


The CYFIRMA Industry Report delivers original cybersecurity insights and telemetry-driven statistics of global industries, covering one sector each week for a quarter. This report focuses on the healthcare industry, presenting key trends and statistics in an engaging infographic format.
Welcome to the CYFIRMA infographic industry report, where we delve into the external threat landscape of the healthcare industry over the past three months. This report provides valuable insights and data-driven statistics, delivering a concise analysis of attack campaigns, phishing telemetry, and ransomware incidents targeting healthcare organizations.
We aim to present an industry-specific overview in a convenient, engaging, and informative format. Leveraging our cutting-edge platform telemetry and the expertise of our analysts, we bring you actionable intelligence to stay ahead in the cybersecurity landscape.
CYFIRMA provides cyber threat intelligence and external threat landscape management platforms, DeCYFIR and DeTCT, which utilize artificial intelligence and machine learning to ingest and process relevant data, complemented by manual CTI research.
For the purpose of these reports, we leverage the following data from our platform. These are data processed by AI and ML automation, based on both human research input and automated ingestions.
While this report contains statistics and graphs generated primarily by automation, it undergoes thorough review and enhancement for additional context by CYFIRMA CTI analysts to ensure the highest quality and provide valuable insights.
The healthcare industry did not feature in any of the 13 observed campaigns, which is a presence in 0% of all campaigns, the same as the previous period (0 out of 7, 0%) in both volume and overall share.
No campaigns with healthcare-related victims were observed since the end of September in our telemetry.

Over the past 90 days, the healthcare industry has not been affected by advanced persistent threat (APT) campaigns.
This is because healthcare is not currently a frequent target for APT actors. This is because healthcare organizations typically manage data with limited intelligence or national security utility, unlike sectors such as defence, energy, or finance, which hold sensitive geopolitical, economic, or technological data.
Additionally, targeting healthcare systems, particularly hospitals, can carry reputational or diplomatic consequences, especially if lives are endangered.
While financially motivated actors like ransomware groups continue to exploit healthcare for extortion, nation-state APTs tend to avoid such targets unless specific biotechnological research, pandemic data, or government-affiliated medical institutions are involved.
As a result, healthcare remains a peripheral focus for most APT campaigns.
Over the past three months, CYFIRMA’s telemetry has identified 3,371 mentions of the healthcare industry out of a total of 68,835 industry-linked mentions. This is from a total of 300k+ posts across various underground and dark web channels and forums.
