



The CYFIRMA Industries Report delivers original cybersecurity insights and telemetry-driven statistics of global industries, covering one sector each week for a quarter. This report focuses on the materials industry, presenting key trends and statistics in an engaging infographic format.
Welcome to the CYFIRMA infographic industry report, where we delve into the external threat landscape of the materials industry over the past three months. This report provides valuable insights and data-driven statistics, delivering a concise analysis of attack campaigns, phishing telemetry, and ransomware incidents targeting the materials industry.
We aim to present an industry-specific overview in a convenient, engaging, and informative format. Leveraging our cutting-edge platform telemetry and the expertise of our analysts, we bring you actionable intelligence to stay ahead in the cybersecurity landscape.
CYFIRMA provides cyber threat intelligence and external threat landscape management platforms, DeCYFIR and DeTCT, which utilize artificial intelligence and machine learning to ingest and process relevant data, complemented by manual CTI research.
For the purpose of these reports, we leverage the following data from our platform. These are data processed by AI and ML automation, based on both human research input and automated ingestions.
While this report contains statistics and graphs generated primarily by automation, it undergoes thorough review and enhancement for additional context by CYFIRMA CTI analysts to ensure the highest quality and provide valuable insights.
Materials industry organizations featured in 3 out of the 15 observed campaigns, which is a presence in 20% of all campaigns.
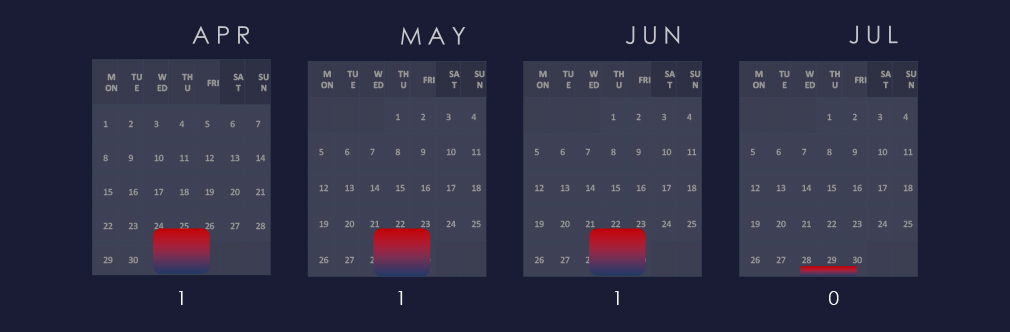
We have observed a resurgence of an observed campaign during June. However, materials industry does not appear to be a target. All 3 victims were from the petrochemical sector.

In two campaigns, we observed overlapping TTPs, splitting the suspected threat actors. In one case we observed MISSION2025 (Apt41 nexus) mixed with Korean language and other Lazarus Group’s malware with Mustang Panda’s TTPs. 3rd campaign was attributed to Sandworm.
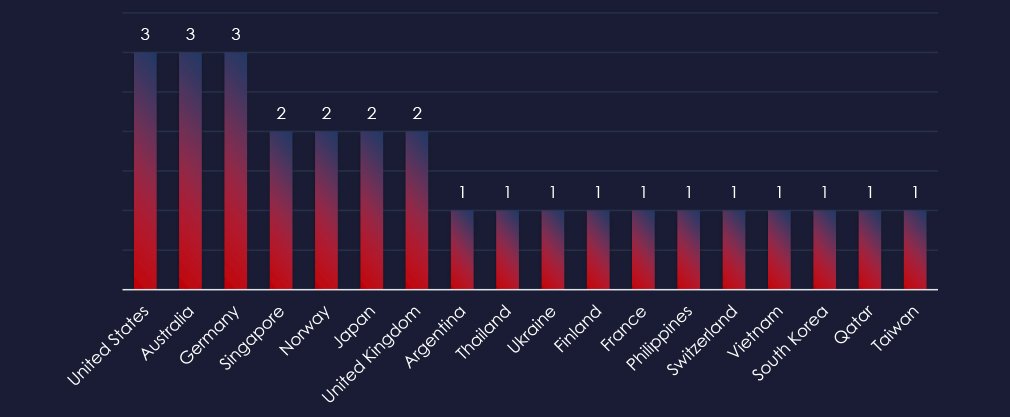
Recorded victims of observed attack campaigns span 18 different countries. Considering suspected TAs, it is suggesting opportunistic targeting for financial gains (Lazarus Group) as well as geopolitically motivated (Sandworm – Russian military intelligence).
