



At CYFIRMA, we are committed to offering up-to-date insights into prevalent threats and tactics employed by malicious actors, targeting both organizations and individuals. In this report, we analysed Hexon Stealer, a stealer capable of extracting browser credentials, autofill data, and other sensitive information which leverages the Electron framework for compiling malware.
We identified several outlets associated with the malware developer which are used to promote the stealer. These sites also feature a login panel, enabling Hexon Stealer users to remotely control compromised systems.
In August, a Telegram channel named “Hexon Stealer” emerged, where a user was actively promoting a Discord-based information stealer. The malware developer claimed that it is capable of exfiltrating Discord tokens, 2FA backup codes, browser cookies, autofill data, saved passwords, credit card details, and even cryptocurrency wallet information.
Hexon Stealer grants full remote access to the compromised system, allowing attackers to monitor screens, control keyboard and mouse inputs, execute terminal commands, and engage in private chats – potentially for ransom negotiations. The malware leverages Coinbase for anonymous cryptocurrency payments, making ransom transactions challenging to trace.

Recently, the administrator of the original Hexon Stealer Telegram channel removed it and rebranded the operation under a new channel called Hexon Grabber. Hexon Stealer is based on the NSIS installer format and is primarily focused on stealing browser cookies, credentials, and crypto-wallets. It is essentially a rebranded version of the Stealit Stealer, which was previously taken down by security researchers who subsequently released its source code for public analysis on GitHub.
| File Name | saa+Setup+1.0.0.exe |
| File Size | 79.91 Mb |
| Signed | File is not Signed |
| MD5 Hash | e173d1216236bccdc15c56bf27859a1d |
| SHA256 Hash | 326c21e845863ea6ebe7d09ec3915d99e18f95e575e97aac2f71ae41160327e1 |
| First Seen in the Wild | August 2024 |
| SSDEEP | 1572864:IFJ39Kk7kli/oS9MXjB8ceyIS7nqYdd6hIEhSmn6nlN/sFuh:I0k7Yan9MT/vP7nMhJnUXs4h |
Hexon Stealer is based on an electron framework, just like most other Discord stealers. This framework enables developers to build cross-platform desktop applications using web technologies like HTML, CSS, and JavaScript by integrating Chromium and Node.js. Meanwhile, NSIS (Nullsoft Scriptable Install System) is an open-source utility for creating efficient, lightweight Windows installers. Hexon Stealer leverages Electron for its desktop application interface and is packaged using NSIS to distribute its malicious payload.
Discord Injection: Injects malicious code into Discord to exfiltrate sensitive information.
Game Account Access: Can potentially compromise the victim’s gaming accounts.
Cryptocurrency Theft: Targets crypto wallets, such as the Exodus wallet, to steal stored assets.
Screen Capture: Allows the attacker to take screenshots of the victim’s desktop.
Pranking & Fake Prompts: Can send fake prompt messages to prank or manipulate the victim.
Chat and Ransom Negotiation: The attacker can engage in direct chats with the victim, potentially demanding a ransom.
System Control: Provides functionality to shut down, restart, lock, or put the victim’s device to sleep remotely.
HWID Authentication: Access to the malware’s dashboard is restricted by requiring the user of Hexon Stealer to enter the victim’s Hardware ID (HWID). The Developer has developed the panel and hosted on port 1337.

Hexon Stealer drops a secondary executable named saa.exe. The file is based on the electron framework.
9a5aa40a67378d078046c2d22e23fa110881f722067a3a413c99cfbfd0402d1f
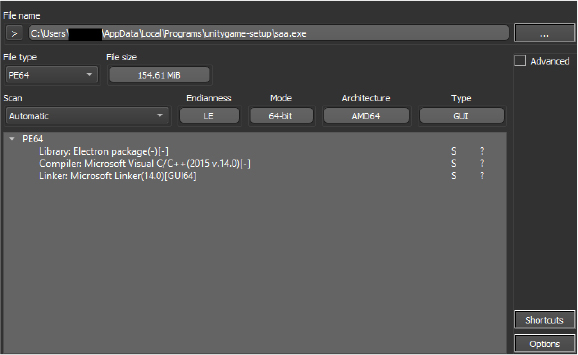
It gathers the stolen browser data and saves it in the Temp folder with a randomly generated filename as shown in the below snippet.
