



The CYFIRMA Industry Report delivers original cybersecurity insights and telemetry-driven statistics of global industries, covering one sector each week for a quarter. This report focuses on the real estate & construction industry, presenting key trends and statistics in an engaging infographic format.
Welcome to the CYFIRMA infographic industry report, where we delve into the external threat landscape of the real estate & construction industry over the past three months. This report provides valuable insights and data-driven statistics, delivering a concise analysis of attack campaigns, phishing telemetry, and ransomware incidents targeting the real estate & construction industry.
We aim to present an industry-specific overview in a convenient, engaging, and informative format. Leveraging our cutting-edge platform telemetry and the expertise of our analysts, we bring you actionable intelligence to stay ahead in the cybersecurity landscape.
CYFIRMA provides cyber threat intelligence and external threat landscape management platforms, DeCYFIR and DeTCT, which utilize artificial intelligence and machine learning to ingest and process relevant data, complemented by manual CTI research.
For the purpose of these reports, we leverage the following data from our platform. These are data processed by AI and ML automation based on both human research input and automated ingestions.
While this report contains statistics and graphs generated primarily by automation, it undergoes thorough review and enhancement for additional context by the CYFIRMA CTI analysts to ensure the highest quality and provide valuable insights.
Real estate & construction organizations featured in 1 out of the 7 observed campaigns, which is a presence in 14.3% of all campaigns.
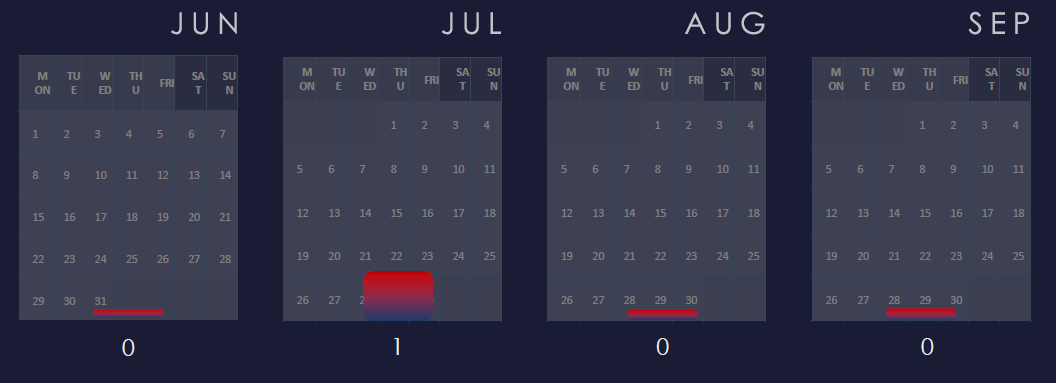
A single observed campaign occurred during July.

Unknown English-speaking threat actors
The observed campaign was carried out by unknown English-speaking threat actors and TTPs are a little murky. However, one pointer is the use of Emotet derivate malware, suggesting, with low confidence that this is Russian-linked cybercrime activity.
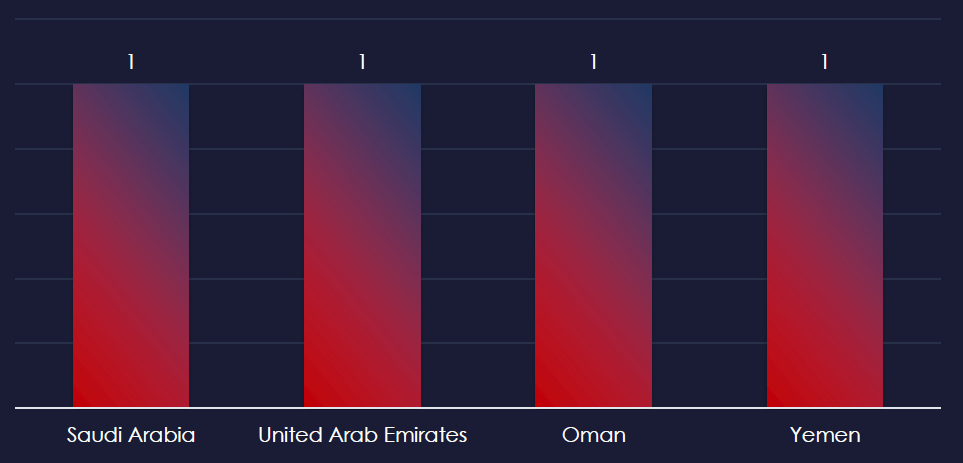
Recorded victims of observed attack campaigns span 4 different countries. All countries are on the Arabian peninsula, suggesting a targeted campaign in the region.
