


Energy Superpower: As the world’s largest oil exporter, any disruption to Saudi energy assets can ripple across global markets, making them a high-value target for both state-sponsored and financially motivated attackers.
Geopolitical Positioning: Its leadership role in the Gulf, close ties to Western allies, and rivalry with Iran place it at the center of cyber operations from adversarial nation-states and proxy groups.
Vision 2030 & Digital Expansion: The accelerated shift toward smart cities, e-government, and digital finance increases the attack surface, especially in sectors like defense, finance, and infrastructure.
Symbolic and Strategic Impact: Hitting Saudi Arabia generates maximum attention. It signals capability, disrupts regional stability, and offers adversaries both tactical and propaganda wins.
Wealth and Investment Influence: The Kingdom’s sovereign wealth, major global investments, and strategic role in OPEC make it a magnet for cybercriminals, fraud schemes, and espionage.
Military and Defense Modernization: As Saudi Arabia expands its defense capabilities and regional military operations, its networks attract the attention of both espionage-focused APTs and disruptive campaigns.
Hosting Critical Global Events: G20, FII, World Expo, bids major global events hosted or backed by Saudi Arabia invite increased cyber activity by groups seeking visibility or disruption.
Technology Partnerships with the West: Deepening partnerships with U.S. and European tech firms create both dependency and risk, exposing the Kingdom to global supply chain and third-party compromises.
Regional Rivalries: Ongoing tension with Iran fuels a steady stream of state-linked cyber operations targeting Saudi energy, government, and defense sectors.
Proxy Conflicts: Saudi involvement in Yemen and broader Gulf security issues attracts retaliatory cyberattacks from Iranian-aligned groups and ideologically driven actors.
Alignment with Western Powers: Strong ties with the U.S., UK, and Israel position Saudi Arabia as a cyber target for adversaries seeking to undermine Western influence in the region.
Normalization with Israel (Ongoing Dynamics): Even indirect engagement triggers threats from hacktivist and state-aligned groups hostile to normalization efforts.
Spillover from Israel–Iran Conflict: The June 2025 strikes between Israel and Iran escalated cyber activity across the region. Iranian-linked actors and sympathetic hacktivists increased disruptive operations, raising Saudi Arabia’s cyber exposure even without direct involvement.
Critical Energy Role in Global Politics: Saudi control over global oil supply chains makes it a high-impact cyber target during geopolitical or economic disputes.
Leadership in the Islamic World: As the de facto leader of the Sunni bloc, Saudi Arabia faces cyber pressure from actors seeking to challenge its political or religious authority.
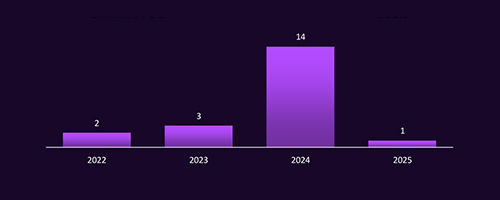
CYFIRMA observed a sharp escalation in campaigns targeting Saudi Arabia, peaking at 14 in 2024 – more than quadruple the previous year. This surge aligns with heightened geopolitical tensions and increased targeting of Saudi energy, government, and defense sectors. The early drop in 2025 should not be seen as a reduced threat; it may reflect evolving tactics, including stealthier, long-term intrusions. The data underscores the need for proactive intelligence and adaptive defenses to counter shifting threat actor strategies.
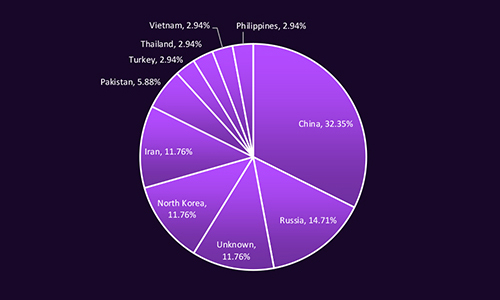
CYFIRMA observed that threat actors targeting Saudi Arabia originate predominantly from China (32.35%), followed by Russia (14.71%), and key regional adversaries including Iran and North Korea (each 11.76%). The presence of actors from Pakistan, Turkey, Southeast Asia, and unidentified origins reflects both geopolitical drivers and opportunistic targeting. This mix of major state-sponsored players and emerging regional threats highlights the multifront nature of Saudi Arabia’s cyber risk landscape.