Two versions of the data are created:
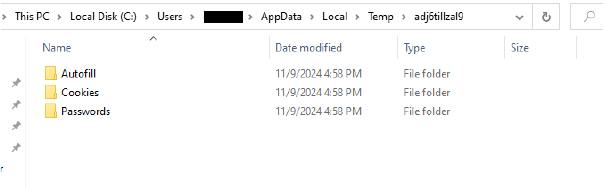
This approach of saving both unarchived and zipped files allows for quick access and efficient exfiltration while using random filenames in the Temp folder helps avoid detection.
Modifying process features and prefetch settings could be used to manipulate system behavior or evade detection by security software (for example, disabling certain features might help the malware avoid detection or hinder analysis by security tools).
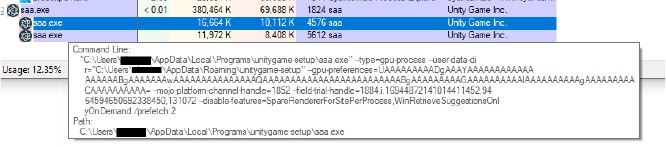
Malware based on the Electron framework often stores its malicious code in JavaScript files inside the ‘app.asar’ folder after extracting the contents of this file using 7-Zip with the Asar plugin.
The code appeared to be obfuscated, making it harder to read and understand, which is a technique used by malware authors to make analysis more difficult.
The developer has likely used tools like JSConfuser to obfuscate the code, as JSObfuscator is unable to detect that the code has been obfuscated by these specific tools. This suggests that the obfuscation is advanced or customized, making it more challenging for traditional deobfuscation methods to recognize the technique.
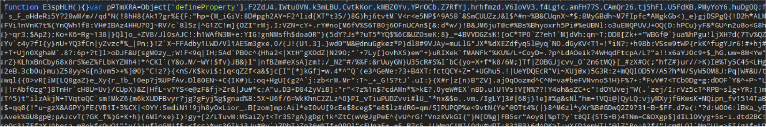
We used a JS beautifier to make the code more readable. The following code snippet appears to be obfuscated JavaScript, likely implemented by the malware author to conceal its actual functionality.
The code employs cryptic variable names like E3spHLH, pPTmXRA, F2ZdJ4, etc., which obscure its purpose and make it difficult to interpret. It also uses Object.defineProperty to modify or hide properties, a common technique to alter JavaScript object properties without detection.
This method is often used to change the behavior of built-in objects or to set hidden values. By manipulating object properties in this way, the code aims to conceal its activities, making it harder to debug or tamper with.
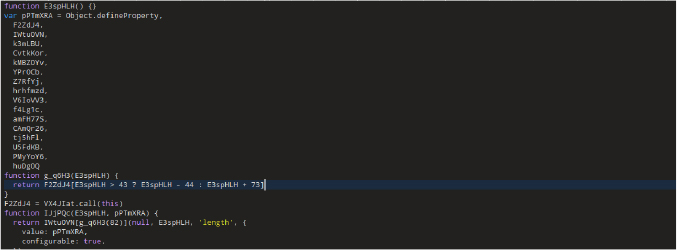
During the investigation, we discovered a Hexon Stealer website where the malware is being actively promoted.
The site features a login dashboard that allows users to monitor their targets, providing them with real-time access to the stolen data and potentially offering tools for further control or exploitation.
