



The CYFIRMA Industry Report delivers original cybersecurity insights and telemetry-driven statistics of global industries, covering one sector each week for a quarter. This report focuses on the manufacturing industry, presenting key trends and statistics in an engaging infographic format.
Welcome to the CYFIRMA infographic industry report, where we delve into the external threat landscape of the manufacturing industry over the past three months. This report provides valuable insights and data-driven statistics, delivering a concise analysis of attack campaigns, phishing telemetry, and ransomware incidents targeting the manufacturing industry.
We aim to present an industry-specific overview in a convenient, engaging, and informative format. Leveraging our cutting-edge platform telemetry and the expertise of our analysts, we bring you actionable intelligence to stay ahead in the cybersecurity landscape.
CYFIRMA provides cyber threat intelligence and external threat landscape management platforms, DeCYFIR and DeTCT, which utilize artificial intelligence and machine learning to ingest and process relevant data, complemented by manual CTI research.
For the purpose of these reports, we leverage the following data from our platform. These are data processed by AI and ML automation, based on both human research input and automated ingestions.
While this report contains statistics and graphs generated primarily by automation, it undergoes thorough review and enhancement for additional context by CYFIRMA CTI analysts to ensure the highest quality and provide valuable insights.
Manufacturing organizations featured in 9 out of the 13 observed campaigns, which is a presence in 69% of all campaigns.
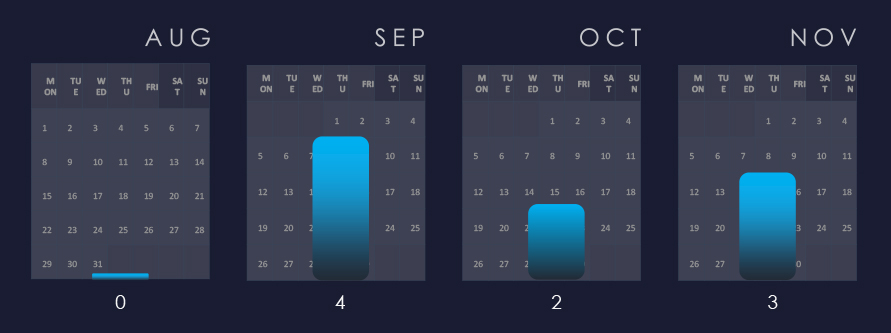
After a mild spike in September, we continued to observe sustained interest in the manufacturing industry.
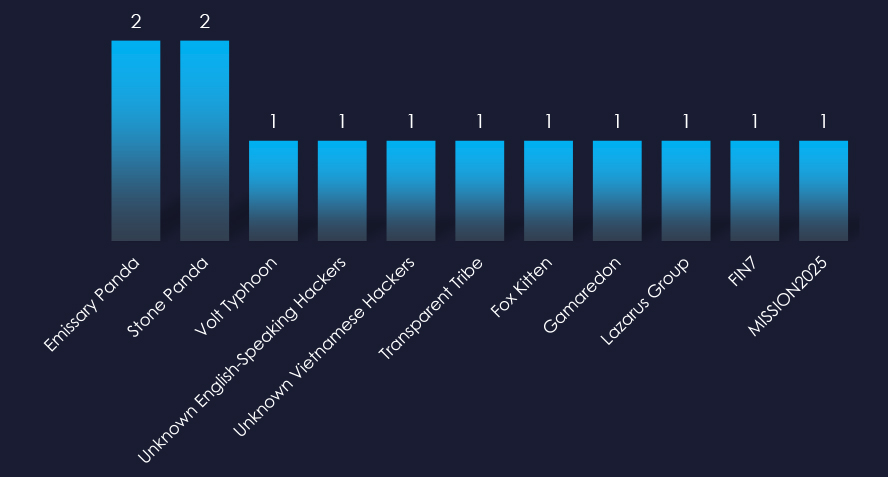
Observed threat actors are varied. While most are linked to China and Russia, we also observed Vietnamese, Pakistani, Iranian, North Korean, and English-speaking threat actors.