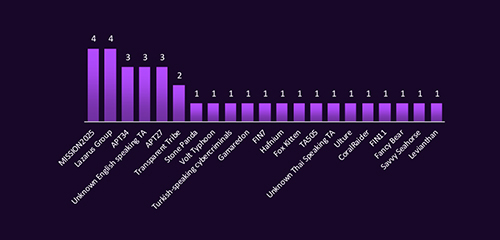
CYFIRMA observed a diverse mix of state-sponsored and financially motivated threat actors targeting Saudi Arabia, led by MISSION2025 and Lazarus Group. Prominent Chinese, North Korean, and Russian-linked APTs, along with cybercriminal groups like FIN and ransomware affiliates, reflect a blend of espionage, disruption, and financial gain motives. The breadth of actors from global APTs to unknown regional players highlights Saudi Arabia’s strategic value and the complexity of defending against multi-vector, multi-origin threats.
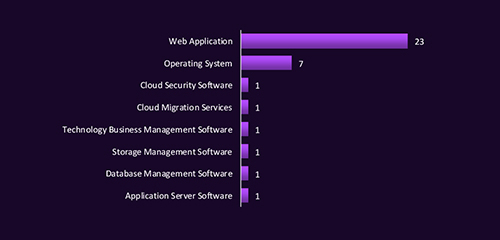
CYFIRMA observed that web applications are the most targeted technology in Saudi Arabia, accounting for over 60% of identified attacks, highlighting a critical vulnerability point for organizations. Operating systems followed as the second most attacked, with limited but notable activity against cloud, storage, and database solutions. The focus on web-facing assets aligns with threat actors’ preference for exploiting publicly accessible systems to gain initial access and pivot deeper into networks.
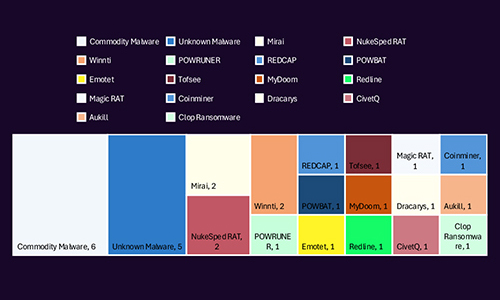
CYFIRMA observed a diverse malware ecosystem targeting Saudi Arabia, dominated by commodity malware and a significant presence of unknown strains signaling both opportunistic and sophisticated campaigns. Notable families such as Mirai, NukeSpeed RAT, and Winnti indicate a mix of botnet activity, espionage, and advanced persistent threats. The appearance of ransomware like Cl0p, alongside credential stealers and RATs, highlights multi-purpose operations aimed at disruption, data theft, and long-term infiltration.
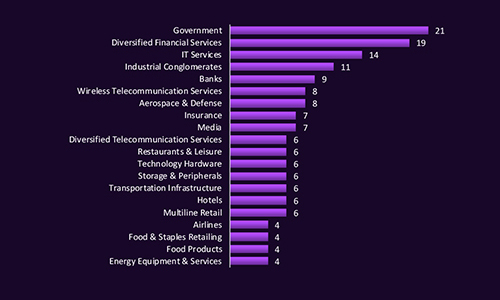
CYFIRMA observed that government and diversified financial services are the most targeted industries in Saudi Arabia, reflecting their strategic importance and high-value data. IT services, industrial conglomerates, and banks also face significant targeting, indicating a focus on sectors critical to national infrastructure and economic stability. The breadth of impacted industries from aerospace and defense to retail and transportation highlights that Saudi Arabia’s cyber risk is economy-wide, not sector-specific.
