



The CYFIRMA Industry Report delivers original cybersecurity insights and telemetry-driven statistics of global industries, covering one sector each week for a quarter. This report focuses on the materials industry, presenting key trends and statistics in an engaging infographic format.
Welcome to the CYFIRMA infographic industry report, where we delve into the external threat landscape of the materials industry over the past three months. This report provides valuable insights and data-driven statistics, delivering a concise analysis of attack campaigns, phishing telemetry, and ransomware incidents targeting the materials industry.
We aim to present an industry-specific overview in a convenient, engaging, and informative format. Leveraging our cutting-edge platform telemetry and the expertise of our analysts, we bring you actionable intelligence to stay ahead in the cybersecurity landscape.
CYFIRMA provides cyber threat intelligence and external threat landscape management platforms, DeCYFIR and DeTCT, which utilize artificial intelligence and machine learning to ingest and process relevant data, complemented by manual CTI research.
For the purpose of these reports, we leverage the following data from our platform. These are data processed by AI and ML automation based on both human research input and automated ingestions.
While this report contains statistics and graphs generated primarily by automation, it undergoes thorough review and enhancement for additional context by CYFIRMA CTI analysts to ensure the highest quality and provide valuable insights.
Advanced Persistent Threat Attack Campaigns
Materials organizations featured in 4 out of the 7 observed campaigns, which is a presence in 57% of campaigns.
Observed Campaigns per Month

The monthly chart shows a spike in November after period of generally low campaign detections in September and October.
Suspected Threat Actors
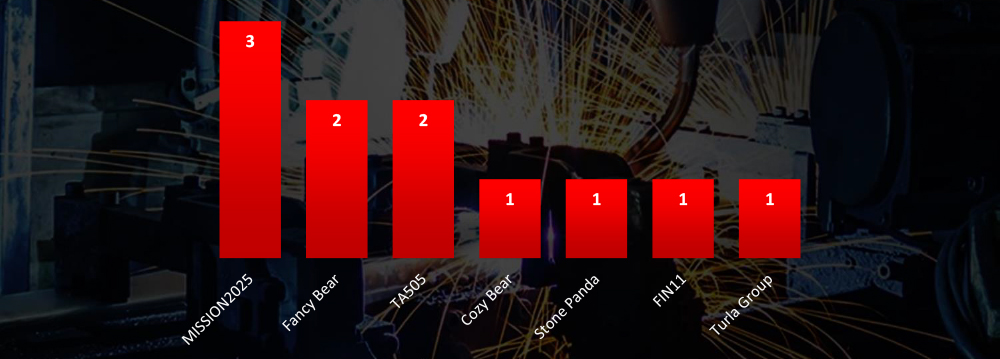
Suspected threat actors are a mix a of nation-state and financially motivated groups.
GEOGRAPHICAL DISTRIBUTION
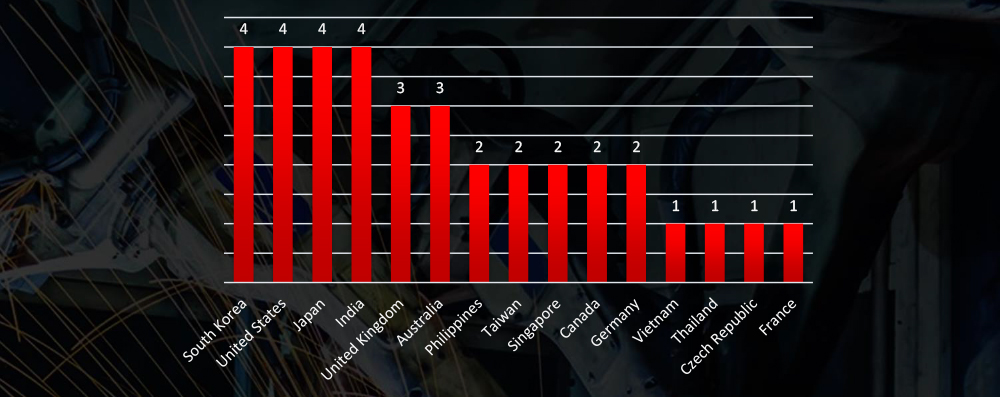
Victims of the observed attack campaigns were recorded in 15 different countries, with many Asian victims in particular.