The healthcare industry placed 8th out of 14 industries in the last 90 days, with a share of 4.9% of all detected industry-linked chatter.
Below is a breakdown by 30-day periods of all mentions.
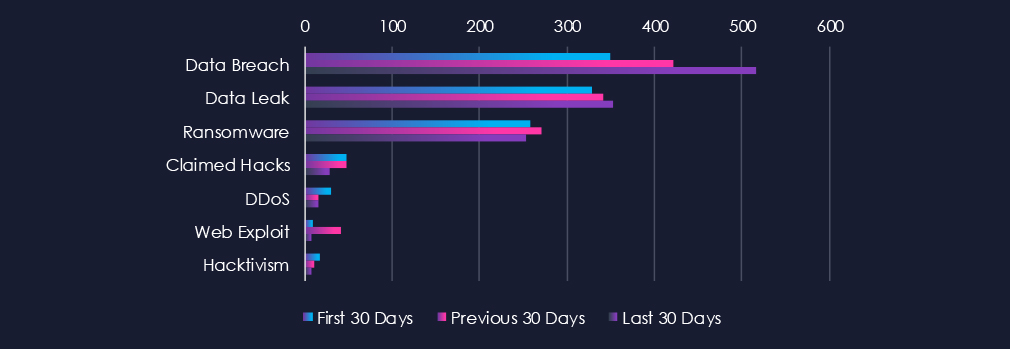
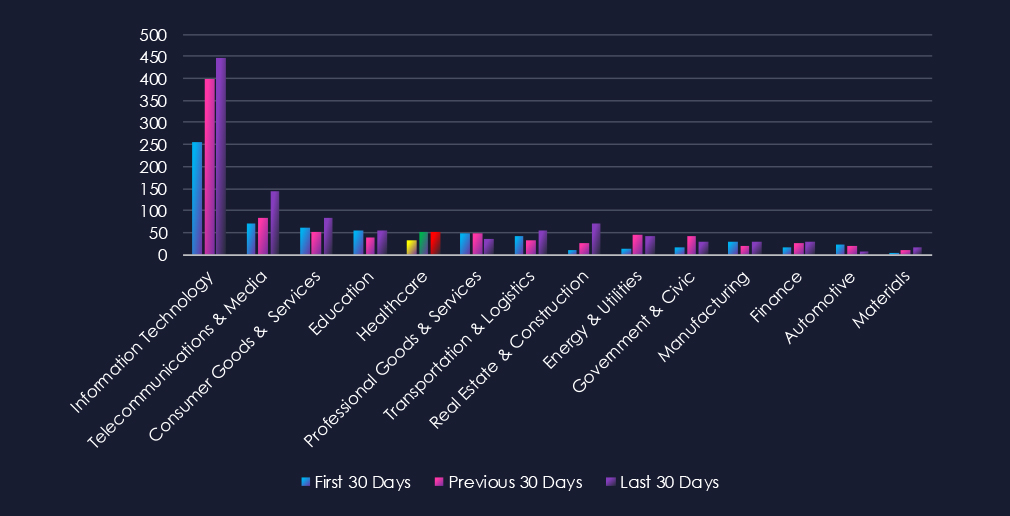
Data Breaches and Data Leaks are the most common category of recorded chatter for this industry. Both categories, and more visibly, Data Breach chatter has gradually grown over the entire 90-day period. Ransomware-related chatter follows in close third place with very stable levels of chatter across 90 days.
In total, the healthcare industry comprises 4.89% of all detected industry underground and dark web chatter in the last 90 days, ranking 8th out of 14 industries.
Below are observed key trends across 90 days:
Data Breach
350 → 421 → 516, Steady and significant growth across all periods. Indicates continued targeting of healthcare organizations, likely due to the high value of patient records and medical research data.
Data Leak
329 → 342 → 353, Relatively stable with a gradual increase. Suggests persistent circulation of healthcare-related data, including patient information, credentials, and insurance details.
Ransomware
258 → 270 → 253, Consistently high with only minor fluctuations. Reinforces ransomware as a top threat for healthcare, where operational disruption pressures victims into paying.
Claimed Hacks
48 → 48 → 29, Stable early on but dropping in the last 30 days. May suggest fewer publicized intrusions, with attackers favouring quieter monetization strategies such as extortion or private data sales.
DDoS
30 → 16 → 15, Downward trend, showing reduced focus on service disruption attacks. Healthcare is more likely to be targeted for data and extortion rather than availability disruption.
Web Exploit
9 → 41 → 7, Sharp spike in the middle period, but dropping again. Suggests short-term exploitation campaigns against healthcare web applications that have since slowed.
Hacktivism
17 → 11 → 8, Steady decline, showing reduced interest from ideologically motivated groups. The threat landscape here is now dominated by financially driven actors.
Over the past three months, CYFIRMA’s telemetry has identified 136 mentions of the healthcare industry out of a total of 2.660 industry mentions. This is from over 10k CVEs reported and updated in the last 90 days.
The healthcare industry ranked 5th out of 14 industries in the last 90 days, with a share of 5.11% of all detected industry-linked vulnerabilities.
Below is a breakdown by 30-day periods of all mentions.
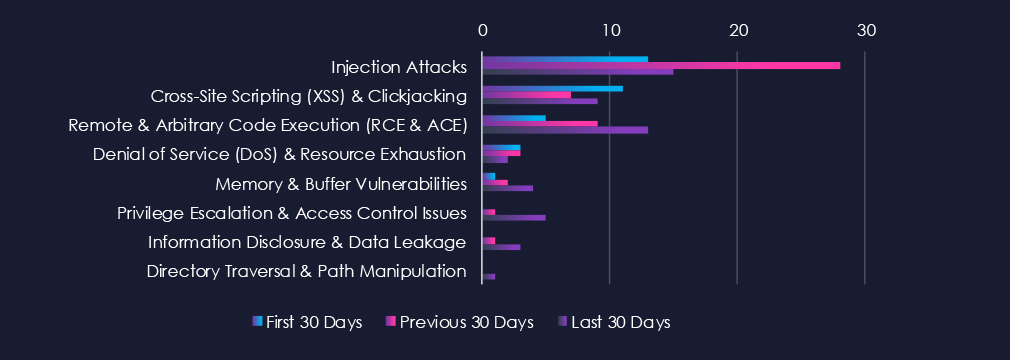
Injection Attacks are the most frequent vulnerability due to an uptick in CVEs during the previous 30 days. Remote & Arbitrary Code Execution (RCE & ACE) and Cross-Site Scripting (XSS) & Clickjacking are following in second and third place. Notably, there is an increase in nearly every category during the last 30 days.