Year-to-Year Elevation: High
CYFIRMA observed a steady rise in global ransomware activity, with 4,723 victims in 2023, peaking at 5,250 in 2024. In just the first half of 2025, 4,228 victims have already been recorded, signaling an aggressive and sustained pace by ransomware groups. The global threat landscape remains highly active, with no signs of slowdown.

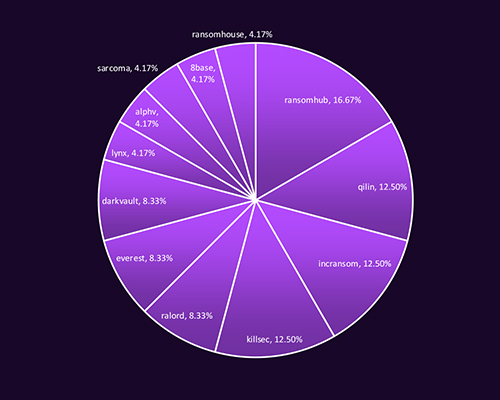
CYFIRMA observed multiple ransomware groups targeting Saudi Arabia, with RansomHub leading at 16.67% of identified incidents. Qilin, Incransom, and Killsec each accounted for 12.5%, indicating a competitive and diverse threat landscape. The presence of both established players like Qilin and emerging groups such as DarkVault and Ralord highlights the mix of experienced operators and aggressive newcomers actively pursuing Saudi targets.
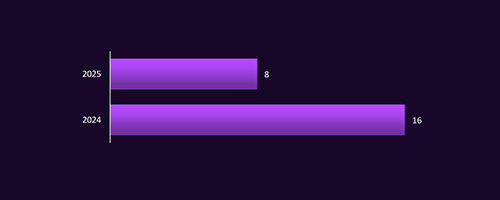
CYFIRMA observed 16 ransomware victims in Saudi Arabia in 2024 and 8 cases already in the first half of 2025 (as of July 31st). This indicates a continued high tempo of ransomware operations. Saudi Arabia remains one of the top targeted countries globally, with threat actors leveraging data theft, extortion, and leak site pressure tactics to maximize impact.
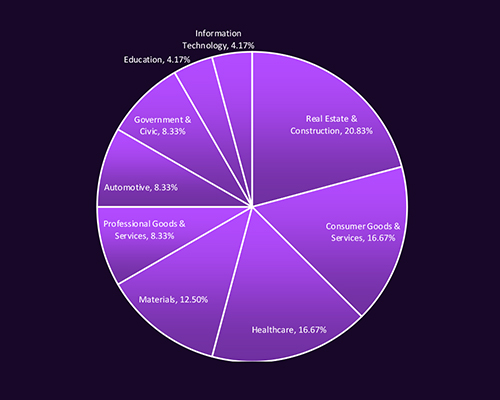
CYFIRMA observed ransomware groups in Saudi Arabia heavily targeting Real Estate & Construction (20.83%), followed by Consumer Goods & Services and Healthcare (each 16.67%). Materials, Government, Automotive, and Professional Services also faced notable activity, reflecting attackers’ focus on sectors with high operational impact and valuable data. The breadth of targeted industries shows that ransomware operators are pursuing both economic disruption and high-return extortion opportunities across critical and commercial domains.
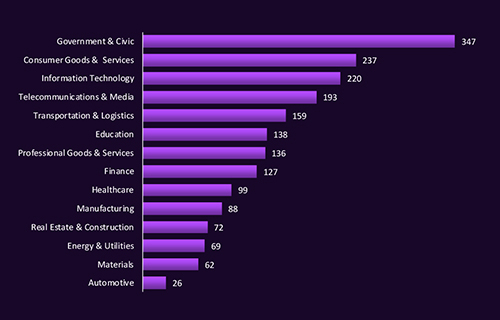
CYFIRMA observed significant dark web chatter around Saudi Arabia, with Government & Civic sectors leading at 347 mentions, indicating persistent interest from threat actors in high-value state targets. Consumer Goods & Services, Information Technology, and Telecommunications also show elevated activity, reflecting targeting of sectors with rich data and operational impact potential. The presence of transportation, finance, and energy sectors in the top mentions highlights the breadth of industries under discussion, suggesting a diverse and active threat landscape.
