



The CYFIRMA Industry Report delivers original cybersecurity insights and telemetry- driven statistics of global industries, covering one sector each week for a quarter. This report focuses on the Information Technology industry, presenting key trends and statistics in an engaging infographic format.
Welcome to CYFIRMA infographic industry report, where we delve into the external threat landscape of the Information Technology industry over the past three months. This report provides valuable insights and data-driven statistics, delivering a concise analysis of attack campaigns, phishing telemetry, and ransomware incidents targeting IT organizations, including services, software and hardware.
We aim to present an industry-specific overview in a convenient, engaging, and informative format. Leveraging our cutting-edge platform telemetry and the expertise of our analysts, we bring you actionable intelligence to stay ahead in the cybersecurity landscape.
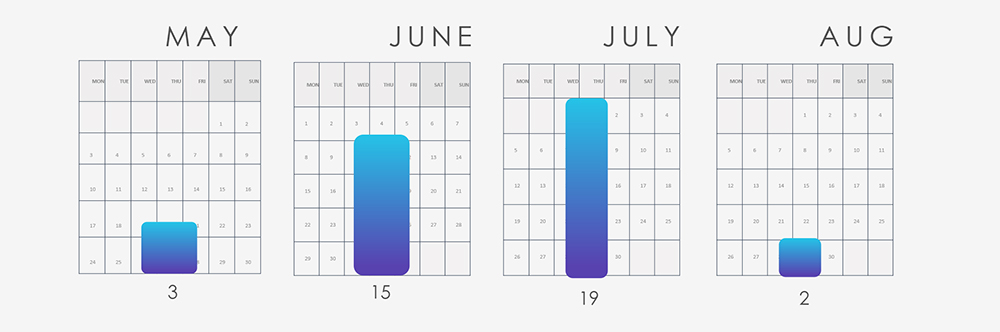
The IT sector was involved in 39 out of the observed 68 campaigns (57%) during the same time period, a substantial count compared to other industries. This is expected, given the persistent presence of IT vendors, their products, and services, which are frequently targeted for access.
The substantial increase in campaign volumes during June and July is consistent with the discovery of the Barracuda ESG vulnerability, heightened activity by the Lazarus Group, and a sequence of ransomware incidents involving the FIN7, FIN11, and TA505 threat actors.
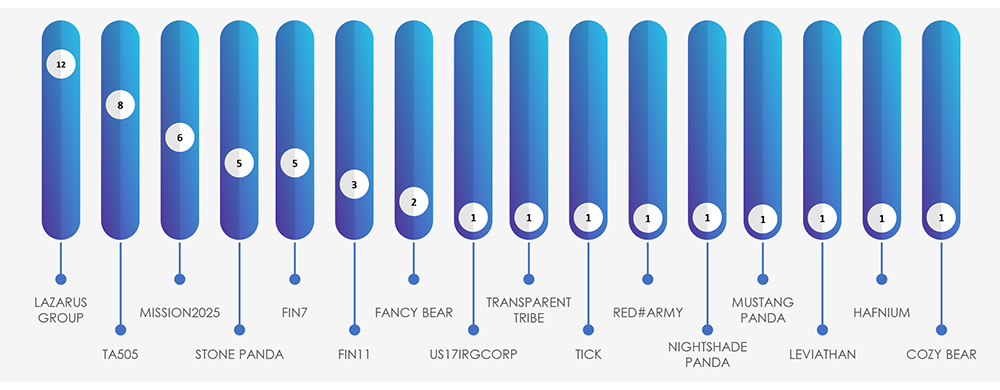
Alongside Lazarus Group, FIN7, FIN11, and TA505, there are multiple suspected threat actors, including various APTs tied to the Chinese nexus of nation-state activity, notably Stone Panda.
It’s important to highlight that MISSION2025 serves as a central point for Chinese APT operations, with several instances of “Pandas” suspected to overlap with it.
The attack campaigns targeting organizations within the IT industry align with the strategic goals of the nation-state APTs involved. EU countries takes the lead as the most targeted region, followed by Japan and USA. This correlates with scattered nature of various IT services, solutions and products vendors.
