



This report examines the reasons, impacts, and responses into the recent cyberattacks in Morocco, which some believe could be linked to the long-standing dispute between Morocco and Algeria over the Western Sahara region. As tensions between the two countries escalate, cyberattacks are expected to increase, targeting government websites, critical infrastructure, military sites, and key industries, such as oil and gas. Pro-Israeli hacktivist groups have claimed responsibility for a recent attack, citing Morocco’s support for Palestine as a motivating factor. This surge in cyber threats highlights the urgent need for strengthened cybersecurity measures across all sectors in Morocco.
Recent cyberattacks in Morocco highlight the growing prominence of cyber warfare in modern geopolitical conflicts. In an era where international relations are increasingly complex, digital attacks have become a powerful tool for state and non-state actors to inflict damage and assert influence.
The involvement of a pro-Israel hacktivist group in these incidents illustrates the influential role of non-state actors in shaping the global cyber landscape. Motivated by ideological and political objectives, such groups can carry out impactful cyber operations with far-reaching consequences. The Moroccan cyberattack serves as a stark reminder of the intricate dynamics between state and non-state entities in cyber warfare. This report explores these incidents in further detail.
Pro-Algeria Hacktivist Groups:
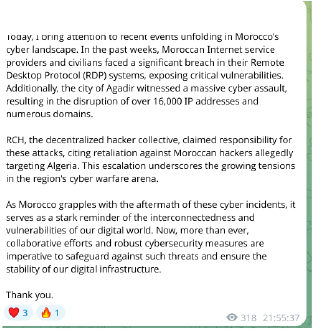
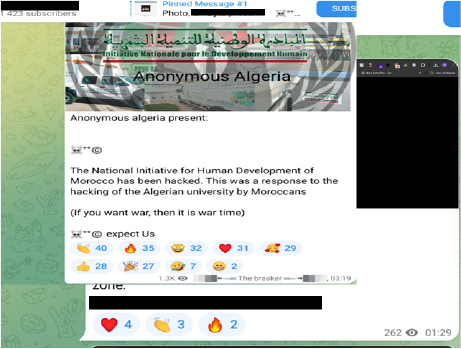
Breakdown:
The Moroccan online journal Maroc Hebdo confirmed they were targeted by a cyberattack on November 16, 2024, which came shortly after the release of the magazine’s latest issue featuring the cover story ‘Algeria Wants War.’ The cyberattack is believed to be a DDoS originating from Algerian hackers, and it was still ongoing at the time of this report’s publication.

The cyber threat landscape has seen a significant recent evolution, with advanced threat actors utilizing increasingly sophisticated tactics to target organizations across a wide range of sectors. Notable among these are hacker collectives like ‘Cyb3r Drag0nz’, ‘Team 1919’, and ‘THE NIGHT HUNTERS’, who have emerged as prominent players in the growing wave of cyberattacks against entities in Morocco.
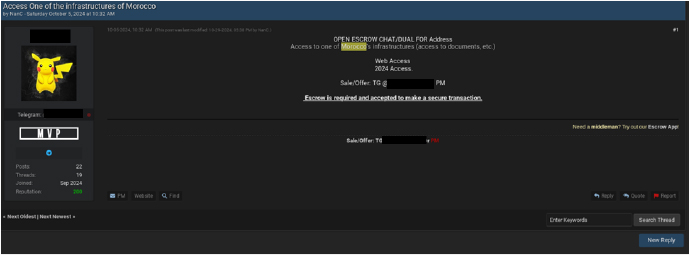
Threat Actor: on October 5, 2024, a threat actor claimed to offer secure transactions for access to one of Morocco’s infrastructure systems, including access to documents and other related assets. Access details are provided, with web access granted upon confirmation of the transaction. The actor instructed interested parties to communicate via Telegram or private message to finalize the terms of the offer.
Threat Actor: This threat actor claimed to have leaked a sample database associated with Résidences Universitaires Al Massira (ruam[.]ma) and the Ministry of National Education. The leaked database from the Ministry of National Education contains login details for 30,000 students.
STORMOUS Ransomware: Last year, the group claimed to sell unauthorized VPN access to Inwi, a telecommunications company based in Morocco. The access allegedly enables bypassing of all security measures, including firewalls and intrusion detection systems, providing entry to the entire network. Additionally, the threat actor employs advanced encryption methods to secure communications, ensuring that access remains strong and resilient against detection attempts.

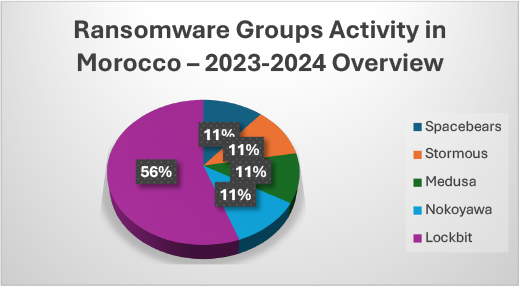
Based on our analysis, we have created a pie chart depicting ransomware attacks observed in Morocco between 2023–2024.
Phishing Campaigns
The relationship between Morocco and Algeria has been historically tense, with ongoing disputes over territory and resources and contention over regional dominance. This tension has spilled over into the cyber domain, with both countries accusing each other of cyberattacks on numerous occasions. The strained relationship between Morocco and Algeria has significant cybersecurity implications and has caused Algeria to be a target for years.
The ongoing tensions create an environment where cyberattacks are more likely to occur, as Algeria will seek any coverts means including in the fifth domain to gain an advantage, increasing the risk of disruptive attacks targeting critical infrastructure, government systems, and private sector entities in Morocco. The cyberattacks also have the potential to escalate, leading to a broader cyber conflict with potentially severe consequences for Morocco’s digital infrastructure and economy.
The threat actors leveraged sophisticated tools and techniques to target Moroccan companies. The primary attack methods used in these cyberattacks included DDoS attacks, web defacement, and ransomware attacks. Below are a few key recommendations that will help to prevent such attacks.
The ongoing cyberattacks against Morocco have targeted various entities across the country, disrupting critical sectors. In response, several cyber threat groups – including the Moroccan Black Army, Moroccan Cyber Forces, Moroccan Soldiers, Moroccan CyberAliens, and Moroccan Dragons (along with their allies) – have escalated their operations, launching retaliatory attacks against Algeria and other pro-Israel nations. This wave of cyber activity appears to be driven by geopolitical tensions. The result of this assessment may encourage the victim country to prioritize and allocate resources to address cybercrime, thereby strengthening their safety measures.