


The Asia-Pacific region, with Malaysia as a critical node, is poised to be a central arena for geopolitical competition in the 21st century. Malaysia’s strategic location, economic significance, and diplomatic maneuvers place it at the nexus of these tensions, requiring adept management of both economic policies and security strategies to navigate the complex geopolitical landscape effectively. As the regional dynamics evolve, the interplay of military build-up, economic dependencies, and cyber warfare will shape the geopolitical risks for Malaysia and its neighbors.
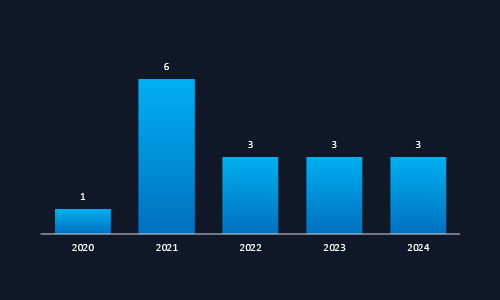
CYFIRMA observed a surge in cyber campaigns targeting Malaysia in 2021, followed by sustained activity through 2024. This pattern reflects Malaysia’s increasing strategic and economic importance in the region. The consistent targeting signals ongoing interest from both state-sponsored and financially motivated threat actors.
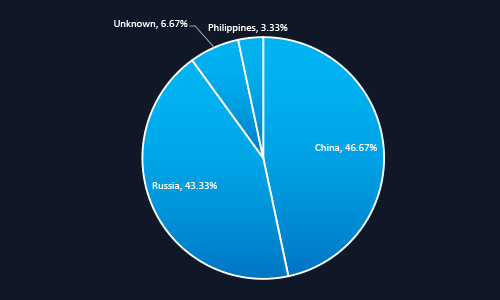
CYFIRMA’s analysis reveals that over 90% of threat actors targeting Malaysia originate from China and Russia, highlighting the influence of geopolitical drivers behind these cyber campaigns. The dominance of state-linked actors suggests a strong focus on espionage, intellectual property theft, and regional influence.
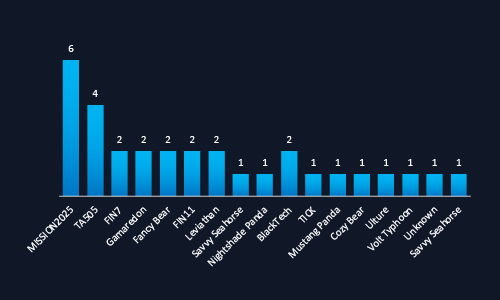
CYFIRMA observed a wide spectrum of threat actors targeting Malaysia, led by MISSION2025 and TA505, both known for their strategic precision and resource depth. The presence of state-sponsored groups like Fancy Bear, Leviathan, and Gamaredon show that Malaysia is no longer flying under the radar, it’s on the global cyber threat map. This “mixed bag” of APT groups, from espionage to financially motivated actors, highlights the need for robust, layered defenses.
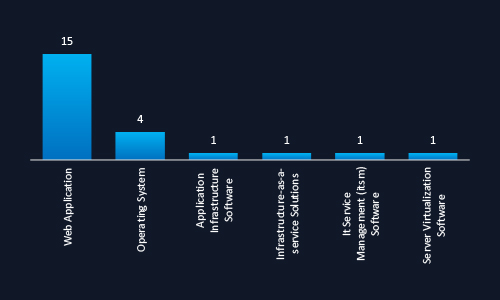
CYFIRMA observed that web applications are the most frequently targeted technology in Malaysia, accounting for the majority of attacks. This highlights a critical risk area as organizations accelerate digital transformation and customer-facing services. Lesser but notable targeting of operating systems and cloud infrastructure suggests expanding attacker interest in backend systems.