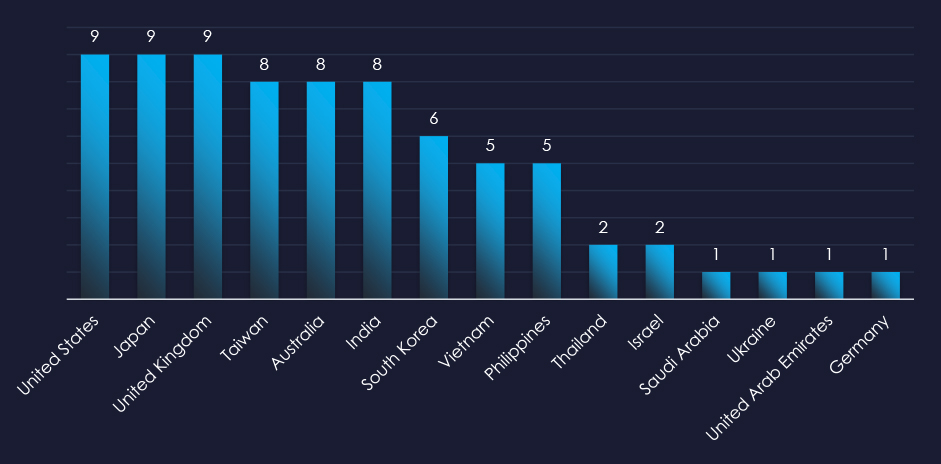
Recorded victims of observed attack campaigns span 15 different countries. Data correlates with known prominent manufacturing countries.
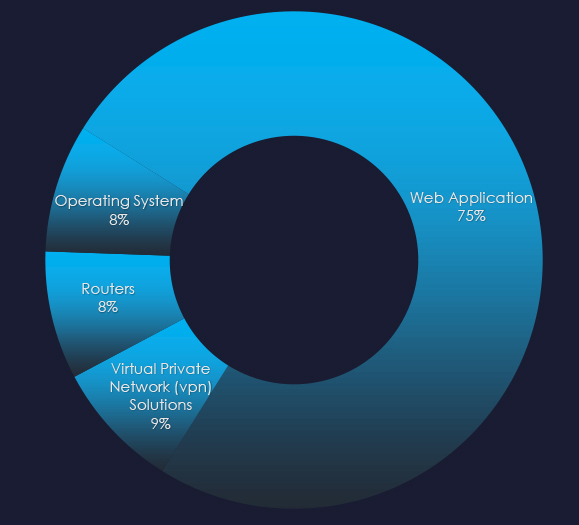
Along with web applications, we observed attacks against operating systems, routers and, VPN solutions.
Risk Level Indicator: High

In the past 90 days, manufacturing organizations have been significantly impacted by advanced persistent threat (APT) campaigns. 69% of observed APT campaigns recorded manufacturing industry victims, with 9 out of 13 total campaigns.
Monthly Trends
We observed a peak of activity in September. However, activity has been sustained since then warranting a high risk factor.
Key Threat Actors
The manufacturing industry is crucial to global economics and geopolitics, making it a frequent target for both financially motivated cybercriminals and nation-state Advanced Persistent Threat (APT) groups.
Notable actors include China-based groups such as Stone Panda (APT10), Emissary Panda (APT27), and Volt Typhoon. Russian-linked groups like FIN7 and Gamaredon have also been active in this sector.
Additionally, Pakistan’s Transparent Tribe (APT36), Iran’s Fox Kitten, and North Korea’s Lazarus Group have targeted the manufacturing industry.
There are also threats from English and Vietnamese-speaking actors which remain unattributed.
Geographical Impact
Cyber campaigns have impacted 15 countries, with those possessing substantial manufacturing economies and trade—such as the United States, the United Kingdom, Japan, Taiwan, and India—being frequent targets. Notably, Vietnam has experienced increased cyber activity, correlating with the growth of its manufacturing sector.
Targeted Technologies
Web applications, operating systems, routers, and VPN solutions have been attacked in observed campaigns.
Over the past 3 months, CYFIRMA’s telemetry detected 126 phishing campaigns themed around manufacturing out of a total of 193,306. All of these are B2B platforms serving manufacturing businesses, rather than being manufacturers themselves, and are therefore not tracked as a distinct category.
The chart below illustrates the global distribution of observed themes. Observed manufacturing-related phishing accounts for 0.06% of all captured phishing attempts.