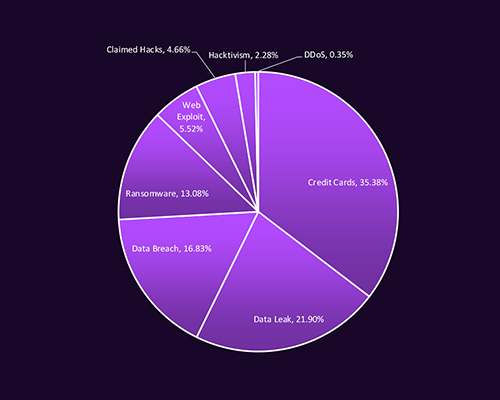
CYFIRMA observed dark web chatter on Saudi Arabia dominated by financial data trading, with credit cards (35.38%) and data leaks (21.90%) leading the discussions. Data breaches (16.83%) and ransomware (13.08%) further indicate sustained interest in monetizing compromised assets. The presence of web exploits, claimed hacks, and hacktivism reflects a mix of financially motivated and ideologically driven threats, highlighting the multifaceted nature of Saudi Arabia’s cyber risk exposure.
The vulnerabilities targeted in Saudi Arabia since January 1, 2025, show a clear focus on high-severity (CVSS 9.8–10) flaws across widely deployed enterprise technologies, many of which are cataloged in the CISA Known Exploited Vulnerabilities list. Exploitation spans network infrastructure, VPN gateways, collaboration platforms, and content management systems, critical entry points for both state-linked actors and financially motivated groups. Notably, over one-third of these CVEs, including CVE-2019-11510 (Pulse Secure VPN) and CVE-2019-19781 (Citrix ADC), are actively leveraged by ransomware operators, underscoring the convergence of opportunistic exploitation and targeted extortion campaigns. The targeting pattern highlights adversaries’ preference for reliable, publicly documented exploits that enable rapid initial access, lateral movement, and high-impact disruption across Saudi government, critical infrastructure, and private sector networks.
| Vulnerability | CVSS | Vendor | Product |
| CVE-2023-36845 | 9.8 | Juniper | Junos OS (J-Web) |
| CVE-2018-10562 | 9.8 | Dasan | Dasan GPON Home Router |
| CVE-2018-1273 | 9.8 | Spring | Spring Data Commons |
| CVE-2018-14839 | 9.8 | LG | NAS N1A1 |
| CVE-2018-15961 | 9.8 | Apache | ColdFusion |
| CVE-2018-6530 | 9.8 | D-Link | D-Link multiple routers |
| CVE-2018-7600 | 9.8 | Drupal | Drupal |
| CVE-2019-10758 | 9.9 | mongo-express | mongo-express |
| CVE-2019-11510 | 10 | Pulse Secure | Pulse Secure VPN |
| CVE-2019-11580 | 9.8 | Atlassian | Crowd/Crowd Data Center |
| CVE-2019-15107 | 9.8 | Webmin | Webmin |
| CVE-2019-16278 | 9.8 | nostromo | nhttpd |
| CVE-2019-16920 | 9.8 | D-Link | D-Link DIR-615, DIR-655C, DIR-825, DIR-835, DIR-855L, DIR-866L, DIR-652, DIR-862L, DHP-1565, DAP-1533 |
| CVE-2019-19781 | 9.8 | Citrix | Application Delivery Controller |
| CVE-2019-2725 | 9.8 | Oracle | Oracle Weblogic Server |
| CVE-2019-3396 | 9.8 | Atlassian | Confluence |
| CVE-2019-3929 | 9.8 | Barco/AWIND | Barco/AWIND OEM |
| CVE-2019-7192 | 9.8 | QNAP | QNAP NAS devices running Photo Station |
| CVE-2019-7256 | 9.8 | Linear | eMerge E3-Series |
| CVE-2019-9670 | 9.8 | Synacor | Zimbra Collaboration Suite |
| CVE-2020-10189 | 9.8 | Zoho | ManageEngine Desktop Central (now Engine Central) |
| CVE-2020-14882 | 9.8 | Oracle | Oracle Weblogic Server |
| CVE-2020-15505 | 9.8 | MobileIron | MobileIron Mobile Device Management (MDM) |
| CVE-2020-16846 | 9.8 | SaltStack | Salt |
| CVE-2020-17496 | 9.8 | vBulletin | vBulletin |
| CVE-2023-28771 | 9.8 | Zyxel | Zyxel |
Persistent Ransomware Activity
Ransomware continues to target high-value sectors such as Real Estate and Construction, Healthcare, and Consumer Goods & Services. While the overall number of incidents has fluctuated, operators are becoming more selective, increasingly employing data-first extortion strategies to maximize leverage and operational impact.
