


The CYFIRMA Industry Report delivers original cybersecurity insights and telemetry-driven statistics of global industries, covering one sector each week for a quarter. This report focuses on the real estate & utilities industry, presenting key trends and statistics in an engaging infographic format.
Welcome to the CYFIRMA infographic industry report, where we delve into the external threat landscape of the real estate & utilities industry industry over the past three months. This report provides valuable insights and data-driven statistics, delivering a concise analysis of attack campaigns, phishing telemetry, and ransomware incidents targeting the real estate & utilities industry.
We aim to present an industry-specific overview in a convenient, engaging, and informative format. Leveraging our cutting-edge platform telemetry and the expertise of our analysts, we bring you actionable intelligence to stay ahead in the cybersecurity landscape.
CYFIRMA provides cyber threat intelligence and external threat landscape management platforms, DeCYFIR and DeTCT, which utilize artificial intelligence and machine learning to ingest and process relevant data, complemented by manual CTI research.
For the purpose of these reports, we leverage the following data from our platform. These are data processed by AI and ML automation based on both human research input and automated ingestions.
While this report contains statistics and graphs generated primarily by automation, it undergoes thorough review and enhancement for additional context by CYFIRMA CTI analysts to ensure the highest quality and provide valuable insights.
Advanced Persistent Threat Attack Campaigns
Real estate & utilities organizations featured in 2 out of the 9 observed campaigns, which is a presence in 22% of campaigns.
Observed Campaigns per Month
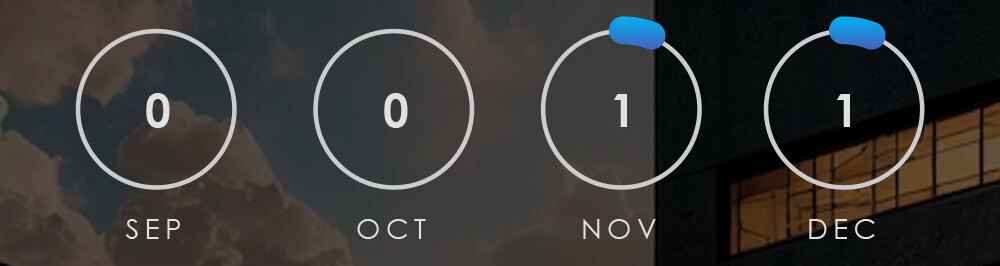
The monthly chart shows a resurgence in November and December after a period of generally low campaign detections in September and October.
Suspected Threat Actors
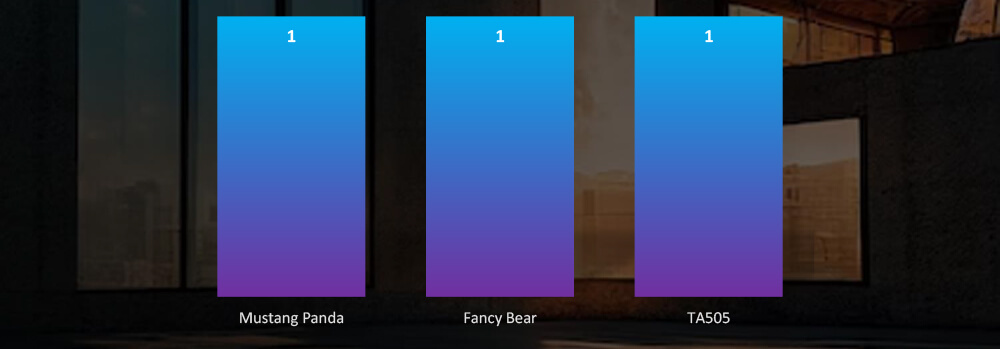
Suspected threat actors are split between Chinese Mustang Panda APT and Russian Fancy Bear/TA505 where campaign TTPs overlaps.