TOP ATTACKED TECHNOLOGY

Attack campaigns focused on attacking web applications, application security software and operating systems.
Risk Level Indicator: High
Monthly activity has significantly declined since the summer surge, which was attributed to North Korean and Chinese threat actors. Consequently, only seven new campaigns have been uncovered in the past 90 days. Long-term data reveals a cyclical pattern: the discovery of new Tactics, Techniques, and Procedures (TTPs) triggers a surge in campaign identification, followed by a period of relative calm. In November, we are again witnessing a rise in the detection of new campaigns.
Regarding suspected threat actors targeting the materials industry, nation-state APTs slightly outnumber financially motivated threat actors. Specifically, both Russian and Chinese APTs show substantial interest in the materials industry.
In terms of geographical impact, we observe an unusually high presence of Asian countries alongside well-known Western countries with robust materials industries. This correlates with the global supply chain and the outsourcing of materials manufacturing and with Chinese APTs actively pursuing the acquisition of advanced materials research and development.
The targeted technologies in the materials industry victims were web applications, application security software, and operating systems.
Since there are consistently no wider phishing attack campaigns impersonating materials sector, it is not tracked as a category.
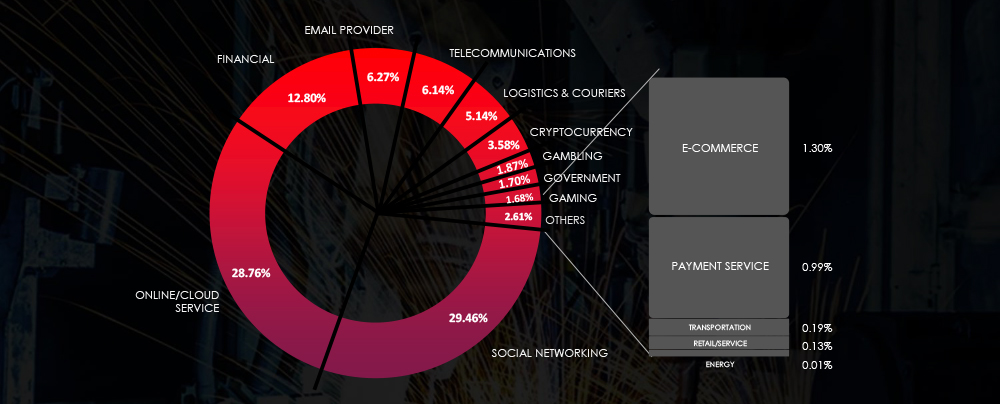
Global Distribution of Phishing Themes per Sector
Risk Level Indicator: Low
Excluding spear-phishing attacks conducted by geopolitically motivated APTs and ransomware affiliates, the materials industry is generally not a primary focus for phishing campaigns due to specific reasons.
Firstly, the industry’s operations involve specialized machinery, intricate production processes, and proprietary technologies. These aspects make it challenging for cybercriminals to comprehend and potentially less lucrative compared to sectors like finance or healthcare.
Moreover, companies in the materials industry typically have limited access to high-value personal or financial information that cybercriminals often seek, such as credit card data or social security numbers. Consequently, the potential gains from phishing attacks on these organizations are relatively lower.
Furthermore, the materials industry often lacks extensive customer databases, which may deter cybercriminals. They tend to prioritize sectors with larger repositories of personal information that can be exploited for illicit purposes.
RANSOMWARE VICTIMOLOGY
In the past 90 days, CYFIRMA has identified 165 verified ransomware victims within the materials industry sectors. This accounts for 10.5% of the overall total of 1,574 ransomware incidents during the same period.
The Monthly Activity Chart

Monthly trends show consistent numbers across months, with August including only last few days.