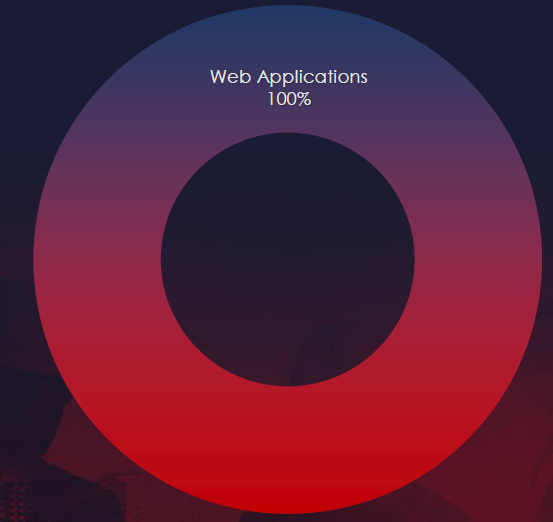
Web applications have been targeted during this campaign.
EXTERNAL THREAT LANDSCAPE MANAGEMENT (ETLM) OVERVIEW
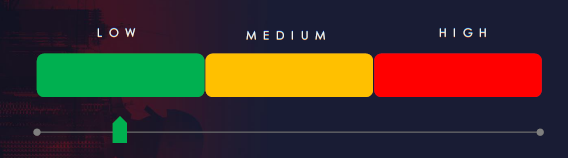
Risk Level Indicator: Low
In the past 90 days, real estate & construction organizations have not been significantly impacted by advanced persistent threat (APT) campaigns. Just 1 out of the 7 observed APT campaigns targeted this industry.
A single campaign was observed in mid-July with real estate developer victims, apart from that we did not observe other campaigns targeting this industry.
Key Threat Actors
At the time of writing this report, we could not attribute the threat actor. We know they are an English-speaking group, but using Emotet-derived malware, which makes a low-confidence link to Russian cybercrime.
Geographical Impact
The campaign impacted a total of 4 countries, all from the Arabian peninsula, making it a geographically targeted campaign.
Targeted Technologies
Web applications emerged as the only apparent targeted technology within this campaign.
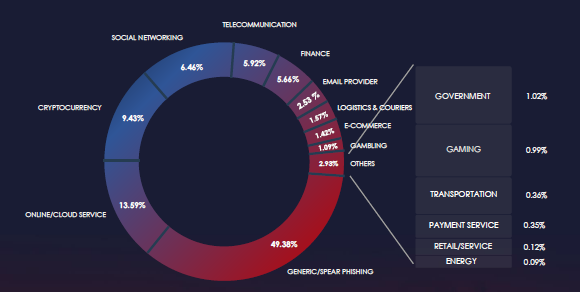
Over the past 3 months, CYFIRMA’s telemetry did not detect any phishing campaigns themed around the real estate & construction sector out of a total of 213,121.
The chart below illustrates the global distribution of observed themes. Real estate & construction is not tracked.
EXTERNAL THREAT LANDSCAPE MANAGEMENT (ETLM) OVERVIEW
Risk Level Indicator: Low

CYFIRMA telemetry did not find any real estate & construction impersonations. However, that does not mean they do not exist. They are certainly used in some areas and as spear-phishing where suitable.
The highly localized and fragmented nature of the real estate & construction industry simply does not present a good lure for widespread “spray and pray” types of campaigns. Furthermore, monetization for local cybercrime is more complex than more popular scams, such as usual banking or courier & delivery themes.
