



The CYFIRMA Industry Report delivers original cybersecurity insights and telemetry-driven statistics of global industries, covering one sector each week for a quarter. This report focuses on the telecommunications & media industry, presenting key trends and statistics in an engaging infographic format.
Welcome to the CYFIRMA infographic industry report, where we delve into the external threat landscape of the telecommunications & media industry over the past three months. This report provides valuable insights and data-driven statistics, delivering a concise analysis of attack campaigns, phishing telemetry, and ransomware incidents targeting the telecommunications & media industry.
We aim to present an industry-specific overview in a convenient, engaging, and informative format. Leveraging our cutting-edge platform telemetry and the expertise of our analysts, we bring you actionable intelligence to stay ahead in the cybersecurity landscape.
CYFIRMA provides cyber threat intelligence and external threat landscape management platforms, DeCYFIR and DeTCT, which utilize artificial intelligence and machine learning to ingest and process relevant data, complemented by manual CTI research.
For the purpose of these reports, we leverage the following data from our platform. These are data processed by AI and ML automation based on both human research input and automated ingestions.
Leveraging our Early Warning platform data set, we present known attack campaigns conducted by known advanced persistent threat actors. Both nation-state and financially motivated.
Each attack campaign may target multiple organizations across various countries.
Campaign durations can vary from weeks to months or even years. They are sorted by the “last seen” date of activity to include the most relevant ones. Note that this may result in campaigns stacking up on later dates, affecting time-based trends.
Attribution to specific threat actors can be murky due to increasingly overlapping TTPs and commodity tools used. While suspected threat actors in this report are attributed with high confidence, we acknowledge the potential for inaccuracy.
Our data focuses on phishing campaigns rather than individual phishing or spear-phishing emails, which may limit visibility into more advanced single-target attacks.
Our primary focus is on detecting brand impersonation over intended targets. Due to our collection methodology and automation, we may not present comprehensive victimology for phishing campaigns across all industries as some are simply not good phishing lures.
Our data on victims in this report is directly collected from respective ransomware blogs, though some blogs may lack detailed victim information beyond names or domains, impacting victimology accuracy during bulk data processing.
In some cases, there are multiple companies that share the same name but are located in different countries, which may lead to discrepancies in geography and industry. Similar discrepancies occur with multinational organizations where we are not able to identify which branch in which country was actually compromised. In such a case, we count the country of the company’s HQ.
During the training of our processing algorithms, we manually verified results for industry and geography statistics at an accuracy rate of 85% with a deviation of ±5%. We continuously fine-tune and update the process.
Data related to counts of victims per ransomware group and respective dates are 100% accurate at the time of ingestion, as per their publishing on the respective group’s blog sites.
Finally, we acknowledge that many victims are never listed as they are able to make a deal with the attackers to avoid being published on their blogs.
While this report contains statistics and graphs generated primarily by automation, it undergoes thorough review and enhancement for additional context by CYFIRMA CTI analysts to ensure the highest quality and provide valuable insights.
Telecommunications & Media organizations featured in 7 out of the 9 observed campaigns, which is a presence in 77% of campaigns.
Observed Campaigns per Month
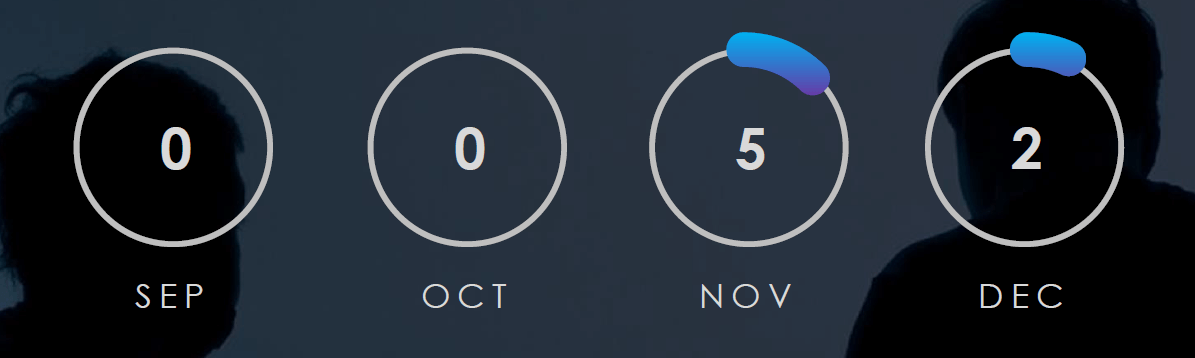
The monthly chart shows a spike in November after a period of generally low campaigns detections in September and October.
