



The cross-site request forgery (CSRF) vulnerability discovered in WordPress Quiz and Survey Master 8.0.8 is a severity(high) security flaw that could potentially compromise user data and the security of the application. CSRF attacks are a common type of web application vulnerability, and the popularity of WordPress makes it a frequent target for cyber-attacks. Our research confirmed the existence of the vulnerability and demonstrated how it could be exploited to perform actions on behalf of a logged-in user. To mitigate the risk of CSRF attacks, developers and organizations must implement secure coding practices, regularly test applications for vulnerabilities, and consider additional security measures such as CSRF tokens or multi-factor authentication. A clear policy for responsible disclosure of vulnerabilities is also essential to ensure that issues are addressed in a timely and effective manner.
The security of web applications is a critical concern for businesses and organizations of all sizes. CSRF vulnerabilities are a type of security weakness that frequently occurs and can permit attackers to deceive users into performing actions that were not intended on a specific website. The A CSRF vulnerability was identified in the WordPress Quiz and Survey Master 8.0.8 plugin, which has the potential to jeopardize the security of the application and user data. This vulnerability highlights the ongoing challenges of securing web applications in the face of evolving cyber threats. This research paper analyzes the vulnerability discovered in WordPress Quiz and Survey Master 8.0.8, examines existing research on CSRF vulnerabilities, and provides recommendations for mitigating the risk of CSRF attacks in web applications. The paper also discusses the importance of implementing secure coding practices, regularly testing applications for vulnerabilities, and having a clear policy for responsible disclosure of vulnerabilities to ensure that issues are addressed in a timely and effective manner.
Key Takeaways:
Regularly testing web applications for vulnerabilities such as CSRF.
Host a web application firewall on the perimeter of the web applications to potentially mitigate the risk of CSRF attacks.
Establishing clear policies for responsible disclosure of vulnerabilities to ensure timely and effective remediation.
Considering additional security measures such as CSRF tokens or multi-factor authentication.
Acknowledgements:
We would like to thank security researchers who discovered the vulnerability in WordPress Quiz and Survey Master 8.0.8 and reported it responsibly to the plugin developers. We would also like to acknowledge the contributions of the wider security community, whose ongoing research and advocacy for improved security practices are essential to protecting web applications and their users.
The WordPress Quiz and Survey Master 8.0.8 plugin was found to have a cross-site request forgery (CSRF) vulnerability, which allows attackers to trick users into performing unintended actions on a targeted website. Specifically, an attacker can craft a malicious link or website that, when visited by an authenticated user of the vulnerable plugin, can cause the user to execute unwanted actions on behalf of the attacker.
The CSRF vulnerability in WordPress Quiz and Survey Master 8.0.8 could potentially compromise user data or the security of the application. An attacker could, for example, create a malicious form that when submitted by a user who is authenticated in the vulnerable plugin, would cause the user’s account to perform unintended actions such as deleting or modifying data.
The vulnerability affects version 8.0.8 of the WordPress Quiz and Survey Master plugin and possibly earlier versions. It is recommended that all users of the plugin update to the latest version to mitigate the risk of CSRF attacks.
According to CISA’s Known Exploited Vulnerabilities CatLog, threat actors have historically exploited vulnerabilities in WordPress plugins to obtain initial access and move laterally within a victim’s environment. We assess that threat actors may attempt to exploit this vulnerability in the near term to obtain initial access to WordPress Quiz and Survey Master 8.0.8 installations, potentially compromising user data and the security of affected websites. This is due to the ease of exploitation and the prevalence of affected installations within WordPress environments. It is important for users to update to the latest version of the plugin and implement additional security measures such as CSRF tokens to mitigate the risk of exploitation.
The CYFIRMA research team analysed different methods of exploiting CVE-2023-0292. We have setup our own lab for analysing the vulnerability.
We have installed Quiz and Survey Master version 8.0.8 which was our scope for this research.
After installing the plugin, a quiz was created that allows users to answer questions and upload media. This feature provides an interactive and engaging experience for the user by allowing them to not only answer questions but also to provide multimedia responses.
