



At CYFIRMA, we provide timely insights into emerging threats and malicious tactics targeting organizations and individuals. CYFIRMA’s research team recently identified a sophisticated dropper binary designed to deploy the “ELPACO-team” ransomware, a new variant of “MIMIC” ransomware. This research report investigates the “ELPACO-team” ransomware: upon execution, the malware deploys a series of malicious tools and legitimate utilities, allowing it to disable system defenses, encrypt a wide range of file types, and perform actions to ensure persistence. It also encrypts critical files across local and network drives, leaving a ransom note for the victim, and targets a specific set of file extensions, while excluding others to avoid corrupting essential system files. The ransomware is a significant threat to both individuals and enterprises, capable of evading detection and hindering recovery efforts.
The “ELPACO-team” is a highly sophisticated 32-bit Windows executable, identified as a member of the Mimic ransomware family. This malware employs a multifaceted approach to attack, utilizing both malicious and legitimate tools to compromise the victim’s system. The binary includes an embedded 7zSFX self-extracting archive, which contains several payloads and utilities used to control and manipulate the victim’s system. It begins by extracting components from an embedded 7zSFX archive, which includes a variety of files such as *Everything.exe*, a legitimate file search utility, and other payloads. The malware then uses these components to disable security features, including Windows Defender, and initiates the encryption of a wide range of file types across both local and network drives.
It is equipped with advanced features, such as stopping virtual machine operations, deleting backup data, and modifying system configurations to ensure ongoing execution. A unique decryption ID is assigned to each victim, and a ransom note is displayed to extort payment. The ransomware also includes mechanisms to ensure persistence, such as modifying system settings and blocking access to recovery options. Its encryption configuration targets critical data files while excluding essential system files, which complicates efforts to restore the system and recover lost data.
Ransomware continues to be one of the most pervasive and dangerous threats in the cybersecurity landscape. From an external threat perspective, it represents a significant risk to organizations worldwide, targeting everything from critical infrastructure to private businesses and individual users. Attackers often employ sophisticated tactics to infiltrate networks, encrypt vital data, and demand hefty ransoms in exchange for decryption keys. This type of cyberattack not only disrupts operations but also causes financial losses, reputational damage, and legal complications.
The external threat posed by ransomware has grown more severe with the rise of ransomware-as-a-service (RaaS), which lowers the barrier for entry for malicious actors. These threats are increasingly linked to advanced persistent threat (APT) groups and cybercriminal syndicates, often with geopolitical motives or financial gains in mind. In addition to traditional ransom demands, attackers are now exfiltrating sensitive data and threatening to release it publicly, further increasing the stakes for organizations. The constantly evolving techniques and the global reach of these threats make ransomware a critical focus for cybersecurity professionals and organizations worldwide.
Mimic ransomware is a sophisticated malware strain that was first observed in the wild in June 2022. Some of its code is believed to be based on the leaked Conti ransomware builder, indicating a shared lineage between the two. These features make Mimic a particularly potent and evolving threat in the cybersecurity landscape. ELPACO-team Ransomware is the new variant of Mimic ransomware. The ransomware has several capabilities, including the ability to disable Windows Defender, terminate critical processes, and delete system recovery files. It also employs multiple threads for faster encryption and is capable of evading traditional detection methods.
As per OSINT telemetry data, the malware sample we analyzed submitted from Russia and the Republic of South Korea indicates potential victims from these areas. It is not yet known how the ransomware is deployed on the victims’ machine, but based on previous experiences with Mimic ransomware and its variants, it is highly likely that ELPACO-team also follows a similar multi-stage deployment process on the victim machine. Typically, attackers would gain initial access either through brute force on exposed services, such as MSSQL, and exploit vulnerabilities to execute arbitrary commands. Following this, they may leverage credential dumping tools, such as Mimikatz to gather credentials and move laterally within the network.
The evolution of this potent strain of ransomware highlights the growing complexity and impact of ransomware attacks, underscoring the need for organizations to continuously strengthen their defenses against these highly adaptive threats.
Basic Details:
File Name: ELPACO-teamv.exe
MD5: 33eeeb25f834e0b180f960ecb9518ea0
SHA-256: 9f6a696876fee8b811db8889bf4933262f4472ad41daea215d2e39bd537cf32f
File Type: Win32 EXE
Basic Info:
The binary is a 32-bit Windows executable, developed using Microsoft Visual C++, and includes an overlay section containing a 7zSFX self-extracting archive. 7zSFX is a self-extracting archive format that packages compressed files with an embedded decompression module, allowing the archive to extract itself without needing separate extraction software.

