



The CYFIRMA Industry Report delivers original cybersecurity insights and telemetry- driven statistics of global industries, covering one sector each week for a quarter. This report focuses on the logistics and transportation industry (excluding automotive for dedicated report), presenting key trends and statistics in an engaging infographic format.
Welcome to the CYFIRMA infographic industry report, where we delve into the external threat landscape of the logistics and transportation industry, over the past three months. This report provides valuable insights and data-driven statistics, delivering a concise analysis of attack campaigns, phishing telemetry, and ransomware incidents targeting logistics, transport, delivery or postal services worldwide.
We aim to present an industry-specific overview in a convenient, engaging, and informative format. Leveraging our cutting-edge platform telemetry and the expertise of our analysts, we bring you actionable intelligence to stay ahead in the cybersecurity landscape.

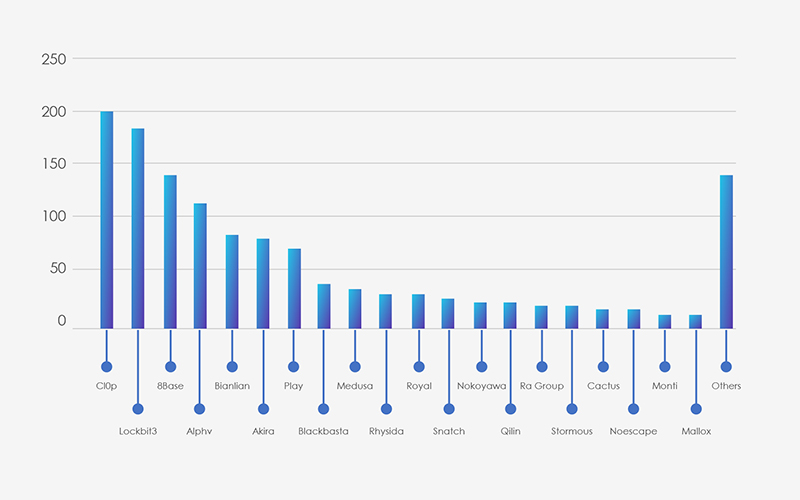
The logistics and transportation industry observed 22 campaigns, fewer as compared to most attacked industries like finance or manufacturing. Nation-state APTs find this industry less strategically interesting for cyber campaigns.
However, financially motivated APTs target this sector due to shared vulnerabilities with manufacturing. Thus, each hour of service interruption is costly.
The rise in cyber activity in June and July likely links to Barracuda ESG vulnerability, coinciding with ransomware reports from victims, involving FIN7, FIN11, and TA505.
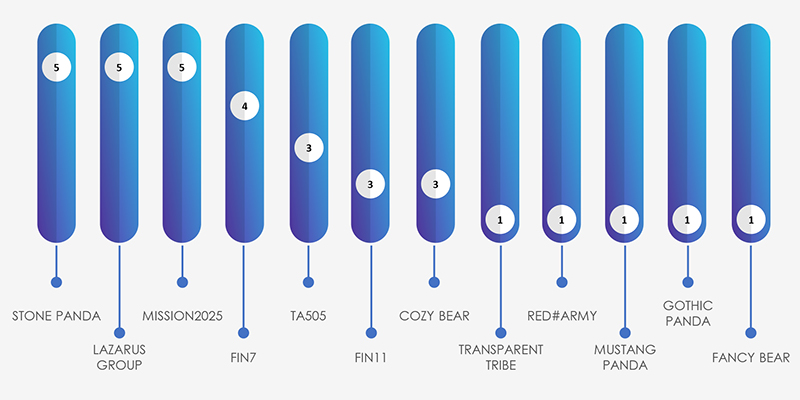
Lazarus Group, FIN7, FIN11 and TA505 are top suspected threat actors, further indicating that financially motivated APTs are lot more interested in logistics and transport than nation-state APTs.
Note that MISSION2025 is a nexus of Chinese APT activity and various Pandas do overlap as suspected TA..
