



At CYFIRMA, we are dedicated to providing timely insights into emerging threats and tactics used by cybercriminals targeting individuals and organizations. This report examines Flesh Stealer, a .NET executable written in C#. The malware does not target CIS countries and is capable of bypassing app-bound encryption employed by Chrome. Developed by a Russian-speaking individual, Flesh Stealer includes various features such as anti-debugging and anti-VM capabilities.
Flesh Stealer has been actively promoted on Discord and Telegram channels, as well as lesser-known underground forums like Pyrex Guru. Employing Base64 obfuscation techniques to conceal its functions and strings, the stealer first emerged in August 2024 and continues to receive updates with new features.
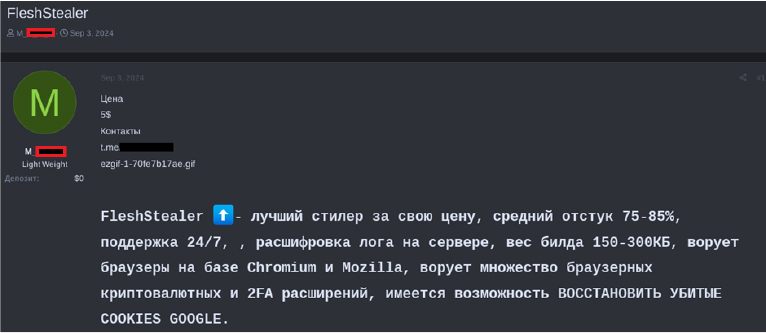
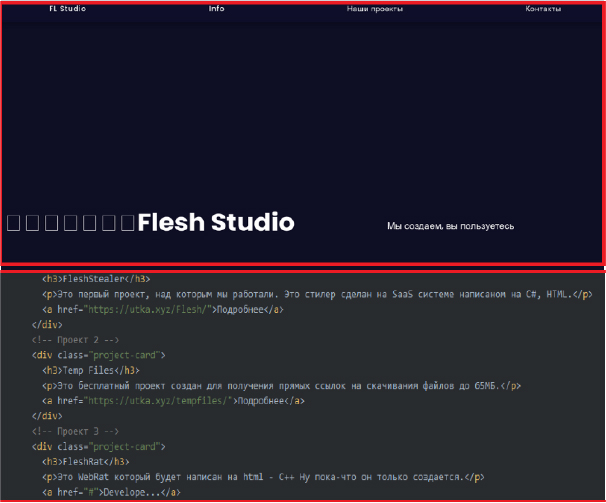
Promotional efforts for Flesh Stealer extended to YouTube, where its developer shared a walkthrough of the malware (however the video was eventually taken down by the platform). A dedicated website that was used to distribute the stealer was also removed, with its last recorded activity occurring in October 2024.
Flesh Stealer is designed to target browsers such as Opera, Chrome, Firefox, and Edge, from which it steals cookies, credentials, and browsing history. Additionally, it also steals data from applications like Signal and Telegram, extracting stored databases and chats, which are then transferred to the attacker’s command and control infrastructure.
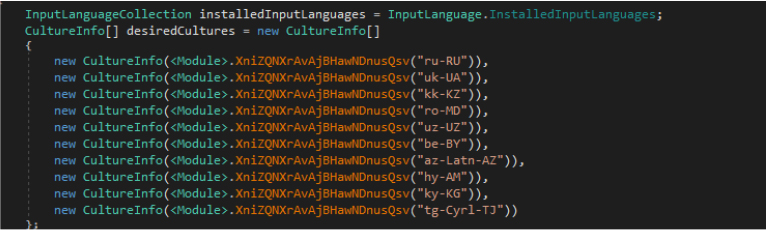
The malware checks for the presence of a specific cultural setting, referred to as CIS countries (Commonwealth of Independent States) by evaluating the installed input languages on the system. If any of the installed languages match, the malware will refrain from executing or infecting the system.
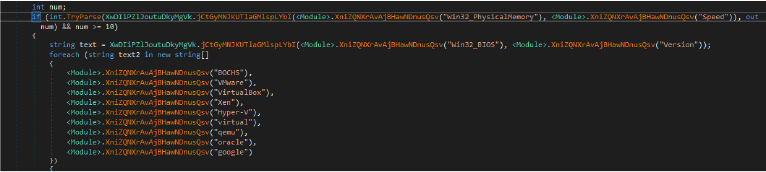
Flesh stealer employs anti-VM techniques to detect if it’s running in a virtualized environment. It checks physical memory characteristics, system speed, and BIOS version as indicators of a virtual machine. Additionally, the malware scans for specific strings such as, BOCHS, VMware, VirtualBox, Hyper-V, Qemu, to identify virtual environments. If any of these conditions are met, the malware will kill its activity to avoid detection and analysis.