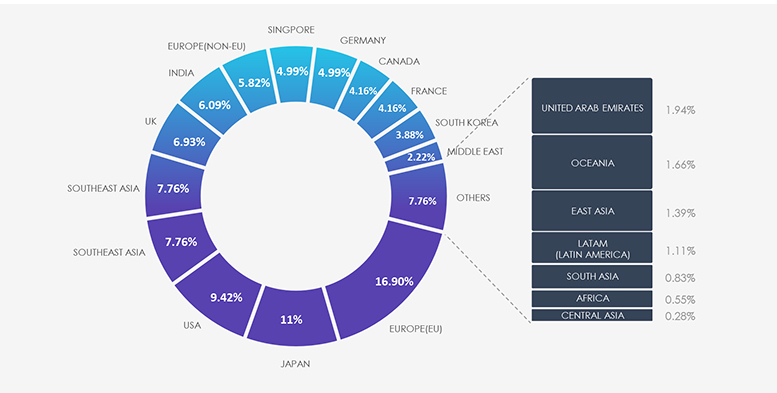
Due to the overlapping nature of monitoring telemetry, further breakdown beyond the top 10 countries is calculated for regions rather than individual countries to maintain clarity.
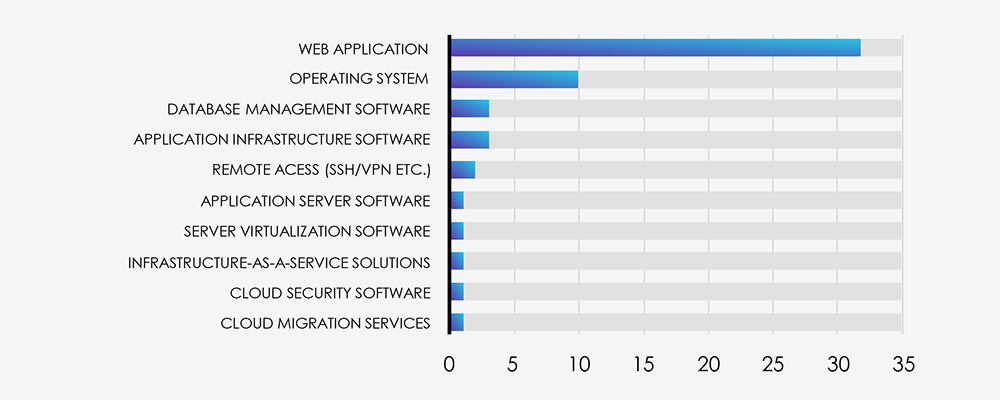
Looking at the technologies targeted, it’s clear that APTs focus on exploiting Web Applications the most, making them the main target for their attacks. After that, Operating Systems also stand out, showing their ongoing vulnerabilities. Additionally, there’s a growing interest in targeting Infrastructure and Cloud Services, which highlights a wider range of vectors attackers are aiming for.
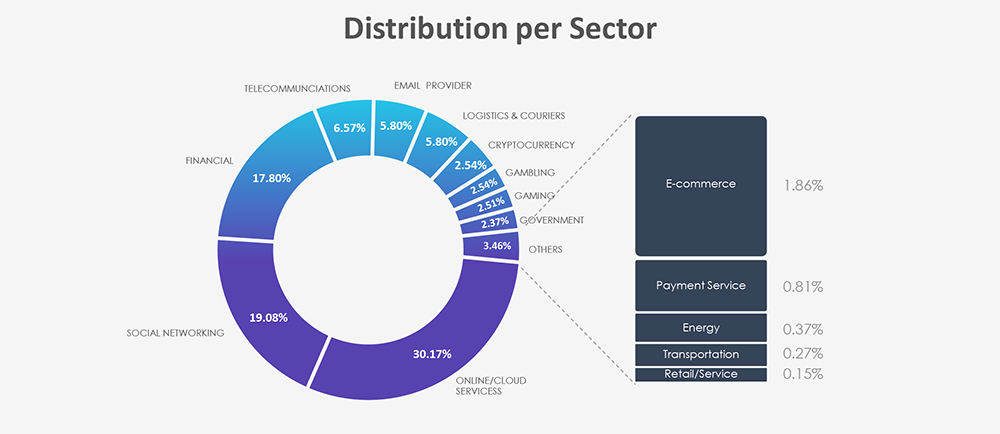
Phishing attacks explicitly targeting or impersonating the IT industry, tracked as Online/Cloud Services and Email Providers are the most frequent. Over the past 3 months, CYFIRMA’s telemetry recorded 79,657 phishing attacks out of a total of 221,453, making up 35.97% of all phishing attack campaigns observed.