The creation of the quiz likely involved setting up a series of questions, along with a system for receiving user responses. The addition of media upload functionality allows users to supplement their answers with visual or audio content, such as images, videos, or audio recordings. Refer Figure 2.0
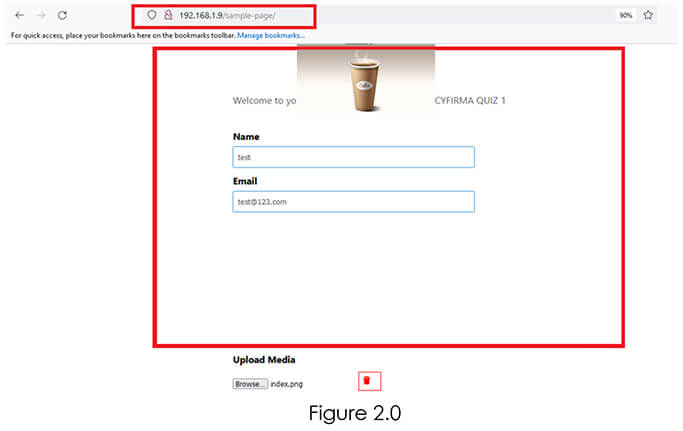
Once the user has selected a media file, the “Delete” icon will become visible, providing the user with the option to delete the file if needed. In this scenario, the “Delete” icon is displayed to the right-hand side of the “Browse” button, which allows the user to select and upload media files.
Next, we have opened the Burp Suite Pro to Intercept the requests on the page.
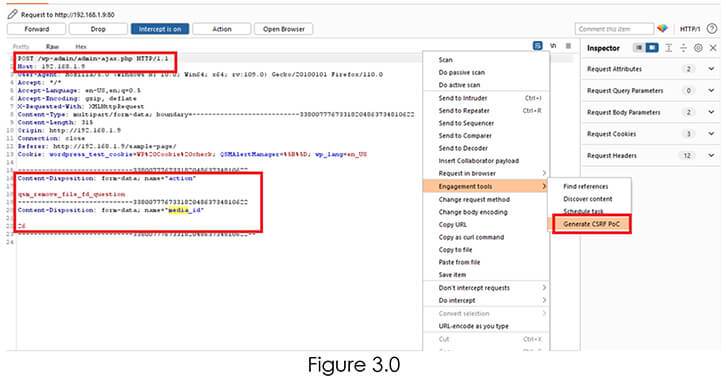
After Clicking the Delete Icon we got the response Refer Figure 3.0.
As part of the file upload feature, Quiz and Survey Master provided file deletion functionality to remove any files that were uploaded during the quiz. This qsm_remove_file_fd_question function is registered with a regular AJAX action.
Next, we have the “media_id” parameter, it is a unique id created to every media file which is uploaded on the WordPress Instance. In our case Media id is 26. Refer Figure 3.0
To find Media id one can simply find in the WordPress Media under the Library View.
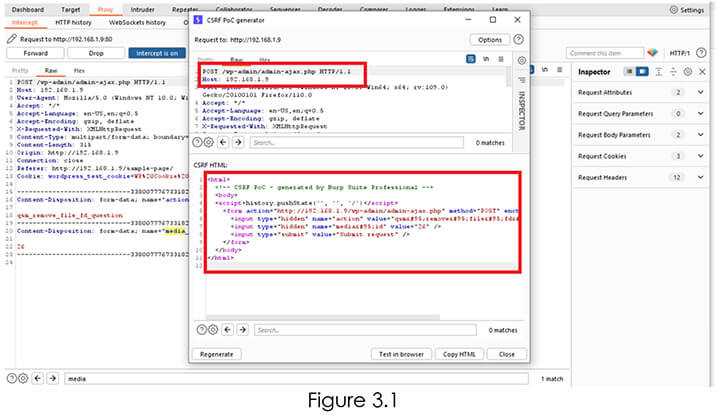
Next, we Generated a CSRF POC Delete a file Arbitrary with media_id with value 26 and saved the file and Exploit.html Refer Figure 3.1.