Breakdown of Monthly Activity by Gang
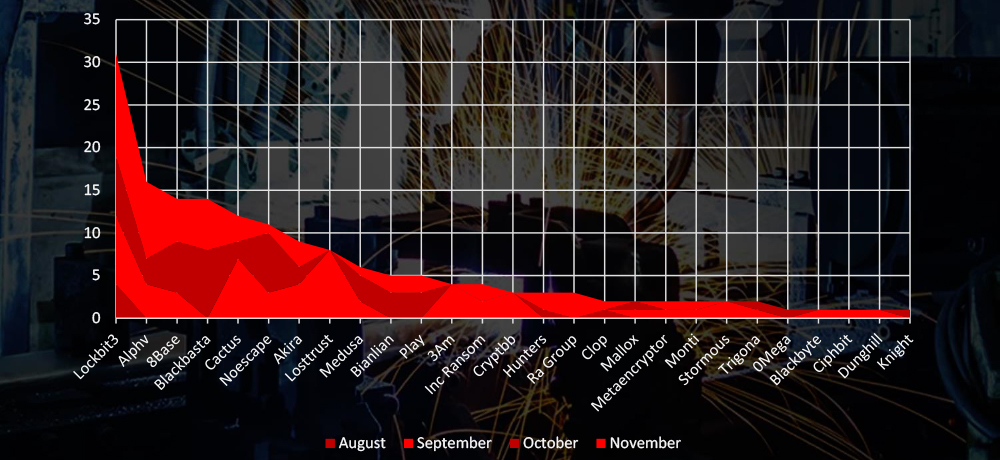
A breakdown of the monthly activity provides insights per group activity. LockBit3 has been consistently active, ALPHV had significant increase in November and BlackBasta recorded materials victims active only in October and November.
Ransomware Victims in Materials Industry per Group
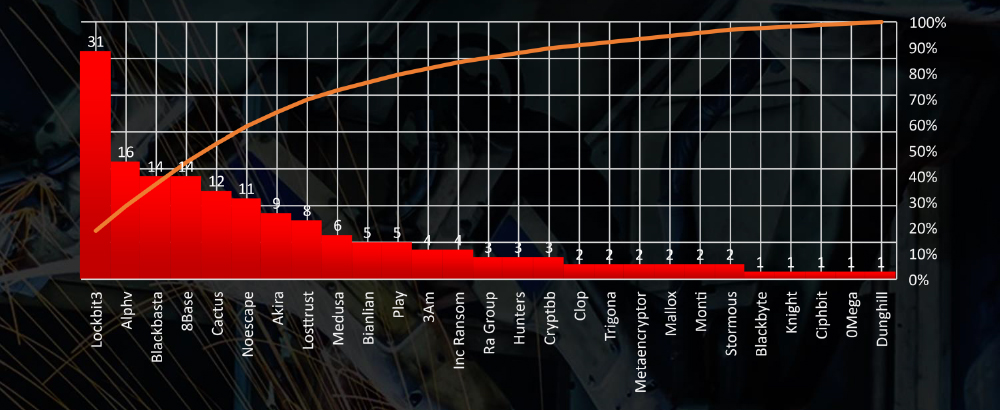
In total 27 out of 49 groups recorded materials industry organization victims in the past 90 days. The top 5 are responsible for half of them.
Comparison to All Ransomware Victims by Group (Top 25)
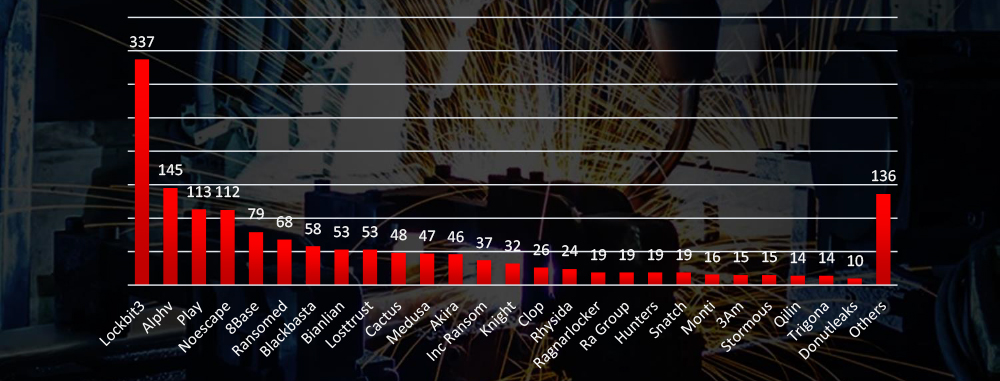
Compared to all recorded victims in the same time period, some groups like Play have comparatively very low share of materials industry victims, suggesting low interest. On the other hand BlackBasta recorded 14 out of all 58 victims in materials industry accounting for 24% of victims, suggesting high interest.