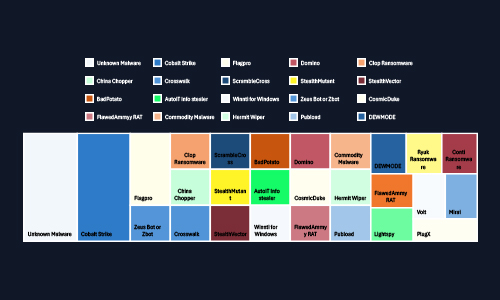
CYFIRMA observed a diverse malware ecosystem targeting Malaysia, ranging from Cobalt Strike and Cl0p Ransomware to stealthy info stealers like AutoIT and FlawedAmmy RAT. The presence of both commodity and advanced malware highlights a blended threat landscape where state actors and cybercriminals deploy overlapping tools. Notably, malware linked to espionage, disruption, and financial gain suggests multi-objective campaigns requiring cross-sectoral cyber defense coordination.
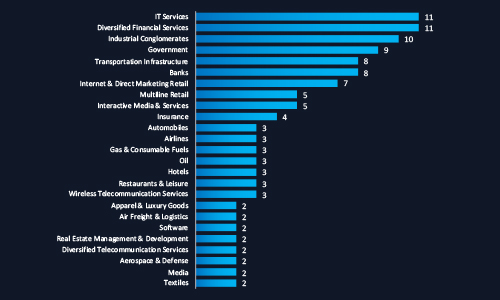
CYFIRMA observed that IT Services, Financial Services, and Industrial Conglomerates are the top targets of cyber threat actors in Malaysia. This trend reflects attackers’ focus on sectors with high digital dependency, sensitive data, and economic influence. The breadth of targeted industries from government to luxury goods highlights a broad threat surface across both critical infrastructure and commercial domains. Organizations and executives must prioritize industry-specific threat mitigation strategies aligned with their sector’s risk profile.
Year-to-Year Elevation: High
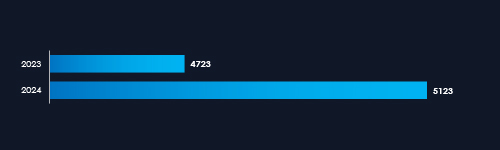
In 2023, CYFIRMA recorded 4,723 verified ransomware victims, while in 2024, the number increased to 5,123, representing an 8.5% year-over-year growth across all industries.
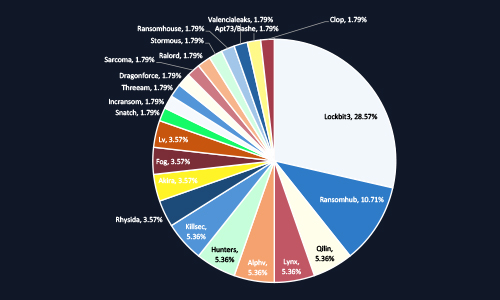
CYFIRMA observed that LockBit3 dominates ransomware activity in Malaysia, accounting for 28.57% of incidents, followed by RansomHub at 10.71%. The presence of over 20 distinct ransomware groups highlights a fragmented yet highly active threat ecosystem. This diversity reflects the increasing use of Ransomware-as-a-Service (RaaS) models, making attacks easier to launch and harder to predict. Organizations should view ransomware as a persistent business risk requiring proactive board-level governance and sector-specific threat mitigation.
In early 2023, the takedown of Hive caused a temporary slowdown in ransomware activity. However, this was followed by a surge driven by Cl0p, leveraging the MOVEit vulnerability.
Similarly, the early 2024 slowdown caused by the LockBit3 takedown was short-lived, as affiliates switched to other Ransomware-as-a-Service (RaaS) and RansomHub quickly emerged to fill the void in the RaaS ecosystem.
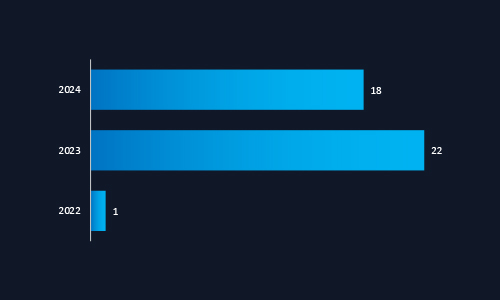
CYFIRMA observed a dramatic rise in ransomware attacks on Malaysian organizations, from 1 victim in 2022 to 22 in 2023, followed by 18 in 2024. While slightly lower than the 2023 peak, the 2024 figure confirms that ransomware remains a persistent and strategic threat. This trend highlights the urgent need for executive oversight in driving ransomware preparedness, incident response, and recovery capabilities across all critical sectors.