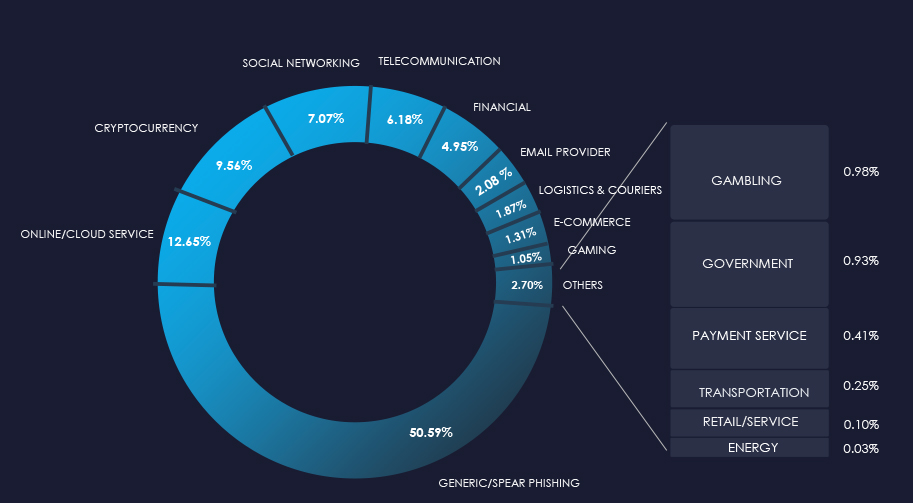
In total 2 manufacturing-related organizations were impersonated in captured phishing attempts during the last 90 days. They are both B2B platforms for manufacturers to trade.
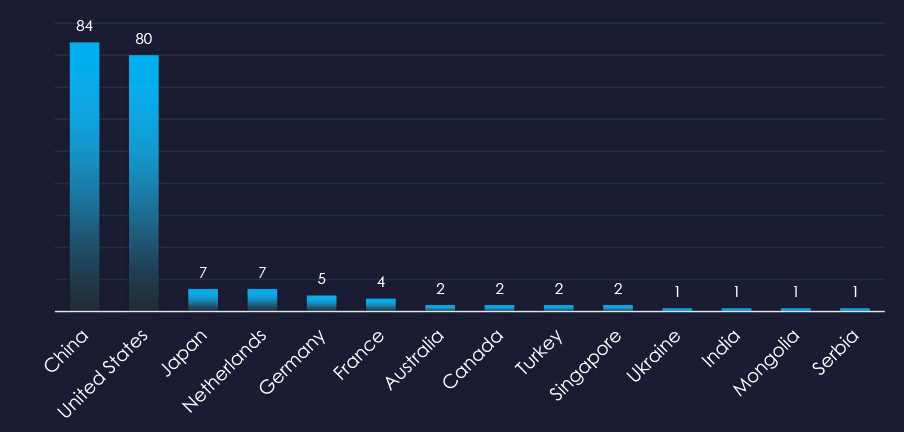
China and the United States are leading sources of manufacturing-themed phishing, consistent with their status as the largest trading partners in manufactured goods.
Risk Level Indicator: Low

Building on insights from previous reports on the manufacturing industry, this sector continues to show limited appeal for broader “spray-and-pray” phishing campaigns.
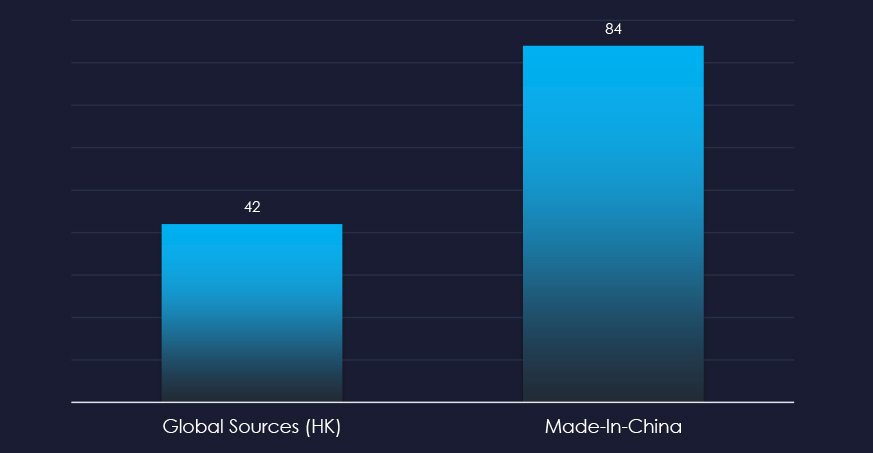
The data highlights Made-in-China as the most impersonated organization linked to manufacturing, although it is a B2B platform for manufacturers and suppliers. Beyond this, Apple, Amazon, or Disney who do have manufacturing operations are present. However phishing is related to their services, not manufacturing.