Suspected Threat Actors
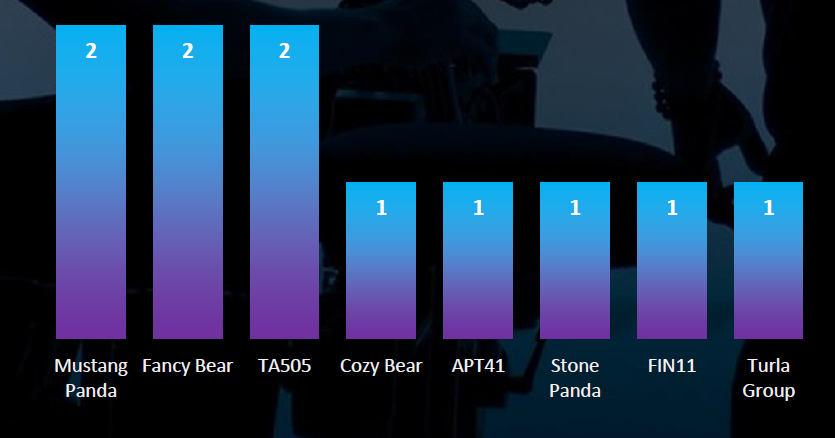
Suspected threat actors are mix a of nation-state and financially motivated groups.
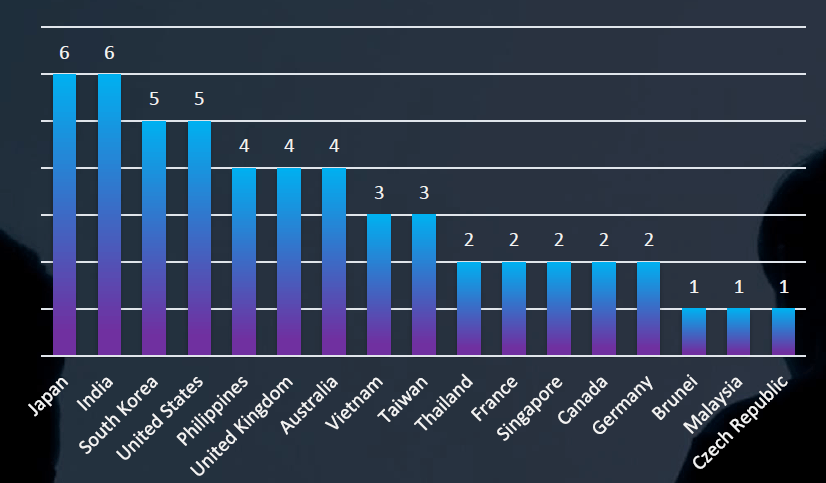
GEOGRAPHICAL DISTRIBUTION
TOP ATTACKED TECHNOLOGY
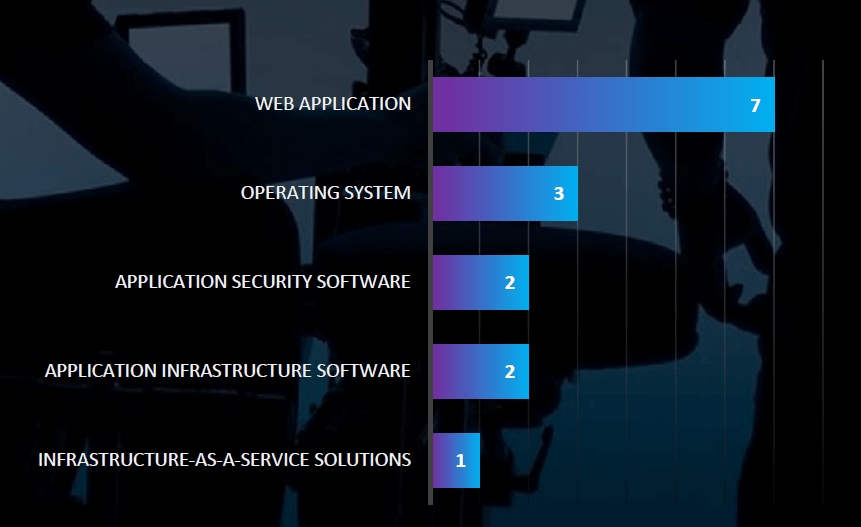
The attack campaign focused on attacking application security software and web applications.
