



At CYFIRMA, we provide cutting-edge insights into the ever-evolving tactics of cybercriminals targeting organizations and individuals. This analysis has uncovered a sophisticated malware campaign exploiting a leading Indian bank’s brand through fraudulent mobile applications. Distributed via phishing links, and social engineering, these fake apps closely mimic legitimate Bank apps, tricking users into revealing credentials, financial data, and personal details. The malware employs advanced evasion techniques, including encrypted communication with Command-and-Control (C2) servers, dynamic payload execution, and runtime behaviour alterations, enabling it to bypass detection by security systems.
The attackers’ primary motive is financial gain through large-scale credential theft, unauthorized transactions, and the sale of stolen banking and personal data on darknet forums. Additionally, the campaign may serve as a stepping stone for broader fraud operations, enabling threat actors to launder money, conduct identity theft, and exploit compromised accounts for further malicious activities.
Our research delves into the threat actors’ tactics, including the use of Telegram bots, SQL injection attacks, and XOR encryption to enhance operational complexity. The report highlights the significant impact of these campaigns and provides actionable recommendations such as advanced threat monitoring, vulnerability patching, and user education to mitigate risks. With these insights, CYFIRMA aims to empower organizations to detect emerging threats and protect customers from sophisticated banking malware attacks.
In today’s digital age, banking mobile applications have become integral to managing financial transactions, offering unparalleled convenience and accessibility. However, this widespread adoption has also attracted the attention of cybercriminals, making these applications prime targets for exploitation. Recently, threat actors have intensified their efforts to compromise financial security by leveraging the bank’s brand through fraudulent mobile applications designed to mimic the legitimate apps.
One such threat, Trojan.rewardsteal/joxpk, demonstrates the evolving sophistication of cyberattacks. Distributed via phishing campaigns and unofficial app stores, this malware not only deceives users into divulging sensitive information but also exfiltrates Personally Identifiable Information (PII), including banking credentials and card details. Utilizing advanced tactics such as string obfuscation, XOR encryption, and Telegram-based Command-and-Control (C2) mechanisms, the malware evades detection and poses a substantial risk to financial institutions and their customers.
This report explores the tactics, techniques, and procedures (TTPs) employed by the attackers, shedding light on the social engineering strategies, malware capabilities, and distribution methods. Additionally, it highlights the need for proactive measures to mitigate risks and protect users from these sophisticated threats.

• Uses both IP-based servers and Telegram bots as Command-and-Control (C2) servers.
• Employs XOR-based string obfuscation to evade detection and hinder analysis.
• Requests personal information and sensitive card details from users.
• Leaks PII, including personal details and banking credentials, exposing users to identity theft.
The screenshot below reveals the source website hosting the malicious APK.
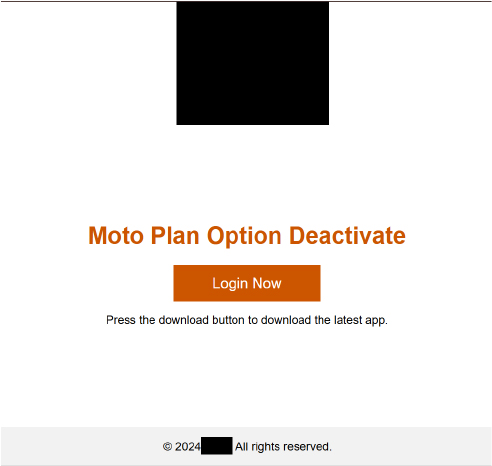
The below shows the redirects in action, highlighting the sequence of URLs or destinations that the traffic is directed to. This process can be indicative of malicious activity, as attackers often use redirects to steer users to phishing sites or to facilitate malware distribution.
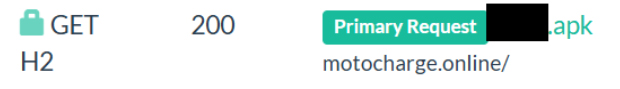
The below WHOIS details, provide information about the domain registration, ownership, and contact details. This can help identify the entity behind the domain and assess its legitimacy.