Analysis of ASN-origin data indicates that platforms Made-in-China and Global Sources (HK), both B2B trading hubs for manufacturers, are targeted from within China and the USA, presumably to target international businesses using these platforms.
Excluding spear-phishing by geopolitically motivated APT groups and ransomware affiliates, the manufacturing industry is generally not a prime target for phishing attacks due to industry-specific factors:
Low Monetizable Value: Specialized machinery and proprietary processes are difficult to exploit compared to financial or healthcare data.
Limited High-Value Data: Manufacturing firms typically lack access to sensitive financial or personal information.
Minimal PII Repositories: The absence of extensive PII databases further reduces their appeal.
These factors make the sector less attractive for generic phishing, despite its importance in global supply chains.
In the past 90 days, CYFIRMA has identified 164 verified ransomware victims in the manufacturing industry. This accounts for 10.8% of the overall total of 1,514 ransomware victims during the same period, placing the manufacturing industry as the 3rd most frequent victim of ransomware.
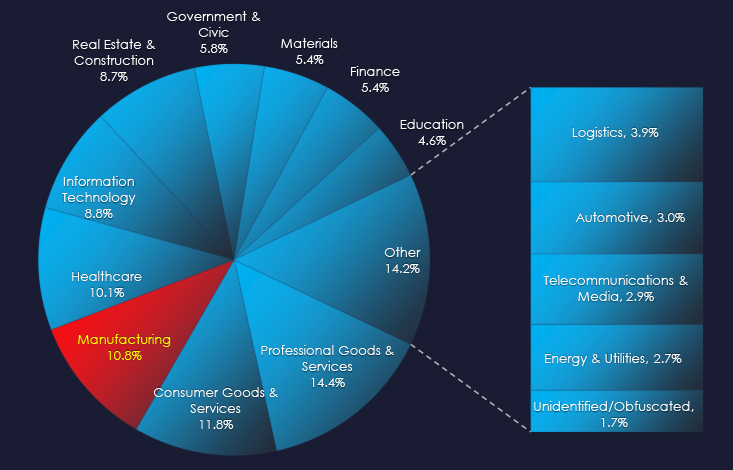
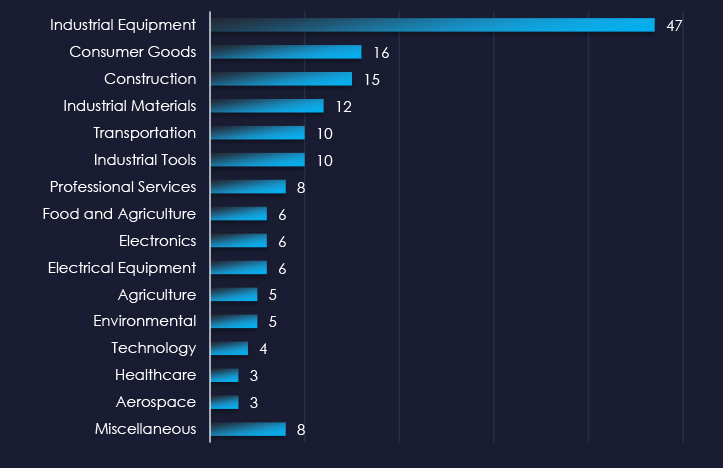
Industrial equipment, tools and materials are the most frequent victims of ransomware in the manufacturing industry.
