



CYFIRMA offers intelligence designed to help customers, clients, and end-users stay vigilant during festivals and upcoming events. These periods, filled with buying, selling, and celebration, also provide an ideal opportunity for cybercriminals and scammers to exploit individuals and businesses for financial or other motives. Hacktivists, on the other hand, may target retail websites to gain attention, knowing that these platforms see increased traffic during festivals. This is why it’s crucial to stay one step ahead and be aware of the risks to ensure a safe and secure online experience.
As the holiday season is reaching its apex, the threat of cyber-attacks targeting retailers and seasonal shoppers becomes ever more present.
The period is an ideal opportunity for cybercriminals to exploit the surge in online transactions, as high volumes of shoppers seeking seasonal deals – alongside the complex network of APIs and third-party connections supporting the online retail ecosystem – rends the industry a lucrative target.
These threats can manifest in various forms, including:
Holidays and festivals heighten consumer activity, which in turn provides increased opportunities for malicious campaigns:
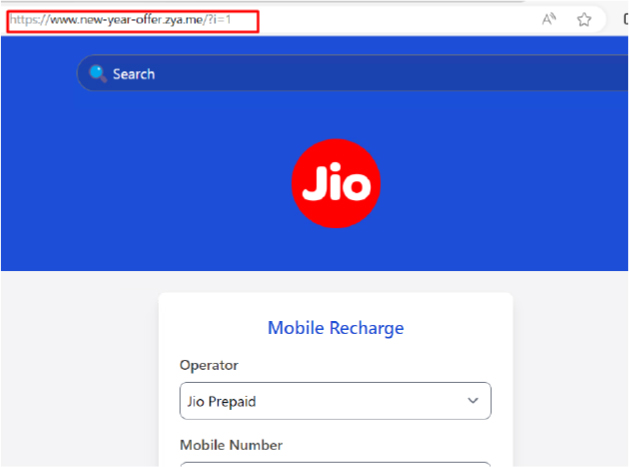
Scammers and cybercriminals frequently employ tactics such as scam pages and phishing to defraud the public, often using the lure of significant discounts (e.g. “New-Year Sales!”) and impersonating well-known e-commerce platforms.
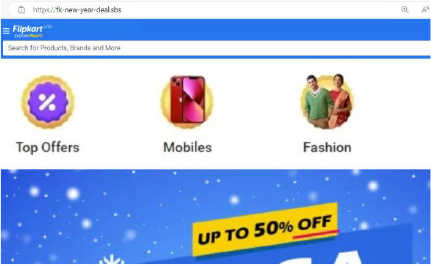
As illustrated above, malicious actors have meticulously crafted look-alike pages to mimic genuine websites, complete with offers that appear too good to refuse (e.g. offering products at a 90% discount).
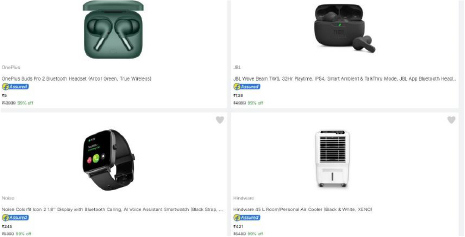
Our investigation revealed that the only payment option is Unified Payments Interface (UPI) – conspicuously lacking other methods like credit cards or Paypal. This restricted payment method raised red flags, leading us to trace numerous UPI receiver numbers linked to these fraudulent transactions, that we have since forwarded to the relevant authorities.
Dark web forums and Telegram channels have become the go-to platforms for fraudsters looking to purchase scam pages and quickly set up fraudulent websites. The rise of Phishing-as-a-Service (PhaaS) has made it even easier for scammers to execute their fraudulent schemes, offering ready-made, customizable phishing websites that can be deployed with minimal effort, allowing cybercriminals – even those with limited technical skills – to easily access and use professional-looking phishing websites tailored to their specific needs.
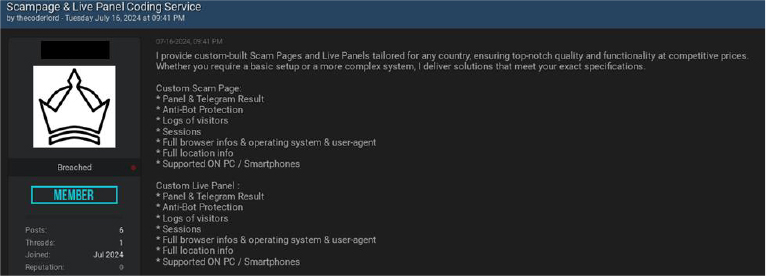
Once a scammer acquires a template, it can be easily customized to target certain demographics, making it appear more legitimate.