But before running the exploit.html we have opened the uploaded media file on clicking on “Click here to view” button on the quiz page which gets visible after quiz is submitted Refer Figure 3.2.
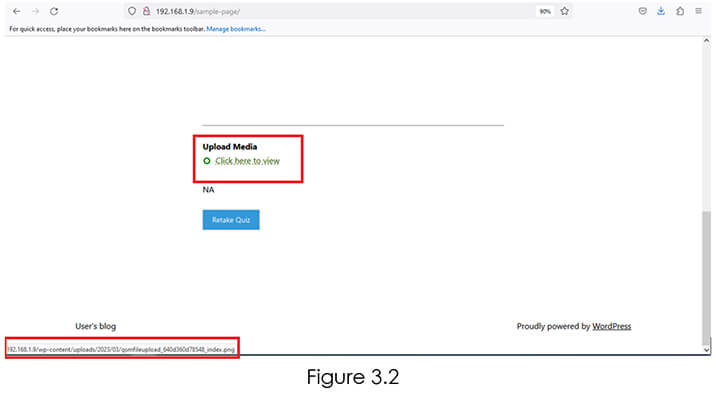
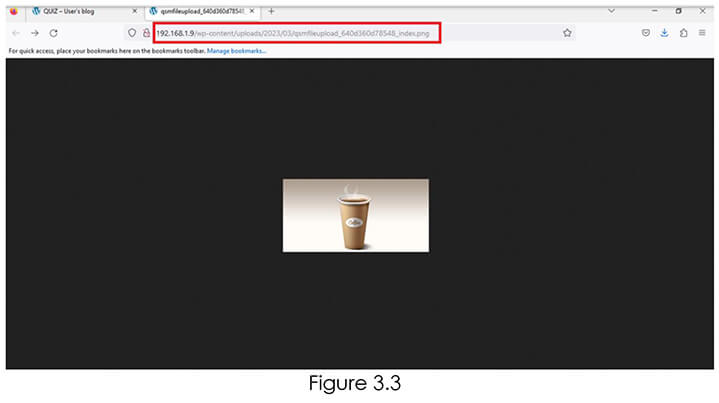
Now as we can see in Figure 3.3, we have the URL of media where it is uploaded.
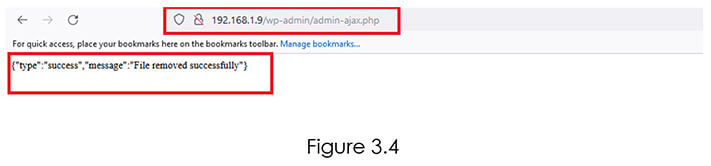
Now as we know the URL where the file is uploaded, we have fired the Exploit.html on a browser where no user is logged in and we got a response {“type”:” success”,” message”:” File removed successfully”}. Refer Figure 3.4.
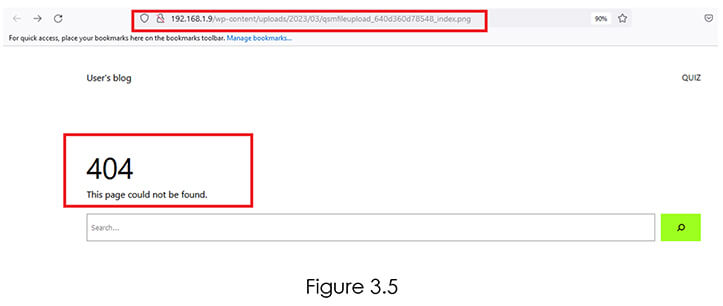
Next to check the file whether media was deleted, we have used the URL address for media_id 26 and therefore no file was present. Refer Figure 3.5.
The WordPress Quiz and Survey Master 8.0.8 Cross Site Request Forgery (CSRF) vulnerability can potentially impact websites using this plugin worldwide. However, the vulnerability is more likely to be exploited by threat actors targeting websites hosted in regions with a higher concentration of WordPress users, such as North America, Europe, and Asia-Pacific.