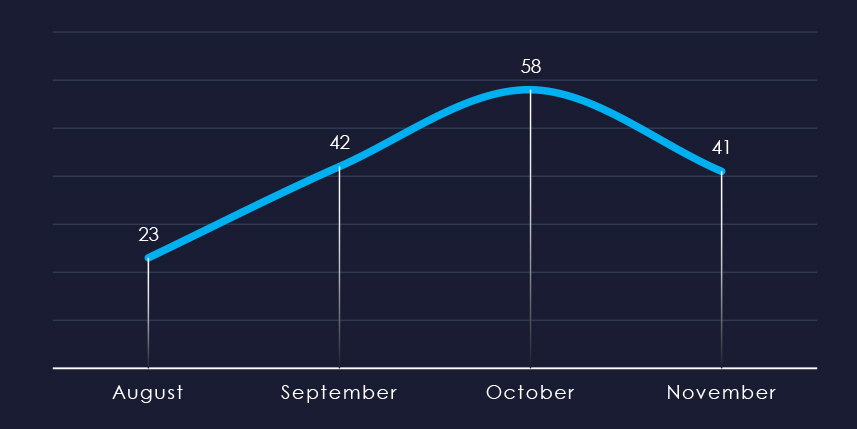
Considering the split months of August and November, we can see sustained numbers of victims with significant growth until October.
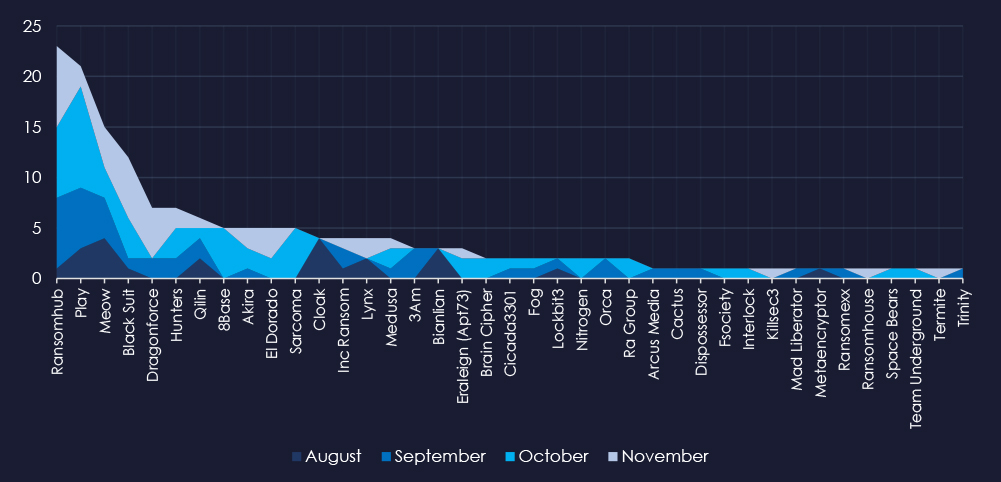
A breakdown of the monthly activity provides insights into which gangs were active each month. For example, RansomHub and Play were very active since September, Dragonforce mainly in November and 8base recorded all victims in October.
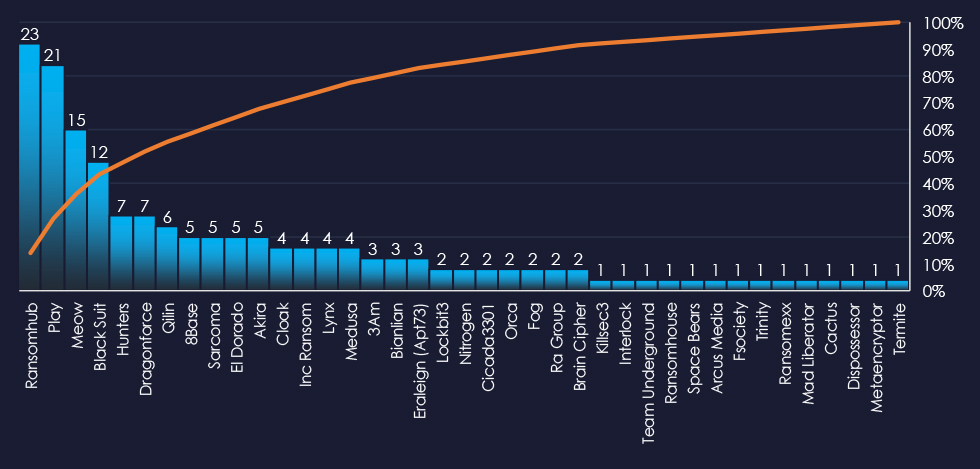
In total 39 out of 62 active groups recorded manufacturing organizations victims in the past 90 days. Notable is the distribution among a large number of groups in this period.