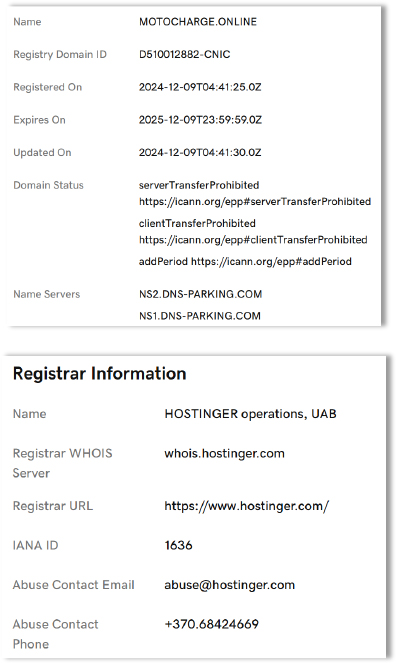
| File Name | Bank[.]apk |
| File Size | 4.67 MB |
| Signed | Signed |
| MD5 Hash | 9d0460f69ed87ee3580c51c4b7c7ed1d |
| SHA-256 Hash | 0c874cbd38d49db0d6b24aee6c57382b1fe912158f8dcb0786933ff2c206e1c9 |
The table below covers important permissions with descriptions that apps use for malicious activity.
| Sr.no | Permissions | Descriptions |
| 1. | RECEIVE_SMS | This permission allows the threat actor to receive and read incoming SMS messages on the device. |
| 2. | SEND_SMS | This permission allows the threat actor to send SMS messages from the device without the user’s consent. |
| 3. | READ_SMS | This permission helps the App to read and access the SMS. |
The following snippet provides clear evidence of string obfuscation, showcasing techniques to conceal the malware’s functionality and evade detection.
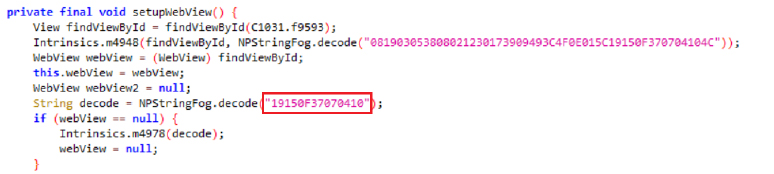
This snippet from the Obfuscated module identifies the cipher type as XOR and the key as “npmanager.” It highlights the malware’s obfuscation techniques to secure its string and evade detection.
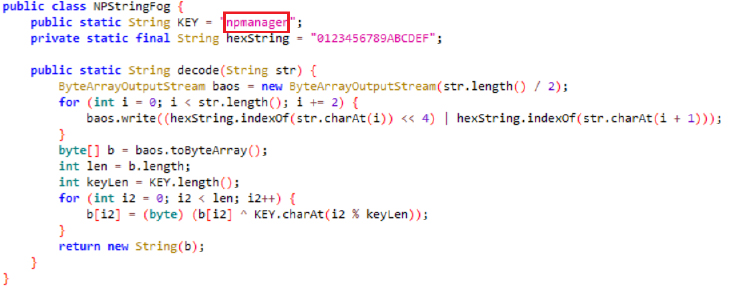
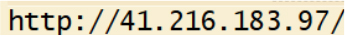
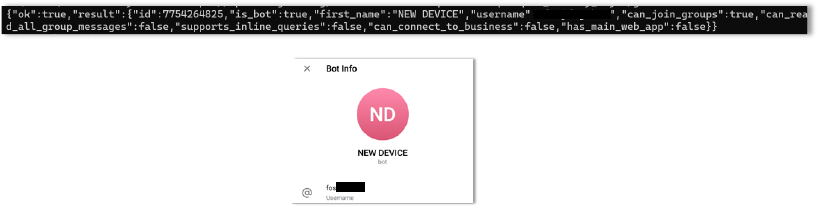
The screenshot below is from the communication servers, showcasing the infrastructure used for data exfiltration. It highlights the use of IP-based servers (41.216.183.97) and a Telegram bot (NEW DEVICE) for C2 operations, ensuring flexibility and stealth in executing malicious activities.
