



The CYFIRMA Industry Report delivers original cybersecurity insights and telemetry-driven statistics of global industries, covering one sector each week for a quarter. This report focuses on the Telecommunications & Media industries, presenting key trends and statistics in an engaging infographic format.
Welcome to CYFIRMA infographic industry report, where we delve into the external threat landscape of the telecommunications and media industries over the past three months. This report provides valuable insights and data-driven statistics, delivering a concise analysis of attack campaigns, phishing telemetry, and ransomware incidents targeting telecommunications and media technology and organizations.
We aim to present an industry-specific overview in a convenient, engaging, and informative format. Leveraging our cutting- edge platform telemetry and the expertise of our analysts, we bring you actionable intelligence to stay ahead in the cybersecurity landscape.
The telecommunications and media sectors experienced 21 campaigns, a significant count in comparison to other industries. This is due to notable interest from both nation-state APTs, driven by their strategic objectives in targeting these sectors, as well as financially motivated groups.
The distinct increase in observed campaigns during June and July aligns with the discovery of the Barracuda ESG vulnerability, intensified activity from the Lazarus Group, and a series of ransomware incidents involving FIN7, FIN11, and TA505 threat actors.
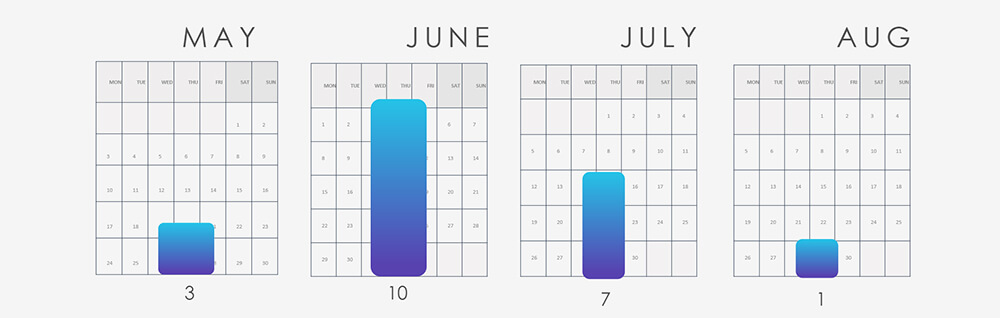
In addition to Lazarus Group, FIN7, FIN11, and TA505, other prominent suspected threat actors are various APTs linked to the Chinese nexus of nation-state activity.
It’s important to highlight that MISSION2025 serves as a central point for Chinese APT operations, with several instances of “Pandas” suspected to have connections within the TA threat group.
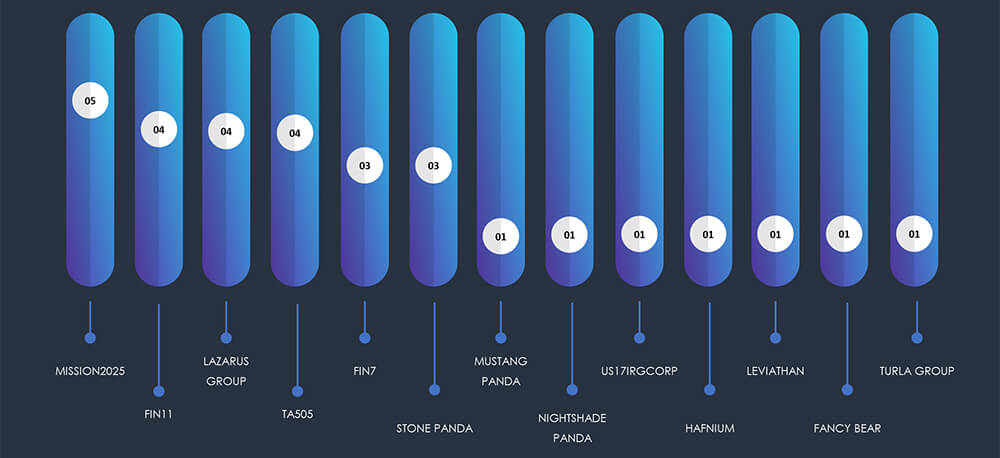
The attack campaigns targeting organizations within the telecommunications and media sectors closely align with the strategic goals of the nation-state APTs involved. Notable is a surge in South Korea, directly corresponding to intensified activity by North Korean threat actors. Moreover, Japan takes the lead as the most targeted country, surpassing even the USA. This trend is tied to the strong interest of Chinese APTs and their strategic aims. Lastly, India is experiencing escalating attention from APTs, reflecting its expanding role in global geopolitics.
