

At CYFIRMA, we are dedicated to providing current insights into prevalent threats and the strategies employed by malicious entities targeting both organizations and individuals. EdskManager RAT is a stealthy and adaptable remote access trojan, leveraging multiple stages of execution and encrypted payload delivery. The malware employs a downloader disguised as legitimate software, followed by in-memory decryption and stealth communication with command-and-control servers. Its use of HVNC (Hidden Virtual Network Computing), advanced persistence techniques, and anti-analysis measures indicates a strong focus on long-term, covert access to infected systems. This report provides a technical breakdown of the malware’s behavior, infrastructure, and objectives, offering insight into its potential impact and strategies for defense.
Remote access trojans (RATs) have evolved significantly in recent years, adopting more sophisticated methods to evade detection and maintain control over compromised systems. EdskManager RAT stands out due to its modular structure, encrypted configurations, and stealth-focused design. Unlike traditional RATs, it integrates covert communication methods and remote-control capabilities that minimize its visible footprint on infected machines. This report presents a detailed technical analysis of EdskManager RAT, focusing on its infection process, persistence, reconnaissance features, and command-and-control mechanisms to support a deeper understanding of the threat and inform effective response strategies.
EdskManager RAT is distributed through a downloader, which is packaged and disguised as a legitimate application, such as a document viewer or Chrome downloader. So far, we have identified 8 variants of this downloader.
This RAT derives its name from two components: “Edsk,” referring to the “Embedded DLL Shell Kit” and the file with the custom .edskv extension—an encrypted DLL containing critical configuration and communication data used by the malware, along with the behavioral pattern by which it is loaded into process memory; and “Manager”, which signifies the initial communication sent to the C2 server.
The threat actor behind the EdskManager RAT leverages the legitimate cloud storage S3 (Simple Storage Service), provided by Amazon, to host the malware package (including legitimate executable, malicious DLLs, and ‘.edskv’ file). As of the date of this report, the S3 storage used to host the malware package has been deleted.
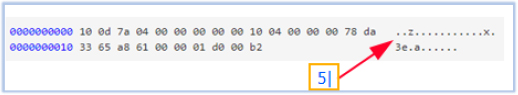
The domain “u[.]arpuu[.]com” is used for command and control. Previously, it resolved to IP address ‘56[.]155[.]36[.]99’ but now resolves to ‘127[.]0.0.1’, a local-host IP, indicating a halting of operations or the cessation of communication with the C2 server.
The decrypted ‘.edskv’ file reveals another potential C2, ‘kimhate[.]com:1516’; however, no communication with this server was observed during our analysis.
Threat Landscape:
EdskManager RAT operates within a dynamic threat landscape, constantly evolving to adapt to new detection methods and security measures. Its ability to obfuscate communication with command-and-control servers and encrypt critical data makes it particularly difficult to track and neutralize. Its potential for switching between C2 servers or altering communication protocols remains a key feature of the malware’s adaptive tactics. The malware can adapt its C2 infrastructure when needed to maintain persistence and evade detection. Additionally, by exploiting legitimate system processes and leveraging social engineering techniques, it remains stealthy and resilient. These adaptive capabilities enable EdskManager to effectively compromise its targets, often without immediate detection, and carry out a variety of malicious activities, such as data exfiltration and system control.
| File Details: Initial Payload | |
| File Name | WindowsFormsApp.exe |
| File Size | 37.84 KB (38744 bytes) |
| Signed | Signed (valid signature, certificate revoked) |
| MD5 | e2ed710d1b3d12e9b4cccadd103355c4 |
| SHA-256 | 85bae6fe73a9e2bf0819a6f60adfc458392a7a56de23f10d3bdddb8e3a97a8ec |
| Time Stamp | 25-05-2025 |
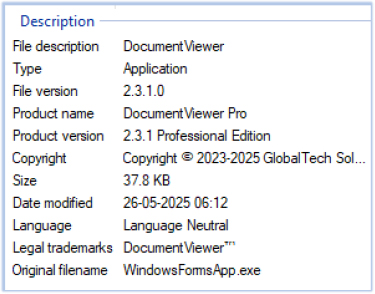
WindowsFormsApp.exe is a 32-bit GUI-based executable that identifies itself as a document viewer application under the name “Document Viewer Pro”.
