


DIGITAL FRONTLINES : INDIA UNDER MULTI-NATION HACKTIVIST ATTACK
At CYFIRMA, we are committed to offering up-to-date insights into prevalent threats and tactics employed by malicious actors, targeting both organizations and individuals. In July–August 2025, India faced a surge of cross-border cyberattacks combining data breaches, DDoS, defacement, phishing, and malware. Pakistani group, Team Insane Pakistan, claimed High Court server breaches; Sylhet Gang-SG disrupted the Defence Ministry site; and Russian-aligned RuskiNet warned of “Operation Trinetara.” Indian groups retaliated under “Operation Vasudev Strike,” hacking Pakistan’s Ibn-e-Sina University. Indonesian group Raizo defaced an Indian transport site, while phishing cloned the eChallan portal, and a fake Income Tax notice spread malware with Chinese indicators—highlighting the growing multinational hacktivism against India’s digital infrastructure.
India’s digital infrastructure has increasingly become a focal point of cross-border cyber hostilities. In July–August 2025, a series of high-impact incidents—including judicial server breaches, government website disruptions, retaliatory defacements, phishing schemes, and malware campaigns—highlighted the growing scale, sophistication, and multinational nature of hacktivist operations targeting Indian entities. These attacks, spanning actors from Pakistan, Bangladesh, Russia, Indonesia, and likely China, underscore a shifting threat landscape where hacktivism and cybercrime blend to challenge national security and public trust.
Targeted Breaches: Team Insane Pakistan allegedly infiltrated High Court servers in Punjab & Haryana and Andhra Pradesh, extracting millions of judicial records, FIRs, and login credentials to publicly embarrass Indian institutions.
DDoS Campaigns: Sylhet Gang-SG disrupted the Indian Ministry of Defense website on Independence Day using distributed denial-of-service attacks and published check-host proofs to amplify impact.
Strategic Announcements: RuskiNet pre-signaled its “Operation Trinetara,” linking cyber retaliation against India to the Palestine conflict to create psychological pressure before actual attacks.
Retaliatory Hacking: Indian collectives Shadow Phantom, Team Red Eagle, and Shadow Protocol coordinated “Operation Vasudev Strike,” compromising Pakistan’s Ibn-e-Sina University site and exposing admin credentials as a show of offensive capability.
Defacement as Messaging: Indonesian group Raizo defaced India’s transport website with political slogans to broadcast dissent and signal cross-border solidarity among hacktivists.
Phishing & Data Harvesting: Attackers cloned the Ministry of Road Transport’s eChallan portal to collect citizens’ sensitive details (names, PAN, mobile numbers, DOBs) under the guise of official services.
Malware Delivery via Social Engineering: A fake Income Tax “Penalty Notification” ZIP file lured victims into executing a 43 MB malicious installer hosted on a suspicious IP. Metadata with Simplified Chinese resources indicated likely Chinese actor involvement, blending spear-phishing with advanced malware tactics. The payload masqueraded as an official document, and upon execution, established communication with the remote IP 103.97.128.77, performed file and registry operations, created persistence through process injection, and concealed its activity via configuration files. The campaign demonstrates sophisticated use of social engineering—inciting panic to drive users to run the malware—as well as technical tradecraft in evasion, data exfiltration, and multi-stage infection flow, thus posing a significant risk to targeted Indian taxpayers.
Data Leaks
On August 14, the Pakistani hacktivist group Team Insane Pakistan claimed to have breached the High Court of Punjab and Haryana’s official servers in India. They shared the targeted government domains and linked the attack with Pakistan’s Independence Day celebration.