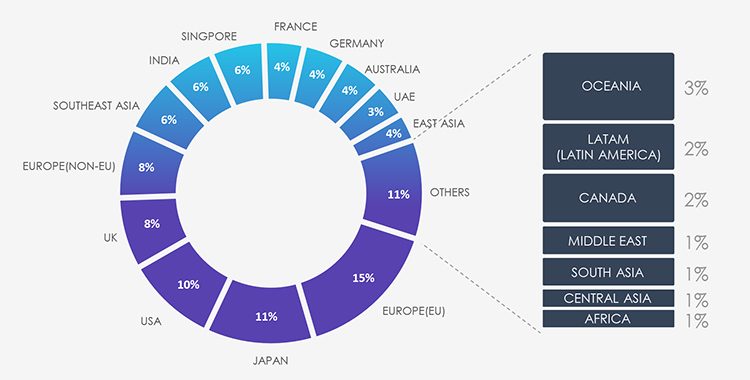
Aligned with the broader threat landscape and respective victimology, the most targeted geographies continue to be Western developed economies and Japan. Additionally, noteworthy are Singapore, India and UAE being strong or large economies with robust logistics industries. Finally, Southeast Asia displays an emerging trend in cyber targeting.
Due to the overlapping nature of monitoring telemetry, further breakdown beyond the top 10 countries is calculated for regions rather than individual countries to maintain clarity.
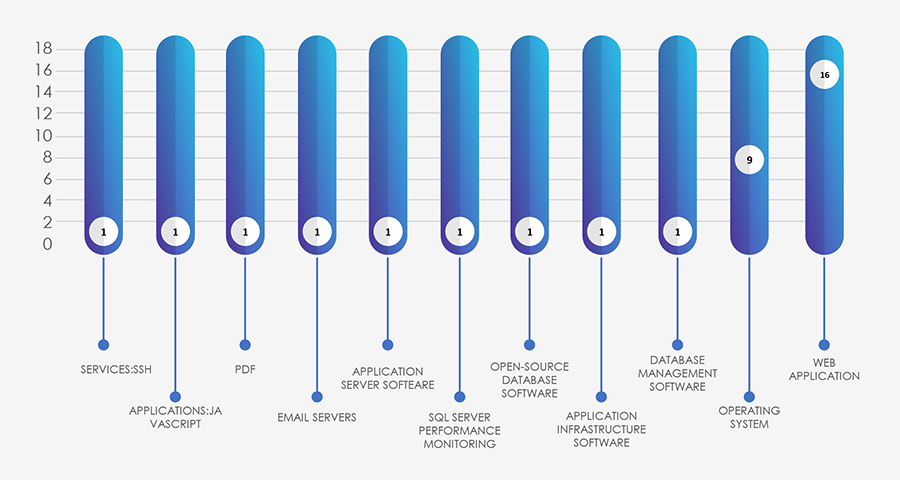
The analysis of technologies targeted by APTs reaffirms a significant emphasis on exploiting vulnerabilities within web applications, followed closely by operating systems. Notably, in the logistics and transportation sector, database software appears to be a significant target.
Phishing attacks, specifically targeting or impersonating logistics, couriers, and transportation, have prominently ranked among the Top 5 targeted sectors. Over the past 3 months, CYFIRMA’s telemetry observed a 6.87% share of the total 220,060 phishing attacks, with the logistics, couriers, and transportation sectors being affected.