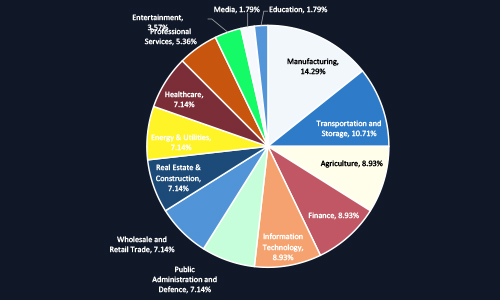
CYFIRMA observed that ransomware actors are heavily targeting Malaysia’s manufacturing sector (14.29%), followed by transportation, agriculture, finance, and IT. The diversity of affected sectors from critical infrastructure to public services reflects broad systemic exposure. This highlights the urgent need for sector-specific cyber risk frameworks and executive-driven investment in resilience and response capabilities across the national economy.
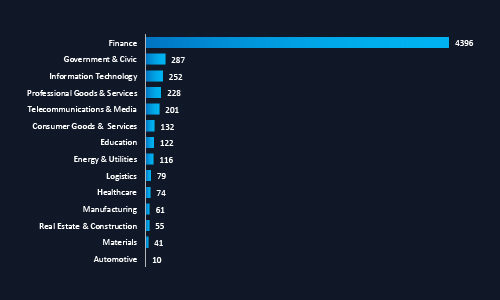
Over the past six months, CYFIRMA observed a disproportionate surge in dark web chatter linked to Malaysia’s finance sector, accounting for over 4,300 mentions, a volume more than 15 times higher than any other industry. This trend signals active reconnaissance, targeting, or sale of financial data and access by cybercriminals. The persistent chatter around government, IT, and telecom sectors also reflects increasing threat actor focus on Malaysia’s Critical National Information Infrastructure (CNII).
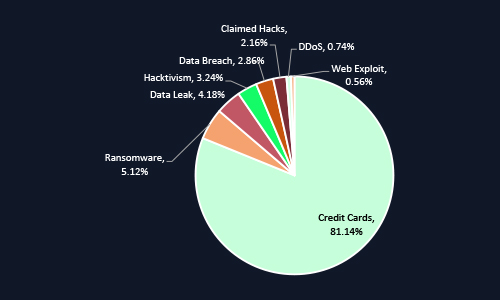
Over the last six months, 81% of dark web chatter related to Malaysia focused on stolen credit card data, highlighting the country’s exposure to financial fraud and underground monetization. Other prominent themes include ransomware (5.1%), data leaks, and hacktivism, signaling broader risks to data privacy and national reputation. The trend reflects a mature cybercrime ecosystem exploiting Malaysia’s digital growth.
Shift Toward Nation-State Targeting
Increased activity from Chinese and Russian-linked APT groups reflects Malaysia’s growing geopolitical and economic significance, especially in semiconductors, energy, and regional diplomacy.
Ransomware Attacks Becoming Industrialized
The rise in ransomware campaigns, led by Lockbit3 and RansomHub, shows growing maturity in Ransomware-as-a-Service (RaaS) operations targeting diverse sectors from manufacturing to public administration.
Financial Platforms in the Crosshairs
Threat actors are exploiting Malaysia’s expanding digital finance ecosystem, with large-scale leaks from platforms like i3investor and PitchIn.my highlighting rising data monetization risks.
Critical Infrastructure Under Siege
Telecommunications, transportation, and energy systems are increasingly targeted both for disruption and intelligence gathering highlighting vulnerabilities in Malaysia’s Critical National Information Infrastructure (CNII) sectors.
Web Applications & Remote Access Exploitation
Web-facing services remain the top attack vector, driven by misconfigurations, vulnerable APIs, and poor identity/access controls.
Data Brokerage on the Rise
Leaked databases containing sensitive personal and organizational data are increasingly traded on underground forums, enabling follow-on attacks like fraud, phishing, and credential stuffing.
Dark Web Economy Targeting Malaysia
Administrative access to telecom portals and government dashboards are being sold with increasing frequency signaling a shift toward persistent and monetizable access.