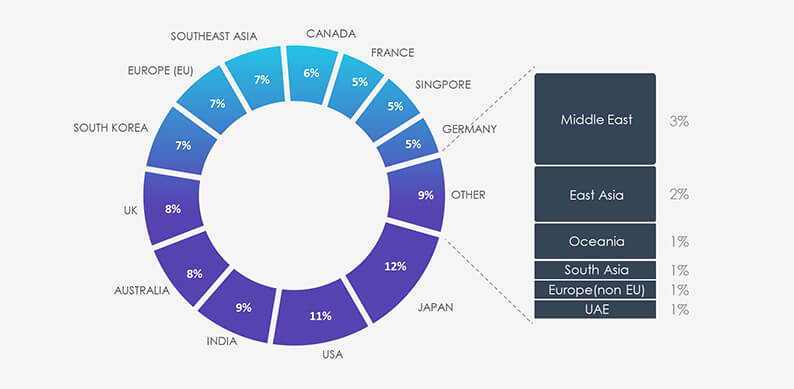
Due to the overlapping nature of monitoring telemetry, further breakdown beyond the top 10 countries is calculated for regions rather than individual countries to maintain clarity.
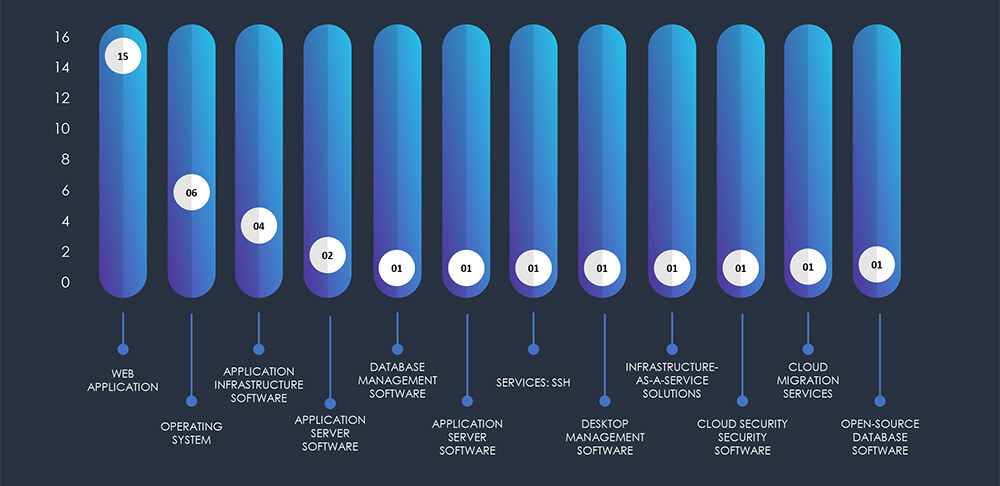
Analysis of targeted technologies shows a focus on exploiting Web Applications, solidifying them as the prime target for APT-driven attacks, followed by Operating Systems, highlighting their continuous vulnerabilities. Finally, the focus on Infrastructure and Cloud Services underscores the broader attack surface that adversaries are increasingly targeting.
Phishing attacks explicitly targeting or impersonating the telecommunications and media industry are among the 4th most popular. Over the past 3 months, CYFIRMA’s telemetry recorded 13,372 phishing attacks out of a total of 208,284, making up 6.42% of the share.
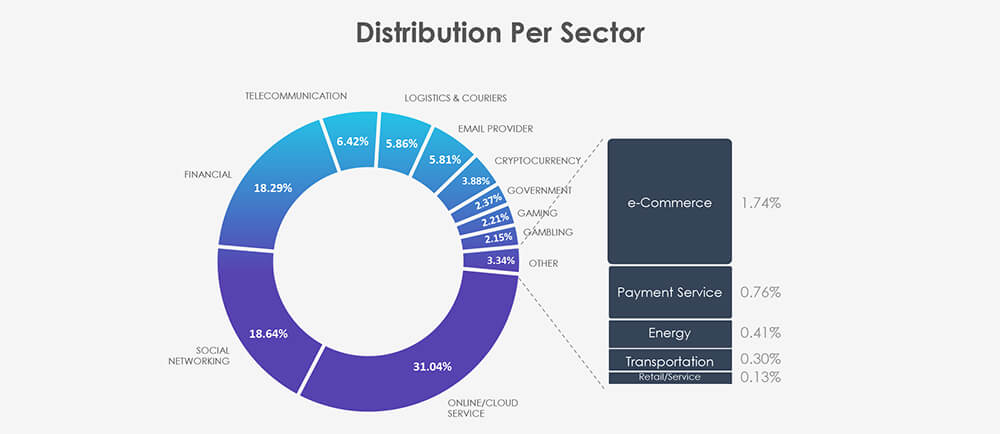
Once more the USA dominates the phishing threat landscape. And more specifically its telecommunications behemoth AT&T. Followed by European powerhouse Orange, Canada’s Bell, and the UK’s BT. Several Singaporean organizations stand out, highlighting an ongoing trend where citizens of the well-off city-state are targeted by lower-level threat actors from neighbouring countries seeking quick profits.
