



The PowerPress plugin, which allows WordPress users to publish and manage podcasts, was found to contain a stored Cross-Site Scripting (XSS) vulnerability. The vulnerability allowed authenticated threat actors with contributor-level permissions or higher to inject malicious web scripts into pages, using the plugin’s shortcode, potentially leading to the theft of sensitive information, manipulation of site content, or redirection of users to malicious websites. The vulnerability was fully addressed in version 10.0.2 of the plugin, the latest version is 10.0.7. and all Wordfence users are fully protected against it. However, users are urged to update their sites to the latest patched version of PowerPress as soon as possible to ensure continued security. The vulnerability was disclosed responsibly by the Wordfence Threat Intelligence team, and the PowerPress development team responded swiftly with a patch release.
Cross-Site Scripting (XSS) is one of the most common and dangerous web application vulnerabilities, which allows attackers to inject malicious scripts into a web page, viewed by other users. Blubrry’s PowerPress plugin is a popular WordPress plugin used for managing and publishing podcasts. Unfortunately, a stored XSS vulnerability was discovered in PowerPress <= 10.0 by the Wordfence Threat Intelligence team on April 5, 2023. This vulnerability enables attackers with contributor-level permissions or higher to inject malicious web scripts into pages using the plugin’s shortcode. The vulnerability was due to the insecure implementation of the plugin’s shortcode functionality, which allows for the injection of arbitrary web scripts into pages. The powerpress_shortcode_handler function did not adequately sanitize user- supplied input, and several functions (for various podcast player options) that use the shortcode attributes, did not adequately escape output. Once a script is injected, it will execute each time a user accesses the affected page. This could potentially result in sensitive information being stolen, manipulation of site content, or redirection to malicious websites. Blubrry was promptly contacted on April 6, 2023, and they released a patch on April 10, 2023. All Wordfence users, including those running Wordfence Premium, Wordfence Care, and Wordfence Response, as well as sites still running the free version of Wordfence, are fully protected against this vulnerability. Users of PowerPress plugin are urged to update their sites with the latest patched version of PowerPress, version 10.0.7 at the time of this writing, as soon as possible. This research highlights the importance of timely patching and the need for secure coding practices to prevent such vulnerabilities.
Key Takeaways:
Acknowledgements:
We would like to thank the researchers who discovered the vulnerability in WordPress PowerPress and reported it responsibly to the plugin developers.
Vulnerability type: Stored Cross-Site Scripting
CVE ID: CVE-2023-1917
CVSS Severity Score: 5.4
CVSS Vector: CVSS:3.1/AV:N/AC:L/PR:L/UI:N/S:U/C:L/I:L/A:N Application: PowerPress
Impact: Potentially compromise user data or the security of the application Severity: Medium
Affected Versions: <= 10.0
Fully Patched Version: 10.0.2
Latest Version: 10.0.7
The vulnerability in PowerPress plugin version <= 10.0 for WordPress allows authenticated attackers with Contributor+ role to inject malicious code via a shortcode, leading to cross-site scripting (XSS) attacks. The issue arises due to improper validation of user-supplied data. A successful exploit could enable attackers to execute arbitrary code, steal sensitive information or perform unauthorized actions on behalf of the user. It is advised to update to the latest version of the plugin to prevent such attacks.
The impact of the Cross-Site Scripting (XSS) vulnerability in WordPress PowerPress 10.0 plugin can be severe, as it can allow attackers to inject malicious code into a website and potentially compromise user data or the security of the application. This can lead to data theft, unauthorized access, and other malicious activities. It is crucial for users to update to the latest version of the plugin to avoid such security risks. Additionally, website owners should regularly monitor their websites for any suspicious activity or vulnerabilities.
The vulnerability affects version 10.0 of the PowerPress WordPress plugin and possibly earlier versions. It is recommended that all users of the plugin update to the latest version to mitigate the risk of cross-site scripting (XSS) attacks.
