



CYFIRMA’s Research team conducted a comprehensive analysis of a server-side request forgery (SSRF) vulnerability CVE-2024-21893 and a command injection vulnerability CVE-2024-21887, affecting Ivanti Connect Secure. Discovered on January 31, 2024, by Ivanti, this vulnerability carries a CVSS score of 8.2, indicating its severity. The flaw targets a server-side request forgery vulnerability within the SAML component of Ivanti Connect Secure. Given its nature, this vulnerability demands immediate attention, underscoring the necessity for swift mitigation measures across all Ivanti installations. This investigation aims to offer valuable insights into the vulnerability’s characteristics, potential ramifications, and the critical significance of promptly addressing it through patching and proactive security protocols.
CVE-2024-21893, disclosed on January 31, 2024, by Ivanti, presents a critical security threat with a CVSS score of 8.2. This vulnerability affects Ivanti Connect Secure (9.x, 22.x), Ivanti Policy Secure (9.x, 22.x), and Ivanti Neurons for ZTA. Ivanti Connect Secure (formerly known as Pulse Connect Secure), Ivanti Policy Secure, and Ivanti Neurons contain a server-side request forgery (SSRF) vulnerability in the SAML component, enabling attackers to access certain restricted resources without authentication. In containerized deployments, this may expose critical data. To exploit the SSRF vulnerability, an attacker crafts a SOAP envelope, containing a malicious signature with a Retrieval Method element pointing to an arbitrary URI, controlled by the attacker. This URI triggers an HTTP GET request to a specified endpoint, allowing the attacker to perform SSRF and a command injection vulnerability (CVE-2024-21887). Recently, CISA has added CVE-2024-21893 and CVE-2024-21887 to the list of Known Exploited Vulnerabilities, emphasizing the need for immediate action to address and remediate this security threat.
Key Takeaways:
Acknowledgements:
The CYFIRMA Research team acknowledges security researchers, who responsibly disclosed this vulnerability.
Vulnerability Type: Server-side request forgery Vulnerability
CVE ID: CVE-2024-21893
CVSS Severity Score: 8.2 (HIGH)
Application: Ivanti
Impact: Allows unauthenticated attackers SSRF Vulnerability
Severity: High
Affected Versions: This vulnerability affects Ivanti Connect Secure (9.x, 22.x), Ivanti Policy Secure (9.x, 22.x)
Patch Available: Yes
The analysis provides a detailed overview of a series of vulnerabilities affecting Ivanti Connect Secure appliances, including an SSRF vulnerability (CVE-2024-21893), discovered in the Security Assertion Markup Language (SAML) component. This SSRF vulnerability allows attackers to bypass previous mitigations and exploit other vulnerabilities, such as an authentication bypass (CVE-2023-46805) and command injection vulnerability (CVE-2024-21887), ultimately leading to unauthenticated remote code execution.
The vulnerabilities in Ivanti Connect Secure, including command injection vulnerability (CVE-2024-21887) and SSRF (CVE-2024-21893), pose a severe risk, enabling unauthorized access, remote code execution, and manipulation of server requests. Exploitation could lead to data breaches, service disruption, and compromise of critical systems, underscoring the urgent need for applying available patches and mitigations to safeguard affected appliances.
The SAML component of Ivanti Connect Secure (9.x, 22.x), Ivanti Policy Secure (9.x, 22.x) and Ivanti Neurons.
Endpoint service devices are crucial components of modern business operations, providing trusted access to an organization’s sensitive information, including personal data, financial details, and proprietary intellectual assets. However, as the use of these services grows, so does the potential for exploitation by malicious actors.
APT5 exploited a zero-day vulnerability in Citrix ADC and Gateway devices (CVE-2023-3519, CVSS: 9.8), allowing pre-authenticated remote code execution on vulnerable devices. The exploitation of FortiOS SSL-VPN (CVE-2022-42475, CVSS: 9.8) has been linked to a Chinese threat actor, which had used it as a zero-day in attacks, aimed at government and other types of organizations. A more recent addition to this concerning trend is the vulnerability identified in Ivanti (CVE-2023-21893; CVSS 8.2). Particularly concerning is the active involvement of threat actor groups such as Volt Typhoon and BRONZE, who have demonstrated a keen interest in exploiting these vulnerabilities. This also underscores the heightened attention from suspected Chinese threat actors.