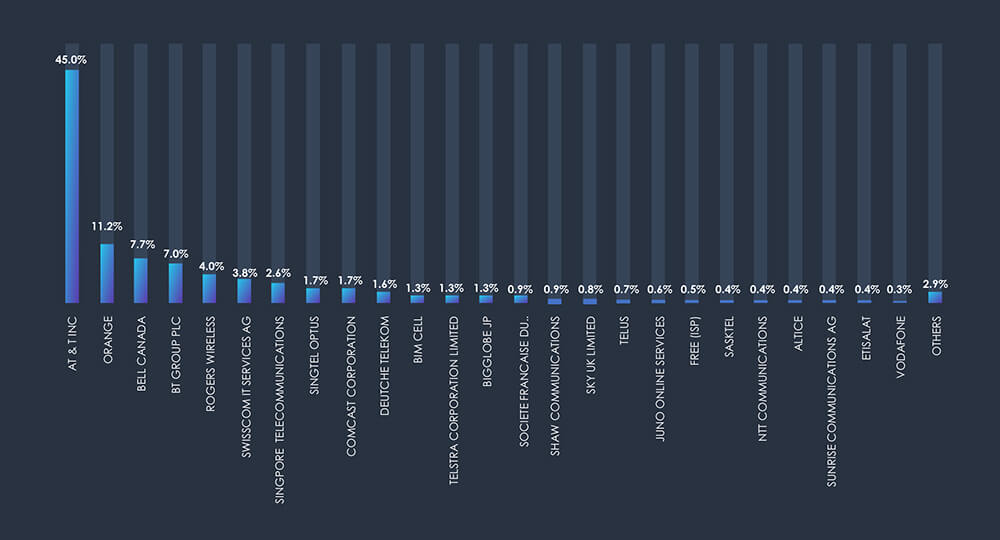
Geographic Distribution
Scams and phishing attempts impersonating local telecommunications organizations have gained global popularity. This approach enables widespread “spray and pray” phishing campaigns at a national level, and this trend is expected to persist. The geographical distribution aligns with the impersonated local service providers.
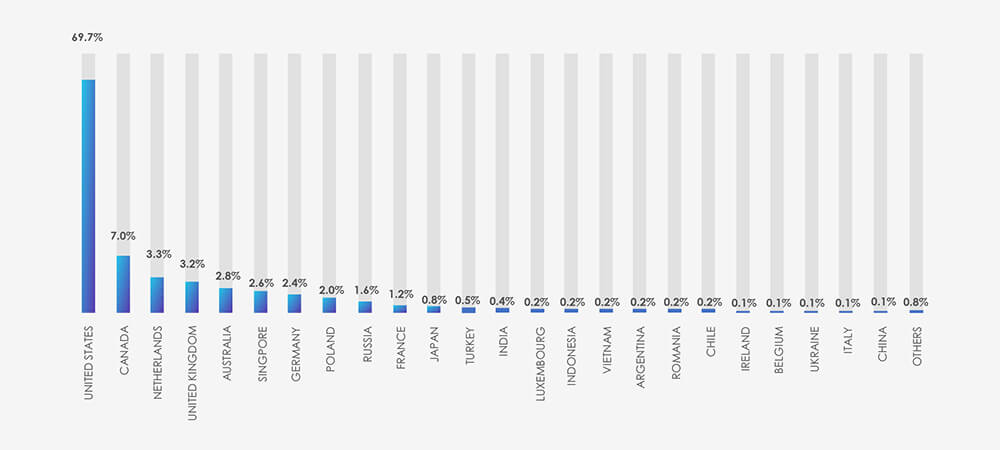
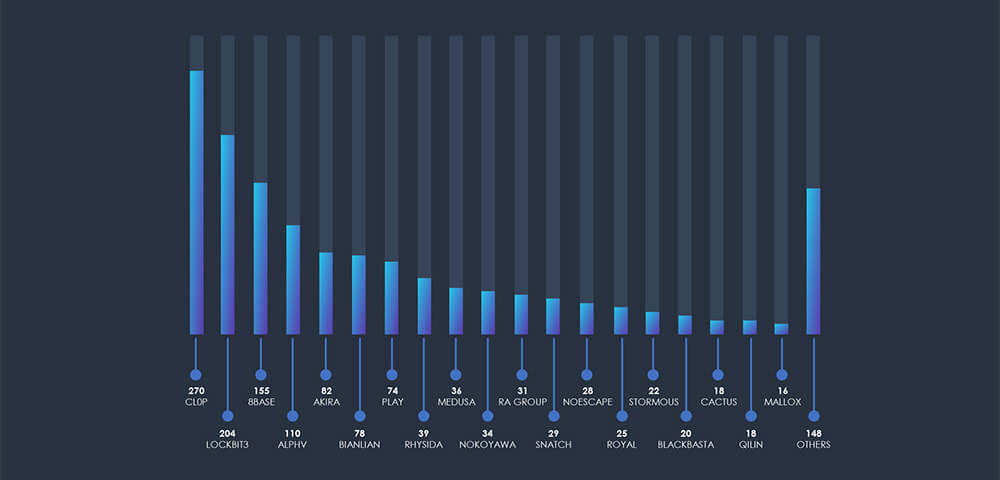
In the past 90 days, CYFIRMA has identified 75 verified ransomware victims within the telecommunications and media sectors. This accounts for 5.2% of the overall total of 1,437 ransomware incidents during the same period, a significant statistic given the industry’s distinct emphasis.