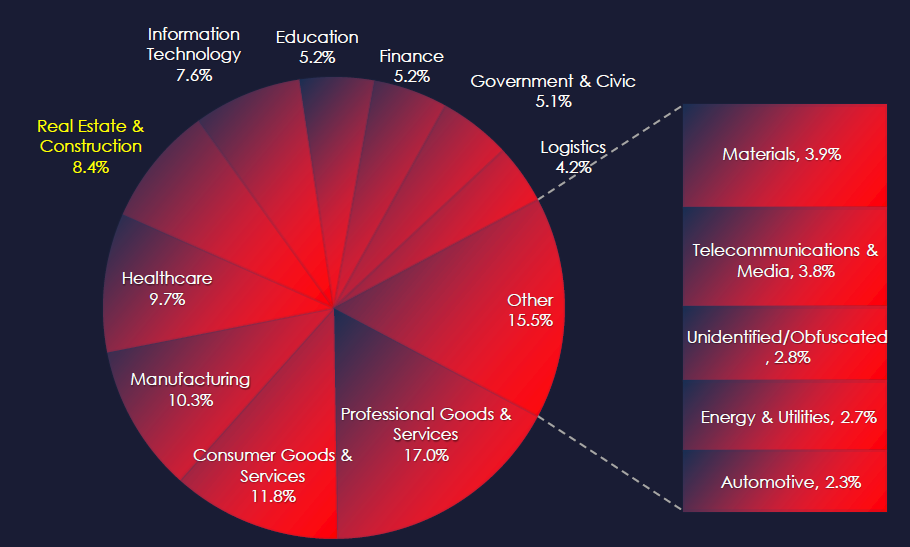
In the past 90 days, CYFIRMA has identified 113 verified ransomware victims in the real estate & construction industry. This accounts for 8.4% of the overall total of 1,346 ransomware victims during the same period.
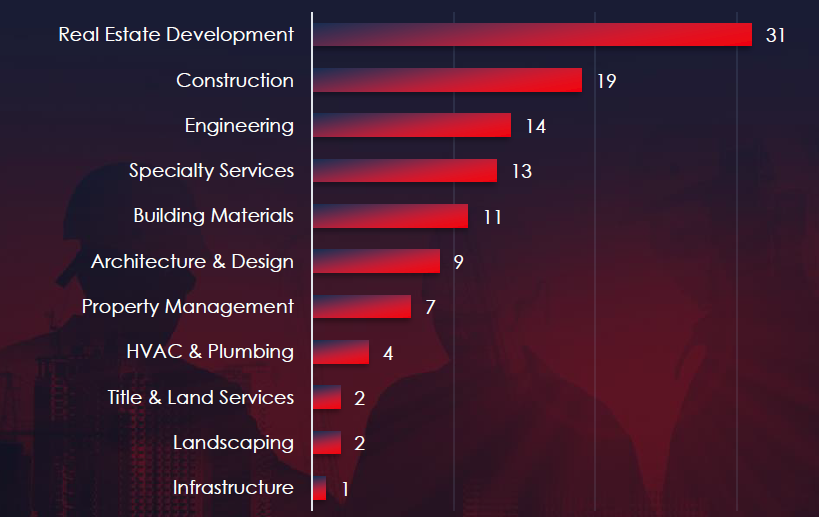
Real Estate Developers and Construction companies are the most frequent victims of ransomware in real estate & construction industry.