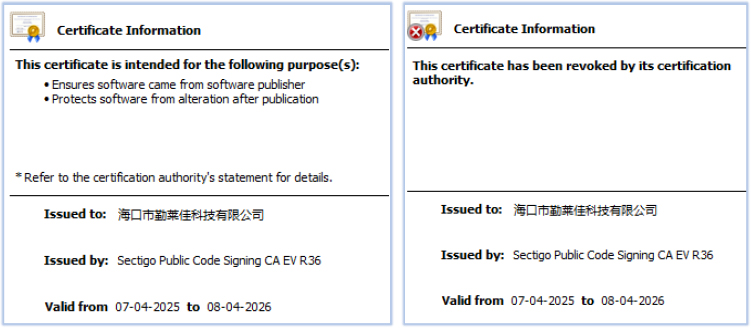
It is a signed file with a valid signature. At the time of signing, the certificate used was valid and trusted; however, as of the date of this report, it has been explicitly revoked by its issuing Certificate Authority:
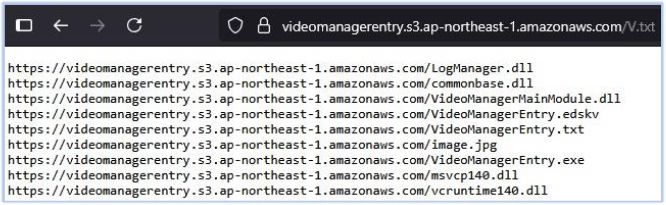
It serves as a first-stage malware, functioning as a downloader that downloads a package of files from the cloud-based storage service referred to as S3 (Simple Storage Service), provided by Amazon Web Services (AWS). First, it accesses the ‘V.txt’ file from the URL hxxps[:]//videomanagerentry[.]s3[.]ap-northeast-1.amazonaws[.]com/V.txt to obtain the file names of the payload components. It then proceeds to download these files, which are hosted on the same cloud storage:
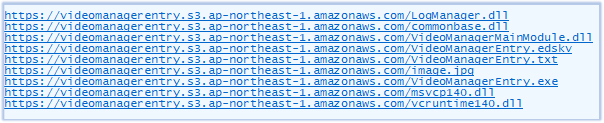
The downloaded files include one legitimate executable (VideoManagerEntry.exe), malicious DLLs (commonbase.dll, LogManager.dll), a file with encrypted content (VideoManagerEntry.edskv), and additional supporting files required for its operation. The downloaded files are saved in the user profile directory (C:\Users\username) within a folder named using a standard 128-bit UUID (Universally Unique Identifier) or GUID (Globally Unique Identifier) format, followed by ‘@27’. For example: ********-****-****-****-************@27, where each asterisk represents a hexadecimal character. This identifier is unique to each compromised host.
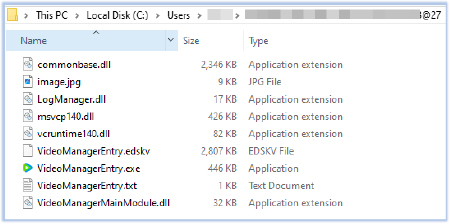
The downloader WindowsFormsApp.exe executes VideoManagerEntry.exe and terminates itself. VideoManagerEntry.exe is a legitimate executable signed with a valid digital certificate:
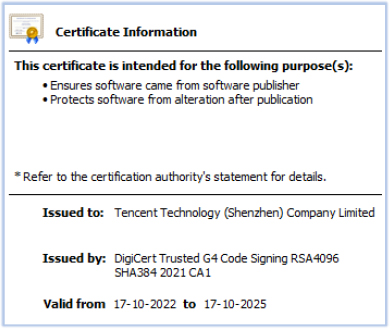
VideoManagerPlayer.exe is used as a front cover to load and execute the malicious DLL files. Both commonbase.dll and LogManager.dll are signed with the same certificate as the downloader WindowsFormsApp.exe, which has since been revoked by the issuing Certificate Authority.
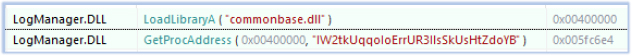
VideoManagerPlayer.exe loads LogManager.dll, which contains only two imports—LoadLibraryA and GetProcAddress, in its Import Address Table (IAT). These are used to dynamically load commonbase.dll from the same directory.
commonbase.dll is the primary malware component responsible for executing all malicious activities. It is a 32-bit GUI-based DLL, developed using Delphi:
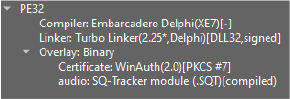
VideoManagerEntry.edskv is a file with a custom extension that contains encrypted content and has a file size of approximately 2.74 MB.