CISA has issued advisories regarding the activities of the Volt Typhoon threat actors, who frequently target vulnerabilities in networking appliances. These appliances include those manufactured by Fortinet, Ivanti Connect Secure (previously Pulse Secure), NETGEAR, Citrix, and Cisco [T1190]. The threat actors are known to use publicly available exploit code for known vulnerabilities [T1588.005], but they are also skilled at identifying and exploiting zero-day vulnerabilities [T1587.004].
Is there already an exploit tool to attack this vulnerability?
Yes, the availability of public proof-of-concept (PoC) exploit code for an Information Disclosure Vulnerability is a serious concern, as it increases the likelihood of malicious actors exploiting the flaw to gain unauthorized access to sensitive information. The fact that PoC code is being shared on Telegram channels further exacerbates the situation, as it makes it even easier for attackers to obtain and utilize the exploit.
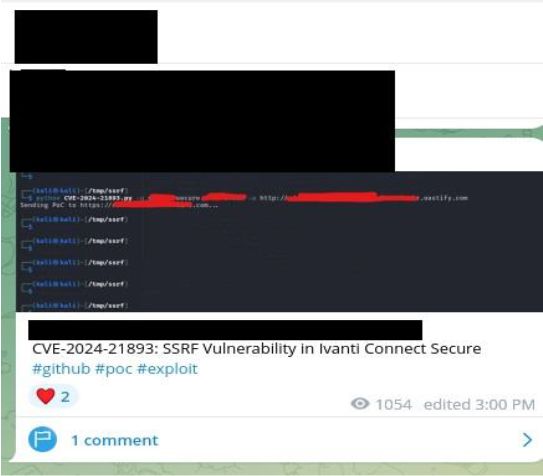
Has this vulnerability already been used in an attack?
Evidence from underground forums indicates active exploitation of the CVE-2023- 21893 vulnerability, particularly targeting educational institutions. Researchers have identified 1,211 IPs involved in exploitation attempts, with 56 unique IPs engaged in these activities over the past 30 days.
Are hackers discussing this vulnerability in the Deep/Dark Web?
Cybersecurity researchers warn of potential CVE-2023-49103 exploitation chatter on the Deep/Dark Web, originating from locations like the US, Russia, Germany, and the Netherlands. Continuous monitoring of underground channels remains critical to detect this global threat.
What is the attack complexity level?
The attack complexity level for CVE-2023-21893 in Ivanti Connect Secure NVD is assessed as high.
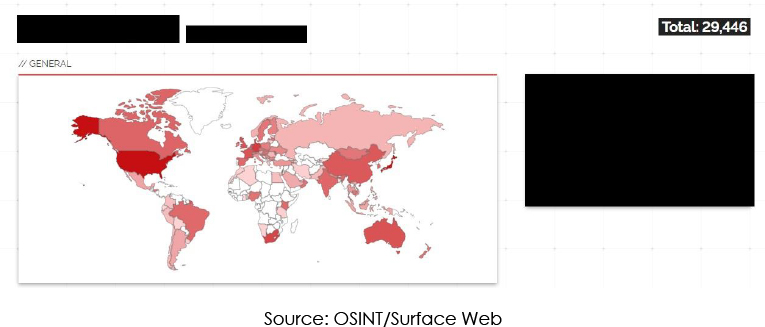
Our investigation revealed a critical unauthenticated information disclosure vulnerability affecting Ivanti Connect Secure. Our research uncovered a staggering number of 29,446 publicly accessible Ivanti Connect Secure (ICS) and Ivanti Policy Secure gateways that may be vulnerable to this flaw.