Risk Level Indicator: High
After a period of low detections during the summer months, we are currently witnessing a surge in new detections in November and early December. Specifically, the Telecommunications & Media industry has recorded victims in 7 out of 9 observed campaigns. This highlights the substantial interest shown by nation-state threat actors in this crucial industry within cyberspace operations.
When it comes to suspected threat actors targeting the telecommunications and media sector, nation-state Advanced Persistent Threats (APTs) significantly outnumber financially motivated threat actors. Both Russian and Chinese APTs are highly active, aligning with the current geopolitical landscape, including the observed geographies of victims.
Regarding geographical impact, we notice a strong presence of Asian countries that are of interest to Chinese APTs. These include well-known regional rivals such as India, Japan, the Philippines, Australia, Vietnam, and of course Taiwan, along with Singapore, Brunei, Malaysia, and Thailand. Russian threat actors, on the other hand, seem to focus on European countries, especially in relation to the ongoing UA-RU conflict.
The targeted technologies in the telecommunications and media industry victims included web applications, infrastructure, and operating systems. Additionally, in December, the Mustang Panda campaign utilized USB drive-by attacks exploiting legitimate software.
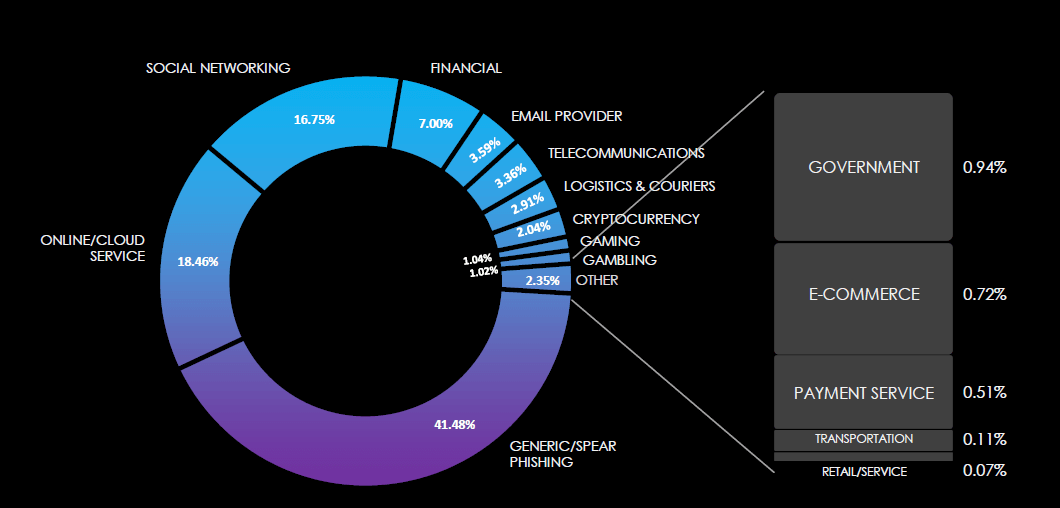
Over the past 3 months, CYFIRMA’s telemetry recorded 10,818 phishing campaigns out of a total of 245,873 that impersonated the telecommunications & media industry, including gaming.
As per the pie chart of all observed campaigns, telecommunications’ share is 3.36% and gaming adds another 1.04%.