GEOGRAPHICAL DISTRIBUTION
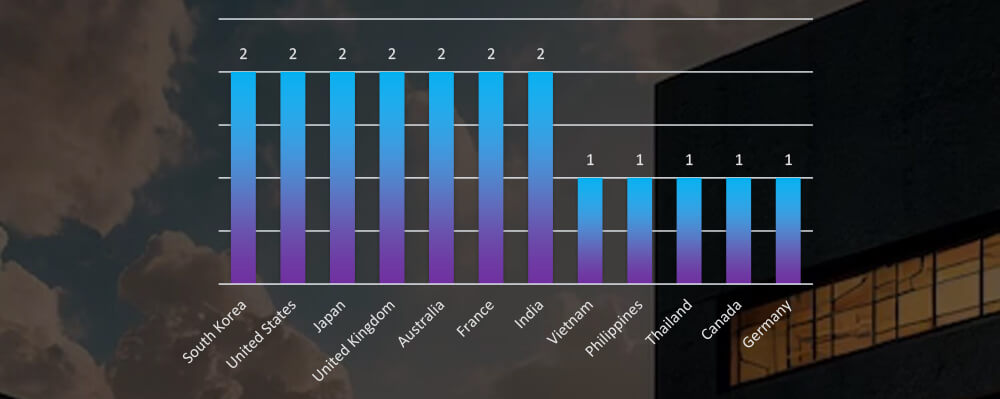
Victims of the observed attack campaigns were recorded in 12 different countries, split roughly evenly between Chinese and Russian national interests.
TOP ATTACKED TECHNOLOGY
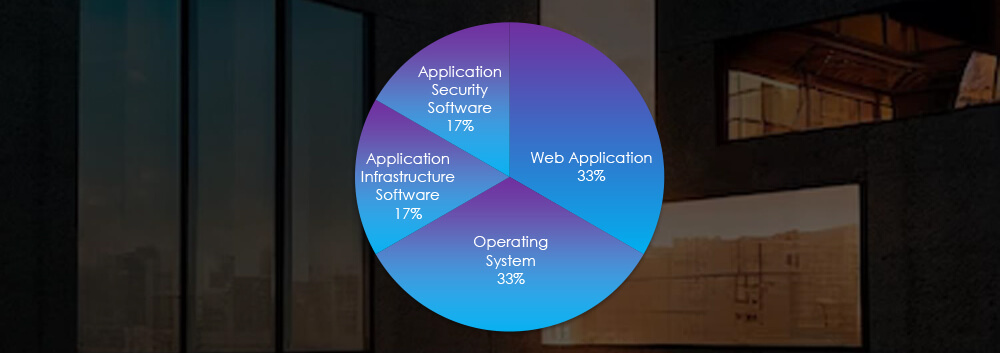
Attack campaigns focused on attacking web applications, operating systems and various applications.
APT CAMPAIGNS EXTERNAL THREAT LANDSCAPE MANAGEMENT (ETLM) OVERVIEW

Risk Level Indicator: Medium
After a period of low detections during the summer months, we have witnessed a resurgence in new detections in November and early December. Specifically, within the real estate & utilities industry, 2 out of the 9 observed campaigns have recorded victims. We consider this moderate level of interest, mainly in utilities, from sophisticated threat actors, compared to other industries.
Regarding suspected threat actors, the two observed campaigns are split between Chinese Mustang Panda and Russian Fancy Bear/TA505. In latter case TTPs do overlap between the two threat actors which are known to collaborate.
Geographically, there is also near equal split between Asian and European countries correlated with geopolitical interest of both China and Russia respectively.
The technologies targeted are mainly Web Application and Operating System.
Over the past 3 months, CYFIRMA’s telemetry recorded 948 phishing campaigns out of a total of 271,093 that impersonated the real estate & utilities industry brands which accounts for 0.3% of all campaigns.