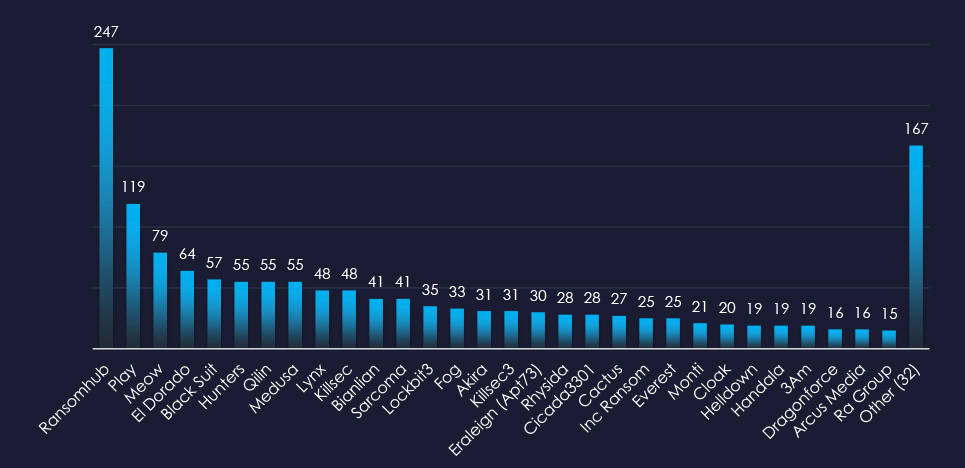
When comparing the manufacturing industry to all recorded victims, Inc Ransom emerges with the highest number of victims overall. Additionally, Blacksuit, Meow, and Play show significant targeting of the manufacturing sector, with 21%, 19%, and 18% of their victims coming from this industry, respectively.
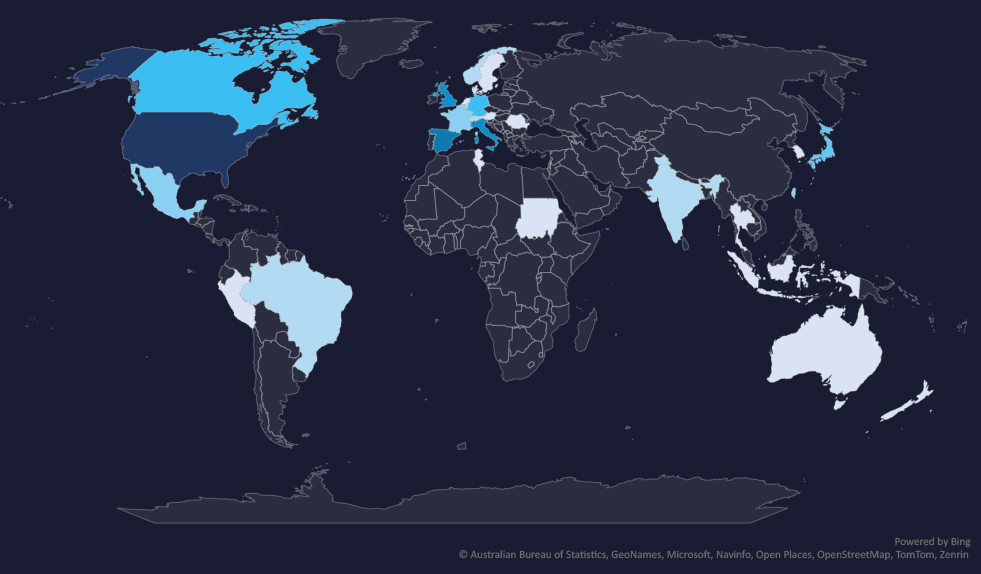
The geographic distribution heatmap underscores the widespread impact of ransomware, highlighting the countries where victims in this industry have been recorded.