The CYFIRMA research team analysed different methods of exploiting CVE-2023-1917. We have setup our own lab for analysing the vulnerability.
1) Installation
We have installed Blubrry PowerPress version 9.10.5 which was our scope for this research.
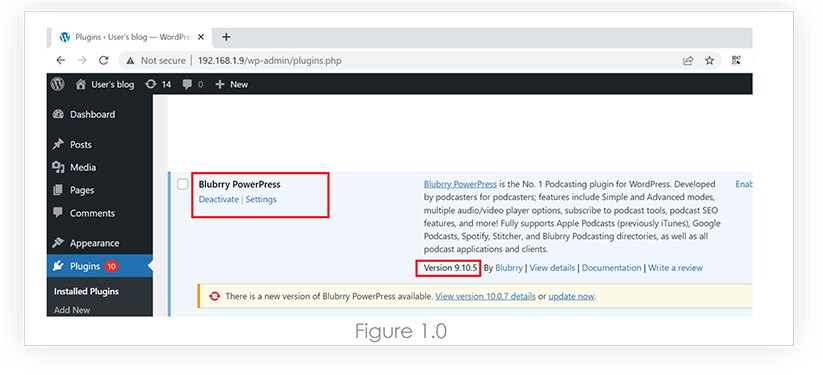
After installing the plugin, we were able to setup Podcasts and manage with the help of Powerpress shortcodes.
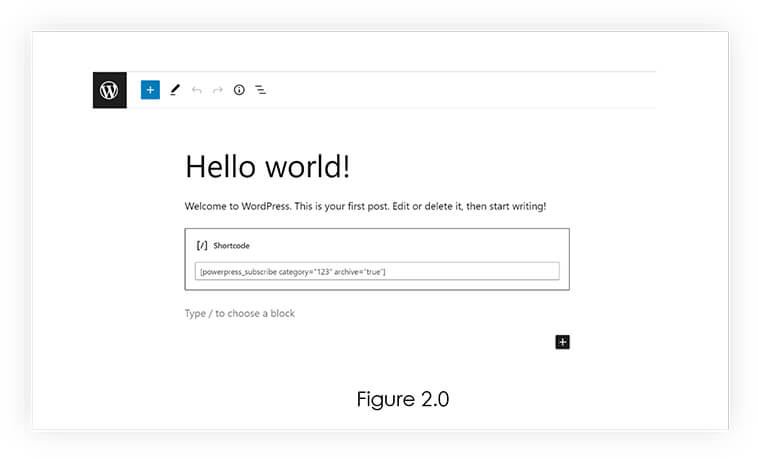
2) Setting up Podcast on Sample Page
To Create Podcast on sample page, we added the shortcode block from the wordpress editor and added the Powerpress shortcode [powerpress_subscribe category=”123″ archive=”true”]. Refer Figure 2.0.
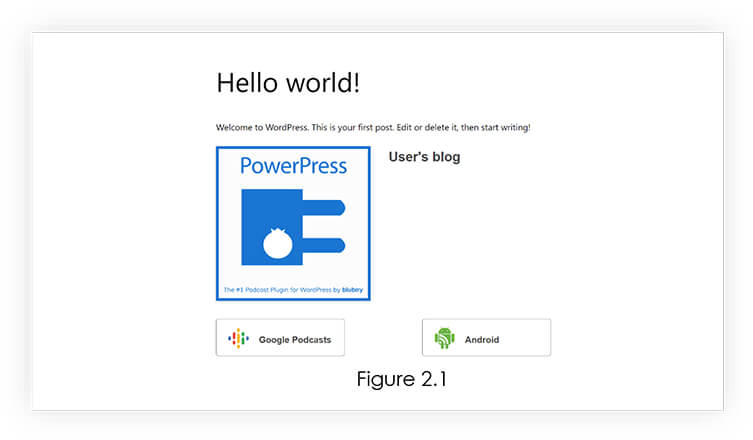
Next, we can see adding shortcodes has given output with Powerpress Podcast features. Refer 2.1.