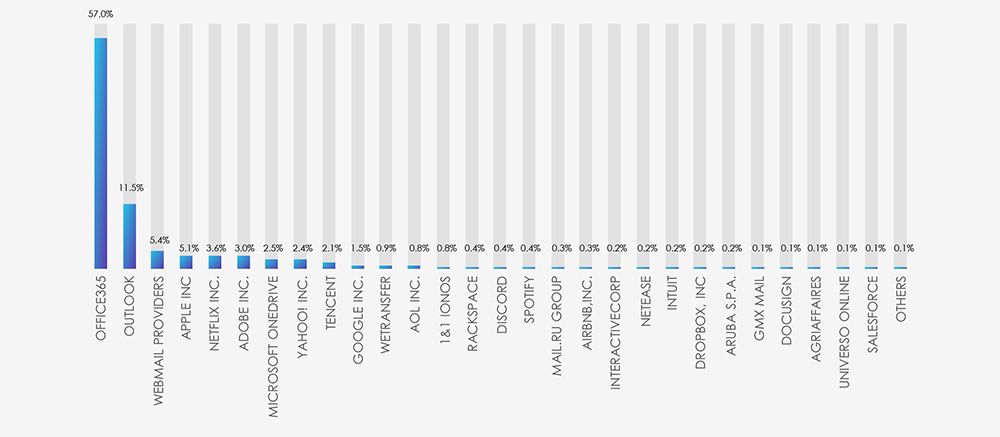
Most impersonated brands or services in IT industry are what most people would expect from their own experience in personal and business mailboxes. Over a half of the campaigns are using Office 365 as phishing lure and another 11% Outlook. At 3rd place are bundled various smaller national webmail providers, followed by the most popular online service providers like Apple, Adobe, OneDrive etc.
Distribution per Sector
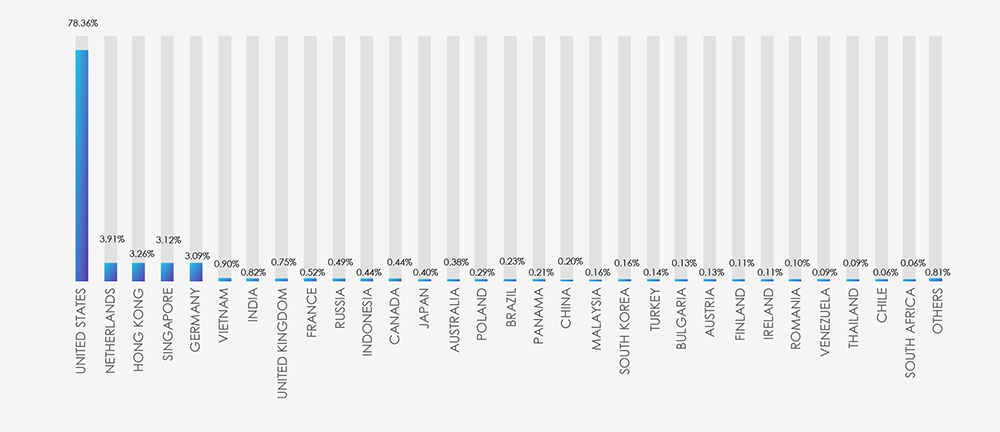
Scams and phishing attempts impersonating IT Industry and online services specifically have been around since the dawn of phishing itself. They allow truly global “spray and pray” phishing campaigns. The geographical distribution based on ASN of phishing origin aligns with the broad threat landscape and countries known to allow for less strict online hosting provider rules.