The decoded string reveals details of the communication servers, highlighting their use of IP-based infrastructure for C2 operations, enabling data exfiltration and stealthy malware activity.
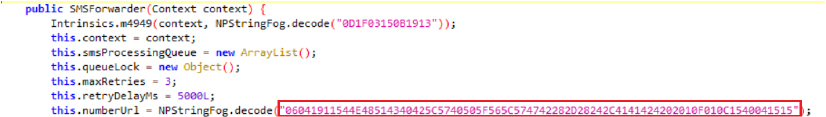
The string below indicates that the app communicates through Telegram bots, enabling remote control and facilitating data exfiltration. This method allows the attackers to maintain flexibility in their command-and-control infrastructure, bypassing traditional security measures. Using Telegram bots, the malware can receive instructions and send stolen data without raising suspicion, making it more difficult for security systems to detect and block the communication.
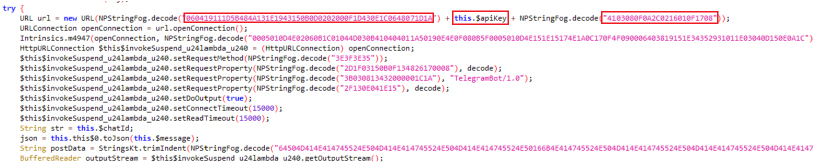


This snippet is using WebView, a component that allows embedding web content within a mobile application. It facilitates the display of HTML pages, enabling seamless integration of web-based content into native apps.
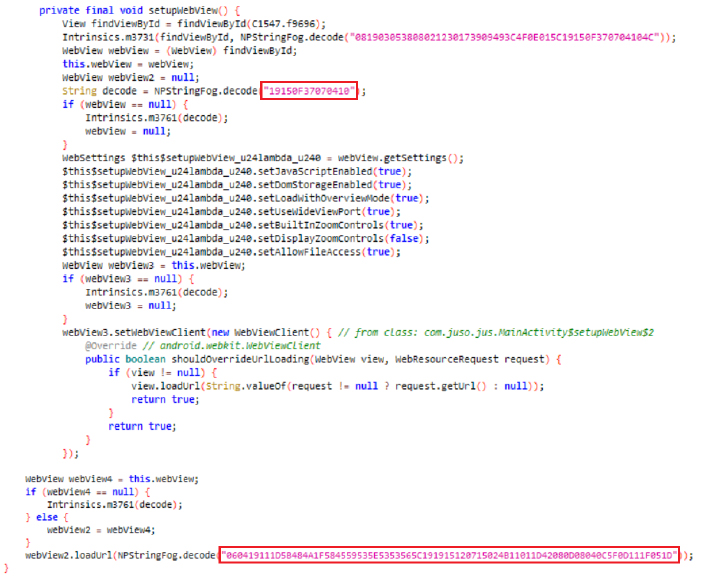
The decoded string is a URL pointing to a cloud-based website-building platform that allows users to create and host websites without needing advanced technical skills. Commonly used for legitimate purposes, it has also been exploited by attackers to create phishing sites, host malware, and deceive users. Due to the simplicity of setting up websites malicious actors can easily create convincing sites to impersonate trusted services and steal sensitive information. This highlights the need for caution when interacting with URLs from unknown sources, as they could lead to compromised or fraudulent sites.
The page below is a snapshot of the communication server, displaying the IP-based infrastructure used for managing the malware’s command-and-control operations. This server facilitates data exfiltration and the execution of remote commands, allowing attackers to maintain control over infected devices.