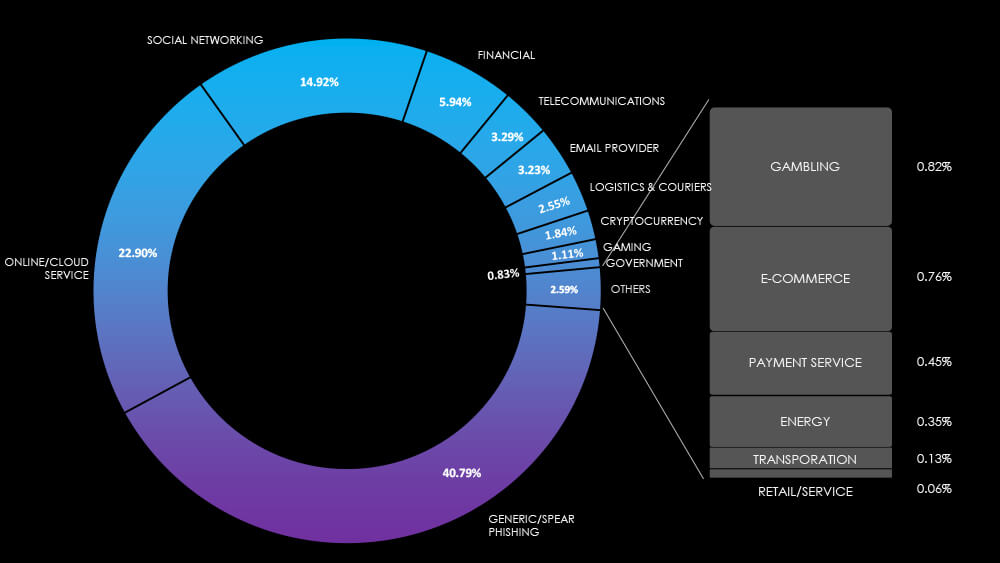
All relevant observed campaigns were energy utilities, which are tracked under the Energy sector. As per pie chart below, this amounts to a very small fraction of themes.
Global Distribution of Phishing Themes per Sector
Top Impersonated Brands
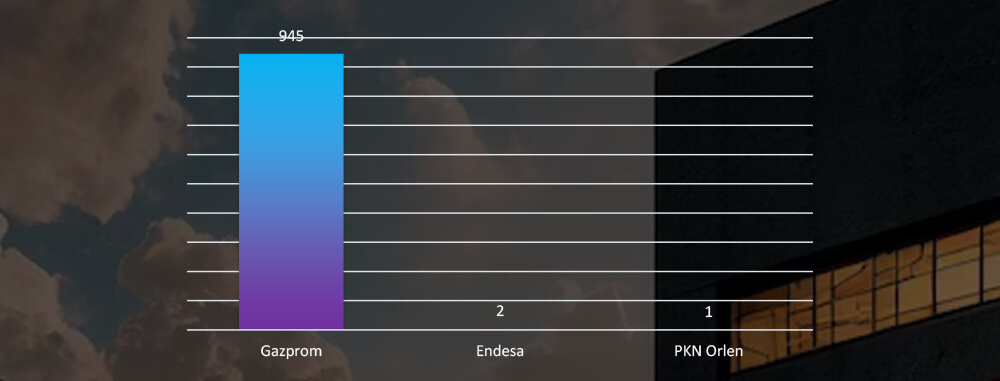
Most of the detected impersonations are from Russian giant Gazprom, with a few for Spanish and Polish energy utilities.
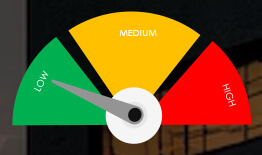
Risk Level Indicator : Low
The real estate industry doesn’t seem to be an interesting phishing lure or a lucrative target at all. For utilities sector its fragmented and heavily localized structure all the way up to county or town level, making it unsuitable for widespread internet or nationwide phishing campaigns. Despite holding substantial personal information that could interest cybercriminals, this data is scattered across various small regions and contains household details rather than more valuable personal information, unlike the financial industry.
As we saw in the data, the only significantly impersonated organization was Gazprom; the Russian natural gas giant present in many other European countries. Along with it were handful of Spanish and Polish national utility conglomerates.
In the past 90 days, CYFIRMA has identified 85 verified ransomware victims within the real estate & utilities sectors. This accounts for 5,8% of the overall total of 1495 ransomware incidents during the same period.
