1185 | Browser Session Hijacking |
| Command and Control | T1071 | Application Layer Protocol |
| Command and Control | T1090 | Proxy |
| Command and Control | T1105 | Ingress Tool Transfer |
| Impact | T1486 | Data Encrypted for Impact |
| Impact | T1489 | Service Stop |
Helldown ransomware poses a significant risk to businesses globally due to its advanced encryption techniques, exploitation of known vulnerabilities, and cross-platform targeting. Its focus on critical industries and regions highlights its potential to cause widespread disruption. Proactive measures, such as patching known vulnerabilities and robust backup strategies, are critical to mitigate its impact.
title: Delete shadow copy via WMIC
status: experimental
threatname:
behaviorgroup: 18
classification: 0
mitreattack:
logsource:
category: process_creation
product: windows
detection:
selection:
CommandLine:
– ‘*wmic*shadowcopy delete*’
condition: selection
level: critical
(Source: Surface Web)
STRATEGIC RECOMMENDATIONS
MANAGEMENT RECOMMENDATIONS
TACTICAL RECOMMENDATIONS