At this stage, commonbase.dll first reads the encrypted content of the ‘.edskv’ file and decrypts it in memory:
It also performs several memory-to-memory operations while reading and decrypting the .edskv file content, serving as an anti-analysis measure to obfuscate its runtime behavior. These operations hinder debugging tools from accurately tracing the execution flow or identifying malicious intent. This technique is commonly observed in malware and packers, where internal buffers are manipulated, code segments are shuffled, or memory sections are overwritten to confuse disassemblers and evade dynamic analysis platforms.
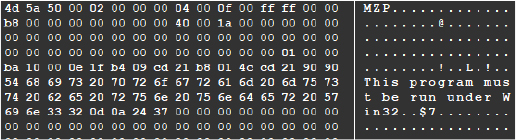
The decrypted content reveals another Delphi-based 32-bit DLL:
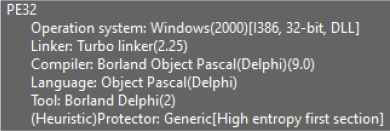
This DLL, decrypted from the ‘.edskv’ file, contains critical configuration and communication-related data and settings used by commonbase.dll during its operation. It also reveals a potential C2 server: kimhate[.]com:1516.
EdskManager RAT creates multiple hidden windows, including some that are initially visible but later concealed, to support its internal operations.
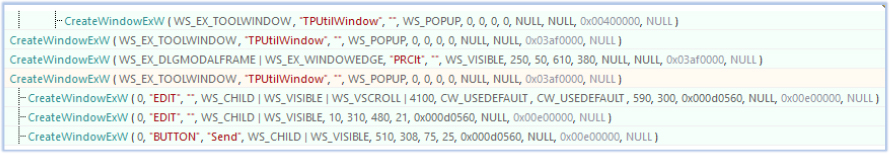
The malware creates two types of hidden windows using the CreateWindowExW function, each serving a distinct purpose in its operation while maintaining stealth and enabling remote control, potentially through HVNC (Hidden Virtual Network Computing).
The first type of hidden window uses the WS_EX_TOOLWINDOW and WS_POPUP styles, creating a borderless, invisible window that doesn’t appear in the taskbar. With zero dimensions, it remains hidden and acts as a background listener.
The second type of window is created with WS_EX_DLGMODALFRAME | WS_EX_WINDOWEDGE and WS_VISIBLE styles, giving it the appearance of a system dialog. Though initially visible, it is hidden almost instantly to operate in the background, potentially facilitating remote communication.
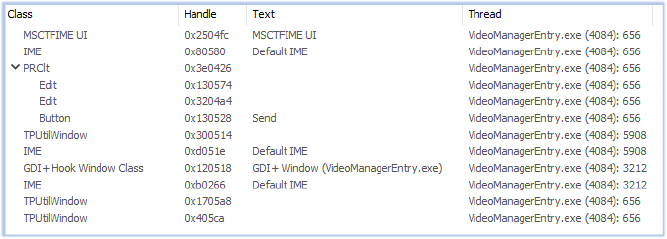
One example of this is the PRClt class window, which briefly appears for a fraction of a second before being hidden. It features a text box and a send button, resembling a chat interface, though its visibility is so fleeting that it’s nearly unnoticeable.
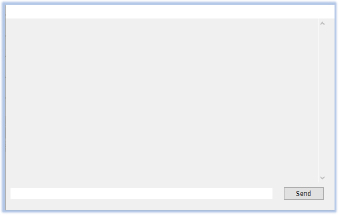
Both types of windows align with the malware’s HVNC (Hidden Virtual Network Computing) capabilities, which allow an attacker to remotely control the infected machine without any visible signs of activity on the victim’s screen.
The primary indicator of HVNC usage is the presence of a hidden window operating invisibly on the victim’s system, featuring a text box and a send button. HVNC tools typically enable attackers to establish a virtual desktop session that remains hidden from the user, allowing remote interaction without visual feedback. In this case, the malware uses the hidden window to facilitate communication with the C2 server without the victim’s awareness.