The Monthly Activity Chart
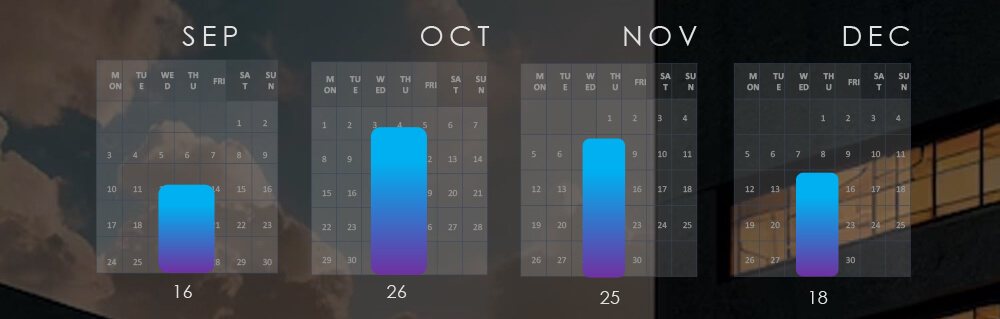
Monthly trends show consistent numbers without a clear trend, when adjusted for partial months.
Breakdown of Monthly Activity by Gangs
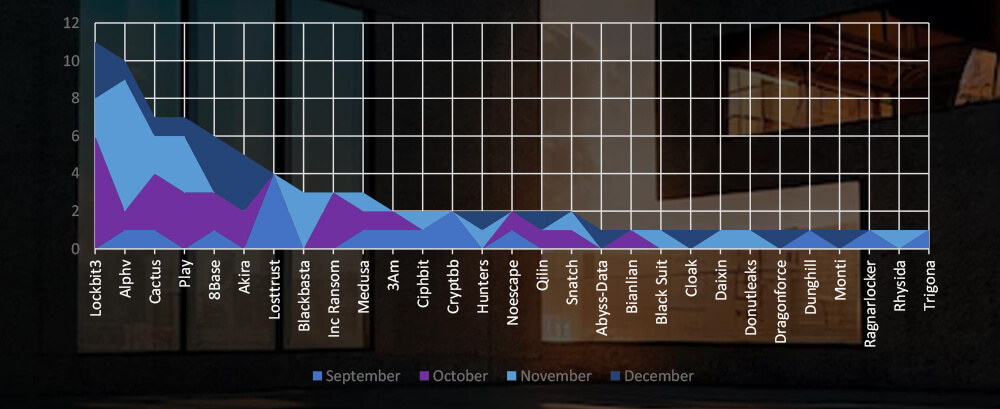
A breakdown of the monthly activity provides insights per group activity. For example, ALPHV has been highly active in November, whereas, Losttrust recorded victims only in September.
Ransomware Victims in Real Estate & Utilities Industry per Group
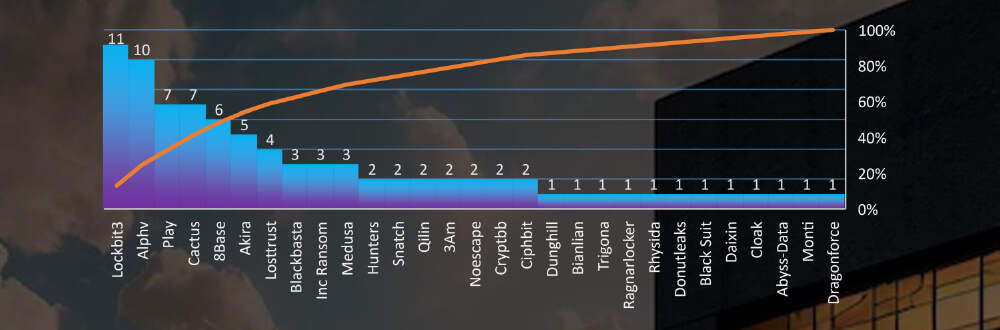
In total 29 out of 50 groups recorded real estate or utilities organization victims in the past 90 days. The top 6 are responsible for half of them.