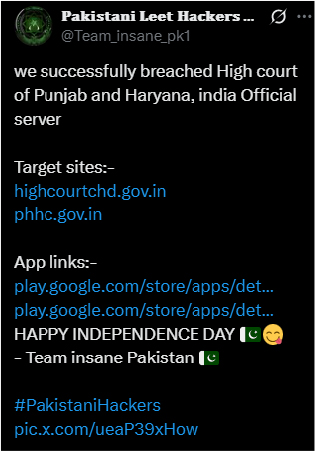
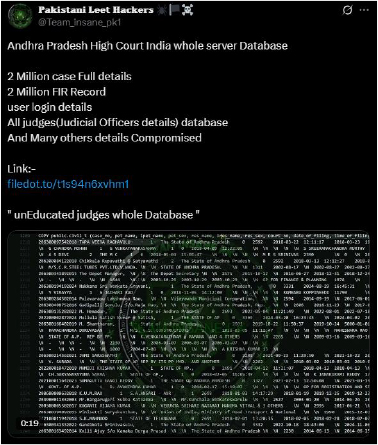
On August 14, the Pakistani hacktivist group Team Insane Pakistan claimed to have breached the Andhra Pradesh High Court server in India. They alleged that over 2 million case details, 2 million FIR records, user login data, and judicial officers’ databases were compromised. The group also mocked the judiciary by calling it an “uneducated judges whole database.”
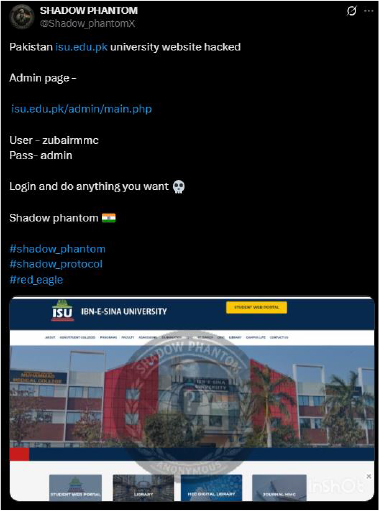
On 15th August, in retaliation, the Indian cyber hacktivist group Shadow Phantom hacked into Pakistan’s Ibn-e-Sina University (isu.edu.pk) website. They exposed the admin panel credentials publicly, allowing unrestricted access to the university’s system as part of their cyber campaign.
DDoS Attack
On August 15, the hacktivist group Sylhet Gang-SG claimed responsibility for taking down the Indian Ministry of Defense website. They shared a check-host link as proof of the disruption.

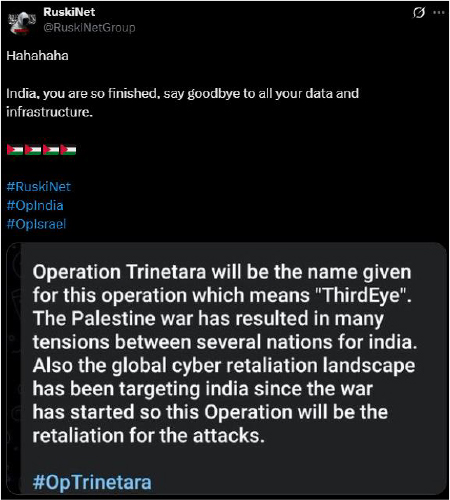
On 1st August, the hacktivist group RuskiNet announced Operation Trinetara (meaning “Third Eye”), warning India of a large-scale cyber retaliation. They linked the campaign to the Palestine conflict and threatened India’s data and infrastructure as part of their coordinated operation.
Hacktivist-Groups Co-Operation
On 12th July 2025, the Indian cyber hacktivist collective Shadow Phantom, Team Red Eagle, and Shadow Protocol announced Operation Vasudev Strike. They declared that on 15th August, the world would witness the power of Indian hackers, positioning the campaign as a retaliation against Pakistan, Bangladesh, Indonesia, and Turkey.