The vulnerability in WordPress Quiz and Survey Master 8.0.8 plugin can potentially impact websites in any industry using this plugin for conducting quizzes and surveys. However, the vulnerability is more likely to be exploited by attackers targeting industries that require frequent user engagement through surveys and quizzes, such as education, media, and entertainment.
The vulnerability in WordPress Quiz and Survey Master 8.0.8 plugin is related to Cross Site Request Forgery (CSRF) attacks. These types of attacks can be launched on any website that is vulnerable to this kind of attack. However, the WordPress platform is particularly vulnerable to these attacks due to its popularity and the large number of plugins available that can introduce new vulnerabilities. Therefore, websites using WordPress, particularly those using the Quiz and Survey Master 8.0.8 plugin, are at risk of being targeted by attackers looking to exploit this vulnerability.
Mitigation of the WordPress Quiz and Survey Master 8.0.8 CSRF vulnerability can be achieved by updating to the latest version of the plugin, which includes a patch for the issue. It is recommended that all users of the plugin update as soon as possible to ensure that their installations are protected from potential attacks.
By implementing these measures, website owners and administrators can significantly reduce the risk of CSRF attacks and protect their users’ data and the security of their websites.
From underground forums, CYFIRMA Research team has observed that unknown hackers are selling zero-day exploits for WordPress plugins.
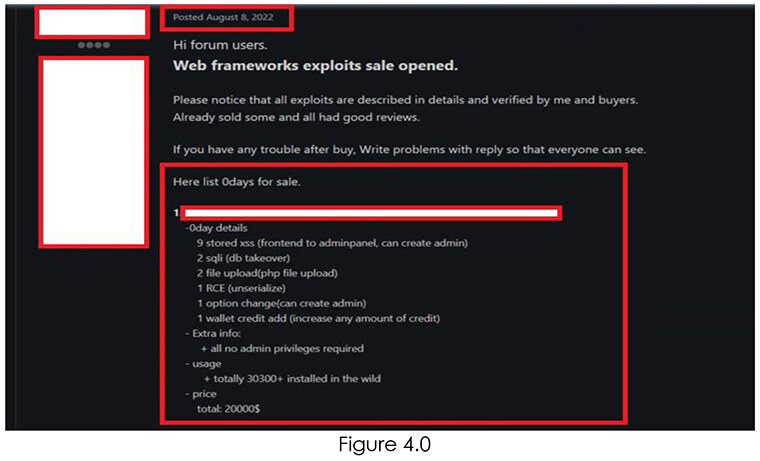
Organizations and individuals using WordPress are advised to remain vigilant and take proactive measures to protect their websites from potential attacks. This includes regularly updating WordPress and all associated plugins, using strong and unique passwords, and implementing additional security measures such as two-factor authentication and web application firewalls. It is also recommended to monitor underground forums and security news outlets to stay informed about emerging threats and vulnerabilities.
After conducting a thorough analysis of the CVE-2023-0292 WordPress Quiz and Survey Master 8.0.8 CSRF Vulnerability, it can be concluded that this vulnerability poses a significant threat to the security of WordPress websites that use the outdated version of the use the Quiz and Survey Master plugin.
This vulnerability allows attackers to perform unauthorized actions on behalf of the victim user, which can include deleting important data. The exploit is triggered when a user is tricked into clicking on a specially crafted link that executes the malicious action without the user’s knowledge or consent.
The vendor of the Quiz and Survey Master plugin has released a patch for this vulnerability, which users are strongly advised to apply as soon as possible. It is also recommended that users regularly update their WordPress plugins and themes, keep their WordPress installation up to date, and use strong and unique passwords to minimize the risk of attacks. As of 23rd March 2023, there are no internet facing servers that are vulnerable to this CVE ID (Source: OSINT).
The CVE-2023-0292 WordPress Quiz and Survey Master 8.0.8 CSRF Vulnerability is a serious security issue that underscores the importance of maintaining strong security practices on WordPress websites. By staying vigilant and taking proactive steps to secure their websites, WordPress users can mitigate the risk of falling victim to attacks that exploit this vulnerability or other security weaknesses.