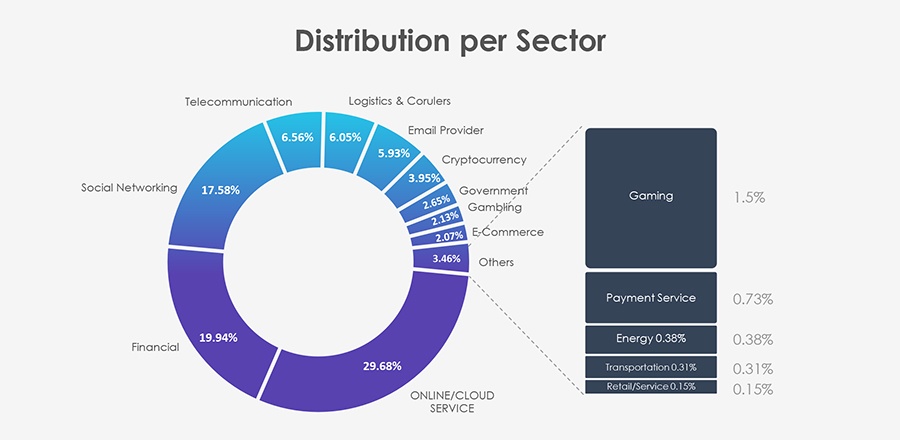
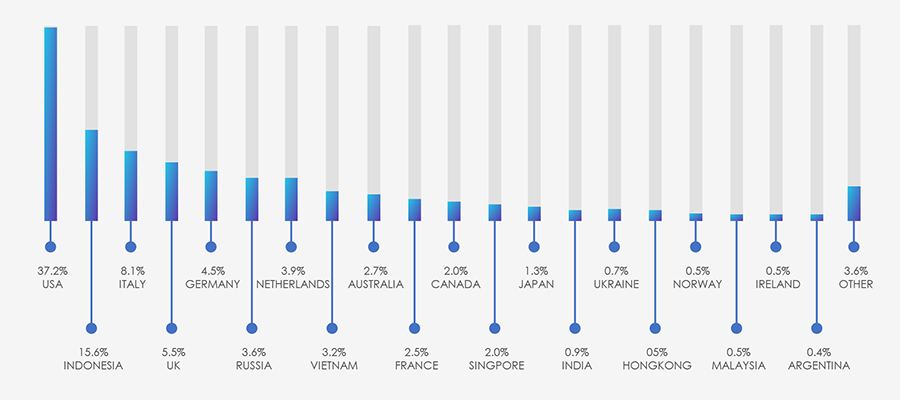
The substantial volume of observed phishing attacks provides intriguing insights. Notably, Indonesia and Vietnam secured the second and eighth positions, comprising 15.6% and 3.2%, respectively, driven by an extensive DHL impersonation campaign originating from multiple Indonesian and Vietnamese ASNs.
The remaining distribution aligns with local national postal services being impersonated.
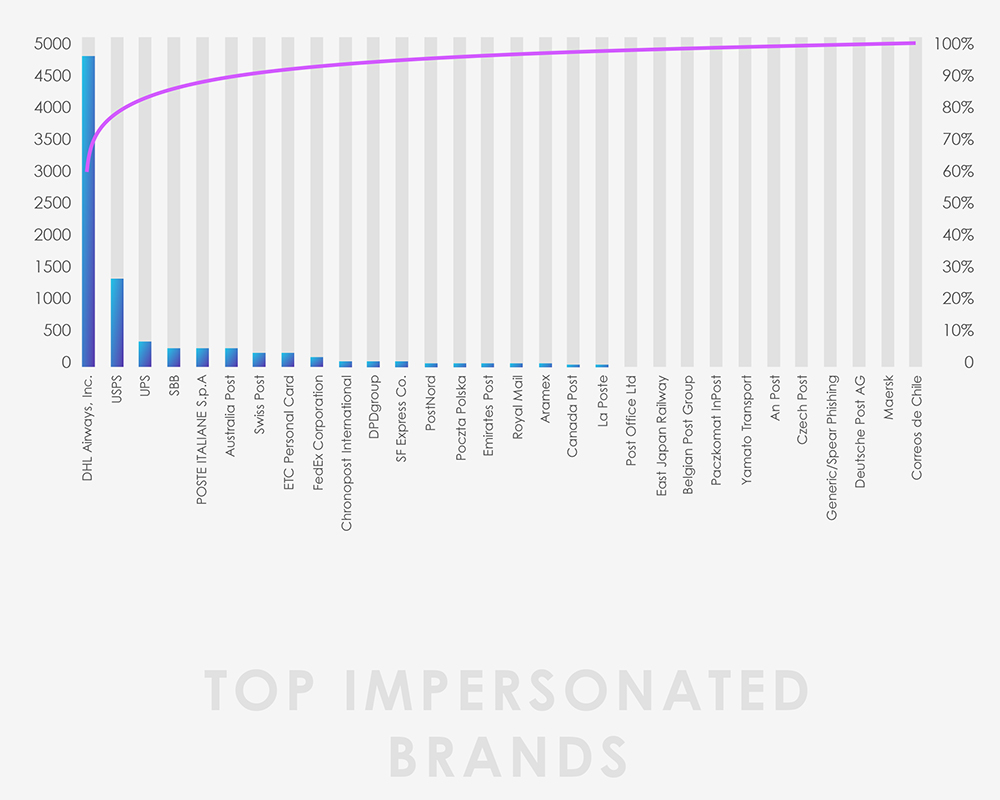
DHL impersonation constitutes a significant 60.4% of all observed campaigns, followed by the United States Postal Service (USPS) at 14.3%, and UPS in third place with 3.9%.