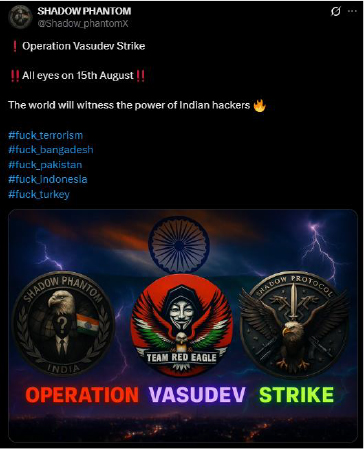
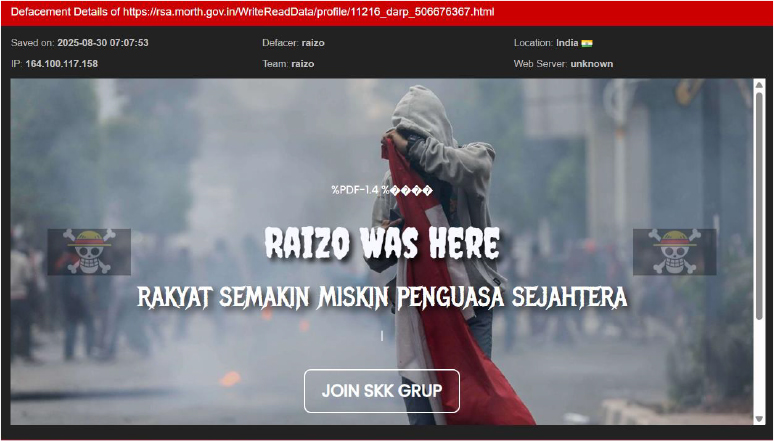
Defacement
On 30th August 2025, the cyber group Raizo defaced the Indian website rsa.morth.gov.in, leaving a message that read “RAIZO WAS HERE” alongside political slogans in Indonesian, suggesting dissatisfaction with government leadership. The attack highlighted emerging cross-border hacktivism, as the group’s statement and iconography were directed at Indonesian audiences, marking India as a target in ongoing digital conflicts involving multiple countries.
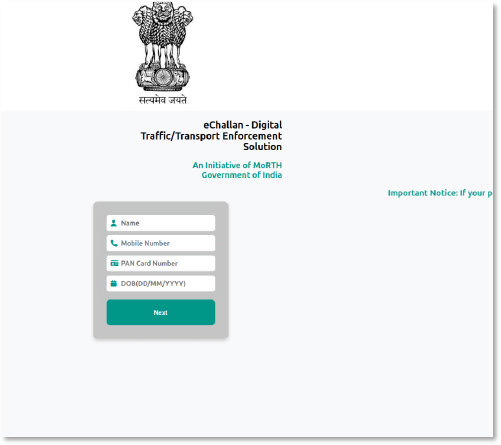
Phishing
The Indian Ministry of Road Transport and Highways’ eChallan portal was targeted in a cyber incident involving impersonation. Attackers replicated the official interface, likely aiming to deceive users and harvest sensitive details, like names, mobile numbers, PAN card numbers, and dates of birth, demonstrating the serious threat of impersonation and data theft against India’s digital infrastructure.
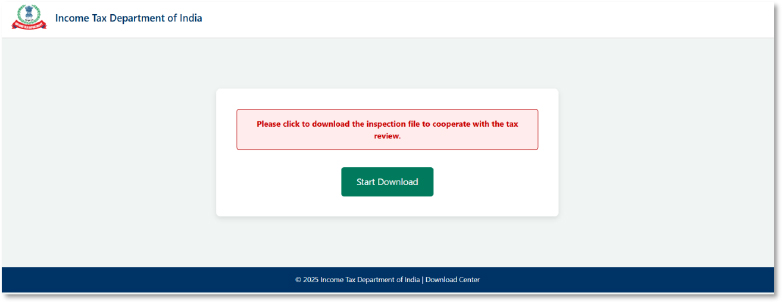
Malware
The presented material illustrates a sophisticated phishing campaign impersonating the Income Tax Department of India, emerging prominently in 2025 during the tax filing season. Attackers have crafted convincing fake websites and fraudulent email communications styled with official logos, terminologies, and formats consistent with government-issued tax penalty notices. These deceptive notices warn recipients of alleged tax compliance deficiencies and mandate urgent document submissions through clickable links or downloadable files.