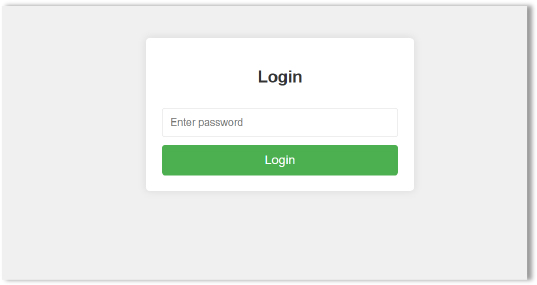
The snapshot highlights a high-severity vulnerability in the C2 server, identified as CVE-2011-2688. This vulnerability lies within the mysql/mysql-auth.pl script of the mod_authnz_external module (version 3.2.5 and earlier) for the Apache HTTP Server. It is an SQL injection issue that allows remote attackers to execute arbitrary SQL commands through the user field, potentially compromising the server and enabling unauthorized access.
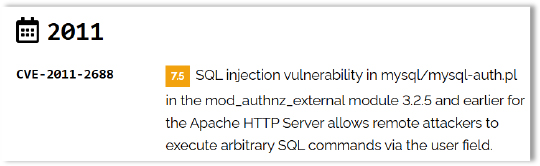
The screenshot below reveals the password of the C2 server, which has been extracted through the exploitation of CVE-2011-2688. This vulnerability, an SQL injection flaw in the mysql/mysql-auth.pl script of the mod_authnz_external module, allows attackers to execute arbitrary SQL commands, enabling them to retrieve sensitive credentials such as the C2 server’s password.

The screenshot below shows the extracted password of the C2 server. Using the retrieved credentials, we accessed the server to investigate its control mechanisms, uncovering its potential to expose sensitive PII and critical data.
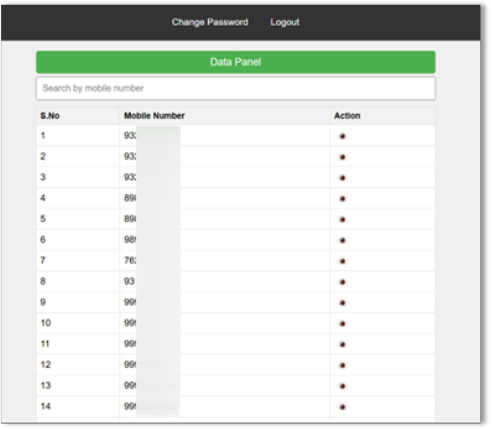

The Trojan.rewardsteal/joxpk malware was traced back to the suspicious website motocharge[.]online, which hosts fraudulent versions of the bank’s mobile banking app. This site, part of a broader attack targeting users of the banking app, distributes malware through phishing links often disguised as ads or app download prompts. The malware collects sensitive data, including login credentials, and communicates with Telegram bots for data exfiltration and command execution. The C2 server associated with the malware is also vulnerable to an SQL injection (CVE-2011-2688), which could allow attackers to extract critical information, such as server passwords. This indicates a multi-layered approach by the threat actor to maintain control over infected devices.
In conclusion, the threat actor behind the malware campaign is leveraging sophisticated techniques, including phishing, obfuscation, and exploiting server vulnerabilities to avoid detection. The attack primarily uses the motocharge[.]online site and Telegram bots for distribution and data theft, highlighting the dangers of cybercriminals exploiting trusted platforms to target users. The campaign’s complexity calls for proactive defense measures from both security teams and users to mitigate risk.