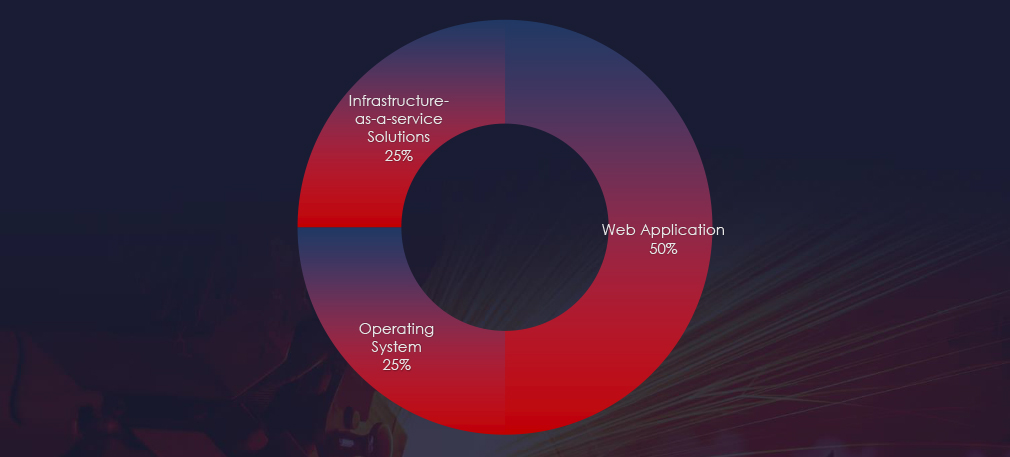
Web applications continues to be as the most targeted technology across industries, followed by operating systems and IaaS solutions.
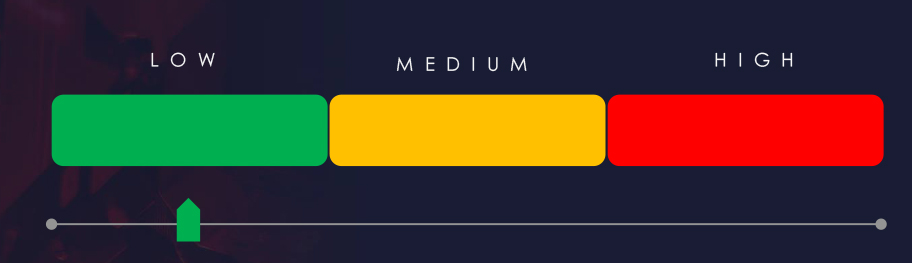
Risk Level Indicator: Low – *Moderate
In the past 90 days, the materials industry has not been significantly impacted by advanced persistent threat (APT) campaigns. 20% of observed APT campaigns recorded victims from the Petrochemical sector, with 3 out of 15 total campaigns affecting this industry.
*The Petrochemical sector warrants moderate risk factors.
Monthly Trends
Despite a general surge in June where we observed most of the campaigns in the last 90 days, the 3 with relevant victims were observed, one for each month from April to June.
Key Threat Actors
In two campaigns, we observed overlapping TTPs splitting the suspected threat actors. In one case we observed MISSION2025 (Apt41 nexus) mixed with Korean language and other Lazarus Group’s malware with Mustang Panda’s TTPs. The 3rd campaign was attributed to the Russian military Intelligence linked group – Sandworm.
Geographical Impact
Observed geographies align with countries known for robust petrochemical industries, most likely targeted for financial gains by Lazarus Group, as well as countries of interest to Russian military intelligence.
Targeted Technologies
Web applications, operating systems, and Infrastructure-as-a-Service emerged as top targeted technologies within the observed campaigns.
Over the past 3 months, CYFIRMA’s telemetry detected no phishing campaigns themed around the materials industry out of a total of 253,086.
The chart below illustrates the global distribution of observed themes. The only materials industry-related phishing observed were Gazprom and Agriaffaires, which are both too big of a stretch to actually count. One is a natural gas giant and the other a farming gear and materials marketplace.