Comparison to All Ransomware Victims by Group (Top 25)
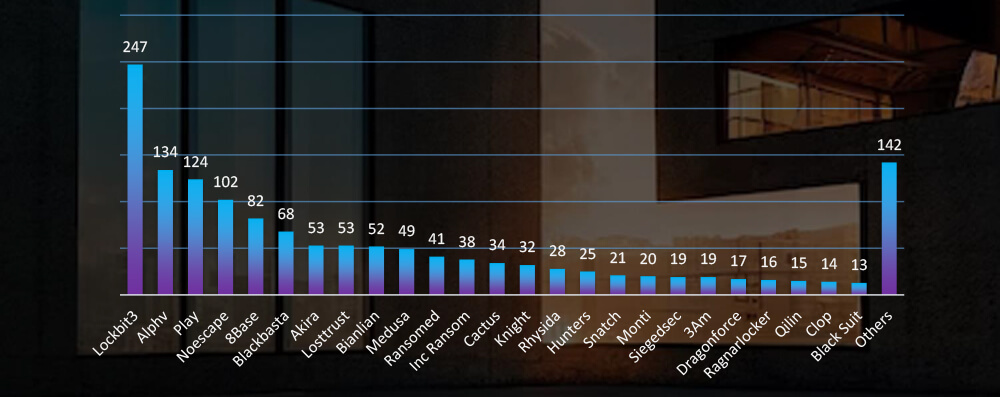
Compared to all recorded victims in the same time period, Cactus gang has a comparatively higher number of victims in this industry, suggesting higher interest. On the other hand, Noescape seems to show little interest.
Geographic Distribution Of Victims
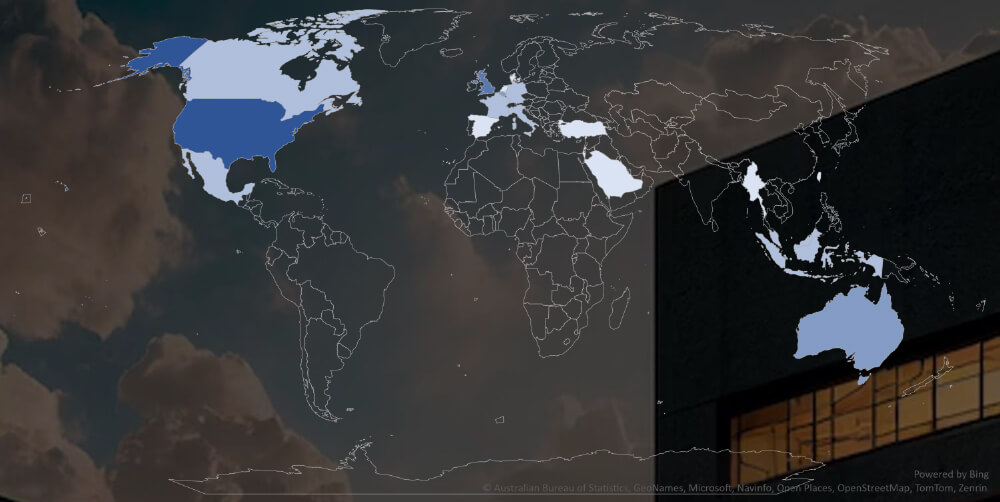
The heatmap of geographic distribution shows concentration in North America, Western Europe and Southeast Asia.
Total Victims per Country
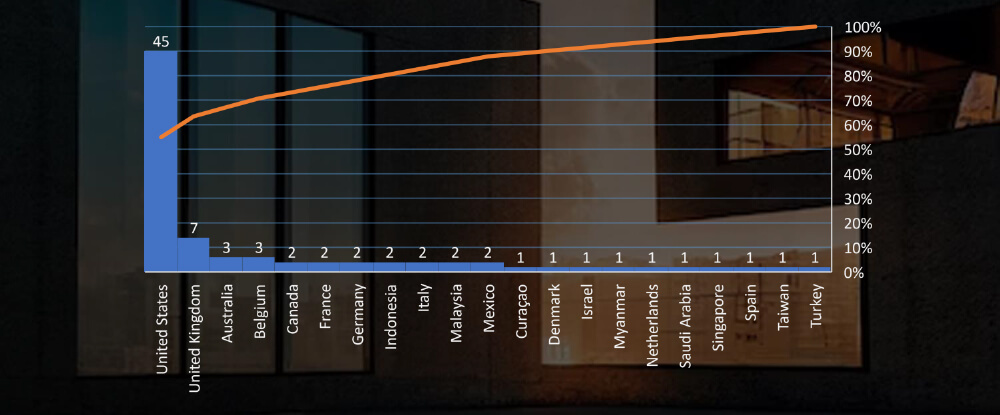
In total 21 countries recorded real estate or utility industry ransomware victims with the US alone accounting for ~52% of all.