An uptick in July’s figures is attributed to the Cl0p gang, which published 12 victims as part of their extensive spree throughout late June and July.
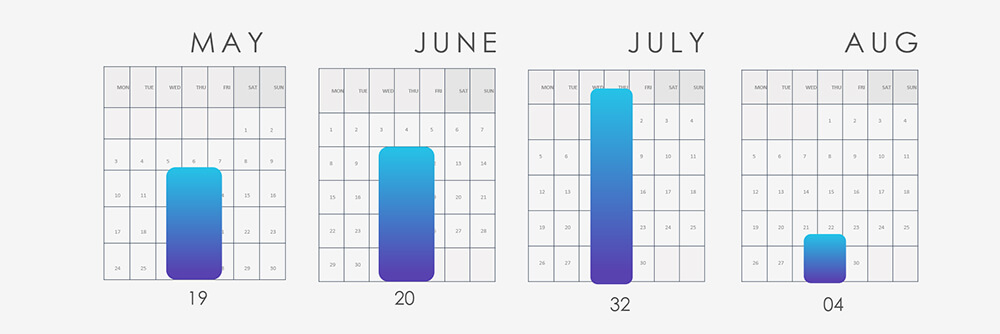
The aforementioned Cl0p gang is distinctly visible in the breakdown chart below. Additionally, the chart highlights that the major groups, namely 8Base, Lockbit3, ALPHV, Akira, and Play, as accountable for the majority of the attacks. Following these are 18 other gangs, each responsible for one or two victims each.
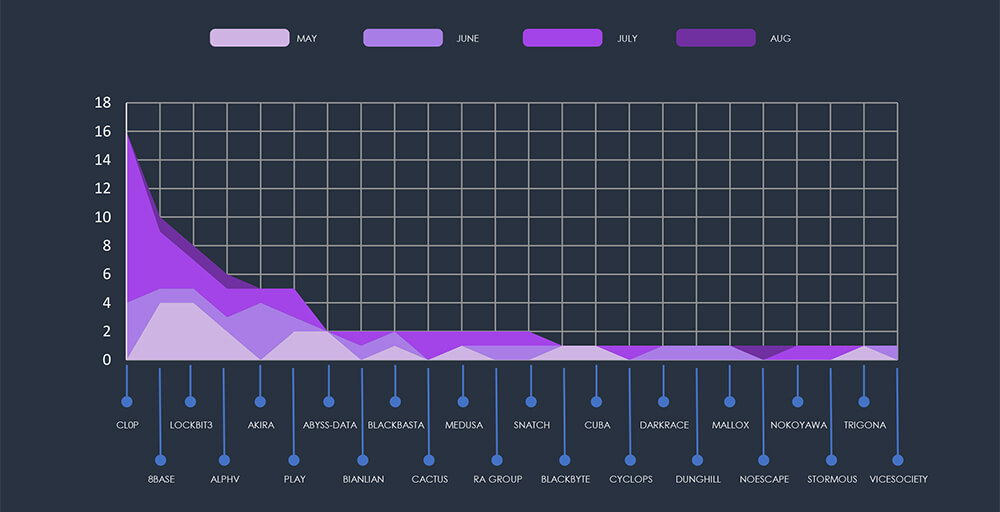
The subsequent chart underscores the dominance of major ransomware gangs, with the top 6 accounting for 70% of all victims. Simultaneously, the chart illustrates how the collective activity of smaller groups contributes to a substantial number of victims.