We extracted the overlay section and unpacked the files within the archive, revealing the following files: 7za.exe, Everything.exe, Everything.dll, Everything64.dll.

7za.exe (MD5: B93EB0A48C91A53BDA6A1A074A4B431E)
Everything.exe (MD5: C44487CE1827CE26AC4699432D15B42A)
Everything32.dll (MD5: 3B03324537327811BBBAFF4AAFA4D75B)
Everything64.dll (MD5: 245FB739C4CB3C944C11EF43CDDD8D57)
7za.exe is a 7-Zip binary used to extract the payload. Everything.exe is a signed binary and a genuine application from Voidtools, known as “Everything,” a freeware for Windows that rapidly locates files and folders by filename. Everything32.dll is another legitimate component of the ‘Everything’ application, used to select target files for encryption. Everything64.dll, however, is a password-protected archive containing the malicious payloads.
“Everything64.dll” malicious archive contains the following files:

DC.exe (MD5: AC34BA84A5054CD701EFAD5DD14645C9)
ELPACO-team.exe (B951E50264F9C5244592DFB0A859EC41)
[email protected]
(MD5:0BF7C0D8E3E02A6B879EFAB5DEAB013C)
Everything.ini (742C2400F2DE964D0CCE4A8DABADD708)
Everything2.ini (51014C0C06ACDD80F9AE4469E7D30A9E)
global_options.ini (26F59BB93F02D5A65538981BBC2DA9CC)
gui35.exe (03A63C096B9757439264B57E4FDF49D1)
gui40.exe (57850A4490A6AFD1EF682EB93EA45E65)
xdel.exe (803DF907D936E08FBBD06020C411BE93)
These files include tools and malicious binaries that are used for different malicious purposes like turning off Windows Defender (DC.exe) and legitimate sdelete.exe (xdel.exe), which is a command-line utility from the Microsoft Sysinternals suite, used for securely deleting files by overwriting data to prevent recovery. It ensures that deleted files cannot be restored, making it a tool often leveraged by attackers to cover their tracks and prevent forensic analysis. The main ransomware payload is ELPACO-team.exe.
Upon execution of the main malicious binary, ELPACO-teamv.exe” acts as a dropper, creating a folder with the name 7ZipSfx.000 in %Temp% folder and dropping its components 7za.exe, Everything.exe, Everything32.dll, Everything64.dll from the embedded SFX archive into the folder.
It then uses the extracted 7za.exe to unpack the password-protected (password: 7183204373585782) Everything64.dll in the same directory by using the following command:
C:\Users\[Username]\AppData\Local\Temp\7ZipSfx.000\7za.exe” x -y -p7183204373585782 Everything64.dll

The Following files are extracted from “Everything64.dll”: “DC.exe”, “ELPACO-team.exe”, “[email protected]”, “Everything.ini”, “Everything2.ini”, “global_options.ini”, “gui35.exe”, “gui40.exe”, “xdel.exe”.
Furthermore, it creates a session.tmp file in the same directory, which stores a session key for resuming encryption if the process is interrupted.

Afterward, it creates a folder entitled BD3FDDDF-6CAF-3EBC-D9CF-C8DF72D8F78A at location C:\Users\[Username]\AppData\Local\ and copies these dropped files to this folder and renames ELPACO-team.exe, which is the main ransomware payload to svhostss.exe, and deletes the folder 7ZipSfx.000 (and the original files from the %Temp% folder).