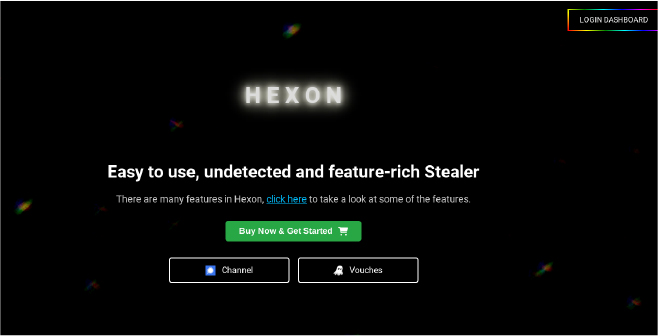
This login panel is located at path /user/login/ and is likely used by the attacker to track compromised systems and manage the stolen information.
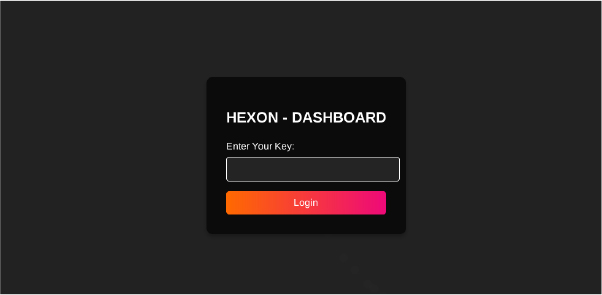
Hexon Stealer has gained a good user base, particularly Telegram, where it boasts over 100+ users, and also operates a Signal group with around 40+ users. The developer, using the moniker ‘Xeina’, has introduced subscription plans for users, offering weekly, monthly, and yearly options. Prior to rebranding to a new channel called HexonGrabber, the old Telegram account was deleted by the developer.
During the investigation, we discovered a domain that referenced the old Hexon Stealer Telegram link, and further digging into discussions related to Hexon Stealer revealed that it was developed by the same creator behind Stealit Stealer.
The Stealit Stealer group was reportedly hacked by a researcher known as the ‘Returnit group’, who allegedly leaked the Stealit source code.
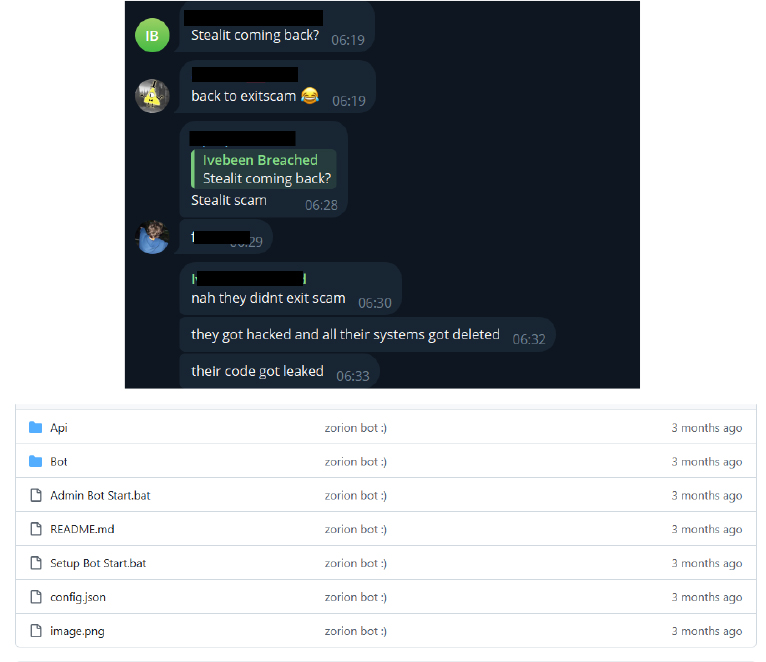
According to chatter, the group encrypted all their network systems. The leaked code, which had its malicious capabilities was removed and sanitized, and then shared publicly on GitHub by the ‘Returnit group’.