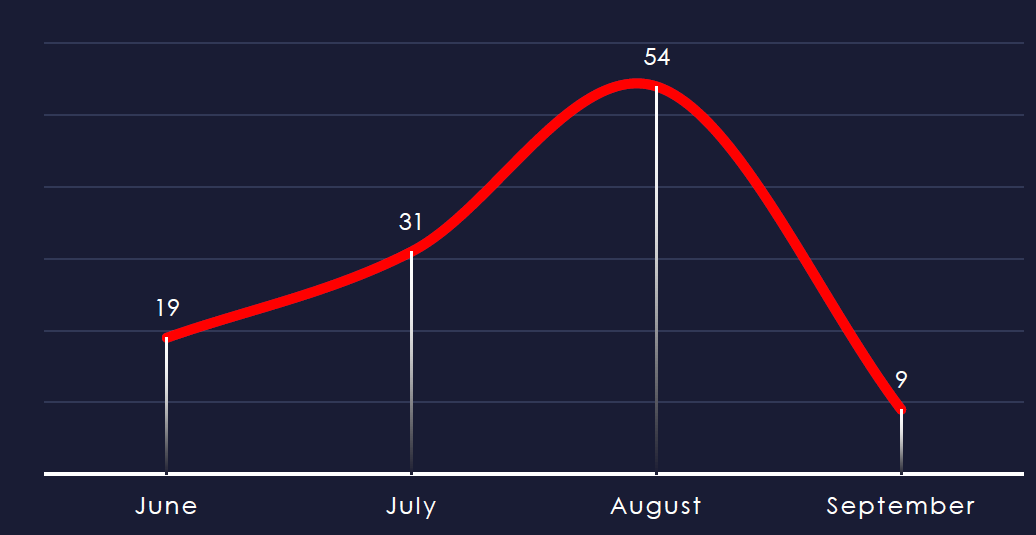
Adjusting for June and September split, we can observe a significant spike of real estate & construction victims during August.
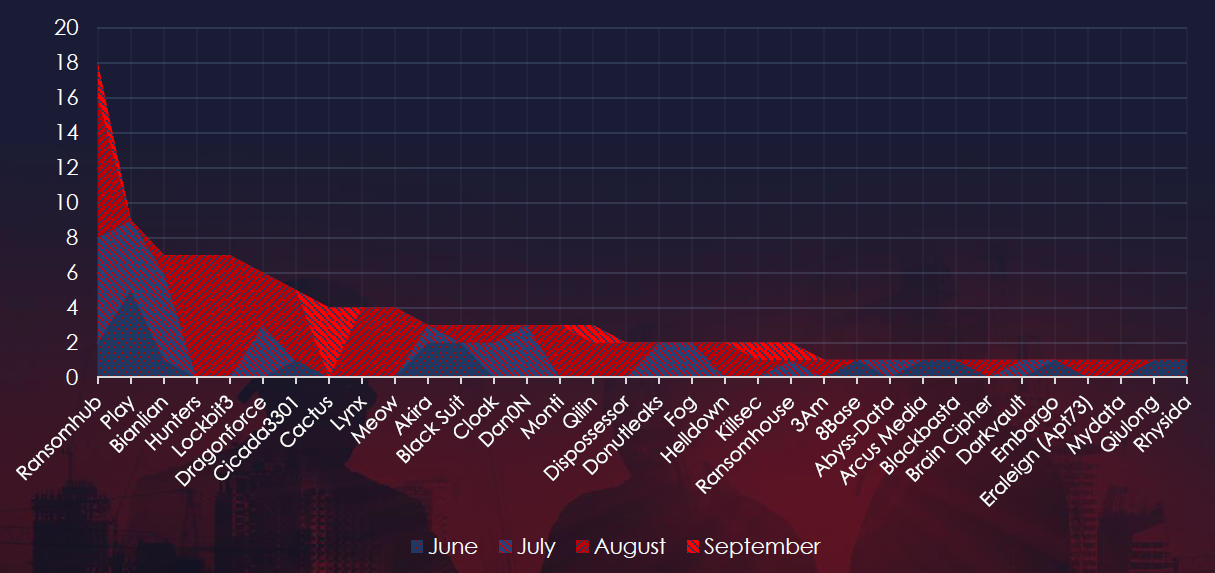
A breakdown of the monthly activity provides insights into which gangs were active each month. For example, Hunters, LockBit3, Lynx, and Meow are responsible for the August spike, reporting all their victims in the same month.