The following process tree outlines the execution flow of the main binary, which includes the extraction of files from Everything.dll using 7za.exe.

Subsequently, a command line executes the 7ZSfx000.cmd batch script, which is dropped into the victim’s temporary directory. This script is designed to repeatedly attempt to delete the ELPACO-teamv.exe (the main binary) until successful, after which it deletes itself.

Afterward, the svhostss.exe binary is executed from the %LOCALAPPDATA%\BD3FDDDF-6CAF-3EBC-D9CF-C8DF72D8F78A directory, triggering the execution of additional dropped binaries and commands.

It executes a sequence of actions involving multiple files. gui40.exe serve as a graphical user interface (GUI) component for the ransomware. Everything.exe is a legitimate utility that is being used here and executes with -startup flag to run automatically upon system startup. Later DC.exe malicious tool executes to disable Windows defender.
Commands executed by the ransomware:
It executes the DC.exe file dropped earlier, which is used to turn off Windows Defender. The /c flag tells it to execute the command that follows and then terminate.

The ransomware watches its own process (e.g. PID: 8016). The -! parameter might imply an aggressive or forceful monitoring mode. It tries to unlock certain memory addresses, while the -startup parameter suggests an operation that configures the program Everything.exe to run automatically during system boot.
It uses Windows command line utility “powercfg.exe to perform various tasks. In Windows, powercfg.exe is used to manage and configure the power settings of a computer. The command powercfg.exe -H off is used to disable hibernation on a Windows system. Running this command turns off hibernation, freeing up disk space by deleting the hiberfil.sys file, which stores the hibernation data. The ransomware uses the commands listed below to ensure recovery options like hibernation or fast system restoration aren’t available, making recovery more difficult after an attack:
The malware leverages legitimate powercfg.exe commands to alter power management settings for strategic purposes, such as preventing system sleep, hibernation, or power-saving modes. Commands like those listed above also execute to modify power configurations associated with the system. By setting these parameters to 0, the ransomware can ensure continuous system operation, allowing malicious processes to run uninterrupted. This tactic may support prolonged data encryption, data exfiltration, or persistence mechanisms by keeping the target system active.
The Powershell command is executed to stop all running VMs, identifies VHDs associated with VMs and dismounts them using Dismount-DiskImage, effectively detaching them from the host systems, and finally dismounting disk images linked to volumes, further severing their active connections. Such commands could potentially be leveraged by the ransomware or malicious scripts to disrupt virtualized environments and interfere with disk management operations:
The bcdedit.exe /set {default} bootstatuspolicy ignoreallfailures command modifies the boot configuration data to ignore boot failures:
The wbadmin.exe is used to delete system state backups and backup catalogues, respectively, preventing the victim from restoring their system from backups:
It executes registry modification commands, enables multiple remote desktop sessions, multiple concurrent sessions, and sets sethc.exe (Sticky Keys) to open cmd.exe, enabling unauthorized command-line access and facilitating remote control by the attackers:
The wevtutil.exe in Windows allows users and administrators to manage event logs and event log subscriptions. Commands are used to clear the logs of the Security, System, and Application event logs. By doing so, the malware erases evidence of its activities, making it difficult for security analysts to trace malicious actions or identify the timeline of events during forensic investigations.
The command chain below combines multiple operations. Ping command, pings to an unreachable IP address (127.2) five times, often used to create a delay or pause in command execution without directly waiting. fsutil command zeros out svhostss.exe file (20,000,000 bytes), possibly corrupting it by overwriting its contents with zeros, and afterward changes the directory to %LOCALAPPDATA%\BD3FDDDF-6CAF-3EBC-D9CF-C8DF72D8F78A, and forcefully deletes all .exe, .ini, .dll, .bat, and .db files in the directory, with the /f flag to force deletion, /q for quiet mode, and /a to select files with any attributes:
fsutil is used to overwrite a specific portion of the file svhostss.exe with zeros. It targets the file at the specified path, starting at offset 0 and zeroing out the first 32MB (20,000,000 bytes). This could be an attempt to corrupt or destroy the contents of the file, potentially rendering it non-functional or as part of a malicious operation to hide or modify the file’s original behaviour:
In accordance with execution, the ransomware also shows status log in the command line window. It begins by collecting system information, such as the OS version, architecture, memory status, and user privileges. The malware ensures it has elevated privileges by granting itself additional privileges to maintain persistence. It is important to note that the log explicitly mentions the version of the ransomware as Mimic 6.3, confirming that the ElPACO-team ransomware is a variant of the Mimic ransomware family.