Global Distribution of Phishing Themes per Sector
Top 25 Impersonated Brands
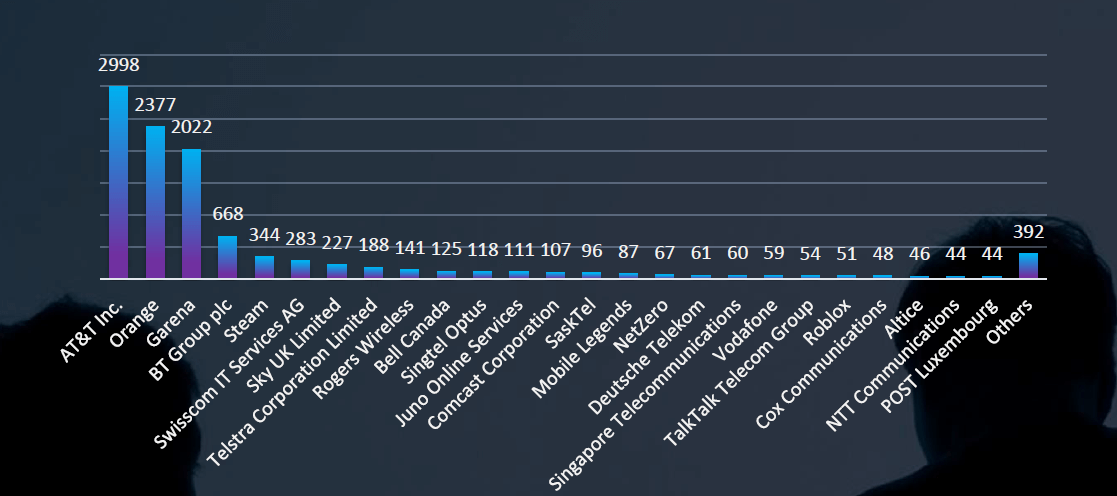
AT&T together with European giant Orange are no surprise on first two places, however, presence of equally high numbers of Singaporean gaming platform Garena is astounding. Furthermore Steam, Mobile Legends or Robolox are recording same volumes as some of the biggest telecommunications providers or broadcasting companies.
Top 20 Countries of Origin
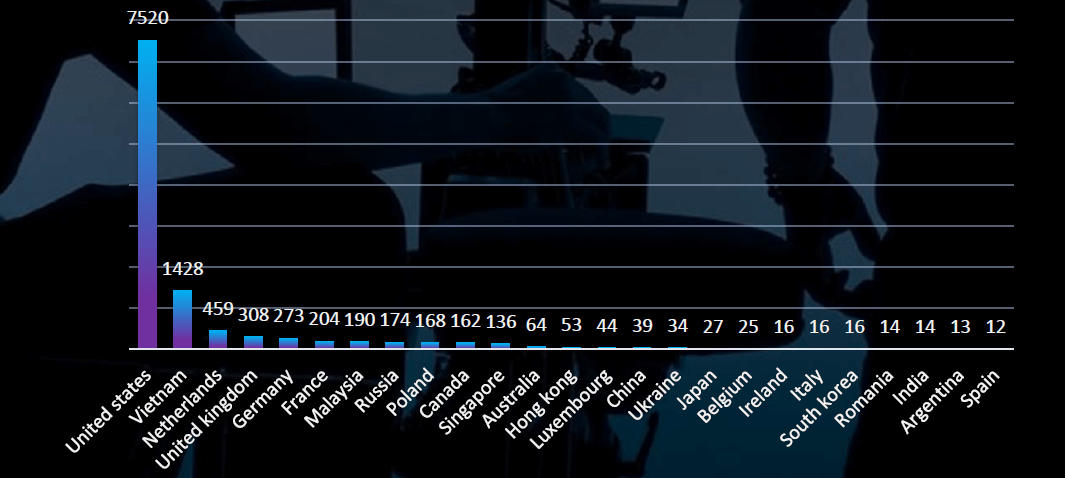
ASN-based original of these phishing campaigns show clear dominance of USA, disproportionate to US brands impersonated, suggesting favorable legitimate infrastructure and availability of compromised systems used as botnets and proxies.
Risk Level Indicator: Medium
The Telecommunications & Media sector has long been a favoured choice for phishing themes. Despite being overshadowed by Online/Cloud Services and Social Networking, they maintain popularity, particularly at a national level in regions where the market is dominated by major providers. Additionally, we are witnessing a steady increase in gaming impersonation, driven by the rising popularity of gaming across various age groups. Notably, the Garena platform, highly favoured in Southeast Asia, has become a prominent phishing lure in the region.