In total, the healthcare industry comprises 5.11% of all detected industry-linked vulnerabilities in the last 90 days, ranking 5th out of 14 industries.
Below are observed key trends across 90 days.
Injection Attacks
13 → 28 → 15, A spike in the middle period followed by a decline, though still elevated. This pattern suggests concentrated researcher focus on input validation flaws in healthcare applications and platforms, which remain a recurring issue.
Cross-Site Scripting (XSS) & Clickjacking
11 → 7 → 9, Moderate but steady volume. Reflects ongoing discovery of client-side vulnerabilities in healthcare portals, patient platforms, and web-facing services.
Remote & Arbitrary Code Execution (RCE & ACE)
5 → 9 → 13, Steadily increasing across all periods. Indicates growing attention to high-impact vulnerabilities in healthcare technologies, where exploitation could have severe operational consequences.
Denial of Service (DoS) & Resource Exhaustion
3 → 3 → 2, Consistently low, suggesting this remains a less common disclosure focus compared to data- and access-related vulnerabilities.
Memory & Buffer Vulnerabilities
1 → 2 → 4, Gradual increase in reporting. Likely tied to older or embedded healthcare systems, where memory handling issues are common.
Privilege Escalation & Access Control Issues
0 → 1 → 5, Notable rise in the latest period, suggests researchers and vendors are paying closer attention to authentication and permissions in healthcare software.
Information Disclosure & Data Leakage
0 → 1 → 3, Recent increase, though still low. Highlights occasional findings of inadvertent exposure of sensitive healthcare data in software products.
Directory Traversal & Path Manipulation
0 → 0 → 1, Isolated disclosure in the latest period, likely tied to specific product vulnerabilities rather than a widespread issue.
In the past 90 days, CYFIRMA has identified 128 verified ransomware victims in the healthcare industry. This accounts for 8.8% of the overall total of 1,457 ransomware victims during the same period, placing the healthcare industry 5th out of 14 industries.
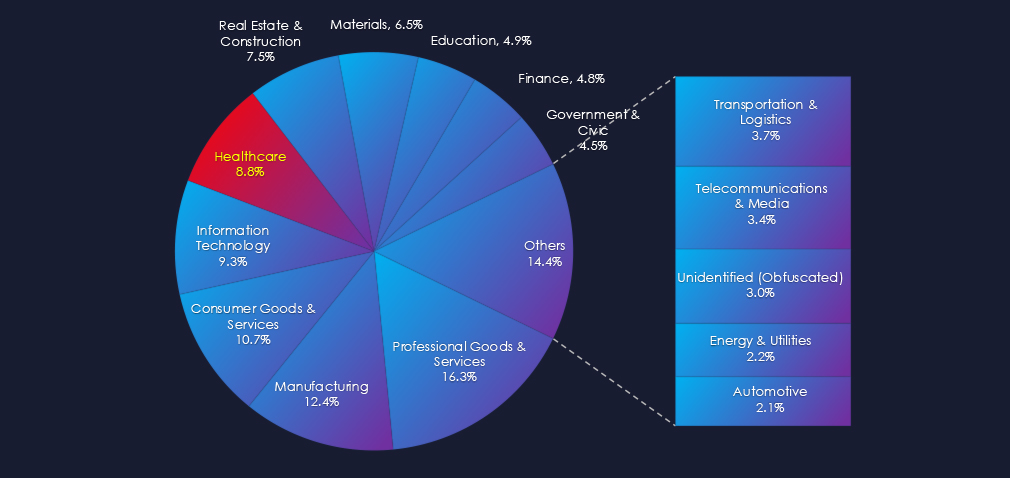
Furthermore, a quarterly comparison shows that interest in healthcare organizations remained nearly unchanged. There was only a minor increase of 3.2% from 124 to 128 victims. However, the overall share slightly increased from 7.76% to 8.8% of all victims.