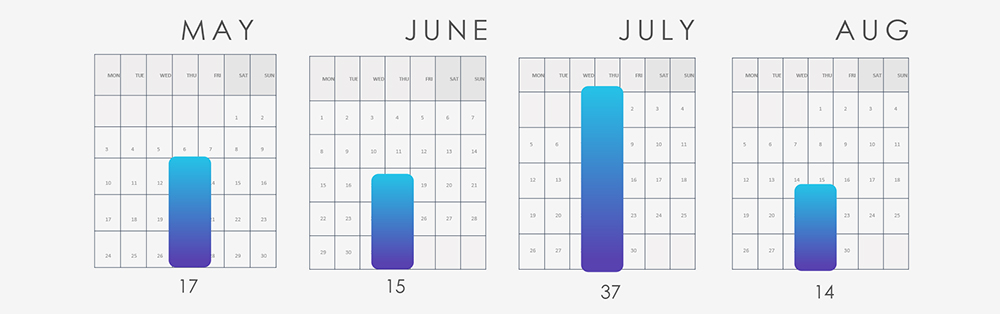
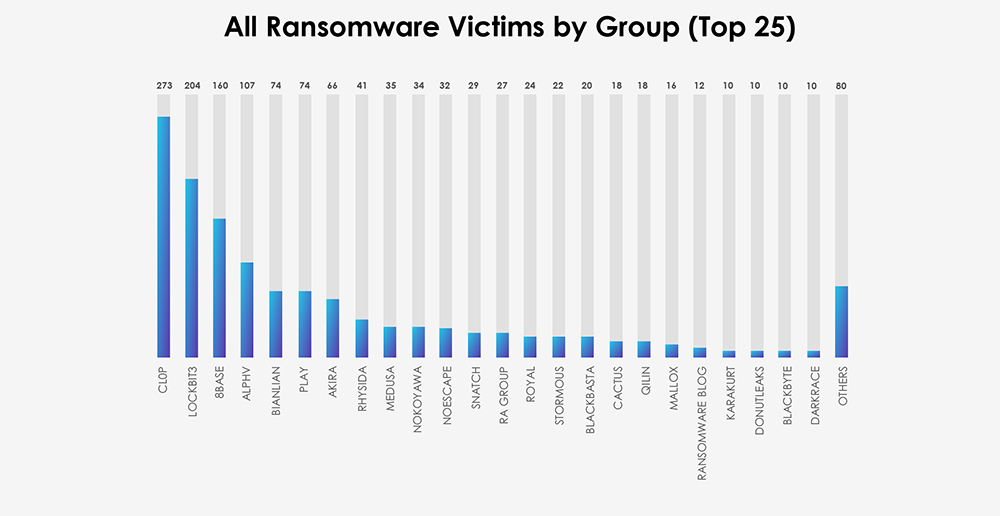
In the past 90 days, CYFIRMA has identified 83 verified ransomware victims within the IT industry sectors. This accounts for 6.6% of the overall total of 1,263 ransomware incidents during the same period, a significant statistic, given the industry’s distinct emphasis.
A marked upsurge in July’s figures is attributed to the Cl0p gang, which published all of their 16 victims in July, as part of their extensive spree throughout late June and July.
The aforementioned Cl0p gang is distinctly visible in the breakdown chart below. Additionally, the chart highlights that the major groups, namely Lockbit3, 8Base, ALPHV and Akira, are accountable for the majority of the attacks. Following these are 12 other gangs, each responsible for between 4 to 1 victims.
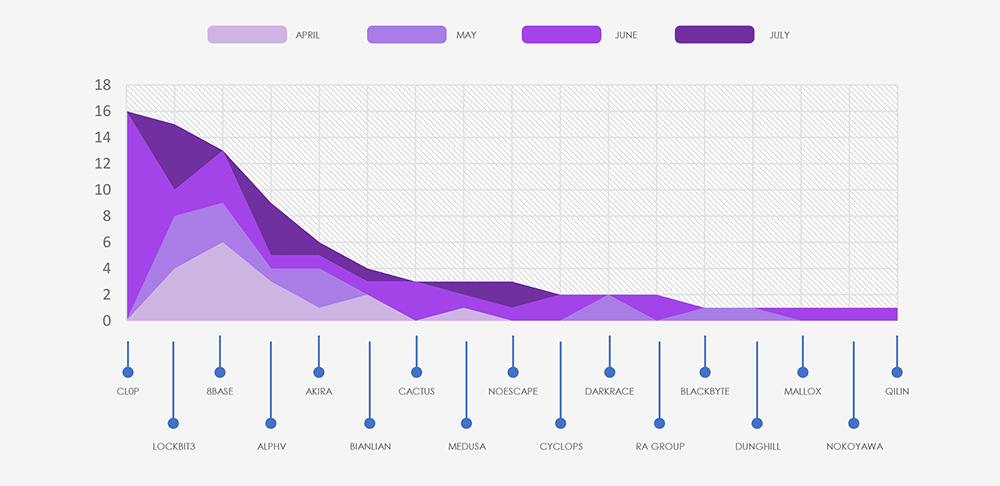
The subsequent chart underscores the dominance of major ransomware gangs, with the top 5 accounting for 75% of all victims. Simultaneously, the chart illustrates how the collective activity of smaller groups contributes to a substantial number of victims.