Victims are deceived into downloading a malicious zip archive labeled “Tax Penalty Notification.zip,” which contains an executable named “103.97.128.77#ClientSetup.exe.” Behavioral and network analysis evidence demonstrates that this payload engages in active communication with a remote IP (103.97.128.77), performs file system manipulations, registry key accesses related to system control, and attempts to conceal itself using configuration files with commands to encrypt, terminate processes, and establishes persistent footholds by creating additional processes, such as “MANC.exe,” “svchost.exe,” “SMSS.exe,” “FSHost64.exe,” and “sysaid.exe,” some of which evade detection by security vendors. The malware stores configuration and log data in local folders like “install” and “log,” utilizes files, such as “YTSysConfig.ini” to set exfiltration parameters (e.g., ServerIP 103.97.128.77), and leverages network activity—including TCP and UDP communications—to receive commands and exfiltrate stolen information. Through these mechanisms, the campaign blends social engineering with advanced post-exploitation, enabling data theft, evasive persistence, and remote control over compromised systems.
The fraudulent campaign leverages social engineering to cause panic and urgency, pushing victims toward actions that compromise their systems and potentially lead to data exfiltration or broader compromise. Official warnings from the Income Tax Department and cybersecurity advisories emphasize that authentic tax communications never request passwords, OTPs, sensitive personal information, or file downloads from unverified sources. Taxpayers are urged to verify all notices directly through sanctioned portals (domains ending in @incometax.gov.in), avoid clicking unsolicited links, and report suspected phishing activities to designated authorities.
This case exemplifies the intersection of social engineering, malware deployment, and network operations exploitation within targeted phishing attacks aiming to defraud and compromise Indian taxpayers amid the critical tax filing season in 2025.
A webpage styled in the theme of the Income Tax Department of India prompts the user to download an inspection file in order to cooperate with a tax review. The central message urges clicking “Start Download” to proceed.
A browser window displays a fake office memorandum from the Income Tax Department, Government of India, combining both Hindi and English text. The notice cites Section 271(1)(c) and requires submission of documents within 72 hours, providing a “Download Documents” button to obtain the required list.

A close-up of a zipped folder labeled “Tax Penalty Notification.zip” is shown, representing the downloaded file referenced on the websites.
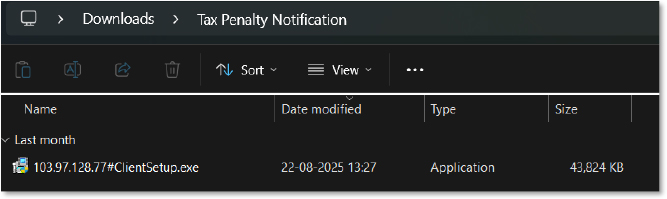
A Windows file explorer window shows the “Tax Penalty Notification” folder within Downloads, displaying the file “103.97.128.77#ClientSetup.exe” with a size of 43,824 KB.
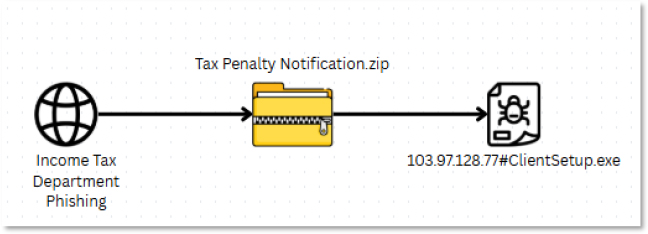
A diagram illustrates the phishing flow: starting with an Income Tax Department-themed phishing site, leading to the download of Tax Penalty Notification.zip, which contains the malicious file “103.97.128.77#ClientSetup.exe”.
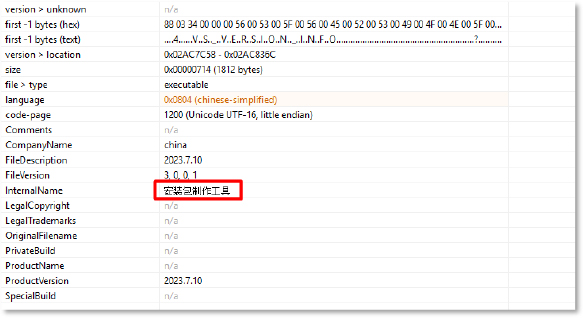
The metadata shows details of an executable file. The language is specified as Chinese-simplified (code-page 1200, Unicode UTF-16), with the company name listed as “china” and the file version 3.0.0.1. The internal name field contains Chinese characters, “???????”, which translates to “Setup Package Creation Tool”, and the file description/version date is “2023.7.10”.