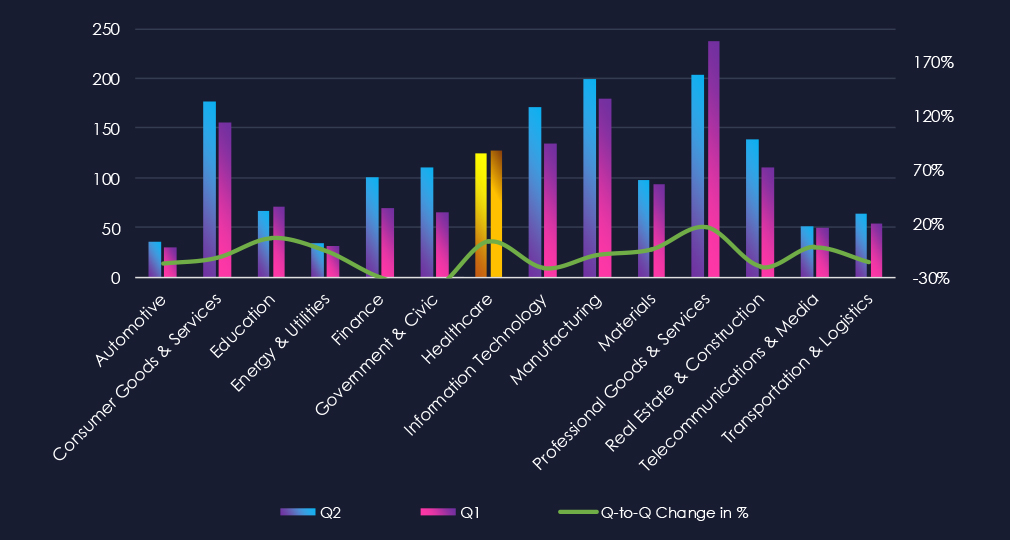
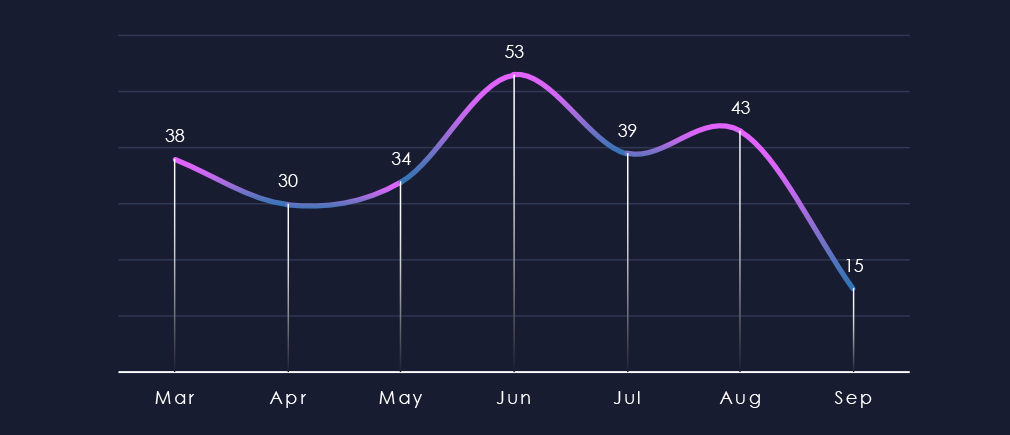
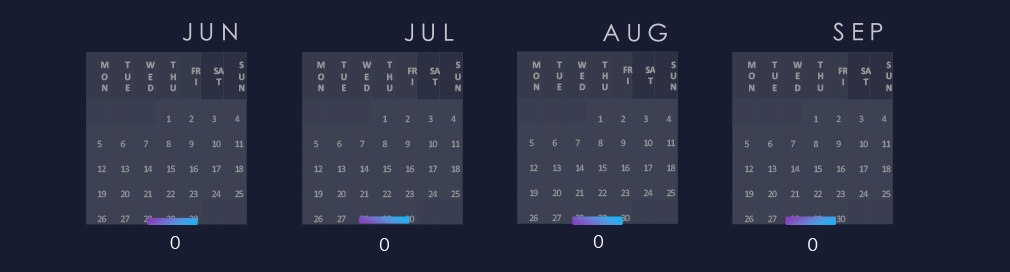
Over the past 180 days, we have observed mostly sustained levels of activity; however, June recorded a noticeable uptick, and numbers have been mildly elevated since.