Data based on ASN (Autonomous System Number)-derived origins reveals an intriguing disparity between targeted regions (based on imitated brands) and the countries of origin. The United States stands out significantly as the most frequent country of origin, accounting for approximately 66%, followed by Vietnam at around 12%, and the Netherlands at roughly 4%. This correlation is closely linked to the favourable digital infrastructure in the US, as well as the availability of compromised systems used within botnets and as proxies. Concurrently, Vietnam appears to be evolving into a significant cybercrime hub within Southeast Asia, consistently maintaining a high representation across various industries.
In the past 90 days, CYFIRMA has identified 64 verified ransomware victims within the telecommunications & media industry sectors. This accounts for 4.5% of the overall total of 1,431 ransomware incidents during the same period.
The Monthly Activity Chart
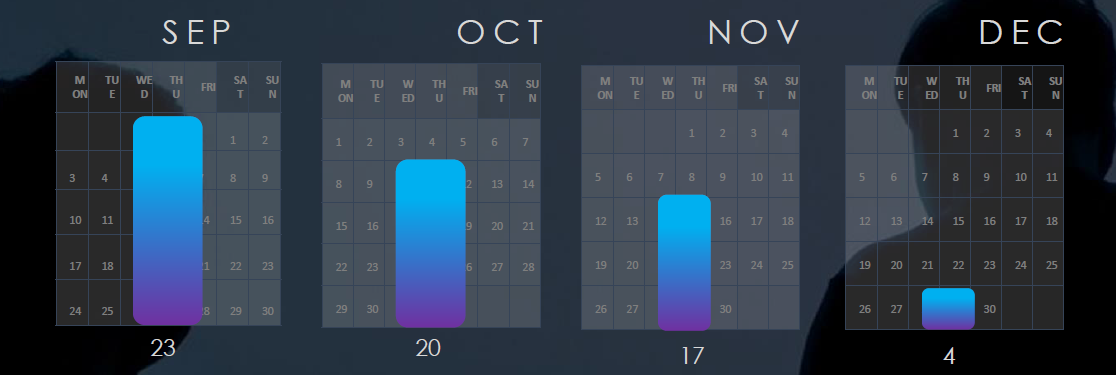
Monthly trends shows slight decrease across months since spike in September.
Breakdown of Monthly Activity by Gangs
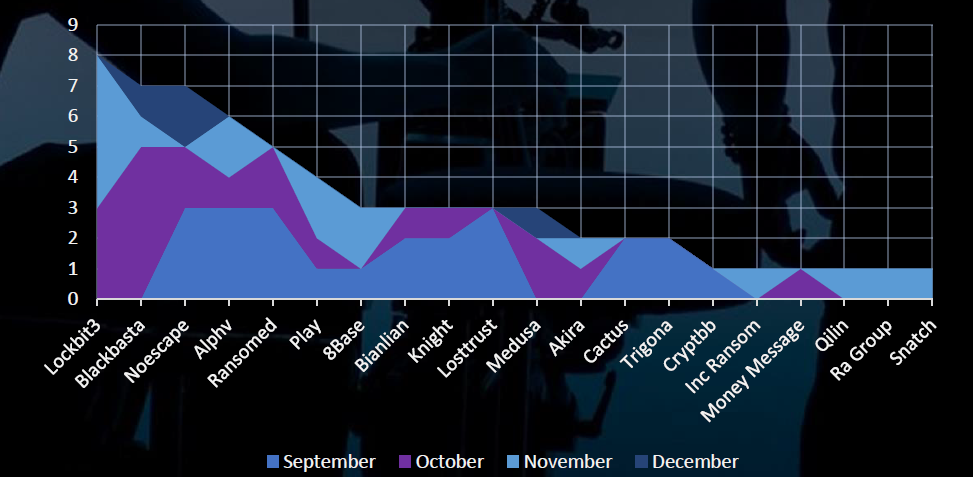
A breakdown of the monthly activity provides insights into per-group activity. For example, LockBit3 was active in October and November, whereas Losttrust, Cactus and Trigona were only in September
Ransomware Victims in Telecommunications & Media Industry per Group
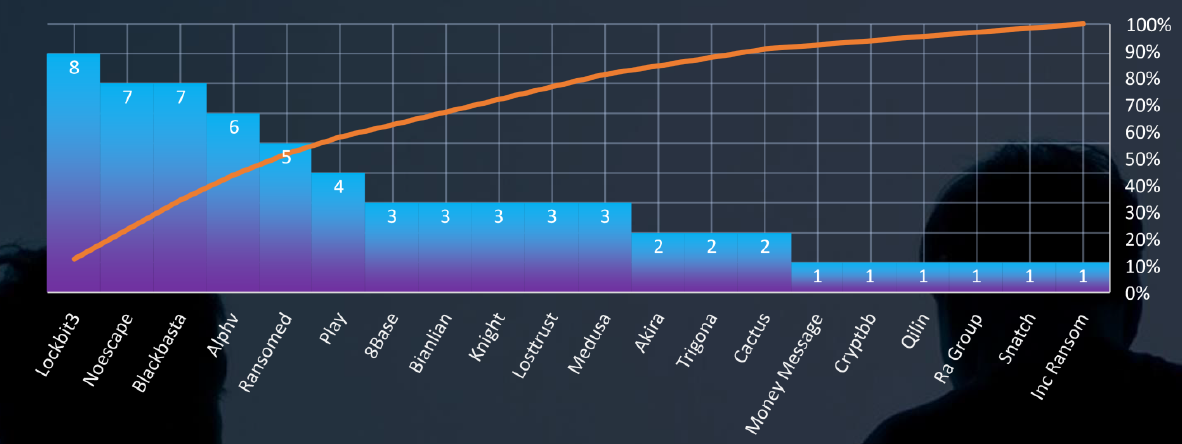
In total 20 out 47 groups recorded telecommunications & media industry organization victims in the past 90 days. The top 5 are responsible for half of them.
Comparison to All Ransomware Victims by Group (Top 20)
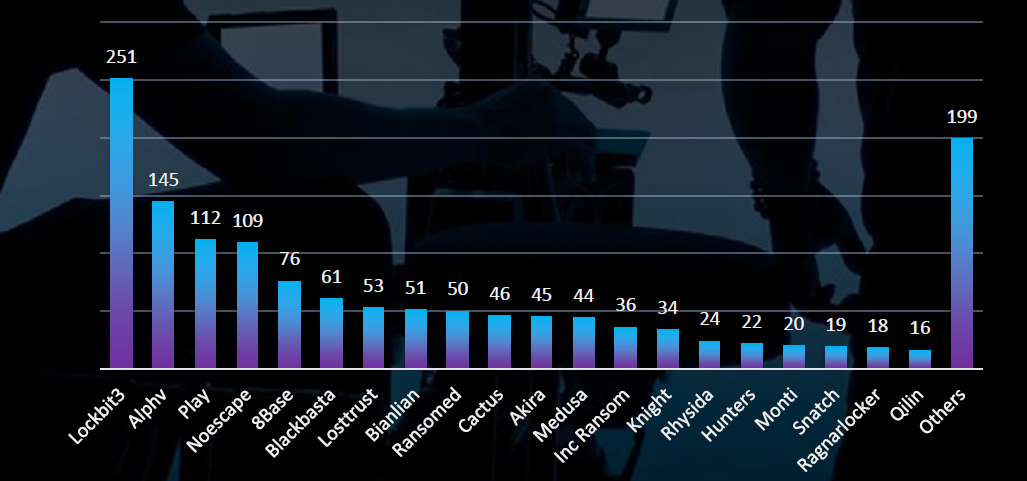
Compared to all recorded victims in the same time period there does not appear to be any outlier with heightened focus on this industry.