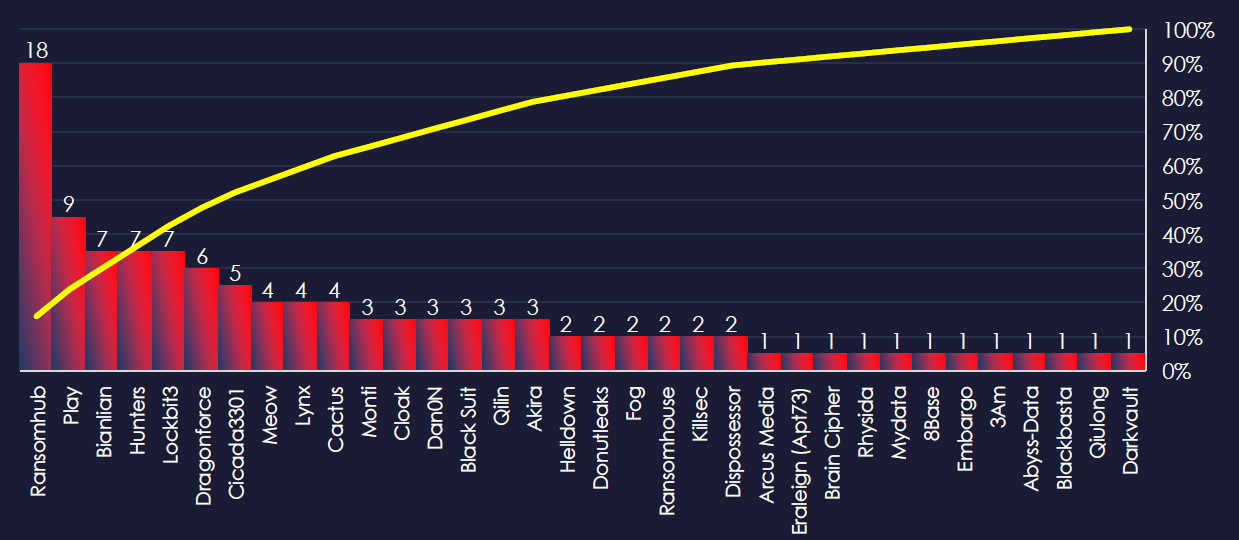
In total 34 out of 60 active groups recorded real estate & construction organization victims in the past 90 days. Notable is the high distribution among a large number of groups in this period.
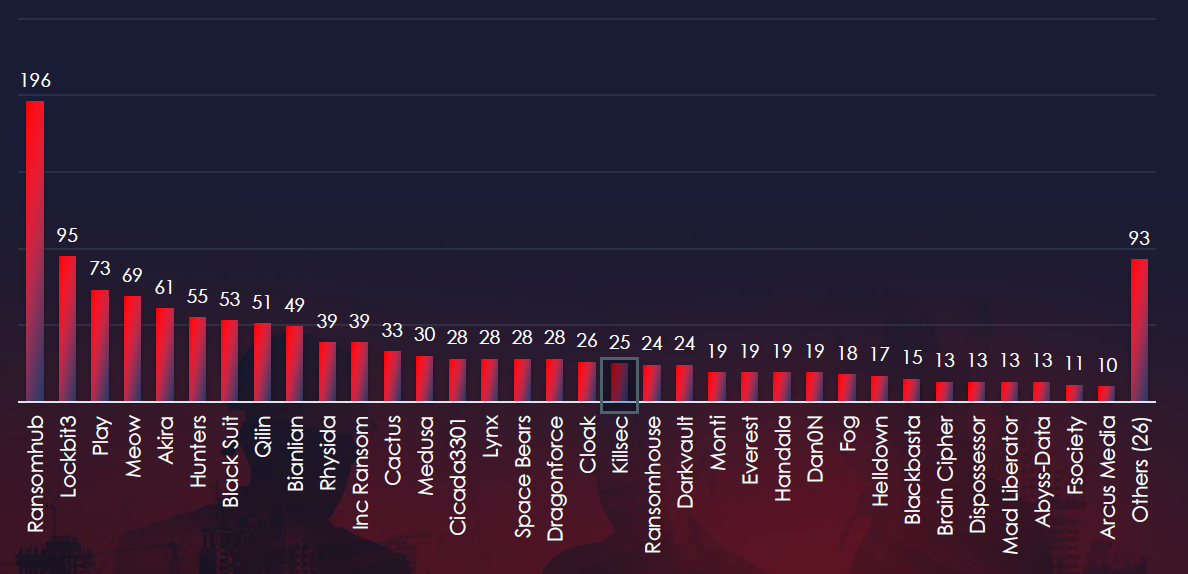
Comparing the real estate & construction industry to all recorded victims, only one of the gangs particularly stands out with a high percentage of victims in this industry. The highest is Dragonforce with 6 out of 28 (21.4%) victims and Cicada3301 with 5 out of 28 (17.8%).