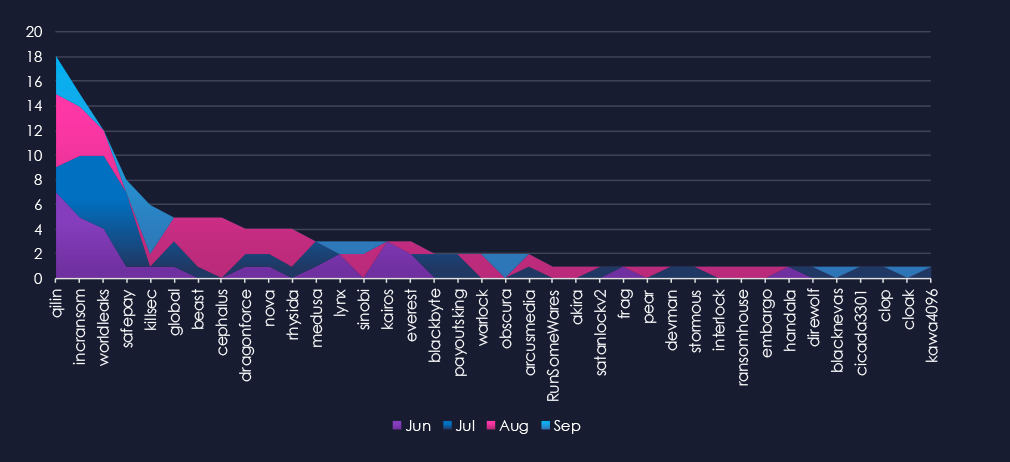
A breakdown of monthly activity per gang reveals which gangs were most active each month. For instance, Qilin and Incransom, the most active gangs, were highly active throughout the 90 days. In contrast, Safepay recorded victims primarily in July, while Cephalus recorded victims mostly in August.
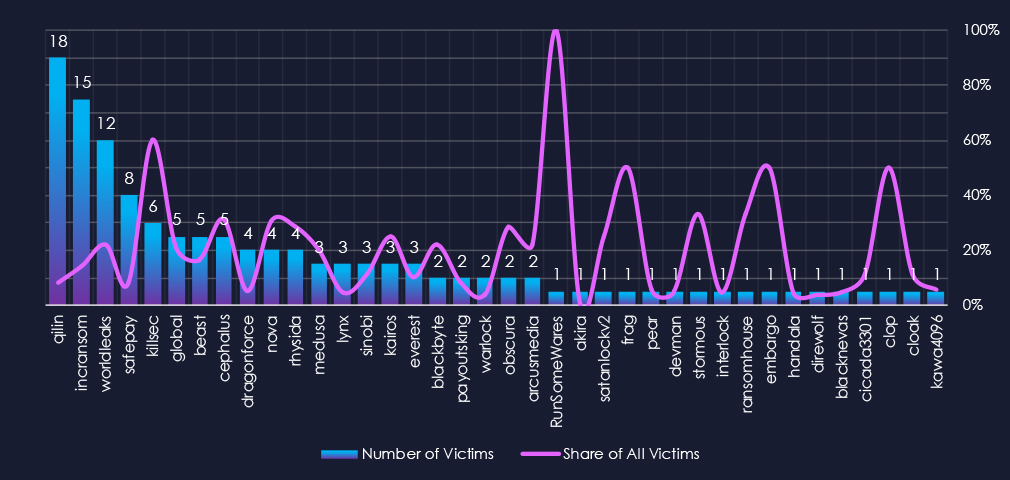
Out of the 72 gangs, 38 recorded victims in the healthcare industry in the last 90 days, representing a participation rate of 53%. Qilin had the highest number of victims (18).
The most disturbing statistic is the overall share of victims for each gang. Many gangs show a primary focus on the healthcare industry, with a high percentage of their victims in this sector.
Among the top 5 gangs, Qilin (8%), Incransom (14%), Worldleaks (21%), and Killsec (60%) recorded the highest shares in the healthcare industry. Furthermore, Cephalus and Nova (both 31%) showed an exceptionally high focus on this industry.
Out of the top 20 gangs, 15 showed double-digit % of victims in the healthcare industry.