Geographic Distribution of Victims
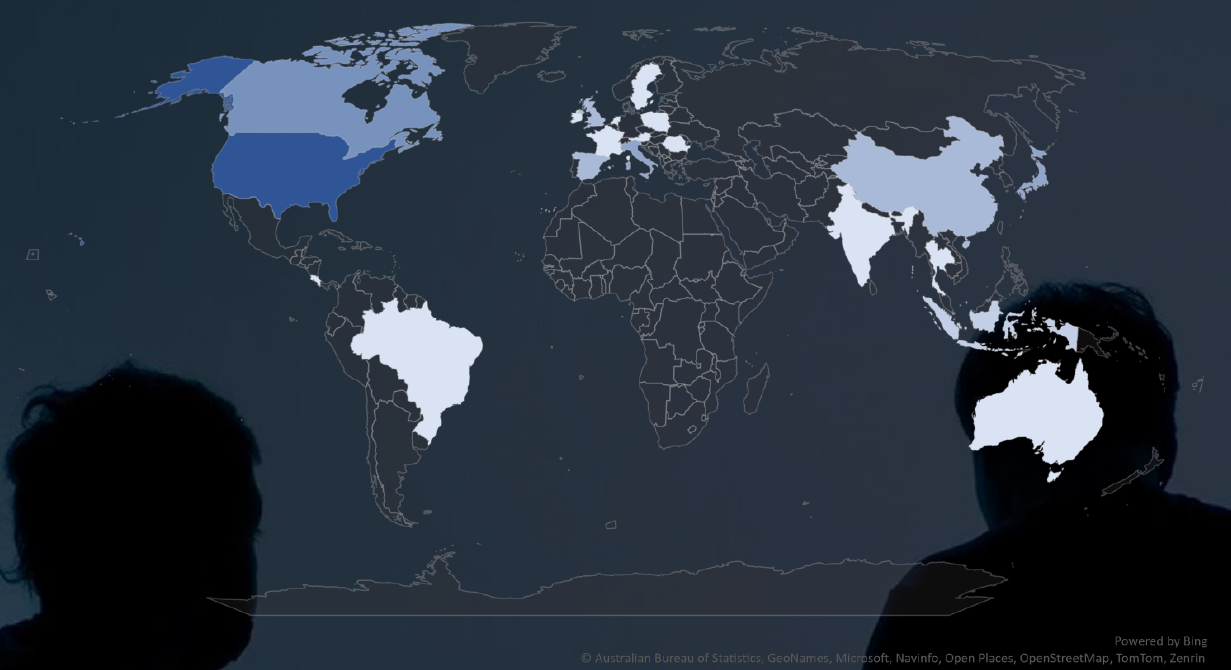
The heatmap of geographic distribution illustrates the global reach of ransomware across continents.
Total Victims per Country
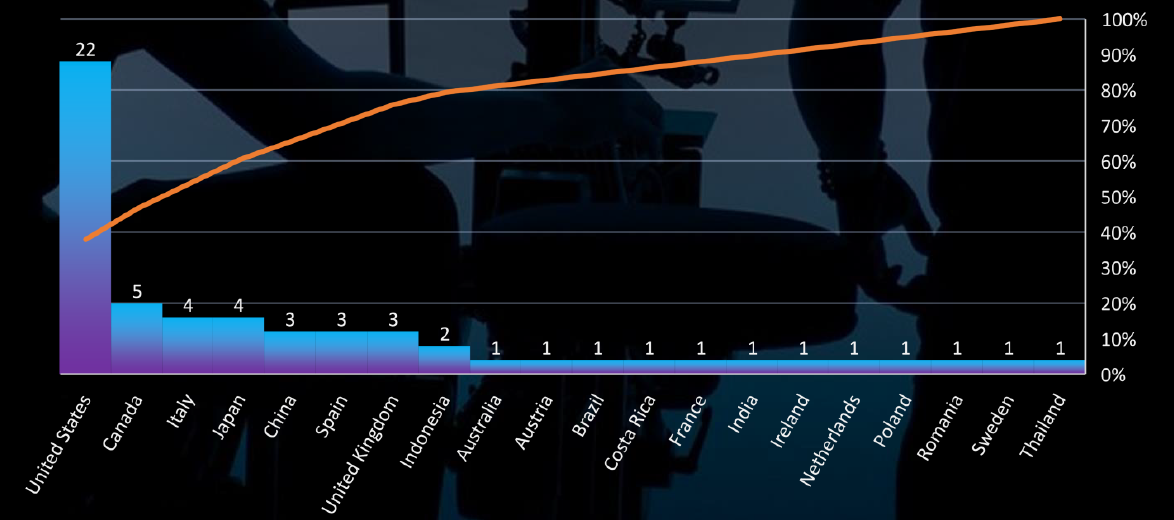
In total 20 countries recorded telecommunications & media industry ransomware victims with the US alone accounting for ~38% of all.