Malware contains a code snippet that implements a conditional check (“if (data_427548 == 1)”) and calls TerminateProcess, using GetCurrentProcess() if the condition is met, immediately terminating the current process.
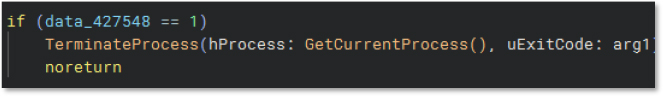
The following code snippet shows handling window messages and UI updates by the malware process. It includes a call to WaitForSingleObject, message passing with SendDlgItemMessageA, UpdateWindow, memory setting routines, and a call to GetSystemDirectoryA, and string assignment to “install”.
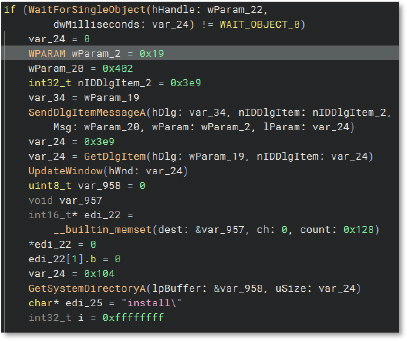
This code snippet shows updates to dialog UI elements, calls to UpdateWindow, setting dialog item texts, string assignment to “SETUP”, and a FindResourceA call. It references a global variable data_423834.
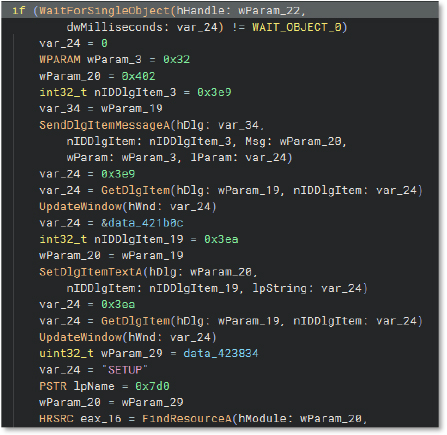
The following displays code performing filename memory initialization, process file name retrieval via GetModuleFileNameA, and conditional assignment between “updatec.exe” and “clientsetup.exe” based on logic checks.
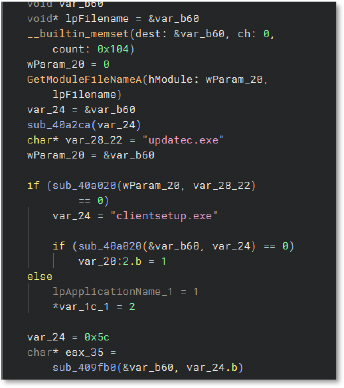
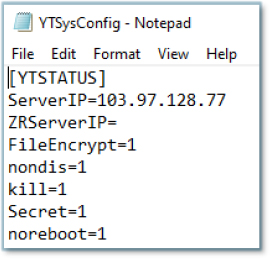
A code snippet shows buffer and memory initialization, string construction for “YTSysConfig.ini”, and assignment of “YTSTATUS” as the application name title in the dialog/property configuration.
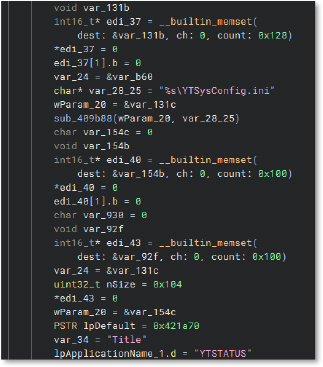
This displays code that uses GetPrivateProfileStringA to read values from an INI configuration file, specifically looking up keys “Title” and “Secret” with reference to the application name “YTSTATUS”.