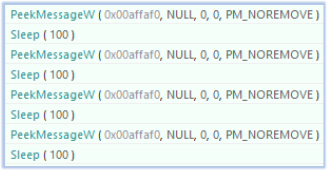
Further evidence of HVNC is observed in the malware’s continuous use of PeekMessageW in a loop—a function commonly used in event-driven models to monitor messages or instructions. This behavior indicates the malware is actively waiting for commands, likely delivered via the C2 server. The absence of visible interaction, combined with persistent message listening on a hidden window, strongly suggests remote control through a virtual session, a hallmark of HVNC functionality:
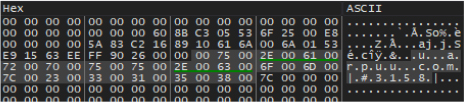
EdskManager RAT uses the socket API to establish communication with its C2 (Command and Control) server. The .itext section of commonbase.dll contains critical C2-related data, including the domain and port information:
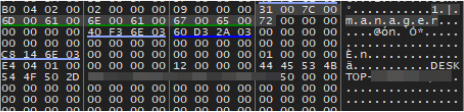
On the other hand, the decrypted .edskv file (DLL) provides additional configurations, including the communication format used by EdskManager RAT and the obfuscation method applied to the transmitted content.
Within a larger memory block, the space is allocated for the buffer, used by the send() function. The initial communication message, ‘1|manager,’ is first written directly into this memory block, sourced from the decrypted edskv memory region.
This message is then compressed using zlib and written to the buffer, used by the send() function:
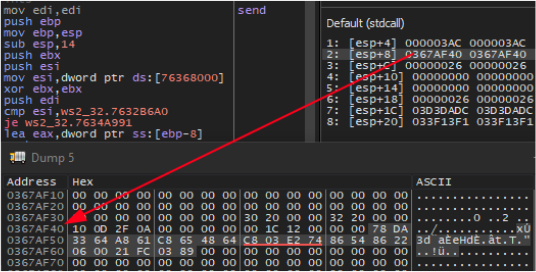
The compressed message is then sent to u[.]arpuu[.]com:3158, which resolves to the IP address 56[.]155[.]36[.]99:
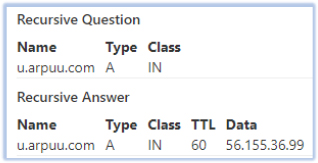
The C2 server responds with a zlib-compressed message containing CltID, likely referring to the client identifier, followed by a random string that appears to serve as an identification token:
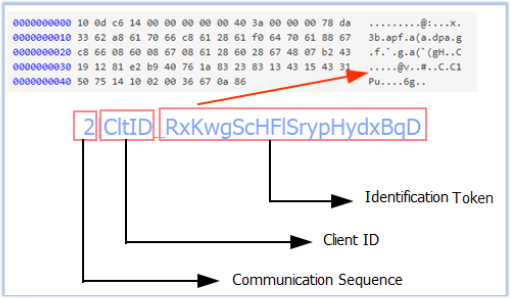
The number preceding the message indicates the communication stage—for example, 1 represents the initial communication sent to the C2, while 2 refers to subsequent communications. The identification string sent by the C2 differs with each communication session.
The malware on the host acknowledges the C2 response by sending a message containing host-specific information, including user group, Windows version, CPU details, installed antivirus software, and display driver information.
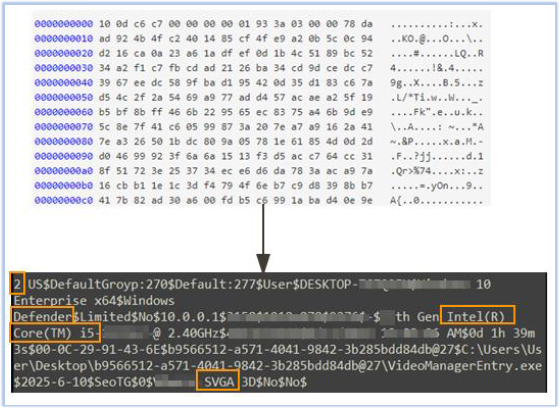
Following this, EdskManager RAT repeatedly sends |5 to the C2 server, likely indicating a status update, a specific command identifier, or signaling that it is awaiting further instructions from the C2:
During analysis, EdskManager RAT was also observed functioning as an information-gathering tool, specifically targeting browser extensions across popular web browsers, such as Chrome, Brave, and Edge. It systematically inspects installed extensions on the victim’s system, likely aiming to identify those that may contain sensitive information or offer opportunities for further exploitation.