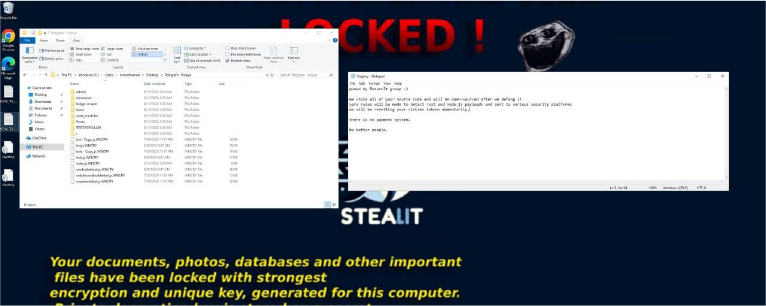
Upon examining the domains side by side, it’s clear that the Stealit old domain shares the same structure as the Hexon Stealer domain.
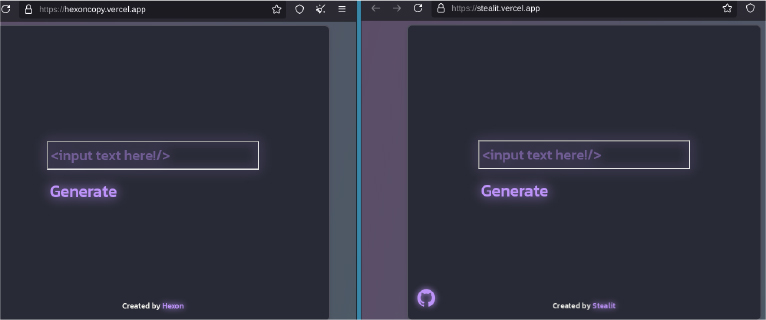
Stealit appears to be a copy of Fewer Stealer, and Hexon Stealer was developed by the same group of people (previously known by the names art6q and dojkv2).
During our investigation, we found that many users in the old group chat were communicating in Turkish. Additionally, when reviewing the HTML source code of the Hexon website, we discovered comments written in Turkish:
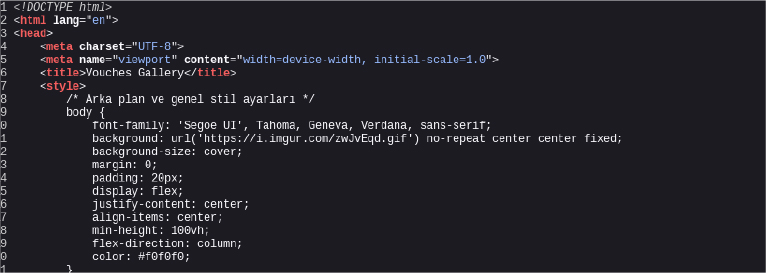
Note that the Stealit developers were also Turkish, so based on this evidence, we can state with medium confidence that the same individuals are behind Hexon Stealer and with high confidence that the author of Hexon Stealer is likely a Turkish person.