It then proceeds to execute several dropped binaries (gui40.exe, Everything.exe) and configures them for autostart. The GUI interface is used to control the operation of the ransomware by executing gui40.exe.

The malware scans local and network drives, attempting to map shared drives and hidden shares, which indicate the malware could spread laterally within the local network, and can exploit vulnerable systems and encrypt them. Additionally, it waits for further signals to continue its operations.

The ransomware employs a comprehensive configuration setup. It uses a randomly generated specified decryption ID TXSrYIrW_8rM6Zms7pibt5YVkS2LwQvsuA-tVaue_x0*ELPACO-team and assigns a specific file extension, ELPACO-team, to the encrypted files. It encrypts files up to 2 MB in size, targets both local and network drives for encryption, and includes a dedicated note file (Decryption_INFO.txt) to notify victims of the attack.

The ransomware configuration also mentions settings to wipe drives, disable Windows Defender, and block system tasks, such as shutdowns and access to the Task Manager. Additionally, it excludes certain files and directories, such as system files and application folders, while prioritizing the encryption of specific file types, including database files, documents, and archives. The configuration ensures that the malware operates stealthily by scanning hidden shares, blocking recovery options, and using multiple threads for both local and network operations. It saves the details of the configuration in dropped files named globl_options.ini.
Here is the list of file extensions on priority to encrypt: TIB, sql, sqlite, sqlite3, sqlitedb, mdf, mdb, adb, db, db3, dbf, dbs, udb, dbv, dbx, edb, exb, 1cd, fdb, idb, mpd, myd, odb, xls, xlsx, doc, docx, bac, bak, back, zip, rar, dt, 4dd, 4dl, abcddb, abs, abx, accdb, accdc, accde, accdr, accdt, accdw, accft, ade, adf, adn, adp, alf, arc, ask, bacpac, bdf, btr, cat, cdb, chck, ckp, cma, cpd, dacpac, dad, dadiagrams, daschema, db-shm, db-wal, db2, dbc, dbt, dcb, dct, dcx, ddl, dlis, dp1, dqy, dsk, dsn, dtsx, dxl, eco, ecx, epim, fcd, fic, fm5, fmp, fmp12, fmpsl, fol, fp3, fp4, fp5, fp7, fpt, frm, gdb, grdb, gwi, hdb, his, hjt, ib, icg, icr, ihx, itdb, itw, jet, jtx, kdb, kexi, kexic, kexis, lgc, lut, lwx, maf, maq, mar, mas, mav, maw, mdn, mdt, mrg, mud, mwb, ndf, nnt, nrmlib, ns2, ns3, ns4, nsf, nv, nv2, nwdb, nyf, oqy, ora, orx, owc, p96, p97, pan, pdb, pdm, pnz, qry, qvd, rbf, rctd, rod, rodx, rpd, rsd, s2db, sas7bdat, sbf, scx, sdb, sdc, sdf, sis, sl3, spq, sqlite2, te, temx, tmd, tps, trc, trm, udl, usr, v12, vis, vpd, vvv, wdb, wmdb, wrk, xdb, xld, xmlff, 7z.
The file extensions excluded from encryption are: ELPACO-team, 386, cmd, deskthemepack, diagcab, diagcfg, diagpkg, dll, info, mui, sys, theme, tmp.
File names excluded from the process of encryption are: desktop.ini, iconcache.db, thumbs.db, ntuser.ini, boot.ini, ntdetect.com, ntldr, NTUSER.DAT, bootmgr, BOOTNXT, BOOTTGT, session.tmp, Decryption_INFO.txt.
The Dirs/folders excluded from encryption: steamapps, Cache, Boot, Chrome, Firefox, Mozilla, Mozilla Firefox, MicrosoftEdge, Internet Explorer, Tor Browser, Opera, Opera Software, Common Files, Config.Msi, Intel, Microsoft, Microsoft Shared, Microsoft.NET, MSBuild, MSOCache, Packages, PerfLogs, ProgramData, System Volume Information, tmp, Temp, USOShared, Windows, Windows Defender, Windows Journal, Windows NT, Windows Photo Viewer, Windows Security, Windows.old, WindowsApps, WindowsPowerShell, WINNT, $RECYCLE.BIN, $WINDOWS.~BT, $Windows.~WS, :\Users\Public\, :\Users\Default\, C:\Users\[Username]\AppData\Local\BD3FDDDF-6CAF-3EBC-D9CF-C8DF72D8F78A
Killing Services: WSearch, pla, DusmSvc, defragsvc, DoSvc, wercplsupport, SDRSVC, TroubleshootingSvc, Wecsvc, fhsvc, wbengine, PcaSvc, WerSvc, SENS, AppIDSvc, BITS, wuauserv, SysMain, DiagTrack, diagnosticshub.standardcollector.service, dmwappushservice, WMPNetworkSvc, SDRSVC, wbengine
The ransomware leverages “Everything.exe” to search for files/folders to encrypt or exclude, utilizing the following search format:
Search mask: <file:><nocase:><path:C:\><ext:; File extensions on priority to encrypt >file:<!endwith:ELPACO-team (Extension used after Encryption)><!” Dirs/Folders excluded from encryption “>wholefilename:Files names excluded from the process of encryption “><!size:0>