Sectors Distribution
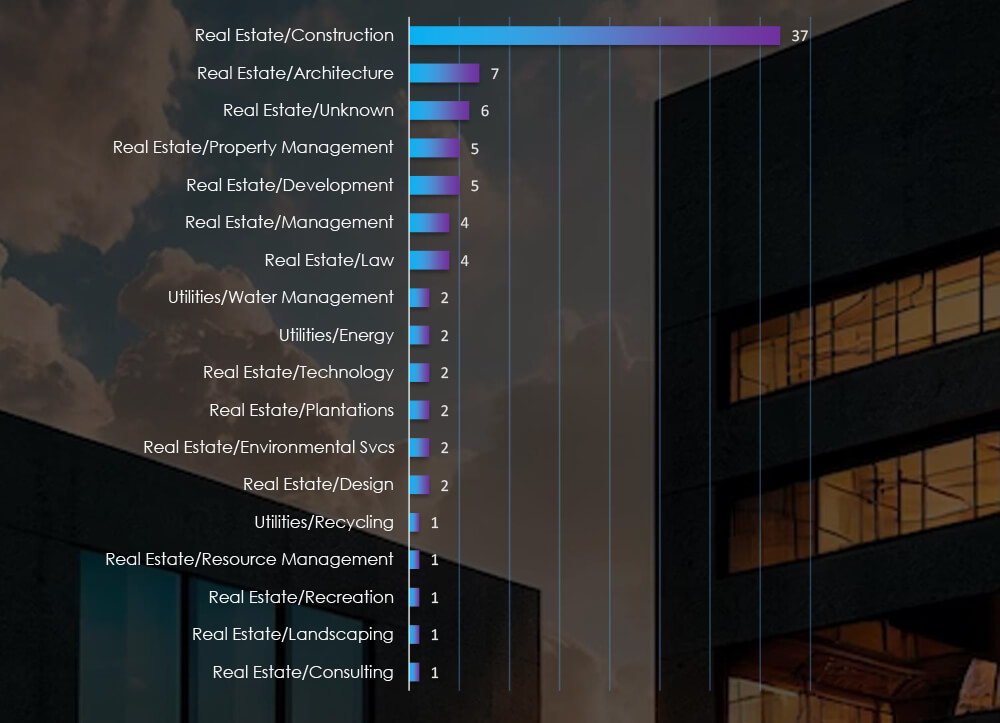
Listing consolidated sectors matched under the real estate and utilities umbrella shows construction as the most attacked sector.
Risk Level Indicator: Moderate

Monthly activity consistently shows a substantial volume of attacks, without a clear trend. A closer look at the groups behind these attacks highlights Lockbit3, ALPHV and Cactus gangs as most prominent. Specifically, ALPHV has been highly active during November, whereas Lockbit3 ramped up in October.
Unlike in other sectors, there isn’t a clear dominance by the largest gangs in this industry. Although Lockbit3 and ALPHV hold a marginal lead, the rest of the field also reports significant numbers of victims.
Of the 50 active gangs in the past 90 days, 29 have targeted the real estate & utilities industry. Particularly, the Cactus gang has recorded a higher number of victims in this sector compared to its overall activity in the same time frame, suggesting a heightened interest. Conversely, the Noescape gangs show relatively low interest.
Among the victims with identified locations in 21 different countries, the United States ranks as the most affected, with 45 victims, followed by the UK and Australia. This is even higher prevalence of US-based victims than we see in other industries. Our hypothesis is that US is by far the biggest real estate market in the world, where relevant organizations and business are abundant and large enough to attract ransomware activity.
Finally, the most vulnerable sector appears to be Construction, including real estate developers, which correlates with our hypothesis of US being the largest real-estate market.
For a comprehensive, up-to-date global ransomware tracking report on a monthly basis, please refer to our new monthly “Tracking Ransomware” series here.
In the cybersecurity landscape of the real estate and utilities industry, ransomware stands as a moderate threat, yet with a notable concentration of victims primarily within the USA, specifically in the construction and development sectors.
Conversely, phishing campaigns pose a low risk in this sector. The industry’s highly localized nature doesn’t provide substantial bait for phishing attempts, with the observed exception being the Russian natural gas giant; Gazprom.
Following a period of relative calm, we have noted two APT campaigns. Mustang Panda and FancyBear/TA505 orchestrated these campaigns, focusing on utility sectors in Asian and European countries, respectively.