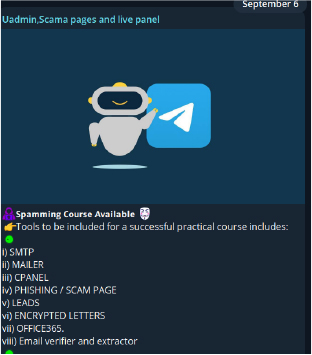
Fraudsters also distribute malicious APK files, exploiting the large number of Android users in India. These APK files often function as Remote Access Trojans (RATs), designed to log keystrokes, steal browser passwords, and harvest other personally identifiable information (PII) from the victim’s device.
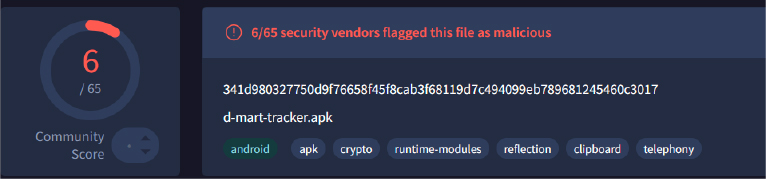
In a previous investigation, CYFIRMA researchers uncovered a fake D-Mart Diwali themed domain dmartdiwalisales[.]site that was distributing an APK file named “d-mart-tracker.apk”. While the file appeared to be a legitimate tracking app, it was actually a Trojan designed to infiltrate users’ devices, and once installed, it could perform a range of malicious activities, including logging keystrokes, stealing stored passwords, and accessing sensitive data.
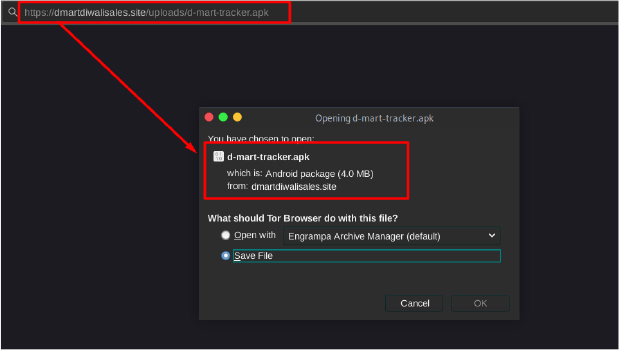
This particular Trojan was flagged as malicious by our OSINT (Open-Source Intelligence) tools, highlighting the ongoing threat posed by these fraudulent APK files. The combination of scam websites and malicious APK distribution makes these campaigns particularly dangerous, as they can compromise not just the victim’s financial information, but also their entire digital footprint.
It has been observed that cybercriminals and advanced threat groups become more active during periods when systems are less likely to be monitored and their targets are less vigilant, allowing a greater variety of opportunities to strike.
Cybersecurity teams are frequently understaffed during holiday periods, making it significantly more difficult for organizations to promptly detect and respond to potential threats – exacerbating an attack’s effect due to the increased likelihood of prolonged non-detection.
Organizations may also get phishing emails disguised as holiday offers, gift vouchers, or discounted travel deals, all of which can easily lure employees into clicking malicious links or downloading infected attachments, inadvertently compromising their organization’s security. This, along with reduced staffing and an increase in holiday-themed phishing attacks creates a perfect storm where organizations are vulnerable to cyberattacks – attacks which may not even be caught until significant damage has been sustained.
Scammers can use malvertising and blackhat SEO tactics to boost their website rankings and target unsuspecting victims, particularly during festival seasons when online shopping surges.
1. Malvertising
Scammers purchase legitimate ad space on websites or ad networks and inject malicious code into the ads. These ads often masquerade as enticing festival-related promotions or deals. When users click on them, they are either redirected to fraudulent websites or exposed to drive-by downloads that automatically install malware on their devices without any interaction. The goal is to steal personal and financial information or infect devices to pivot further.