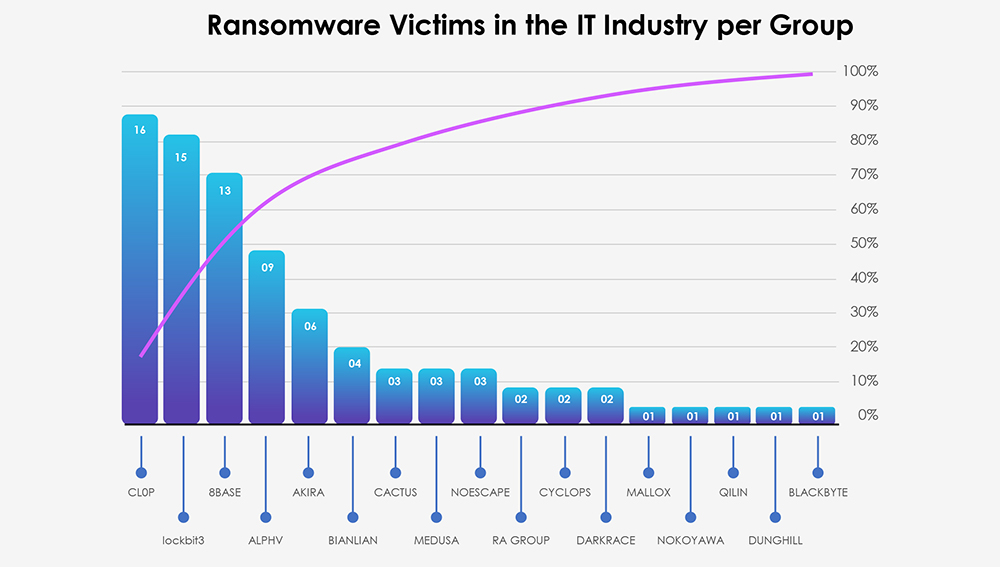
From 45 gangs active in past 90 days, only 17 recorded verified victims in IT industry. Interestingly big gangs like Play or Rhysida have no recorded IT industry victims at all in the past 90 days.
Out of the 83 victims identified, the United States emerges as the most affected by ransomware attacks in the IT sector, with 37 incidents attributed. This reaffirms the US’s role as the primary target cutting across various industries, owing to its economic significance and robust digital infrastructure.
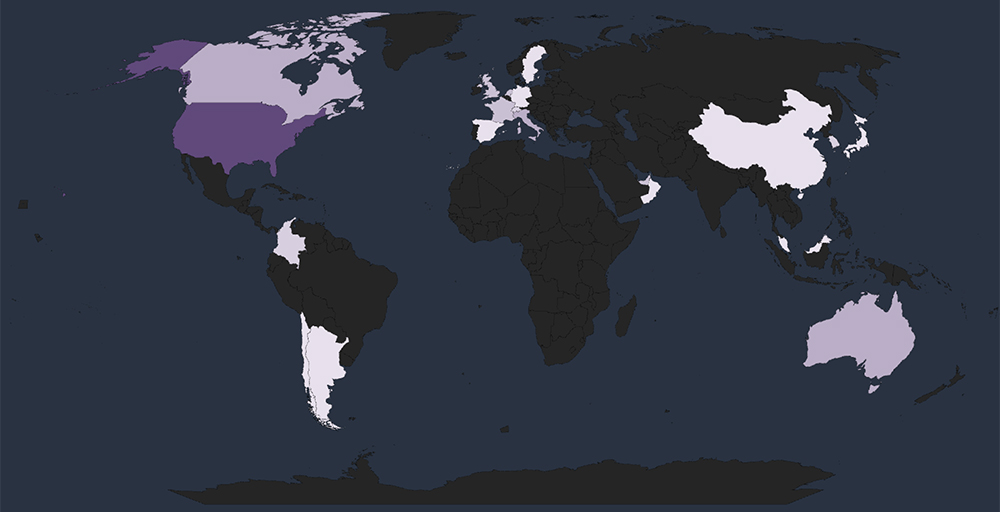
Global Spread – Apart from the USA, Australia, Canada, and Italy each reported 4 victims, trailed by France, Netherlands, UAE, and the UK with 3 victims each.