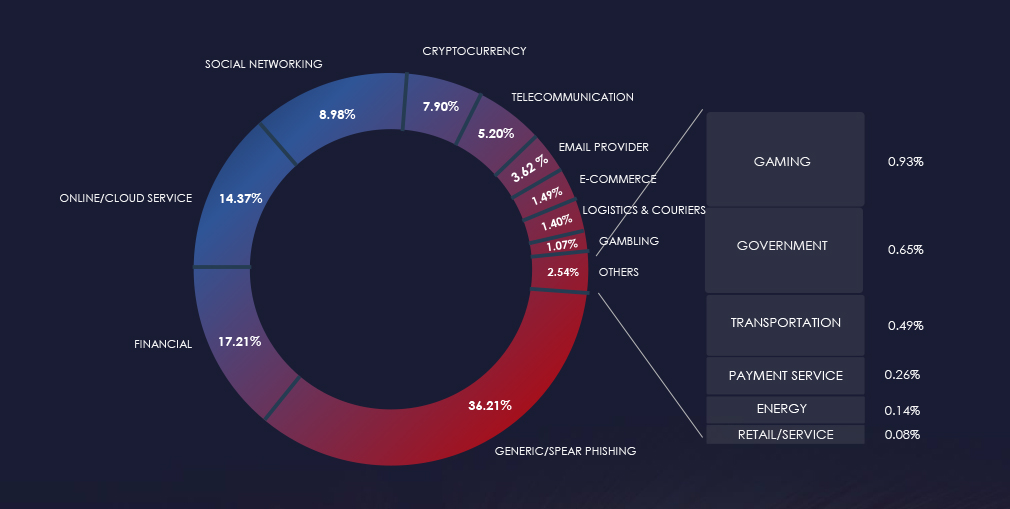

Risk Level Indicator: Low
The materials industry warrants a low risk factor.
Excluding spear-phishing attacks conducted by geopolitically motivated APTs and ransomware affiliates, the materials industry is generally not a focus for phishing campaigns due to a few reasons.
Firstly, the industry’s operations involve specialized machinery, intricate production processes, and proprietary technologies. These aspects make it challenging for cybercriminals to comprehend and potentially less lucrative compared to sectors like finance or healthcare.
Moreover, companies in the materials industry typically have limited access to high-value personal or financial information that cybercriminals often seek, such as credit card data or social security numbers. Consequently, the potential gains from phishing attacks on these organizations are relatively lower.
Furthermore, the materials industry often lacks extensive customer databases. In summary, there is nothing to gain for lower-level cybercriminals behind large phishing campaigns. They tend to prioritize sectors with direct ways to monetize or with larger repositories of personal information that can be exploited for illicit purposes.
In the past 90 days, CYFIRMA has identified 60 verified ransomware victims in materials industry. This accounts for 5.0% of the overall total of 1,190 ransomware victims during the same time period.
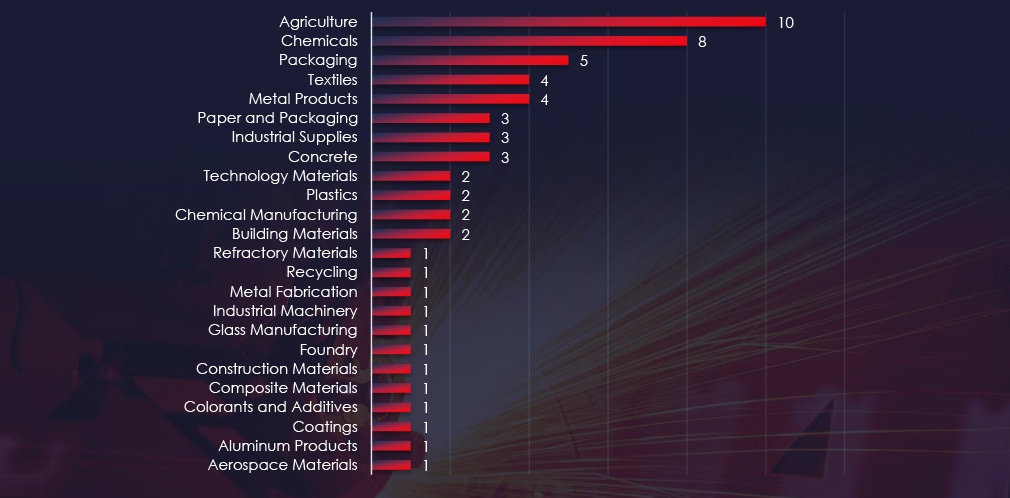
Agriculture and chemical production are the most frequent victims of ransomware in the materials industry.