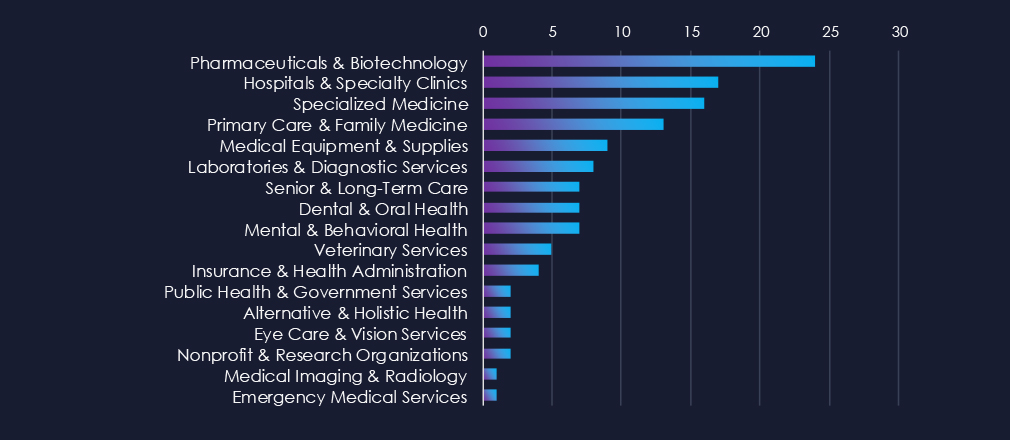
Pharma & Biotech, as well as Hospitals & Clinics, are the most common victims of ransomware in this industry. Additionally, Specialized Medicine, Primary Care, and Medical suppliers are frequently targeted.
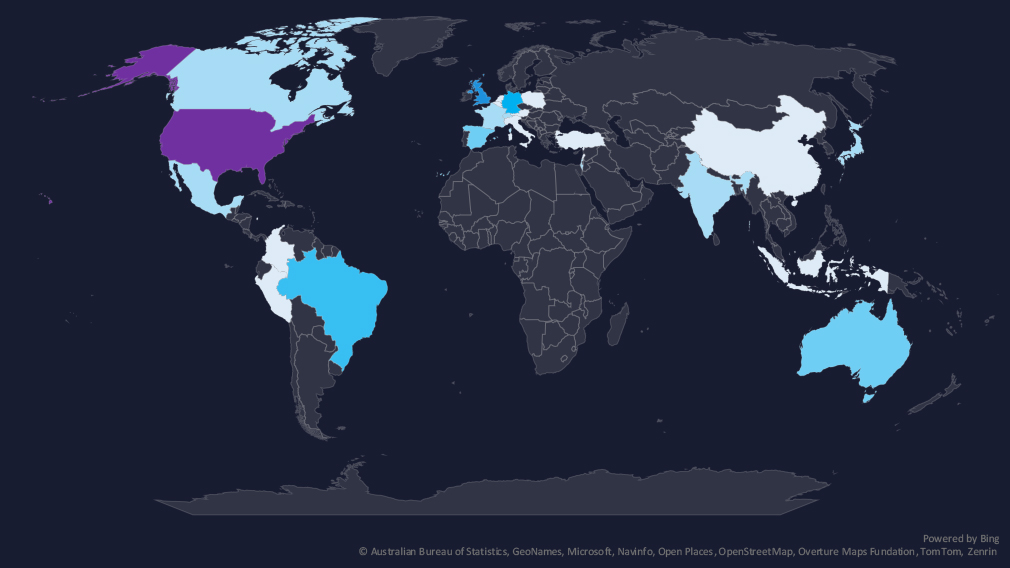
The geographic distribution heatmap underscores the widespread impact of ransomware, highlighting the countries where victims in this industry have been recorded.
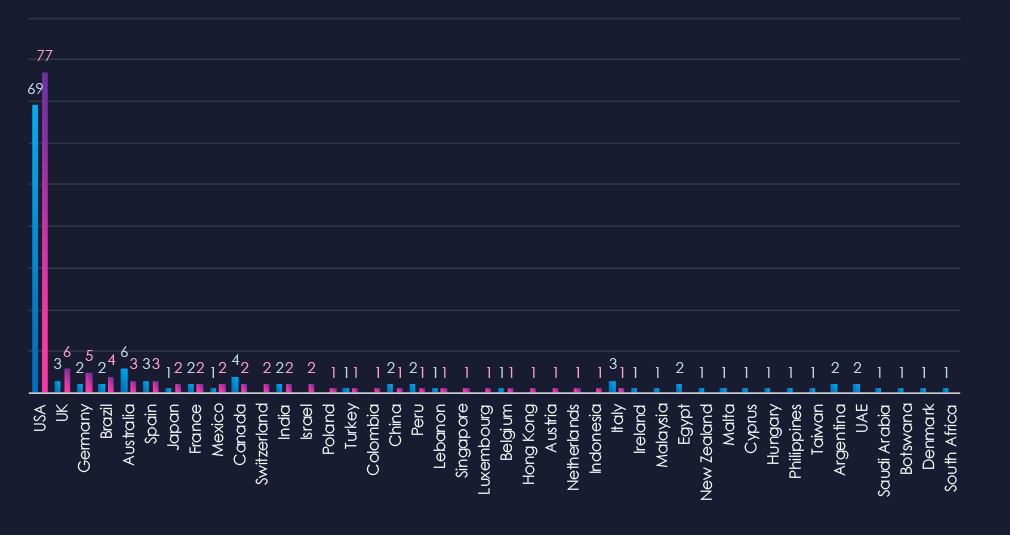
The chart shows quarter-to-quarter changes in targeted countries. Data is sorted by the last 90 days and compared to the previous 90 days, marked in blue.