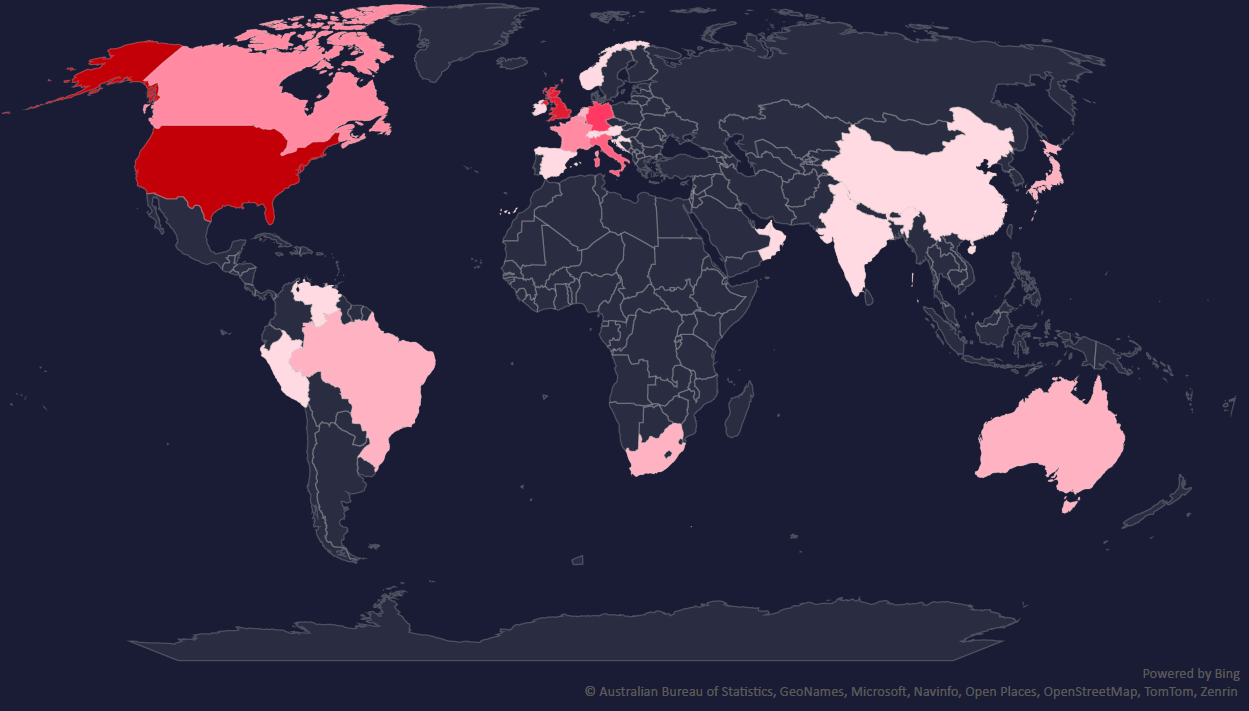
The geographic distribution heatmap underscores the widespread impact of ransomware, highlighting the countries where victims in this industry have been recorded.