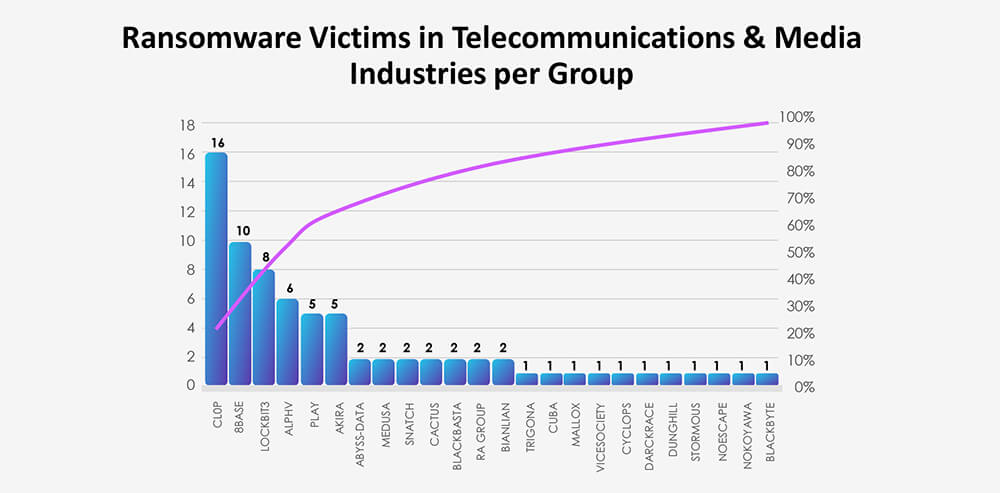
For the most part, the corresponding victim count per group within the telecom and media sectors aligns with the total counts indicated in the chart below. Of particular significance are the Banlian, Rhysida, and Nokoyama groups, which reported comparatively fewer victims in proportion.
Among the 75 identified victims, the United States stands out as the most impacted by ransomware attacks in the telecom and media sectors, accounting for 39 instances. This further solidifies the US’s position as the largest target spanning across industries, given its economic importance and resilient digital infrastructure.
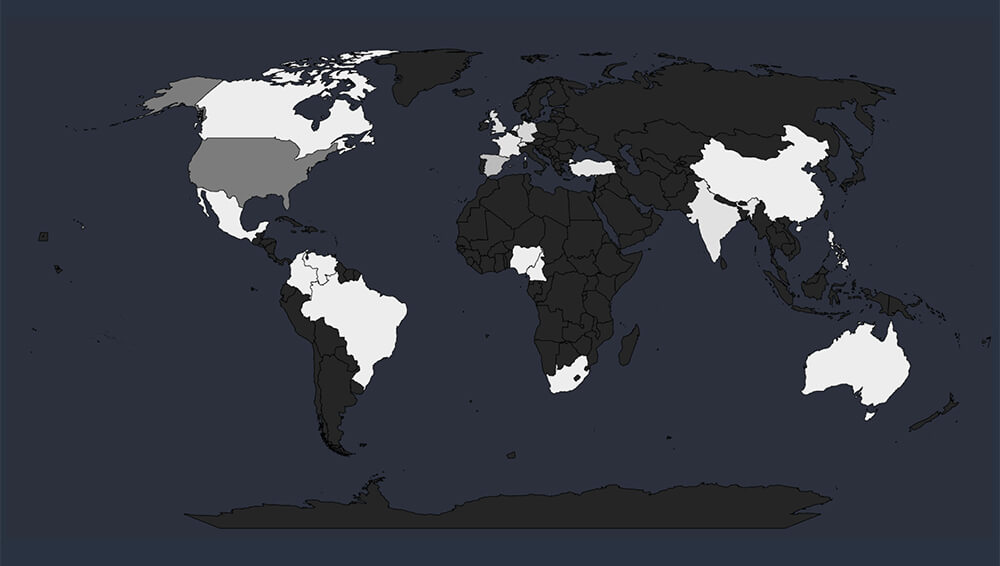
Global Spread – The United States is trailed by Spain (5 victims), and then the United Kingdom, Germany, and Switzerland, each with 3 victims. France, India, the Philippines, and Turkey also have 2 victims each.