Together, these countries, in addition to the USA, account for 73% of all victims.
Geographical Vulnerability – The distribution of victims serves as a reminder that no region is exempt from ransomware threats. Cyber attackers have the capability to breach and target vulnerable organizations globally. This trend indicates that many threat actors prioritize exploiting vulnerabilities within organizations, regardless of their geographical locations.
The visual representation below illustrates the distribution of ransomware incidents over the past 90 days, portraying a diverse array of sectors within the IT industry.
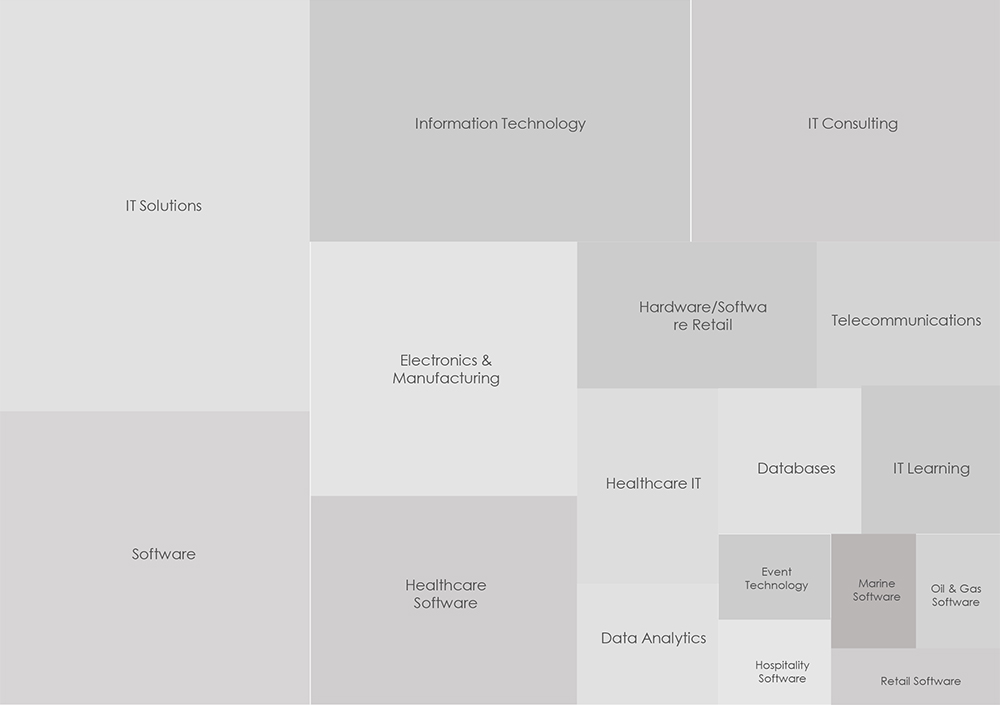
The distribution of attacks closely aligns with the broader presence of these sectors within the IT industry. Yet, a notable concern arises from the substantial targeting of healthcare software and IT services vendors, constituting 12% of the victim count.
The IT industry consistently attracts cyberattacks, drawing the interest of both financially motivated cybercriminals and nation-state APT groups.
Global IT services and solutions providers hold particular allure for foreign entities due to their strategic significance. Moreover, these worldwide online services frequently feature in phishing attacks, capitalizing on their recognized brand for global campaigns.
Software-as-a-Service, IT solutions, and consulting organizations are regular targets of ransomware. Their operation’s sensitivity, entailing client data, positions them as prime targets for extortion.
In summary, the IT industry’s sectors confront diverse and ongoing global cyber threats. Particularly, small and medium-sized organizations focusing on local markets often find themselves in the crosshairs of financially motivated threat actors. Their reliance on open-source code, frequently prone to various 0-day vulnerabilities, and the handling of client data, both contribute to their vulnerability. This data, in the hands of threat actors, can provide pathways for attacks on client systems.