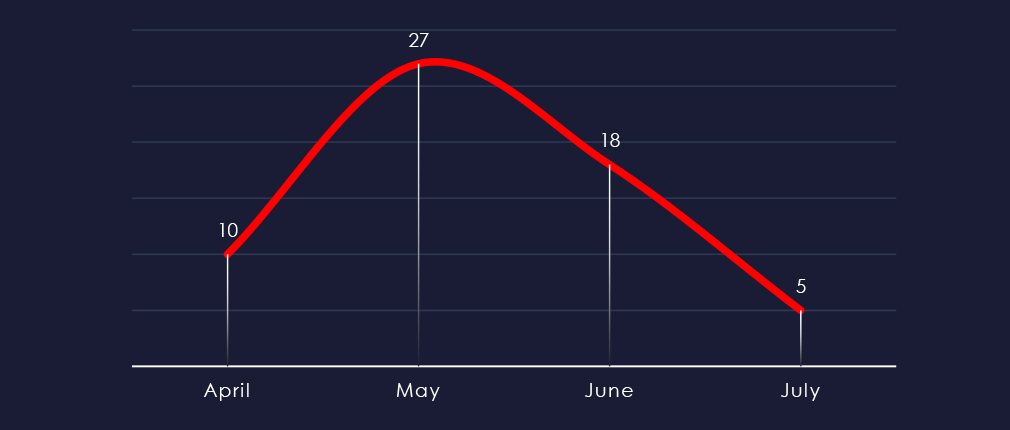
Considering nearly equal split of April and July, we can see sustained numbers of victims with a notable uptick during May.
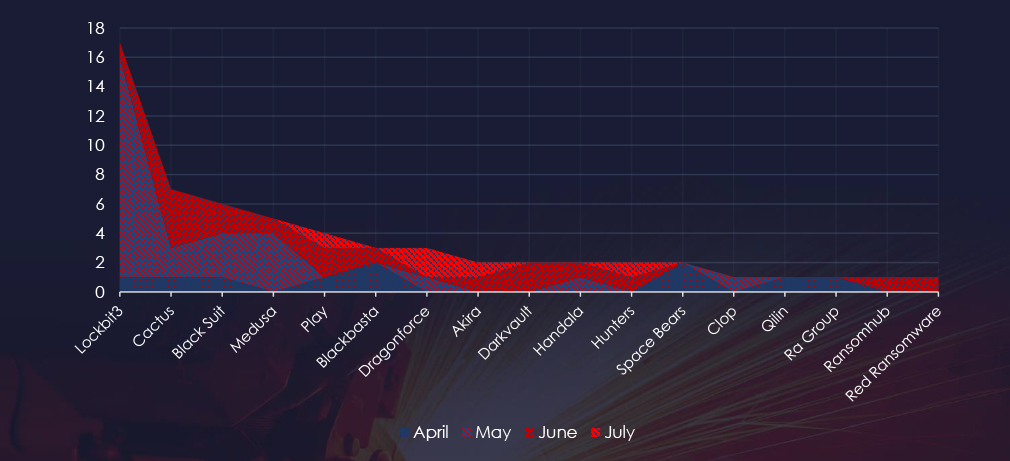
A breakdown of the monthly activity provides insights into which gangs were active each month. LockBit3 came back in May with a vengeance and is behind the uptick in the monthly activity. Cactus gang largely contributed to the May victim count.
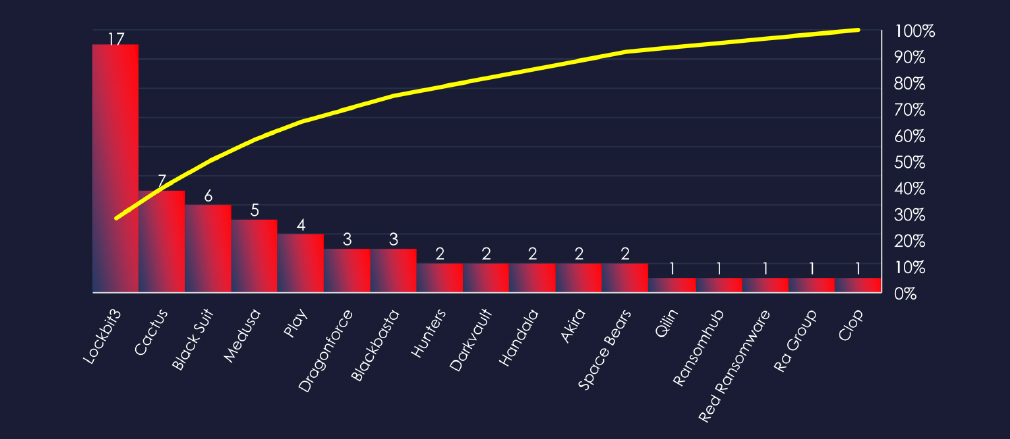
In total 17 out of 58 active groups recorded materials industry victims in the past 90 days. This is a relatively low participation rate compared to other industries.