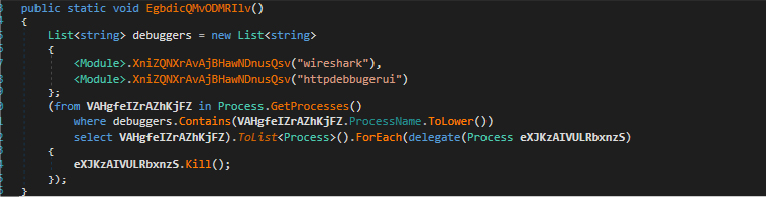
Flesh stealer has anti debugging technique it scans for debugging tools – such as Wireshark and HttpDebuggerUI – by retrieving a list of all active processes on the system. It then compares the running processes against a predefined list of debugger names. If a match is detected, the malware attempts to kill the debugger process.
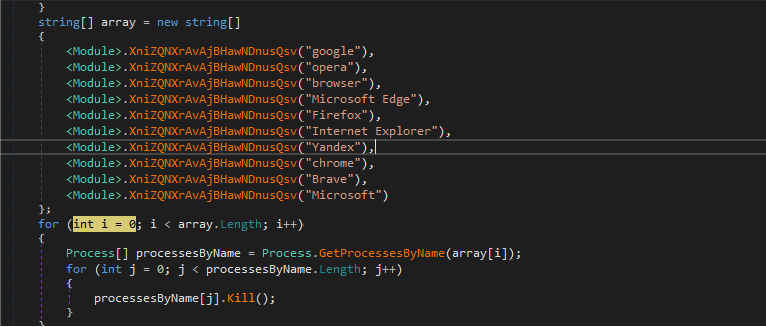
This below code is to extract sensitive information such as saved passwords, cookies, and from popular browsers like Chrome, Firefox, Brave and Edge, checking for the presence of these browsers on the victim’s system. As highlighted in the video title of flesh stealer, it can additionally work on Chrome 129, and is capable of bypassing Chrome’s App Bound Encryption to access protected data.
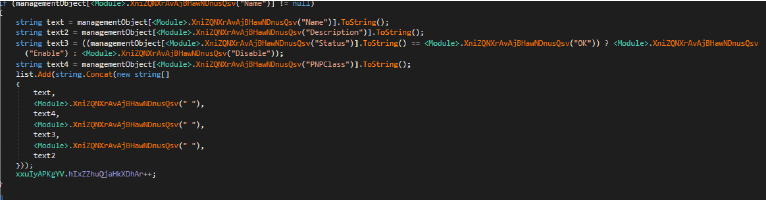
The code leverages the Windows Management Instrumentation (WMI) component to gather details about Plug and Play (PnP) devices attached to the victim’s system, retrieving specific properties of these devices, such as name, description, status, and PNPClass. The code then saves all these details to a file named device.txt.
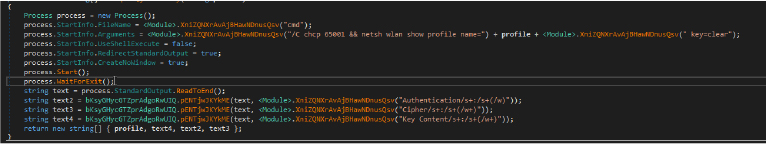
Flesh stealer also extracts Wi-Fi network credentials from the victim’s system using the ‘netsh’ command-line tool to retrieve detailed information about a specific Wi-Fi profile. The extracted information contains authentication type and encryption algorithm and password.
In August 2024, the Flesh Stealer developer created a domain to promote the malware, offering a free version of the stealer. However, the website is now offline.
On January 29, 2025, the developer announced that Flesh Stealer now supports version 131 of Chrome.
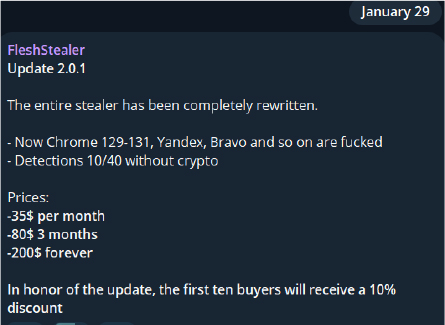
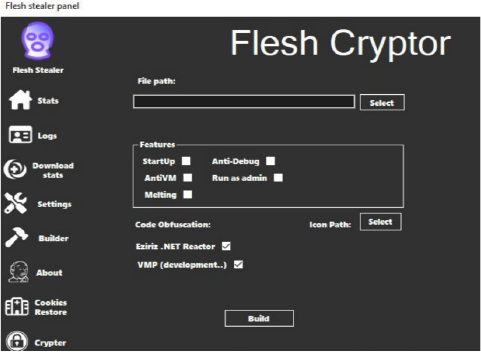
The user of Flesh Stealer obliges the control panel to customize their stealer with various functions, such as enabling anti-debug features, adding the stealer to startup, or running it with administrator privileges. All victim logs are sent to the attacker’s hosted infrastructure and can be viewed in the logs section of the panel.