| No. | Tactics | Techniques |
| 1 | Execution (TA0002) | T1047: Windows Management Instrumentation T1059: Command and Scripting Interpreter |
| 2 | Persistence (TA0003) | T1547.001: Registry Run Keys / Startup Folder T1574.002: DLL Side-Loading |
| 3 | Privilege Escalation (TA0004) | T1055: Process Injection T1547.001: Registry Run Keys / Startup Folder |
| 4 | Defense Evasion (TA0005) | T1036: Masquerading T1055: Process Injection T1497: Virtualization/Sandbox Evasion |
| 5 | Credential Access (TA0006) | T1003: OS Credential Dumping |
| 6 | Discovery (TA0007) | T1012: Query Registry T1057: Process Discovery T1018: Remote System Discovery T1082: System Information Discovery |
| 7 | Collection (TA0009) | T1005: Data from Local System |
| 8 | Command and Control (TA0011) | T1573: Encrypted Channel T1071: Application Layer Protocol |
The following queries can be used by analysts to search for new login panels or websites associated with the Hexon Stealer. These queries are not specific to any particular cybersecurity search engine:
| General Query | Pattern |
| HTML Title | “Hexon Stealer” |
| HTML Body | “Hexon Stealer” |
| Body Hash: Sha1 | e85b03f4f2fff63c48c6983ac1e8d6c0a505ca56 |
| FeatureID or FID | fid="ODroozJyunq06YGdOsWHuQ==" |
| No. | Indicator (SHA-256) | Remarks |
| 1 | 326c21e845863ea6ebe7d09ec3915d99e18f95e575e97aac2f71ae41160327e1 | Hexon Stealer 1st Payload |
| 2 | b55afdbd2e8d258a54aefd98570e4749ad993f4322ec7e3b27d7a7ab413f7246 | JS file |
| 3 | 9a5aa40a67378d078046c2d22e23fa110881f722067a3a413c99cfbfd0402d1f | Hexon Stealer 2nd Payload |
| 4 | Hexon[.]fun | Domain |
| 5 | hexoncopy[.]vercel[.]app | Domain |
| 6 | stealit[.]vercel[.]app | Domain |
| 7 | 72[.]145[.]3[.]21 | IP/Login Panel |
| 8 | 20[.]19[.]32[.]198 | IP/Login Panel |
| 9 | 20[.]151[.]152[.]98 | IP/Login Panel |
| 10 | 20[.]199[.]91[.]177 | IP/Login Panel |
| 11 | 4[.]233[.]148[.]165 | IP/Login Panel |
Discord stealers are growing rapidly, with low-skill cybercriminals frequently compiling old stealer codes and promoting them under new names on apps such as Telegram, Session, or Signal. These stealers often leverage the Electron framework to target credentials, gaming accounts, Discord Nitro, and other sensitive information. Based on our investigation, we have high confidence that the developer behind this stealer is Turkish, and medium confidence that the group is a rebranding of the Stealit Stealer group, which previously utilized the code of Fewer Stealer to create new variants.
Implement Defense-in-Depth Strategy: Develop a comprehensive defense strategy that combines network segmentation, robust perimeter defenses, and endpoint security to create multiple layers of protection against such threats.
Invest in Threat Intelligence: Engage with threat intelligence services to stay informed about the evolving tactics, techniques, and procedures employed by malware operators. Regularly update defenses based on the latest threat intelligence to enhance proactive detection capabilities.
Enhance Employee Training: Conduct regular cybersecurity training programs to educate employees about phishing threats, social engineering, and safe browsing practices. Building a security-aware culture can significantly reduce the likelihood of successful infostealer infections.
Develop an Incident Response Plan: Establish a robust incident response plan that outlines clear procedures for identifying, containing, eradicating, and recovering from a stealer infection. Regularly test and update the plan to ensure effectiveness.
Conduct Regular Security Audits: Perform periodic security audits to assess the effectiveness of existing security controls, identify potential weaknesses, and validate the organization’s overall security posture. Use the findings to make informed adjustments and improvements.
Collaborate with Industry Peers: Engage in information sharing and collaboration with industry peers, cybersecurity communities, and relevant authorities. Sharing threat intelligence and best practices can enhance collective resilience against emerging threats like info stealers.
Update and Patch Systems: Regularly update and patch operating systems, software, and applications to address vulnerabilities that malware like stealer exploits. Automated patch management tools can streamline this process and minimize the attack surface.
Utilize Advanced Endpoint Protection: Deploy advanced endpoint protection solutions that incorporate behavioral analysis, heuristic detection, and threat intelligence to identify and mitigate the specific techniques employed by the following stealer. Ensure these solutions are regularly updated with the latest detection rules, such as the one given in the report.
Implement Application Whitelisting: Restrict the execution of unauthorized applications by implementing application whitelisting. This helps prevent the execution of unknown or malicious binaries, hindering the stealer’s ability to run on endpoints.