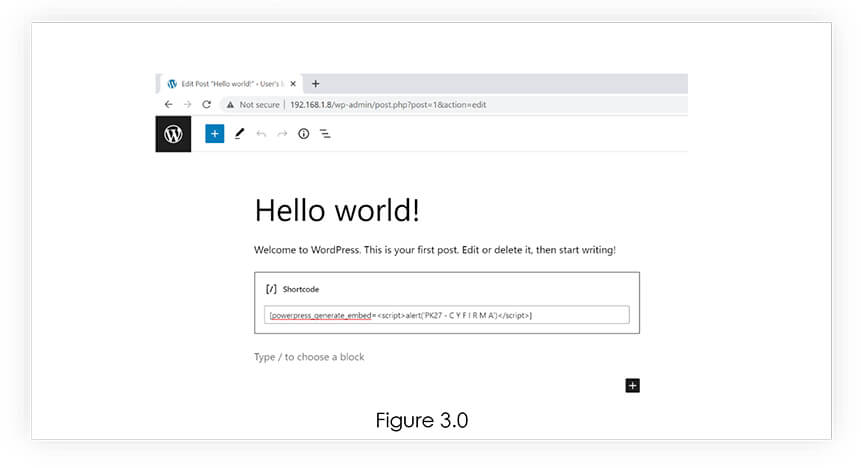
3) The Vulnerability
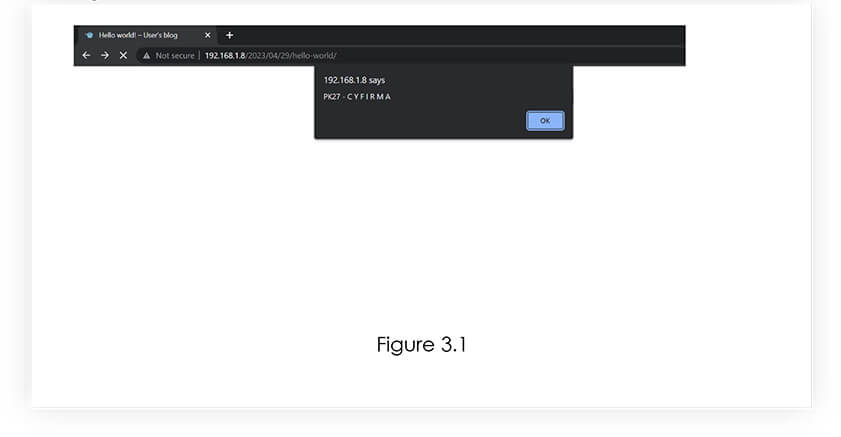
Next, we have added the [powerpress_generate_embed], which in our case is vulnerable to Stored Cross-Site Scripting. Apart from this, [powerpress_shortcode_handler] is also vulnerable for same vulnerability. Refer Figure 3.0.
To check the stored vulnerability, we have checked the page where the shortcode was applied and it was reflecting the vulnerability. Refer Figure 3.1.
Target Geography:
Based on the information available, the PowerPress 10.0 Cross-Site Scripting (XSS) vulnerability in WordPress can potentially impact websites worldwide that use the PowerPress plugin.
However, it is more likely to be exploited by attackers targeting websites hosted in regions with a higher concentration of WordPress users, such as North America, Europe, and Asia-Pacific. Websites in these regions may be at a higher risk of exploitation due to the larger pool of potential victims and a higher likelihood of finding vulnerable websites. Additionally, the severity of the vulnerability and the popularity of the PowerPress plugin may increase the likelihood of exploitation.
Target Industry:
The PowerPress 10.0 Cross-Site Scripting (XSS) vulnerability in WordPress can potentially impact websites across various industries, using the PowerPress plugin. However, the vulnerability may be more attractive to attackers targeting specific industries that regularly publish multimedia content, such as podcasters, bloggers, news media outlets, and other content creators.