The developer of Flesh Stealer is a Russian speaker and employs the common tactic of avoiding attacks on CIS countries, a strategy often used by Russian or CIS-based developers to avoid being banned from Russian-based forums. The developer is active on two or three forums, including PyrexGuru, Dzen.
The Flesh Stealer channel has been active since August 17, 2024, and has over 210 users. There are three channels: one for Russian speakers, one for English speakers, and another one for Product feedback, the latter created on October 31, 2024, which currently has over 10 users.
| Indicators | Remarks |
| d96e63fb18eb2e587f33e100501f66cc83225b8f19a374ad5817bc7c1ec07896 | Analysed Version |
| b388d2b53453add11982a0e5b86ee01bbaf318ee77483300731d2202ce906146 | Free Version |
| Utka[.]xyz | Old Domain of Flesh Stealer |
| Tactics | Technique | Object |
| Execution | T1047: Windows Management Instrumentation T1129: Shared Modules |
Access WMI data in .NET Link function at runtime on Windows |
| Defense Evasion | T1140: Deobfuscate/Decode Files or Information T1112: Modify Registry T1027: Obfuscated Files or Information T1497.001: Virtualization/Sandbox Evasion: System Checks |
Decode data using Base64 in .NET Delete registry keys Encrypt data using DPAPI Anti-VM strings targeting Xen |
| Discovery | T1082: System Information Discovery T1057: Process Discovery T1033: System Owner/User Discovery T1087: Account Discovery T1083: File and Directory Discovery T1012: Query Registry T1518: Software Discovery T1016: System Network Configuration Discovery |
Get OS Version, Disk Information, Hostname, Number of Processors. Find process by name or PID Checks if a File or directory exists. Gather Networking Interfaces details. |
| Collection | T1113: Screen Capture | Capture Screenshots |
| Command and Control | T1105: Ingress Tool Transfer | Download and Write a File |
New stealers are emerging daily on platforms like Telegram, and, despite Telegram’s new transparency policies, malware developers continue to use these platforms to promote their stealer and host their command-and-control (C2) servers – through bots or webhooks – to control targets or collect their data. Flesh Stealer has received positive feedback from its users, motivating the developer to regularly update it with new features.
Threat Intelligence Integration: Continuously monitor and incorporate threat intelligence feeds into your organization’s cybersecurity framework to stay updated on emerging threats like Flesh Stealer.
Incident Response Planning: Develop and maintain a robust incident response plan that includes handling sophisticated malware attacks targeting sensitive data and credentials.
Collaboration with Industry Groups: Partner with cybersecurity communities, CERTs, and government agencies to share intelligence and best practices for mitigating threats posed by advanced stealers.
Employee Awareness and Training: Conduct regular awareness programs to educate employees about phishing tactics, malware risks, and the importance of safe browsing habits.
Access Management: Implement strict access controls, applying the principle of least privilege (PoLP) to limit exposure to critical systems and sensitive data.
Vendor and Third-Party Risk Assessment: Evaluate third-party software, plugins, and extensions for potential vulnerabilities that could be exploited by malware like Flesh Stealer.
Backup Policy Enforcement: Ensure regular and secure backups of critical data to enable recovery in case of data exfiltration or ransomware attacks.
Endpoint Protection and Monitoring: Deploy advanced endpoint detection and response (EDR) tools to monitor, detect, and mitigate malware activities such as process injection and registry modifications.
Browser and Extension Hardening: Disable unnecessary browser extensions, enforce the use of vetted plugins, and restrict downloads from untrusted sources.
Behavioral Analytics: Leverage machine learning-based tools to detect anomalous behavior, such as unauthorized data access or system modifications, indicative of malware activities.
Anti-Phishing Mechanisms: Employ email filters, sandboxing, and DNS filtering to block phishing attempts that distribute malware like Flesh Stealer.
Credential Hygiene: Enforce multi-factor authentication (MFA) and encourage users to avoid reusing passwords across platforms.