Geographic Distribution Of Victims
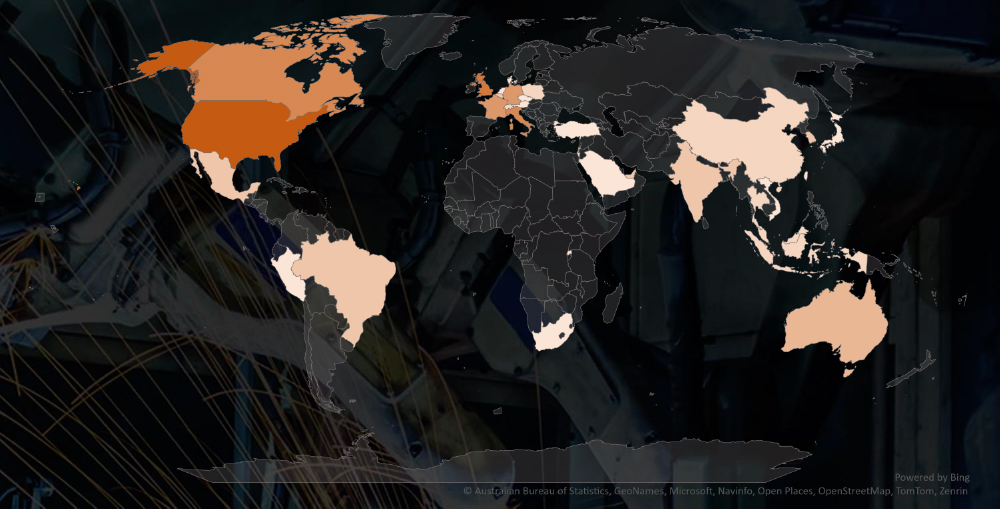
The heatmap of geographic distribution illustrates the global reach of ransomware across continents and is considerably correlated with economies known for materials and specifically mining industry.
Total Victims per Country
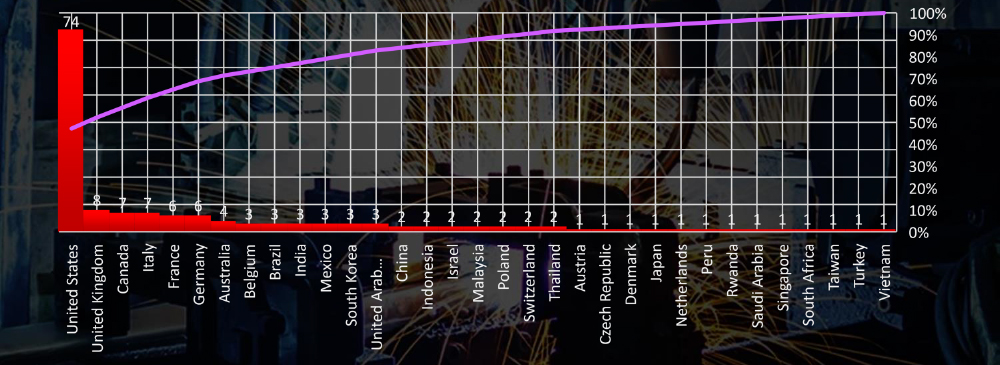
In total a high number of 33 countries recorded materials industry ransomware victims with the US alone accounting for ~48% of all.