Collectively, these countries, along with the USA, make up 81% of all victims.
Geographical Vulnerability – The distribution of victims across all continents underscores the absence of immunity to ransomware threats in any region. Cyber attackers possess the capability to breach and target vulnerable organizations worldwide. This pattern suggests that many threat actors prioritize exploiting vulnerabilities within organizations, irrespective of their geographic locations.
The visual representation below illustrates the distribution of ransomware incidents over the past 90 days, portraying a diverse array of sectors within the telecommunications and media industry.
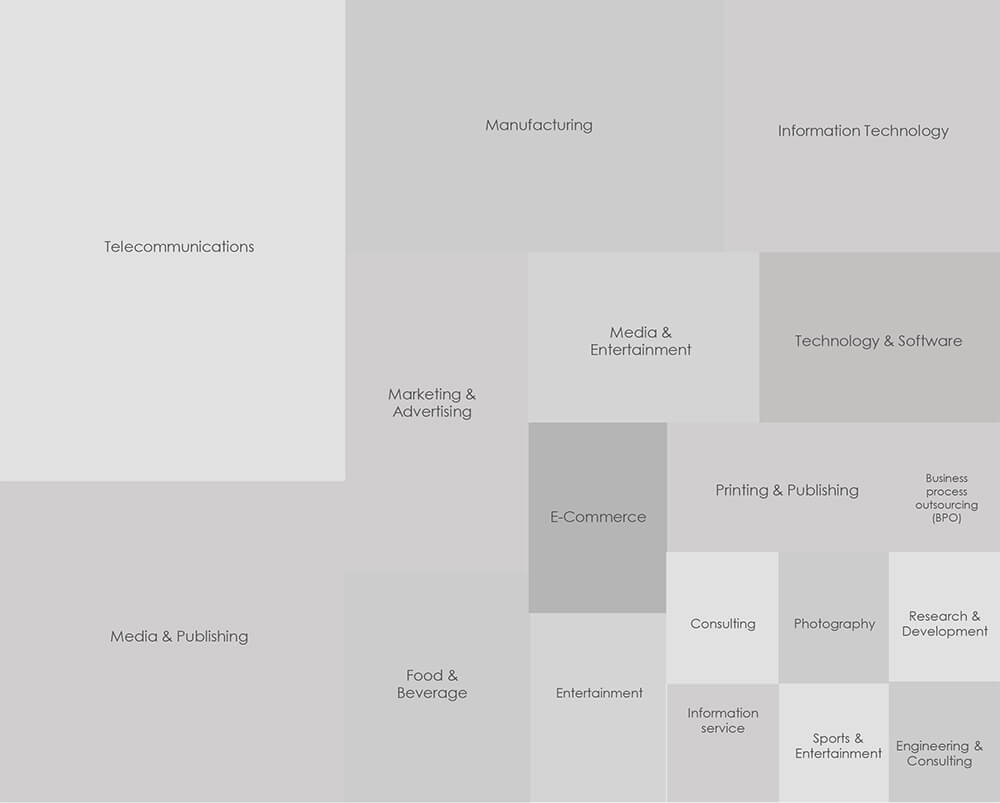
The ransomware’s extensive targeting encompasses a wide array of victims, spanning from national telcos, publishing companies and photography to engineering consulting and fibre cable manufacturing. This highlights the opportunistic character of ransomware attacks, where organizations seemingly unrelated to the cyber domain find themselves unsuspected targets.
The telecommunications and media industries are notably frequent targets of cyberattacks, appealing to both financially motivated cybercriminals and nation- state APT groups.
Local telecommunications providers are especially attractive to foreign entities due to their strategic value. Additionally, these providers often feature prominently in phishing attacks, leveraging their brand recognition for nationwide campaigns.
Media conglomerates and organizations involved in marketing, advertising, and content distribution, including print, publishing, news, and sports, encounter a significant volume of ransomware attacks. The time-sensitive nature of their operations makes them prime targets for extortion.
In summary, the telecommunications and media sectors face consistent and varied cyber threats on a global scale.