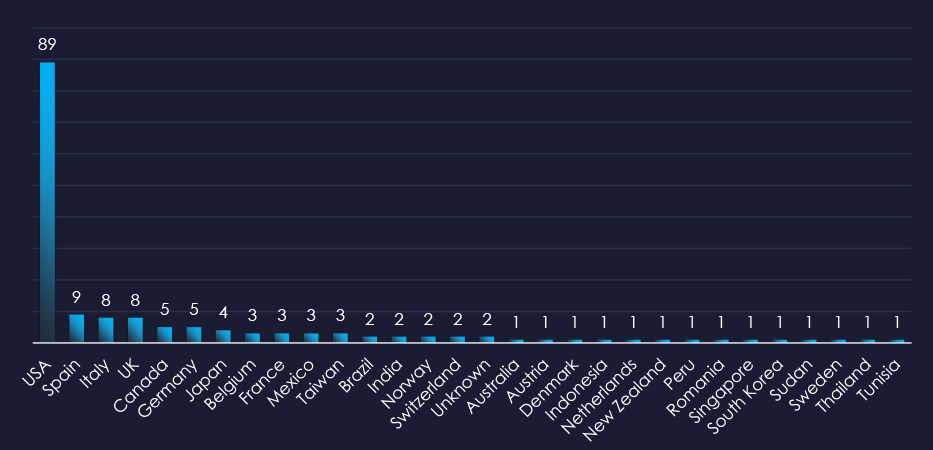
In total 30 countries recorded ransomware victims with the US alone accounting for ~54% of all victims with identified geography.
Risk Level Indicator: High

The manufacturing industry is placed as the 3rd most frequent victim. It faces a sustained and high ransomware threat, with attacks affecting a wide range of sub-sectors and a broad geographic distribution.
Monthly Activity Trends
Ransomware activity in the manufacturing industry recorded a growth from August to November even when considering partial months.
RansomHub and Play were the most active groups overall, during the entire 90-day period, Dragonforce mainly in November, and 8base recorded all victims in October.
Ransomware Gangs
A total of 39 out of 62 active ransomware groups targeted the manufacturing industry, representing 63% participation.
RansomHub: Although only 9% of their victims were in the manufacturing industry (23 out of 247 victims), they accounted for the highest number of victims overall.
BlackSuit, Meow, and Play: These groups showed a stronger focus on manufacturing, with 21%, 19%, and 18% of their victims respectively coming from the sector (12 out of 57, 15 out of 79, and 21 out of 119 victims). This indicates a heightened interest in targeting manufacturing.
Geographic Distribution
The geographic distribution of ransomware victims in the manufacturing industry reflects the industry’s global nature and the widespread reach of these attacks:
54% of all victims with identified geography are located in the US.
In total, 30 countries recorded ransomware victims in the manufacturing industry.
For a comprehensive, up-to-date global ransomware tracking report, please refer to our new monthly “Tracking Ransomware” series here.
Over the past 3 months, CYFIRMA’s DECYFIR platform recorded 5,901 reported vulnerabilities with score higher than 8. This is out of a total 17,755 reported vulnerabilities.
Filtered by relevant vendors, we have observed 174 vulnerabilities with score 8 or above and related to specifically to manufacturing industry.
4 of those reported vulnerabilities have a known exploit.
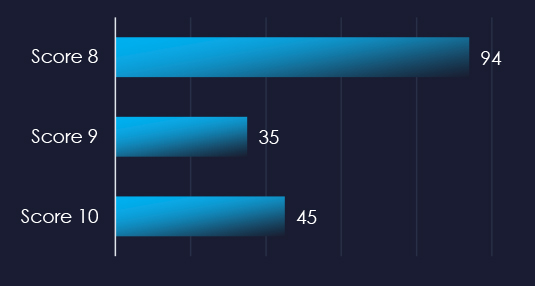
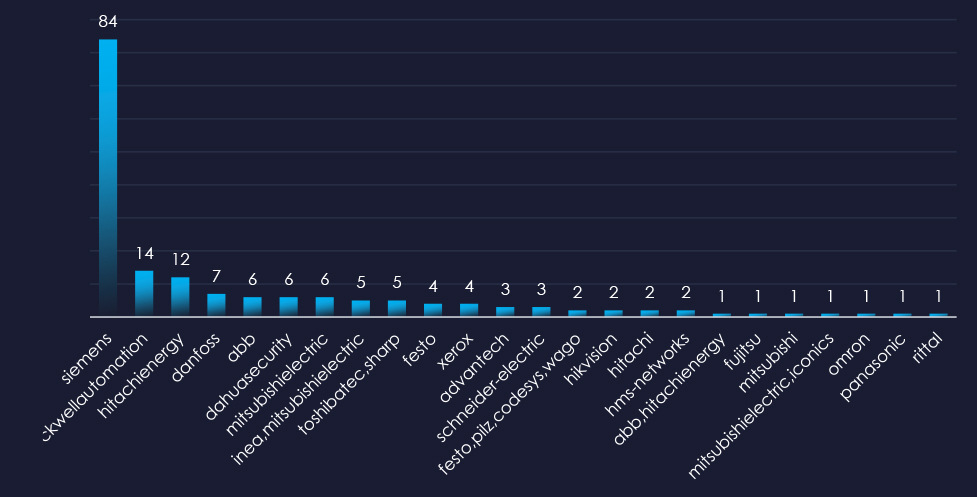
Siemens, Rockwell Automation, and Hitachi Energy are top 3 vendors with reported vulnerabilities with risk score 8 or above.