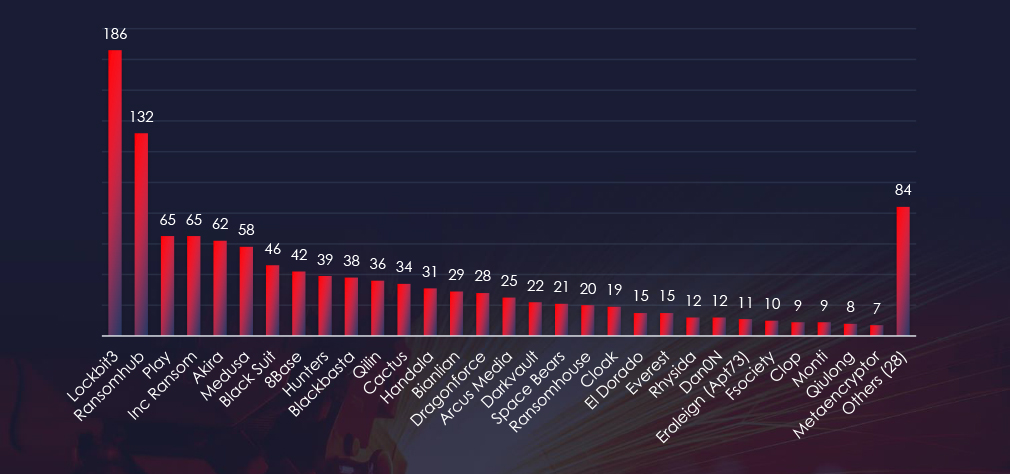
Comparing the materials industry to all recorded victims, only one gang – Cactus stands out with 7 out of 34 (20.6%) victims in this industry, suggesting a focus on this industry.
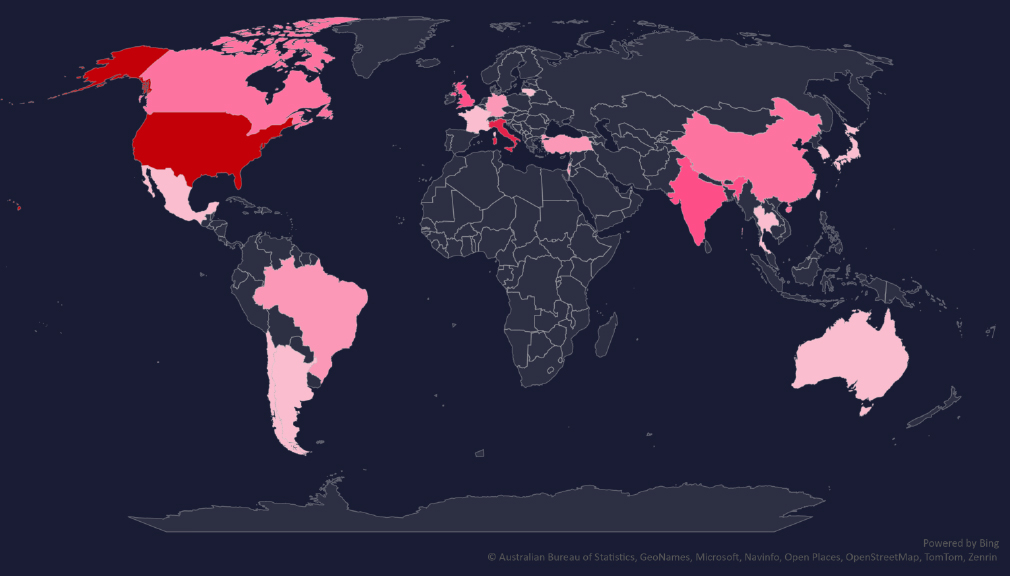
The geographic distribution heatmap underscores the widespread impact of ransomware, highlighting the countries where victims in this industry have been recorded.