Sectors Distribution
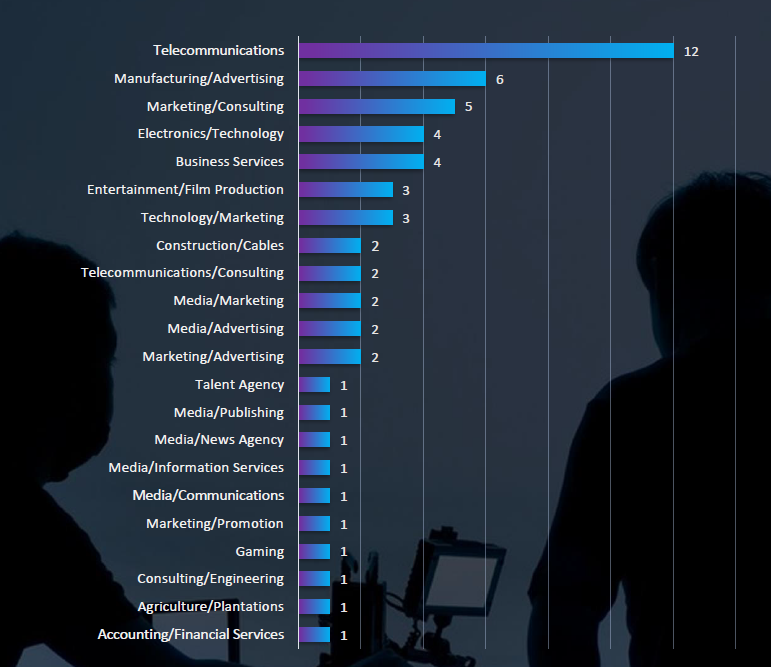
Listing consolidated sectors matched under the telecommunications & media industry umbrella shows victims across sectors, including some niches.
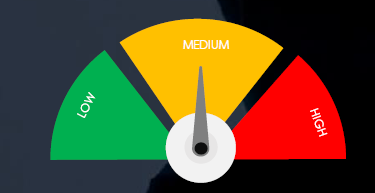
Risk Level Indicator : Medium

The Telecommunications & Media industry experiences a moderate level of victimization from ransomware attacks, accounting for 4.5% of all recorded victims across industries. Monthly activity indicates a slight decline since the peak in September, although the overall activity remains consistently high. Analysis of responsible groups identifies LockBit3 as the gang with the highest number of victims. However, unlike in other industries, LockBit3 doesn’t maintain a significant margin over Noescape, Blackbasta, or ALPHV, with only one or two fewer victims respectively. Suggesting low interest from LockBit3 and their affiliates.
In September, an increased number of victims were attributed to ‘mid-size’ gangs such as Noescape, ALPHV, Cactus, or Losttrust. Conversely, LockBit3 contributed to the majority of victims in October and November, alongside Blackbasta.
Out of the 47 active gangs in the last 90 days, 20 recorded victims in the Telecommunications & Media sector, representing a relatively lower share compared to other industries. Moreover, no gangs stand out with a particularly high share of victims compared to their overall activity, suggesting that there are no gangs specifically targeting this industry.
Geographically, victims are dispersed globally, with the US accounting for 38% of all victims, followed by Canada, Italy, and Japan.
The hardest-hit sectors include Telecommunications, encompassing local service providers, followed by Advertising-related manufacturing and Marketing/Consulting.
For a comprehensive, up-to-date global ransomware tracking report on a monthly basis, please refer to our new monthly “Tracking Ransomware” series here.
The Telecommunications & Media industry ranks among the most targeted sectors by nation-state threat actors, owing to its strategic significance in cyberspace operations and its role in controlling and monitoring propaganda media. Particularly noteworthy is the activity of Chinese Advanced Persistent Threats (APTs) across the entire ASEAN region.
Local telecommunications service providers continue to be a popular phishing lure, increasingly followed by gaming, particularly in the Southeast Asia region where Vietnam seems to be emerging as a phishing cybercrime hub.
The threat from ransomware remains moderate, with no gangs displaying notably high interest. Conversely, the largest gangs record relatively low numbers of victims, while mid-sized gangs are responsible for the majority.