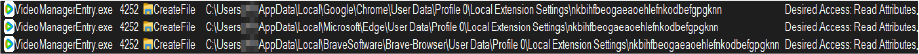
This activity, known as extension enumeration, is commonly used to profile the victim’s environment, assess potential vulnerabilities, or locate valuable data for exfiltration. For example, the RAT may be searching for password managers, cryptocurrency wallets, or other extensions that store sensitive user data, such as authentication tokens or financial information.
This behavior, while not directly stealing data, serves as a reconnaissance step. The malware collects information about installed extensions to determine whether any can be targeted for data theft or exploitation. In some cases, it may also check for security-related extensions, such as antivirus tools or privacy blockers, to evade detection or attempt to disable them. Although primarily preparatory, this step lays the groundwork for subsequent stages involving data exfiltration or exploitation of vulnerabilities within the identified extensions.
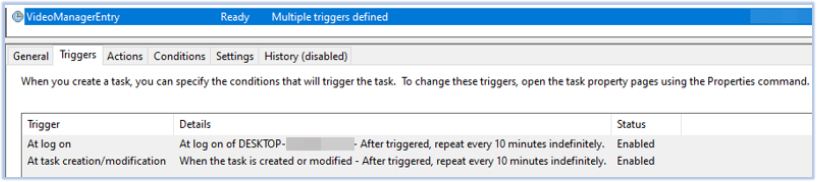
EdskManager RAT establishes persistence by creating a scheduled task and setting an autorun registry entry:
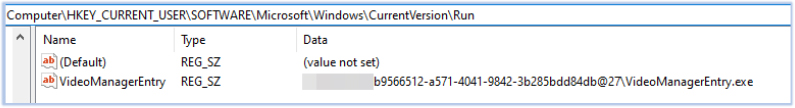
Another persistence mechanism is established by adding a shortcut path to the current user’s Startup folder. The malware creates a .lnk file in the C:\Users\Public\Documents directory, which is linked to execute on system startup:
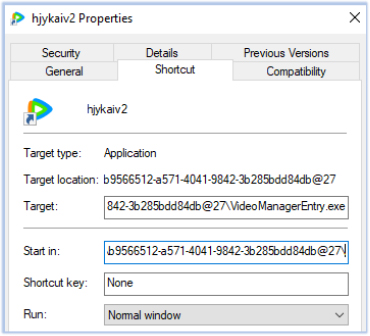
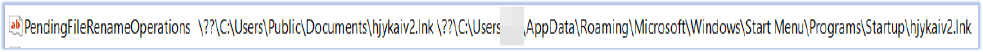
It then created the PendingFileRenameOperations key under the Session Manager registry (Computer\HKLM\SYSTEM\CurrentControlSet\Control\Session Manager) to move the shortcut to the current user’s Startup folder. This ensures that VideoManagerEntry.exe is automatically executed upon user login after a system reboot:
Analyzing EdskManager RAT offers important insights into its operational features. Based on the findings, the following points summarize the key features of this RAT malware:
EdskManager RAT demonstrates a wide range of capabilities designed to ensure stealth, persistence, and control over compromised systems. Through a multi-stage infection chain and the use of encrypted configuration files, the malware maintains a covert and flexible architecture. Its ability to communicate stealthily with command-and-control servers, switch between multiple C2 domains, and leverage HVNC for invisible remote access highlights its adaptability and sophistication. Additionally, the RAT performs extensive system reconnaissance, evades analysis through memory-level obfuscation, and establishes persistence via multiple mechanisms. With features such as keylogging, clipboard monitoring, and potential data exfiltration, EdskManager RAT poses a serious threat to targeted environments, emphasizing the need for proactive detection and defensive strategies.
As threats like EdskManager RAT continue to evolve, it is essential for organizations to implement robust cybersecurity measures and proactive defense strategies to mitigate associated risks. Users should exercise caution when opening files from untrusted sources or clicking on unfamiliar links, particularly those promoting suspicious software or content. Implementing strong cybersecurity practices—such as using reputable antivirus solutions, regularly updating all software, and staying alert to social engineering tactics—can greatly enhance protection against sophisticated malware. Additionally, educating users about potential threats and fostering a security-conscious culture within organizations are critical steps in reducing the risks posed by EdskManager RAT and similar threats.