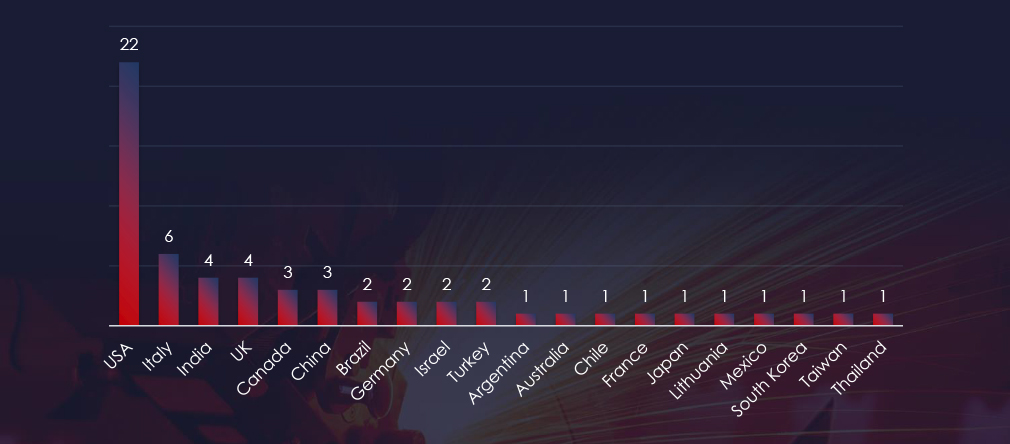
In total 20 countries recorded ransomware victims with the US alone accounting for ~37% of all victims with identified geography.

Risk Level Indicator: Moderate
The materials industry ranked 8th out of 14 industry categories. Encompassing 5.0% of all ransomware victims, it faces a significant ransomware risk.
Agricultural and chemical materials were the most frequent victims.
Monthly Activity Trends
Ransomware activity in the materials industry has shown a sustained number of victims each month with an uptick in May.
LockBit3 returned in May and together with Medusa is largely responsible for the uptick. The Cactus gang was behind many June victims.
Ransomware Gangs
A total of 17 out of 58 active ransomware groups targeted the materials industry in the past 90 days:
Cactus: 20.6% of their victims were from this industry (7 out of 34 victims), implying a possible focus on this industry.
Lockbit3: Due to its large affiliate base and sheer volume, it presents a high risk (17 out of 186 victims).
The distribution of attacks, a relatively small number of groups indicates that the materials industry is a challenging target compared to a lot more victimized manufacturing.
Geographic Distribution
The geographic distribution of ransomware victims in the materials industry highlights the widespread nature of these attacks.
37% of all victims are located in the US, followed by Italy, India, and the UK.
In total, 20 countries reported ransomware victims in this industry
For a comprehensive, up-to-date global ransomware tracking report, please refer to our new monthly “Tracking Ransomware” series here.
In the past 90 days, the materials industry has faced varying low to moderate risk levels across monitored threat categories.
APT Campaigns: The risk is low to moderate, with 20% of the observed APT campaigns targeting the petrochemical sector. Notable actors included MISSION2025 (APT41 nexus), Lazarus Group, Mustang Panda, and Sandworm. These campaigns mainly exploited web applications, operating systems, and Infrastructure-as-a-Service, impacting countries with robust petrochemical industries. Activity was observed consistently from April to June.
Phishing: The risk remains low for the materials industry, which is generally not a focus for phishing campaigns. The industry’s specialized machinery, intricate production processes, and limited access to high-value personal or financial information make it less lucrative for cybercriminals. Phishing attacks tend to target sectors with more direct ways to monetize or larger repositories of exploitable personal information.
Ransomware: The materials industry faces a moderate ransomware risk, ranking 8th out of 14 industry categories and encompassing 5.0% of all ransomware victims. Agricultural and chemical materials were the most frequent targets. Monthly activity showed sustained numbers, with an uptick in May due to LockBit3 and Medusa, and many June victims attributed to the Cactus gang. In the past 90 days, 17 ransomware groups targeted the industry, with Cactus and LockBit3 posing significant risks. The geographic distribution of victims is widespread, with 37% in the US, followed by Italy, India, and the UK, affecting 20 countries in total.