Though these figures might pale in comparison to the largest organizations, it is noteworthy that nearly every country experiences phishing attempts through the impersonation of local postal or other delivery services, facilitating localized scams.
Globally, courier and parcel delivery phishing and scams have emerged as prominent trends in recent years, driven by the heightened utilization of these services during pandemic lockdowns, and this trend is expected to persist for the foreseeable future.
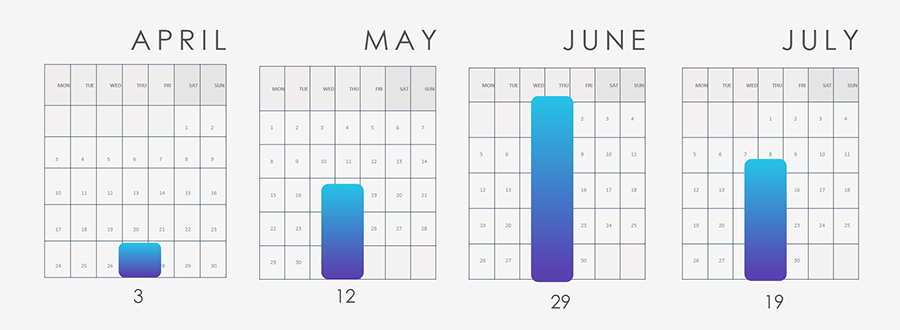
Over the past 90 days, CYFIRMA has verified 63 ransomware victims from diverse logistics and transportation sectors, constituting 4.5% of the overall total of 1,392 ransomware incidents during the same period.
The low victim count in April can be dismissed as it only accounted for a few days. Notably, there was a substantial spike in ransomware incidents during June.
Examining the monthly activity breakdown of each group reveals that significant players such as Lockbit3, Blackbasta, and Banlian reported the majority of their victims during June, exhibiting lower volumes in other months. Similarly, Akira, ALPHV, and Black Suit also reported a considerable number of victims in June.
However, no evidence suggests a coordinated attack on the logistics and transportation industry. Instead, the spike in June appears coincidental, likely stemming from individual group activities, rather than a joint effort.
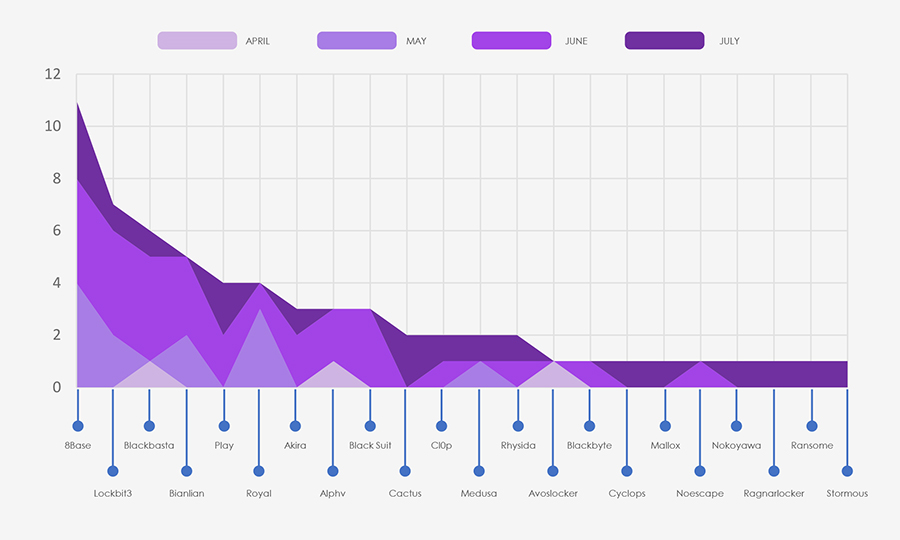
The distribution of incidents per group indicates varying levels of interest in logistics and transportation, among different threat actor groups.