| S/N | Indicators | Type | Context |
| 1 | 85bae6fe73a9e2bf0819a6f60adfc458392a7a56de23f10d3bdddb8e3a97a8ec | File | WindowsFormsApp.exe |
| 2 | 16e01dd4c60462c0a870bf55ec987514e122f27b306858e73f71a8ca4b896423 | File | WindowsFormsApp.exe |
| 3 | 3514868a52911536a884e2cc7aea6b2ed4610ee81f03022c326e57500eeb463d | File | WindowsFormsApp.exe |
| 4 | 94292cd6fd027073928bdca471a66582954235e84ac6d8e8bb80fe623a6ad4bf | File | WindowsFormsApp.exe |
| 5 | d19ca1798eaa49f3a803294d240c7bcf121b8c1f0f261aa7d7a30011fafb2385 | File | WindowsFormsApp.exe |
| 6 | e380ed76df494f9c2d219c91e695d5459baa545db0348a9dbc9c28ad742a30bb | File | WindowsFormsApp.exe |
| 7 | a04f1e64fd7e2ef6decbfd2e26ad2a3066862fbe039a3bbed5cc9b6eacd4edf9 | File | mpextms.exe |
| 8 | 288006abe0e58125af3fcfb35556198171bd4895188f4d9b755183d7f21b1e0e | File | UIHost Module |
| 9 | 21a4e405282159cfb3ddda661ad239e401cdbf02556facc30135bee6ee084539 | File | commonbase.dll |
| 10 | bb180e01f4cbb88a5f15b84f11d11ca7751584b1104c11717ba19b1cb7c47288 | File | LogManager.dll |
| 11 | 7f7f25bd4a4aa47755d844acfe3c88ff9bf38b03670eb32e0888a576c0e0d6a2 | File | VideoManagerEntry.edskv |
| 12 | U[.]arpuu[.]com | Domain | C2 |
| 13 | kimhate[.]com | Domain | C2 |
| 14 | https[:]//videomanagerentry[.]s3[.]ap-northeast-1[.]amazonaws[.]com | URL | Malware source |
| 15 | Computer\HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Run\VideoManagerEntry | Registry Key | Persistence mechanism |
| 16 | Task Name: VideoManagerEntry | Scheduled Task | Persistence mechanism |
| No. | Tactic | Technique |
| 1 | Initial Access (TA0001) | T1566: Phishing T1189: Drive-by Compromise |
| 2 | Execution (TA0002) | T1204: User Execution |
| 3 | Persistence (TA0003) | T1547.001: Registry Run Keys / Startup Folder T1053.005: Scheduled Task |
| 4 | Defense Evasion (TA0005) | T1622: Debugger Evasion T1140: Deobfuscate/Decode Files or Information T1564.003: Hidden Window T1027.013: Encrypted/Encoded File T1497: Virtualization/Sandbox Evasion |
| 5 | Discovery (TA0007) | T1082: System Information Discovery T1087.001: Local Account T1010: Application Window Discovery T1217: Browser Information Discovery T1007: System Service Discovery T1124: System Time Discovery T1673: Virtual Machine Discovery |
| 6 | Collection (TA0009) | T1115: Clipboard Data T1005: Data from Local System T1056: Input Capture T1113: Screen Capture |
| 7 | Exfiltration (TA0010) | T1041: Exfiltration Over C2 Channel |
| 8 | Command and Control (TA0011) | T1001: Data Obfuscation |
rule EdskManager_RAT_Artifacts
{
meta:
description = “Detects components and persistence artifacts of the EdskManager RAT malware”
author = “CYFIRMA Research”
category = “malware”
malware_family = “EdskManager RAT”
strings:
// File names
$filename1 = “WindowsFormsApp.exe”
$filename2 = “commonbase.dll”
$filename3 = “LogManager.dll”
$filename4 = “VideoManagerEntry.edskv”
// Registry and task artifacts
$regkey = “SOFTWARE\\Microsoft\\Windows\\CurrentVersion\\Run\\VideoManagerEntry”
$taskname = “VideoManagerEntry”
// URLs/domains (some obfuscated for safety)
$url1 = “videomanagerentry.s3.ap-northeast-1.amazonaws.com”
$c2_1 = “u.arpuu.com:3158”
$c2_2 = “kimhate.com:1516”
condition:
uint32(0) == 0x4550 and (
2 of ($filename*) or 2 of ($url1, $c2_1, $c2_2, $regkey, $taskname)
)
}