The ransomware encrypts files and appends the extension ELPACO-team after encryption, as defined in the malware’s configuration.

Later it drops a ransom note named Decryption_INFO.txt at location C:\, %LOCALAPPDATA% and displays the ransom note by executing the command:
notepad.exe C:\Users\[Username]\AppData\Local\Decryption_INFO.txt

The ransom note left by the ransomware operators highlights that the victim’s data has been encrypted due to a significant security vulnerability. It provides a unique decryption ID and states that the only way to recover the files is by purchasing a decryption tool and key. The attackers can be contacted via email at [email protected] or on Telegram at @DataSupport911 or https[:]//t[.]me/DataSupport911. The note warns against renaming encrypted files or using third-party decryption tools, as these actions may lead to permanent data loss. The attackers promise cooperation and assure victims that they uphold a reputation for fulfilling decryption once payment is made.
The ransomware achieves persistence by modifying registry entries. It creates registry entry at Computer\HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Run with the name svhostss, ensuring that the svhostss.exe file, located at C:\Users\[Username]\AppData\Local\BD3FDDDF-6CAF-3EBC-D9CF-C8DF72D8F78A\, runs automatically each time the user logs into Windows.

The ransomware includes a GUI interface, managed by the gui40.exe binary, which operates as a child process of the main payload svhostss.exe. This interface offers customizable performance and feature settings for the attacker. The main menu features multiple tabs: the “Options” tab allows the selection of file extensions to encrypt and exclusions for specific folders or files. The “Priority” tab, displayed by default when the GUI launches, includes checkboxes for affected drives/volumes, which are encrypted after pressing the “Start Encrypt” button. The “Notice” tab displays the ransom note content, excluding the decryption ID that is added once encryption begins. The final tab logs the activities and tasks performed during the encryption process.