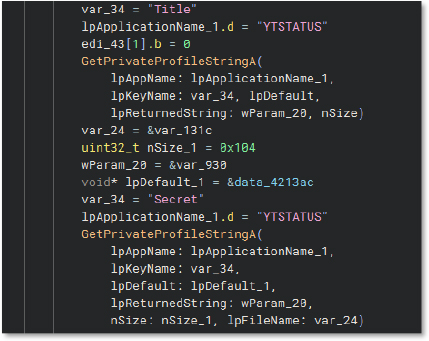
The code performs conditional checks related to “setuptool.exe” and sets application parameters, initializes buffer memory, and assigns the string “/setuptool” under certain conditions.
Dynamic Analysis
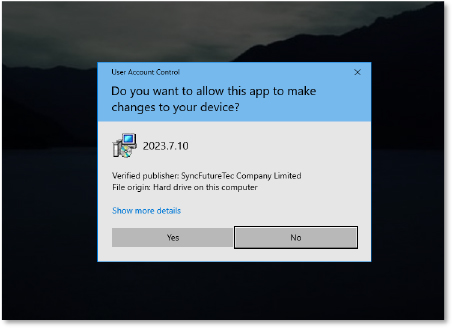
The Windows User Account Control (UAC) prompt displayed the application name as “2023.7.10”, the verified publisher is “SyncFutureTec Company Limited.”
The image shows a process tree after executing the file “103.97.128.77#ClientSetup.exe”. It creates another process with persistence, named “MANC.exe”. Under it, there are child processes including “svchost.exe,” “SMSS.exe,” “FSHost64.exe,” and “sysaid.exe.” Some processes use “Microsoft 基础应用程序” (Microsoft Basic Application).
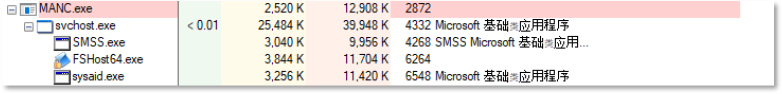
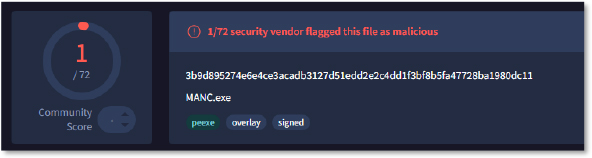
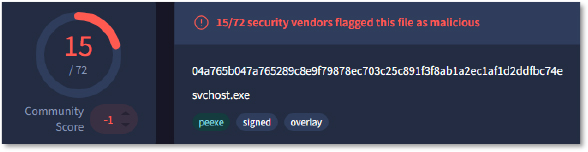
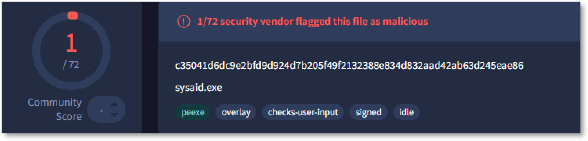
The executables (MANC.exe, svchost.exe, sysaid.exe) have lower detection by the security vendors, while SMSS.exe and FS… have no detection yet.
A process activity log shows file operations performed on the file “YTSysConfig.ini” located in “C:\Users\malwin\Desktop\Tax Penalty Notification”. The listed actions include CreateFile, WriteFile, and CloseFile APIs, all executed successfully by a process with PID 5760.
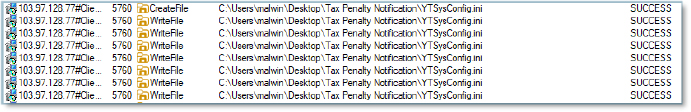
The configuration file “YTSysConfig.ini”. includes several parameters under the header [YTSTATUS], notably specifying ServerIP as 103.97.128.77. This IP address is associated with data exfiltration activity.