These industries often use the PowerPress plugin to enhance the user experience of their multimedia content by embedding audio and video players into their websites. As a result, a successful exploitation of the PowerPress vulnerability can allow attackers to inject malicious code into the embedded players, potentially compromising the security of the website and its visitors.
Target Technology:
The PowerPress 10.0 Cross-Site Scripting (XSS) vulnerability in WordPress is related to a specific plugin, the PowerPress plugin. However, the vulnerability may not be limited to just this plugin, as WordPress itself is a popular and widely used content management system (CMS) that can be vulnerable to various types of attacks.
Due to its popularity and the large number of plugins available, WordPress websites can be targeted by attackers looking to exploit vulnerabilities in the platform or its plugins. In the case of the PowerPress vulnerability, the exploit could be used to inject malicious code into multimedia players on affected websites.
The PowerPress 10.0 Cross-Site Scripting (XSS) vulnerability in WordPress poses a significant risk to websites using the PowerPress plugin. Attackers can exploit this vulnerability to inject malicious code into multimedia players on affected websites, potentially compromising user data or spreading malware. To mitigate this risk, several measures can be taken, including:
Implementing these mitigations can help reduce the risk of exploitation for the PowerPress XSS vulnerability and improve the overall security posture of the website.
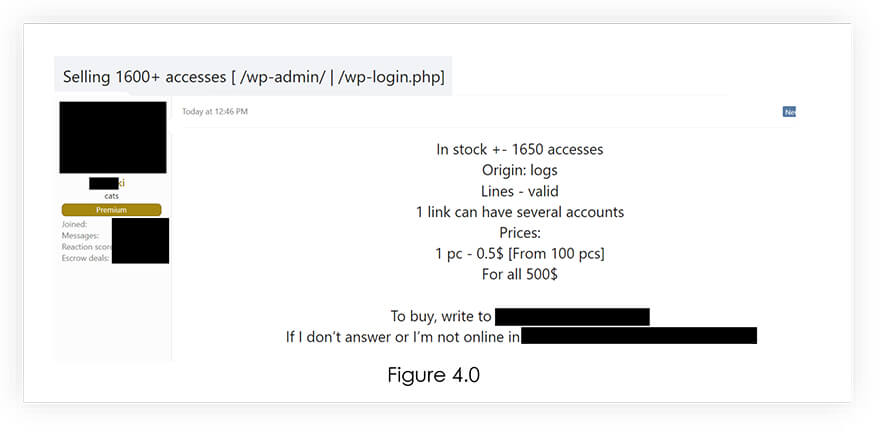
From underground forums, CYFIRMA Research team has observed that unknown hackers are selling WordPress accounts with wp-admin and wp-login access, which could help the malicious actors to gain the access and install vulnerable version of Powerpress.
Organizations and individuals using WordPress are advised to remain vigilant and take proactive measures to protect their websites from potential attacks. This includes regularly updating WordPress and all associated plugins, using strong and unique passwords, and implementing additional security measures such as two-factor authentication and web application firewalls. It is also recommended to monitor underground forums and security news outlets to stay informed about emerging threats and vulnerabilities.
To summarize, the PowerPress 10.0 Cross-Site Scripting (XSS) vulnerability in WordPress can pose a significant threat to websites, using the PowerPress plugin. Attackers can exploit this vulnerability to inject malicious code into multimedia players on affected websites, potentially compromising user data or spreading malware. However, website administrators can mitigate this risk by updating the PowerPress plugin to version 10.0.1 or later, implementing Content Security Policy (CSP) headers, using a web application firewall (WAF), regularly scanning the website for vulnerabilities, and educating website administrators and content creators on XSS risks. Implementing these best practices can improve the overall security posture of the website and reduce the risk of exploitation for this vulnerability.