Sectors Distribution
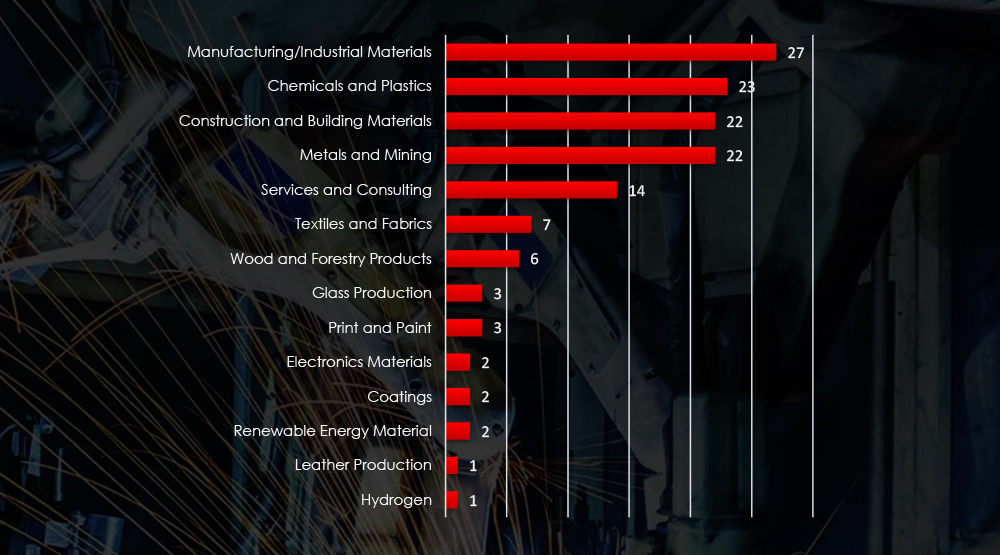
Listing consolidated sectors matched under the materials industry umbrella shows victims across sectors, including some niches.
RANSOMWARE EXTERNAL THREAT LANDSCAPE MANAGEMENT (ETLM) OVERVIEW
Risk Level Indicator: High
The materials industry ranks alongside manufacturing as one of the most targeted sectors for ransomware attacks. Over the last 90 days, approximately one in every ten ransomware victims belonged to the materials industry. Monthly cyber activity consistently demonstrates a significant volume of attacks, with a slight peak observed in September. Analysis of responsible groups highlights LockBit3 as the gang with the highest number of victims. In September, an increased number of victims were attributed to Cactus, Losttrust, 3AM, and various mid-sized and smaller gangs. However, during October and November, ALPHV and BlackBasta recorded the most victims.
Data on the total number of victims per group reveals that larger gangs predominantly target the materials industry, with the top five accounting for half of all victims. Nevertheless, since September, there has been a noticeable rise in the share of victims attributed to newer or rebranded mid-sized groups, indicating an evolving landscape.
Among the 49 active gangs in the past 90 days, 27 have specifically targeted the materials industry. Notably, BlackBasta has exhibited significant interest in this sector, with approximately 25% of their victims belonging to the materials industry.
Geographically, victims span across 33 different countries, with the United States experiencing the highest impact, followed by the UK, Canada, and Italy. The global distribution of victims across continents is particularly striking within the materials industry, surpassing the spread observed in any other industry.
For a comprehensive, up-to-date global ransomware tracking report on a monthly basis, please refer to our new monthly “Tracking Ransomware” series here.
The materials industry, particularly in strategic sectors like defence and cutting-edge technology, confronts significant risks from sophisticated threat actors. Our data highlights a persistent wave of cyberattacks conducted by Chinese and Russian Advanced Persistent Threat (APT) groups across varied regions, notably prominent in Asian countries.
The materials sectors remains a prime target for ransomware gangs, accounting for one in every ten victims in the last 90 days. LockBit3 stands out as the most active, while BlackBasta recorded a quarter of all victims within this industry. Notably, our data indicates a growing number of victims, both from larger and mid-sized ransomware groups, reflecting an evolving threat landscape.
Chemicals/Plastics, Construction and Building materials together with Mining recorded the most ransomware victims.
Due to its complexity and lack of easily exploitable data, the materials industry isn’t an appealing target for phishing cybercriminals. These businesses often lack direct access to high-value personal or financial information and maintain limited customer databases.