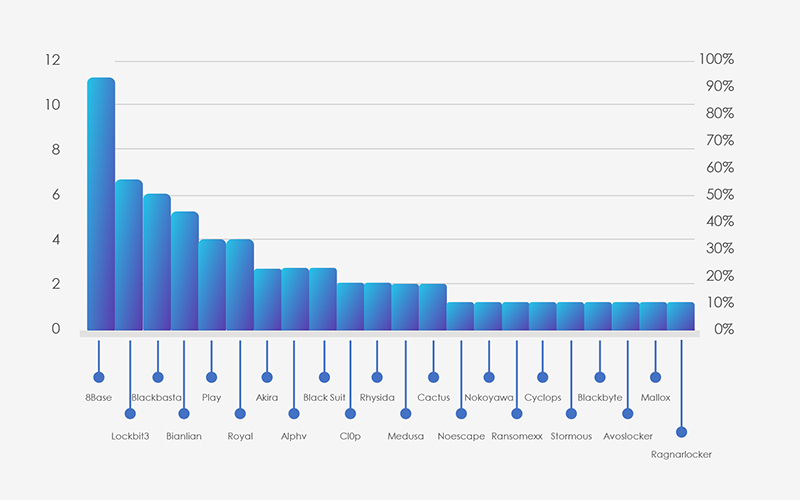
When comparing to the chart of all victims, it becomes evident that Cl0p and ALPHV have notably fewer victims in this industry. On the other hand, the Black Suit group stands out, accounting for 3 out of 5 victims in the logistics sector.
Out of the 63 known victims, the United States stands as the most affected by ransomware attacks in the logistics and transportation industry, accounting for 26 cases. This reaffirms the US’s position as a prime target across industries, owing to its economic significance and robust digital infrastructure.
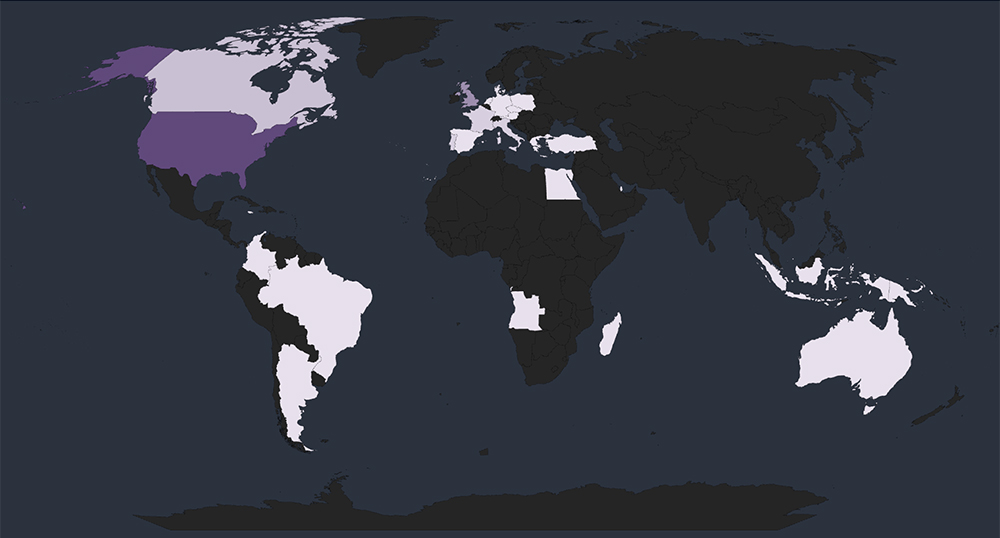
Global Spread – Remaining known incidents with identified victim’s countries are the United Kingdom (6 victims), Canada (3 victims) France, Portugal and Italy (2 victims each). Together with the USA, these countries collectively account for 65% of all victims.
Despite the concentration of attacks in certain countries, ransomware incidents have a global reach. The presence of victims in countries like Madagascar, Papua New Guinea, Angola, and Qatar shows that no region is immune to ransomware threats. Cyber attackers are capable of reaching and targeting vulnerable organizations across the world.