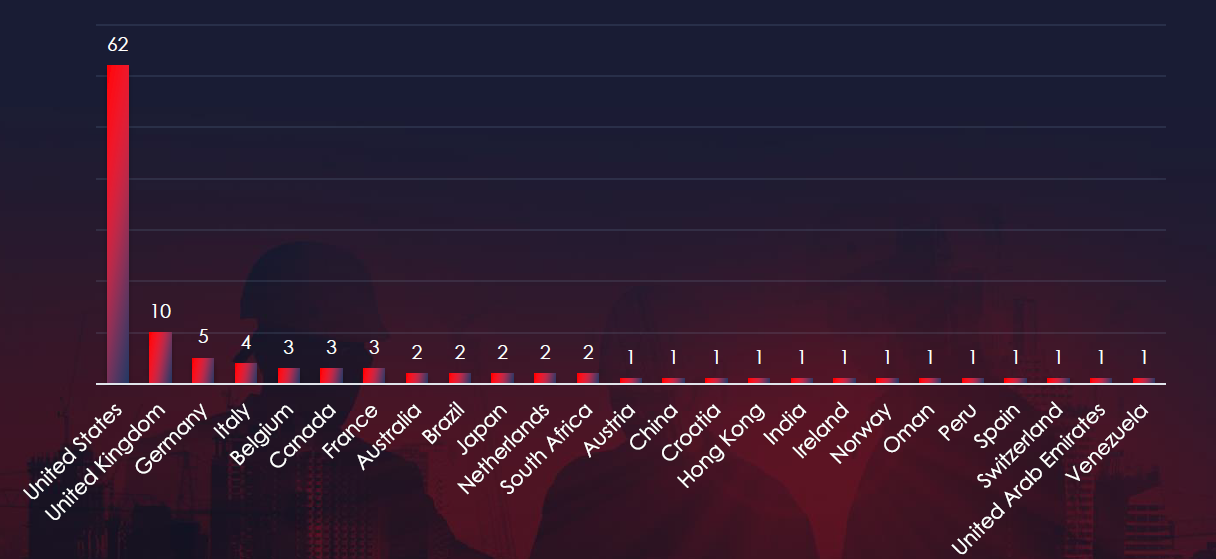
In total 25 countries recorded ransomware victims with the US alone accounting for 54% of all victims with identified geography.
Risk Level Indicator: High
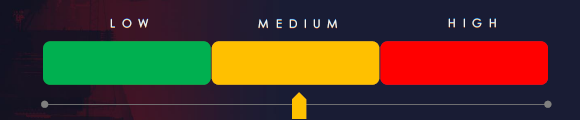
The real estate & construction industry is placed with 5th most victims. It faces a significant ransomware threat. We maintain high-risk factors for the U.S. where 54% of all victims come from, otherwise, the risk is moderate.
Monthly Activity Trends
Ransomware activity in the real estate & construction industry has shown a high surge during September with multiple groups reporting victims during August.
Hunters, Lockbit3, Lynx, and Meow reported victims only in August, but also the most active group – RansomHub reported a significant number.
Ransomware Gangs
A total of 34 out of 60 active ransomware groups targeted this industry in the past 90 days:
Dragonhouse: 21.4% of their victims were from the real estate & construction industry (6 out of 28 victims).
Cicada3301: 17.8% of their victims were from the same industry (5 out of 28 victims).
The distribution of attacks among many groups indicates no single gang dominated the ransomware landscape in the real estate & construction sector.
Geographic Distribution
The geographic distribution of ransomware victims in the real estate & construction industry highlights the widespread nature of these attacks:
54% of all victims with identified geography are located in the US. In total, 25 countries reported ransomware victims in this industry.
For a comprehensive, up-to-date global ransomware tracking report, please refer to our new monthly “Tracking Ransomware” series here.
Over the past 90 days, the real estate & construction industry has faced varying levels of cyber threats across APT campaigns, phishing, and ransomware.
APT Campaigns: The industry faces a low risk, with only 1 out of 7 observed APT campaigns targeting real estate developers in the Arabian Peninsula. The attack involved web applications, with no clear attribution of the threat actor, although Emotet-derived malware suggests a potential link to Russian cybercrime.
Phishing: Phishing risk remains low for this sector, as the fragmented nature of the industry makes it an unattractive target for widespread campaigns. There were no observed impersonations, though spear-phishing remains a possibility in localized contexts.
Ransomware: The industry faces a high risk, ranking 5th in terms of victims. 54% of all identified ransomware victims are located in the US, with significant activity seen in September. Multiple ransomware groups, including RansomHub, Dragonhouse, and Cicada3301, have targeted this sector, though no single gang dominated. In total, 25 countries reported ransomware victims in this industry.