The likely reason for providing a GUI interface is to allow the attacker to remotely control the system, customize options, and initiate encryption as needed, potentially as part of a broader attack campaign.
The screenshot below displays the “Options” tab of the ransomware’s GUI interface. This tab specifies that the extension “ELPACO-team” will be appended to encrypted files and allows the attacker to manage various settings, such as extension priorities for encryption, exclusion of files/directories, and termination of specific processes and services. Additional features like “Disable Windows Defender” and “Encrypt hidden drives” and so on can be toggled using checkboxes. The interface also includes a dropdown menu to automate feature selection with presets like “Maximum Speed”, “Average”, “Full Encrypt”, and “Builder”, which adjusts checkboxes and modifies file priority extensions, exclusions, and more based on the chosen option.

The “Notice” tab displays the content of the ransom note, which is also dropped on the victim’s machine as Decryption_INFO.txt but without the decryption ID. The decryption ID is generated and appended only after the encryption process begins.
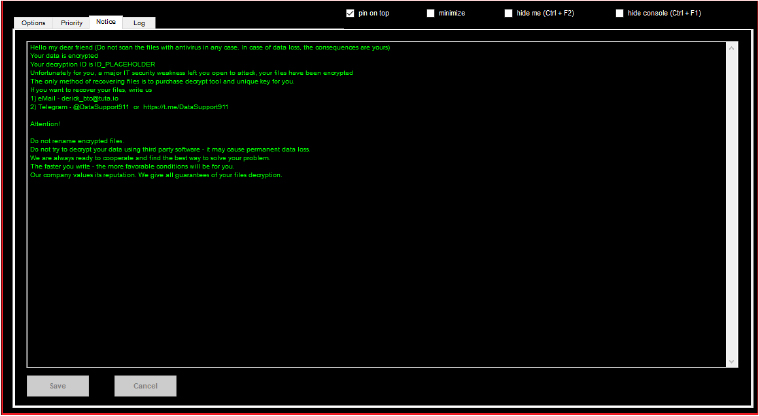
The final tab in the interface is the log, which records detailed information about the activities and task progress carried out by the malware. This log can be viewed as a text report by clicking the “See log” button.

Once the encryption begins, all customized options are disabled, and the ransomware proceeds with the encryption process based on the selections configured in the options tab.