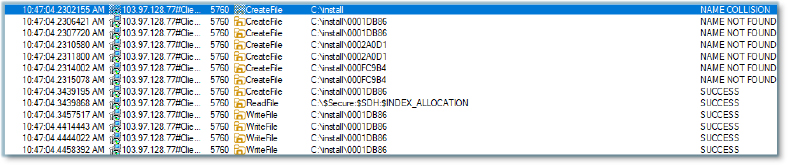
A process activity log records CreateFile and WriteFile operations involving the folder “C:\install” and its contents. Several filenames (e.g., C:\install\0001DB86) are referenced.
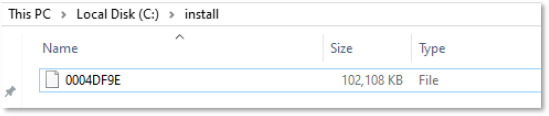
A directory listing displays the contents of the install folder:
The contents of the “log” folder reveal multiple text documents, such as “AdoBase”, “AssistantThC”, “FSHost32”, “installok”, and others, along with file sizes and modification times.
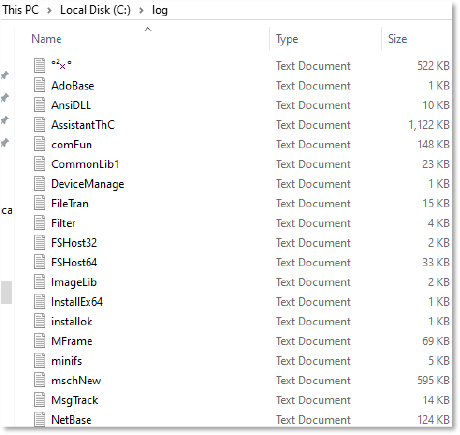
The contents of the “UfsdCrypt” file (C:\log folder) include entries for UD_Initialize, MyQueryDosDevice, and StartFilter, with time stamps and device references, containing both English and Chinese text.
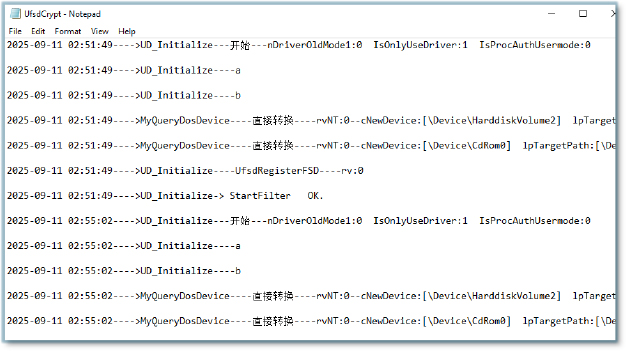
The process svchost.exe (PID 4332) established TCP connections to the remote address 103.97.128.77, using ports 6671 and 6681, respectively, and listening on UDP port 6677, indicating command receiving capability of the malware.
The events of July–August 2025 highlight a significant escalation in hacktivist-driven cyber operations against India, with coordinated attacks spanning data breaches, DDoS disruptions, defacements, phishing schemes, and malware campaigns. The involvement of multiple foreign actors—including groups from Pakistan, Bangladesh, Russia, Indonesia, and likely China—illustrates a shift from isolated incidents to organized, multinational campaigns targeting critical institutions and public-facing services. India’s retaliatory actions signal a growing cycle of offensive and defensive cyber activity in the region. Together, these incidents underscore the urgent need for stronger threat intelligence, proactive defense measures, and cross-agency coordination to protect national security and public trust in digital infrastructure.
| No | Indicator (SHA-256) | Remarks |
| 1 | https://rto[.]dc7[.]live | URL |
| 2 | https://wtqz3bn75j7ha49f82k[.]dewakartu[.]top/ | URL |
| 3 | https://fhauifhyileydhfl[.]com/ | URL |
| 4 | https://yunvxi[.]com/ | URL |
| 5 | https://enzedi[.]com/ | URL |
| 6 | 54660fd2ff160f70a3ae5d8e54fca990562e4bfee1f8fdc882261e35420d209b | SHA256 |
| 7 | b75dec6f19a3dec025862a0d6e7dd565ad49c327cd85c21d5135ccffef60e68f | SHA256 |
| 8 | 103.97.128.77 | IP |
| 9 | 202.189.10.112 | IP |