Vulnerability Over Geography – The spread of ransomware attacks across various countries suggests that many threat actors prioritize exploiting vulnerabilities within organizations, regardless of their geographical location.
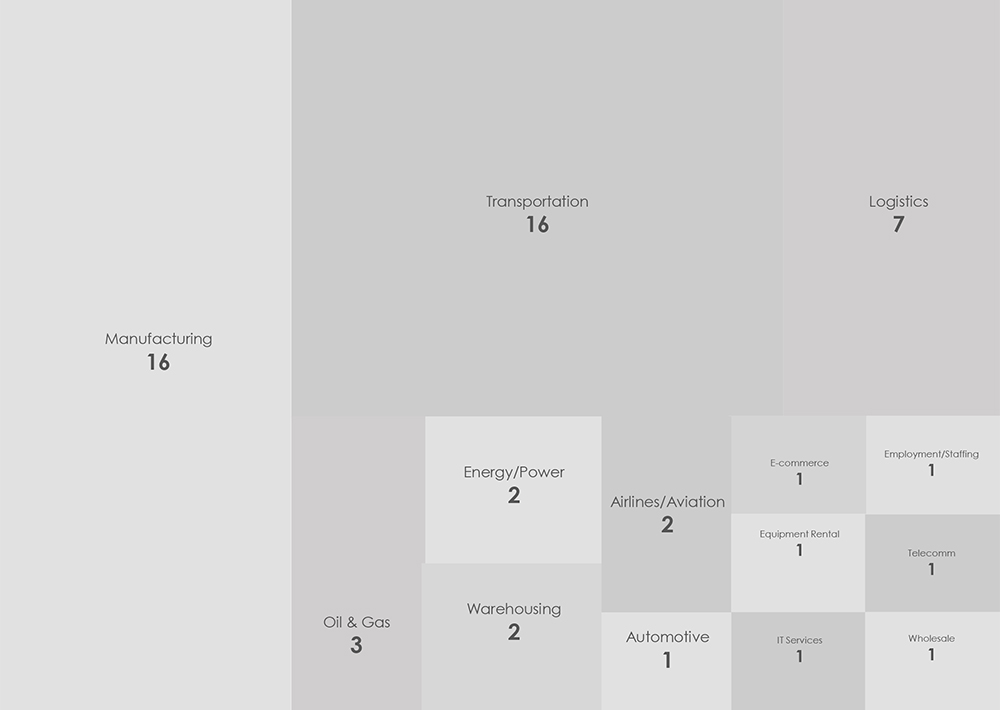
The distribution of ransomware incidents over the past 90 days spans across multiple sectors of logistics & transportation, with several experiencing significant impact. Notably, the manufacturing of logistics equipment and transportation sectors both recorded 16 victims, while logistics accounted for 7 victims. The oil & gas and energy transport sectors each faced 3 and 2 victims, respectively, and warehousing and airlines/aviation sectors each had 2 victims.
The data indicates that manufacturing, across all industries, remains among the hardest- hit sectors, closely followed by transportation. These sectors share a common vulnerability, where even a minute of service disruption incurs high costs, granting cybercriminals potent leverage to enforce ransom demands.
Moreover, the ransomware’s broad targeting extends beyond the hardest-hit sectors, encompassing businesses involved in dangerous goods transportation, moving equipment rental, and specialized telecommunication for truck fleets. This underscores the opportunistic nature of ransomware attacks, where even niche sectors become targets for cybercriminals.
In conclusion, while logistics and transportation may not be at the forefront of the most attacked industries, they do bear a significant burden of cyber-attack victims. Their susceptibility to financially motivated threat actors, particularly ransomware, stems from the substantial cost of service outages. However, the inherent complexities of halting an entire fleet of vehicles make them a distinct challenge, when compared to the relatively easier disruption of assembly lines in manufacturing.
A notable trend that has emerged is the prevalence of delivery and postal services in phishing attack impersonations. Exploiting the popularity of both personal e- commerce and business shipping, threat actors seek to profit from fabricated fees or, more concerning, gain initial access to targeted organizations.