| Title | NIST LINK |
| Mitsubishi Electric Europe B.V. SmartRTU devices allow XSS via the username parameter or PATH_INFO to login.php. | https://nvd.nist.gov/vuln/detail/CVE-2018-16061 |
| Mitsubishi Electric Europe B.V. SmartRTU devices allow remote attackers to obtain sensitive information (directory listing and source code) via a direct request to the web URI. | https://nvd.nist.gov/vuln/detail/CVE-2018-16060 |
| An issue was discovered on Mitsubishi Electric Europe B.V. ME-RTU devices through 2.02 and INEA ME-RTU devices through 3.0. An unauthenticated remote configuration download vulnerability allows an attacker to download the smartRTU’s configuration file (which contains data such as usernames passwords and other sensitive RTU data). | https://nvd.nist.gov/vuln/detail/CVE-2019-14927 |
| An issue was discovered on Mitsubishi Electric Europe B.V. ME-RTU devices through 2.02 and INEA ME-RTU devices through 3.0. An unauthenticated remote OS Command Injection vulnerability allows an attacker to execute arbitrary commands on the RTU due to the passing of unsafe user-supplied data to the RTU’s system shell. Functionality in mobile.php provides users with the ability to ping sites or IP addresses via the Mobile Connection Test. When the Mobile Connection Test is submitted action.php is called to execute the test. An attacker can use a shell command separator (;) in the host variable to execute operating system commands upon submitting the test data. | https://nvd.nist.gov/vuln/detail/CVE-2019-14931 |
Over the past 90 days, manufacturing organizations have faced low to high cyber risks across monitored categories.
APT Campaigns: 69% (9 out of 13) of observed campaigns targeted the sector, peaking in September with sustained activity since. Key threat actors included Chinese groups (Stone Panda/APT10, Emissary Panda/APT27, Volt Typhoon), Russian groups (FIN7, Gamaredon), Pakistan’s Transparent Tribe (APT36), Iran’s Fox Kitten, and North Korea’s Lazarus Group. Unattributed English and Vietnamese-speaking actors were also active. Attacks impacted 15 countries with significant manufacturing economies like the U.S., U.K., Japan, Taiwan, and India, and increased activity in Vietnam.
Phishing: The sector shows limited appeal for broad phishing campaigns. Made-in-China was the most impersonated organization but as a B2B platform. Companies like Apple, Amazon, and Disney appeared, but phishing targeted their services, not manufacturing. The industry is less attractive for generic phishing due to specialized machinery, limited high-value data, and minimal PII repositories.
Ransomware: Ranked as the 3rd most frequent victim, the industry faces a high ransomware threat with attacks affecting various sub-sectors globally. Activity grew from August to November. RansomHub and Play were the most active groups throughout the period. Out of 62 active ransomware groups, 39 targeted manufacturing (63% participation). Groups like BlackSuit, Meow, and Play showed a strong focus on manufacturing, with 21%, 19%, and 18% of their victims in the sector, respectively. 54% of victims are located in the U.S., with attacks recorded in 30 countries.
Vulnerabilities: Of 17,755 reported vulnerabilities, 5,901 were high-severity (scored above 8). Specifically, 174 high-scoring vulnerabilities related to manufacturing were identified, with 4 having known exploits requiring immediate attention.