Researchers have unveiled a series of exploits targeting Ivanti Connect Secure appliances, exploiting multiple vulnerabilities to achieve unauthenticated remote code execution (RCE). Initially, an authentication bypass flaw (CVE-2023-46805) is combined with a command injection vulnerability (CVE-2024-21887) to gain an unauthenticated RCE. Subsequently, a new Server-Side Request Forgery (SSRF) vulnerability (CVE-2024-21893) is leveraged to circumvent the mitigation measures implemented for the initial exploit chain. The /dana-ws/saml20.ws endpoint was found to be accessible without authentication. Crafting an XML SOAP envelope with a malicious signature to trigger SSRF, the XML payload manipulates the KeyInfo element to initiate an HTTP GET request to a controlled server, further leveraging the SSRF to exploit the command injection vulnerability (CVE-2024-21893) by modifying the SSRF URI to target the vulnerable /api/v1/license/keys-status endpoint.
The SSRF vulnerability resides in the SAML component of Ivanti Connect Secure and is triggered by crafting a malicious XML SOAP envelope. This envelope contains a signature with a Retrieval Method element, specifying an arbitrary URI, leading to SSRF when processed.
The SSRF is further exploited to make an HTTP GET request to a locally-bound service, vulnerable to command injection, thereby achieving unauthenticated RCE. Ivanti has released mitigations and patches to address these vulnerabilities, emphasizing the critical need for prompt application to safeguard against exploitation. This analysis underscores the significance of layered security measures and proactive vulnerability management in mitigating the risk posed by sophisticated exploit chains.
With the SSRF vulnerability in Ivanti Connect Secure, organizations can consider implementing additional layers of security, such as network segmentation to restrict access to sensitive resources. Employing robust access controls and authentication mechanisms can also help prevent unauthorized access to critical systems. Additionally, keeping software components up to date with the latest security patches and versions, including the xmltooling library, is crucial to addressing known vulnerabilities. Regular monitoring and logging of network traffic can aid in detecting and responding to suspicious activities, providing an additional layer of defense against potential exploitation attempts.
Target Geography: Organizations worldwide that rely on Ivanti Connect Secure, particularly those using the affected versions susceptible to CVE-2024-21887 and CVE-2024-21893, are at risk. This vulnerability has a broad geographical impact, affecting regions like North America, Central Europe, and Asia, especially where the SAML component of Ivanti Connect Secure is prevalent. Regardless of their location, organizations globally could face exploitation risks if they employ the affected versions of Ivanti Connect Secure.
Target Industry: The CVE-2024-21887 and CVE-2024-21893 vulnerability found in Ivanti Connect Secure presents a significant threat to organizations spanning multiple sectors, such as healthcare, finance, government, telecommunications, and more, which heavily rely on Ivanti Connect Secure for their automation needs. Malicious actors equipped with knowledge of this vulnerability might strategically target specific industries, considering the perceived value of the data or services facilitated by Ivanti Connect Secure. Industries dealing with sensitive information or relying extensively on Ivanti Connect Secure for automation could become prime targets for exploitation.
Target Technology: The vulnerability analysis exposes a severe SSRF weakness (CVE-2024-21893) and command injection vulnerability (CVE-2024-21887) within Ivanti Connect Securer’s SAML handling, enabling attackers to sidestep prior mitigations and execute arbitrary code remotely. Exploitation not only jeopardizes the integrity of Ivanti Connect Secure instances but also poses a broader threat to interconnected systems and infrastructure. Given the potential ripple effect on an organization’s technological ecosystem, implementing robust mitigation strategies becomes imperative to safeguard against widespread compromise.
Presently, discussions about this vulnerability are underway, yet there’s no evidence or suggestion of any exploits being offered for sale on the forum.

In conclusion, the SSRF vulnerability identified in Ivanti Connect Secure poses a significant risk to organizations, allowing threat actors to bypass security measures and potentially gain unauthorized access to sensitive systems. The exploitation of this vulnerability highlights the importance of thorough security assessments, regular software updates, and robust access controls. Organizations must remain vigilant in identifying and mitigating such vulnerabilities to safeguard their networks and data against malicious activities. By implementing comprehensive security measures and staying informed about emerging threats, organizations can effectively mitigate the risks associated with SSRF vulnerabilities and enhance their overall cybersecurity posture.