The ransomware has the following capabilities:
The analysis of the ELPACO-team ransomware highlights its sophisticated nature, characterized by the use of legitimate tools and custom payloads to conduct an effective and stealthy cyberattack. The malware’s ability to disable Windows Defender, modify system configurations, encrypt a wide range of file types, and prevent system recovery demonstrates a high level of technical proficiency. The ELPACO-team ransomware ensures its continued operation through persistent mechanisms, registry modifications, and anti-shutdown tactics. Its targeted approach to encrypting essential user data while excluding system-critical files ensures the victim’s device remains operational, facilitating ransom payment. Given the malware’s comprehensive use of both built-in Windows utilities and external tools, organizations must adopt a robust defense strategy that includes endpoint detection, advanced behavioural monitoring, and regular data backups to mitigate the impact of such ransomware attacks. Proactive measures, such as user awareness training and enhanced system hardening, are essential to defend against evolving threats like ELPACO-team ransomware. The ELPACO-team ransomware underscores the evolving complexity of modern ransomware operations and the need for a multi-layered cybersecurity approach to detect, prevent, and respond to such sophisticated threats.
| Sr No. | Indicator | Type | Remarks |
| 1 | 33eeeb25f834e0b180f960ecb9518ea0 | MD5 File Hash | ELPACO-team.vexe |
| 2 | B93EB0A48C91A53BDA6A1A074A4B431E | MD5 File Hash | 7za.exe |
| 3 | AC34BA84A5054CD701EFAD5DD14645C9 | MD5 File Hash | DC.exe |
| 4 | 0BF7C0D8E3E02A6B879EFAB5DEAB013C | MD5 File Hash | [email protected] |
| 5 | C44487CE1827CE26AC4699432D15B42A | MD5 File Hash | Everything.exe |
| 6 | 742C2400F2DE964D0CCE4A8DABADD708 | MD5 File Hash | Everything.ini |
| 7 | 51014C0C06ACDD80F9AE4469E7D30A9E | MD5 File Hash | Everything2.ini |
| 8 | 3B03324537327811BBBAFF4AAFA4D75B | MD5 File Hash | Everything32.dll |
| 9 | 245FB739C4CB3C944C11EF43CDDD8D57 | MD5 File Hash | Everything64.dll |
| 10 | 1B37DC212E98A04576AAC40D7CE7D06A | MD5 File Hash | global_options.ini |
| 11 | 26F59BB93F02D5A65538981BBC2DA9CC | MD5 File Hash | global_options.ini |
| 12 | 03A63C096B9757439264B57E4FDF49D1 | MD5 File Hash | gui35.exe |
| 13 | 57850A4490A6AFD1EF682EB93EA45E65 | MD5 File Hash | gui40.exe |
| 14 | FADE75EDBF62291FBB99C937AFC9792C | MD5 File Hash | session.tmp |
| 15 | B951E50264F9C5244592DFB0A859EC41 | MD5 File Hash | svhostss.exe |
| 16 | 803DF907D936E08FBBD06020C411BE93 | MD5 File Hash | xdel.exe |
| 17 | B951E50264F9C5244592DFB0A859EC41 | MD5 File Hash | ELPACO-team.exe |
| No. | Tactic | Technique |
| 1 | Initial Access (TA0001) | T1566: Phishing T1190: Exploit Public-Facing Application |
| 2 | Execution (TA0002) | T1059: User Execution ID: T1203: Exploitation for Client Execution T1204.002: Malicious File |
| 3 | Persistence (TA0003) | T1547.001: Boot or Logon Autostart Execution: Registry Run Keys / Startup Folder |
| 4 | Defense Evasion (TA0005) | T1070.004: Indicator Removal: File Deletion |
| 5 | Discovery (TA0007) | T1082: System Information Discovery T1083: File & Directory Discovery T1016: System Network Configuration Discovery |
| 6 | Collection (TA0009) | T1005: Data from Local System |
| 7 | Impact (TA0040) | T1486: Data Encrypted for Impact |
import “hash”
rule ELPACO-team_Ransomware_Hash_Detection {
meta:
description = “To identify ELPACO-team ransomware hashes”
author = “CRT”
date = “15-11-2024”
condition:
hash.md5(0, filesize) == “33eeeb25f834e0b180f960ecb9518ea0” or
hash.md5(0, filesize) == “B93EB0A48C91A53BDA6A1A074A4B431E” or
hash.md5(0, filesize) == “AC34BA84A5054CD701EFAD5DD14645C9” or
hash.md5(0, filesize) == “0BF7C0D8E3E02A6B879EFAB5DEAB013C” or
hash.md5(0, filesize) == “C44487CE1827CE26AC4699432D15B42A” or
hash.md5(0, filesize) == “742C2400F2DE964D0CCE4A8DABADD708” or
hash.md5(0, filesize) == “51014C0C06ACDD80F9AE4469E7D30A9E” or
hash.md5(0, filesize) == “3B03324537327811BBBAFF4AAFA4D75B” or
hash.md5(0, filesize) == “245FB739C4CB3C944C11EF43CDDD8D57” or
hash.md5(0, filesize) == “1B37DC212E98A04576AAC40D7CE7D06A” or
hash.md5(0, filesize) == “26F59BB93F02D5A65538981BBC2DA9CC” or
hash.md5(0, filesize) == “03A63C096B9757439264B57E4FDF49D1” or
hash.md5(0, filesize) == “57850A4490A6AFD1EF682EB93EA45E65” or
hash.md5(0, filesize) == “FADE75EDBF62291FBB99C937AFC9792C” or
hash.md5(0, filesize) == “803DF907D936E08FBBD06020C411BE93” or
hash.md5(0, filesize) == “B951E50264F9C5244592DFB0A859EC41”
}