Financial Data as a Prime Target
Dark web monitoring reveals sustained interest in Saudi financial data, particularly credit card information and large-scale data leaks. These assets are actively traded for use in fraud schemes, identity theft, and business email compromise.
Sustained State-Aligned Cyber Operations
Threat actors linked to China, Russia, Iran, and North Korea remain highly active, conducting long-term espionage campaigns and pre-positioning activities against government, energy, and defense sectors, with an increasing focus on operational technology (OT) environments.
Spillover from Regional Geopolitical Tensions
The escalation of the Israel–Iran conflict has amplified hacktivist activity, opportunistic DDoS attacks, and phishing campaigns against Saudi entities, often serving as a diversion for more strategic intrusion operations.
Exploitation of Web Applications and Edge Devices
Initial access frequently occurs through vulnerable web-facing applications and exposed edge infrastructure. High-severity vulnerabilities from CISA’s Known Exploited Vulnerabilities (KEV) catalog, such as Citrix ADC, Pulse Secure VPN, Confluence, and WebLogic, remain key attack vectors.
Identity-Focused Intrusions
Attackers are increasingly bypassing perimeter defenses by exploiting authentication weaknesses, including MFA fatigue attacks, token theft, and session hijacking, particularly against Microsoft 365 and single sign-on (SSO) platforms.
Supply Chain and Managed Service Provider (MSP) Compromise
Adversaries are leveraging trusted third-party vendors and service providers to gain access to multiple Saudi organizations simultaneously, elevating the strategic importance of supply chain risk management.
Diverse and Evolving Malware Ecosystem
Observed campaigns utilize both commodity malware and advanced, custom-built tools, including Mirai, Winnti, and NukeSpeed RAT, indicating parallel objectives of monetization and intelligence collection.
Broad Sector Targeting with Government Focus
While targeting spans multiple industries, including diversified financial services, IT, telecommunications, and banking, the Government and Civic sector remains the most prominent focus, as evidenced by dark web chatter and targeting trends.
OT/IT Convergence Exploitation
Actors are increasingly moving laterally from IT networks into OT systems in sectors such as logistics, energy, and manufacturing, enabling the potential for both data compromise and operational disruption.
Shift Toward Stealth and High-Value Targets
Although incident volumes may decline year-over-year, this reflects a shift in adversary strategy toward fewer but more sophisticated operations, emphasizing stealth, persistence, and high-impact outcomes.
Public Sentiment as a Strategic Factor
Sentiment analysis from January to August 2025 indicates 42% positive, 32% negative, and 26% neutral perceptions of Saudi Arabia. Positive sentiment is driven by Vision 2030 reforms, economic diversification, and cultural initiatives, while negative sentiment centers on human rights concerns, political repression, and foreign policy positions. This mixed perception can influence the country’s geopolitical profile, soft power, and attractiveness as a target for ideologically motivated cyber activity.