During high-traffic shopping seasons, like festivals, these malicious ads are more likely to attract users searching for special offers, significantly increasing the chances of a successful scam.
2. Blackhat SEO
Blackhat SEO uses unethical tactics such as keyword stuffing, cloaking, and link farming to manipulate search engine rankings. Scammers create fake websites optimized for popular festival-related search terms (e.g., “top Diwali deals, Christmas sale”) to push their fraudulent pages to the top of search results, increasing the likelihood that users will click on these fake sites.
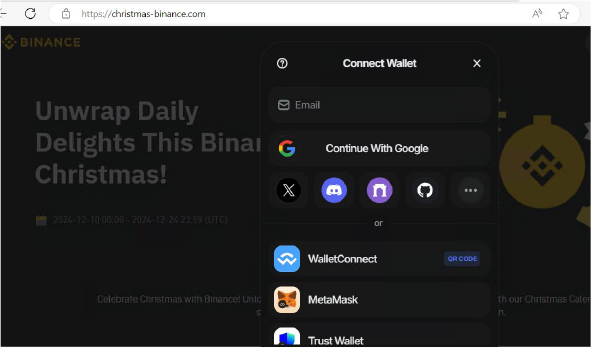
3. Typosquatting: additionally, scammers often register domain names that are very similar to well-known brands or stores, exploiting common typing mistakes to redirect users to malicious websites.
For example, as seen in the screenshot, a fraudulent page impersonating Binance is designed to deceive users by requesting their login credentials upon visiting. Unsuspecting users who fail to recognize the scam may inadvertently provide their credentials, enabling threat actors to employ dumping tactics to harvest sensitive information.
Artificial Intelligence is reshaping our world, but it’s also being exploited by cybercriminals to craft highly advanced schemes.
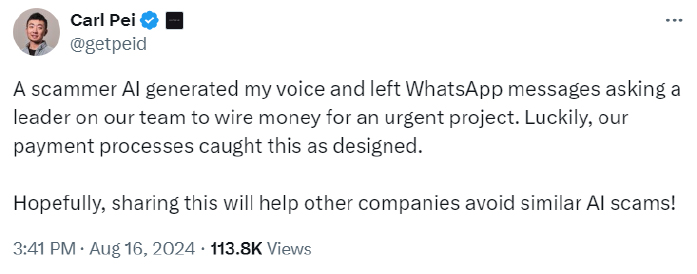
In a recent incident, Carl Pei, the CEO of Nothing smartphone brand, revealed that a scammer used AI to clone his voice and carried out a vishing (voice phishing) attack on the Nothing team, asking for money. This case highlights how scammers and cybercriminals are exploiting advanced technologies like AI for their own gain.
Using deepfake technology, cybercriminals are now able to create highly realistic videos of celebrities or public influencers endorsing fake deals, sales, or giveaways. Scammers could, for example, produce a convincing deepfake video of a well-known celebrity “promoting” a fake shopping site offering massive holiday discounts on festival goods. These videos are shared across social media platforms, and because they look genuine, many people trust the message and click on the provided links.
Malicious content like this can easily go viral during festivals, as people are excited to share offers, discounts, or videos with their friends and family, especially via platforms like WhatsApp. Unfortunately, without verifying the authenticity of these offers, people often unknowingly forward scam links or deepfake videos, contributing to the spread of fraudulent schemes.
These AI-generated emails can include personalized greetings, relevant products, and attractive festival discounts, making them hard to distinguish from real promotional emails.
With many upcoming festivals, expect a surge in new scamming domains. This season isn’t just an opportunity for scammers, it’s also the perfect time for hackers to create phishing emails containing malicious attachments to gain initial access or spread malware. Many cybercriminals take advantage of bulletproof server providers, which are notorious for ignoring abuse reports, allowing them to host malicious sites or distribute malware without fear of takedown.
The intersection of evolving technology and festive culture is likely to lead to more sophisticated and opportunistic cybercrime. As digital celebrations become mainstream, there will be a critical need for stronger cybersecurity measures, awareness, and vigilance – especially during festive seasons when people are more emotionally and financially engaged.
| Indicator | Remarks |
| fk-new-year-deal[.]sbs | Fake Website |
| new-year-offer[.]zya[.]me | Fake Website |
| 341d980327750d9f76658f45f8cab3f68119d7c494099eb789681245460c3017 | Android Trojan |