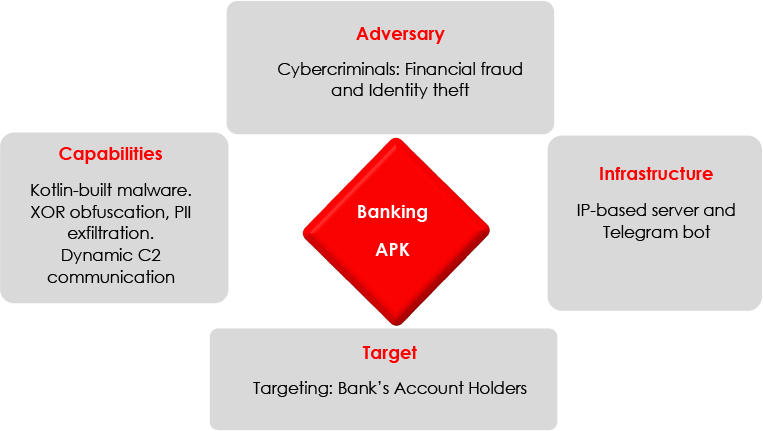
The external threat landscape continues to evolve, with cybercriminals employing increasingly sophisticated techniques to exploit vulnerabilities and compromise user data. The case of Trojan.rewardsteal/joxpk targeting Bank users through fraudulent mobile applications exemplifies the growing complexity of these threats. By leveraging tactics such as advanced malware obfuscation, SQL injection vulnerabilities, and communication through Telegram bots and IP-based servers, attackers can stealthily exfiltrate sensitive information and maintain persistent access to compromised systems.
This highlights the critical need for a proactive and multi-layered cybersecurity strategy. Organizations must continuously monitor external threats, identify vulnerabilities, and implement effective countermeasures, including patching known exploits and educating users on the risks of phishing and malicious applications. By adopting a comprehensive approach to external threat management, organizations can reduce their exposure to cyber risks, safeguard sensitive data, and ensure the security and trust of their users.
YARA Rule:
rule Bank_Fraud_App
{
meta:
author = “CRT”
description = “Detects fraudulent mobile apps impersonating Bank”
date = “2025-02-04”
severity = “High”
category = “Banking Malware”
strings:
$telegram_bot = “/bot” ascii nocase
$hex_pattern = { 6c 43 6c 43 6c 20 63 72 65 64 69 74 20 63 61 72 64 }
$wix_webview = “wixsite.com” ascii nocase
condition:
any of ($telegram_bot, $hex_pattern, $wix_webview)
}
Strategic Recommendations:
Management Recommendations:
Tactical Recommendations:
MITRE ATT&CK MAPPING (MOBILE)
| Tactic | Technique | ID | Description |
| Execution | Scheduled Task/Job | T1603 | Adversaries create or modify scheduled tasks for execution. |
| Persistence | Foreground Persistence | T1541 | Malware remains active in the foreground to ensure persistence. |
| Privilege Escalation | Scheduled Task/Job | T1603 | Using scheduled tasks to escalate privileges. |
| Defense Evasion | Hide Artifacts | T1628 | Techniques to hide malicious artifacts from detection. |
| Defense Evasion | Hide Artifacts: User Evasion | T1628.002 | Evading detection by imitating legitimate user behavior. |
| Credential Access | Clipboard Data | T1414 | Capturing sensitive data copied to the clipboard. |
| Discovery | System Network Configuration Discovery | T1422 | Identifying network configurations and connected devices. |
| Collection | Clipboard Data | T1414 | Harvesting clipboard data for sensitive information. |
| Impact | Data Manipulation | T1641 | Modifying data to disrupt operations or mislead users. |
| Impact | Data Manipulation: Transmitted Data Manipulation | T1641.001 | Altering transmitted data for malicious purposes. |
| No | Indicators of Compromise (IOCs) | Type | Remarks |
| 1 | https[:]//motocharge[.]online/ | Domain | Source |
| 2 | 41[.]216[.]183[.]97 | IP | C2 |
| 3 | 92[.]113[.]19[.]132 | IP | Source |
| 4 | 0c874cbd38d49db0d6b24aee6c57382b1fe912158f8dcb0786933ff2c206e1c9 | SHA-256 | SHA256 |