Healthcare victimology is completely dominated by the US for-profit healthcare sector. 60% of all victims are from the USA. The UK, Germany, and Brazil follow with elevated numbers. Australia, Canada, and Italy recorded fewer victims.
The healthcare industry placed 5th out of 14 monitored industries, recording 128 victims in the last 90 days. There was a very minor increase of 3.2% from 124 victims in the previous 90-day period.
Overall share also mildly increased from 7.76% to 8.8% of all ransomware victims.
Monthly Activity Trends
Monthly activity was mostly stable across the last 180 days with an elevation during Jun, followed by a mild elevation into July and August.
Healthcare industry ransomware activity is highly localized to the USA due to its for-profit model. *The USA warrants high risk, while the rest of the world is moderate to low.
Ransomware Gangs
A total of 38 out of 72 active ransomware groups targeted this industry in the past 90 days – 53% participation:
Qilin: The most active, with 18 victims and 8% (18 out of 223) victims.
Worldleaks, Killsec: Highest shares in top 5, 22% (12 out of 55) and 60% (6 out of 10) victims among top gangs.
Cephalus, Nova: Extremely high share of healthcare victims (both 31%) showing healthcare is their primary focus.
Geographic Distribution
The geographic distribution of ransomware victims is relatively high and spread across the globe. However, as mentioned, the USA dominates with 77 victims accounting for 60% of all ransomware in this industry. Followed by the UK (6), Germany (5), and Brazil (4), which all recorded an elevation in the last 90 days.
Australia, Canada, and Italy recorded lower numbers.
Overall, 27 countries were impacted.
For a comprehensive, up-to-date global ransomware tracking report, please refer to our new monthly “Tracking Ransomware” series here.
APT Campaigns (Low): Healthcare remains a peripheral target for nation-state APTs. Over the past 90 days, no major APT campaigns directly targeted the sector. Unlike defense, finance, or energy, healthcare lacks high-value geopolitical or economic data. Attacks against hospitals also carry reputational and diplomatic risks, as they could endanger lives. State actors typically only engage when biotechnological research, pandemic data, or government-linked medical institutions are involved. Financially motivated groups, especially ransomware operators, continue to pose the greater threat.
Underground & Dark Web Chatter (Moderate): The sector represented 4.9% of chatter, ranking 8th overall. Breach-related mentions rose sharply to 516, highlighting healthcare’s continued appeal due to the value of patient records. Data leaks remained stable but persistent, reinforcing constant exposure. Ransomware chatter stayed consistently high, while claimed hacks declined, suggesting a shift toward private extortion or resale. DDoS and hacktivism mentions decreased, showing reduced focus on disruption and ideology. Web exploit chatter spiked mid-period, then dropped, suggesting short-lived exploitation of the healthcare web app.
Vulnerabilities (Moderate): Healthcare accounted for 5.1% of vulnerabilities, ranking 5th. RCE reports steadily grew, showing increased discovery of high-impact flaws. Injection attacks spiked mid-period but remain a concern. XSS remained moderate, while memory vulnerabilities rose, likely tied to legacy systems and embedded devices. Privilege escalation and information disclosure issues have increased recently, signaling weak access control and occasional exposure of sensitive data. Overall, vulnerabilities reflect both systemic flaws in healthcare IT and risks tied to aging infrastructure.
Ransomware (Moderate*): Healthcare ranked 5th for ransomware, recording 128 victims (+3.2% from the previous period). Share of all victims rose to 8.8%. Activity was stable, with small peaks in June–July. Attacks are highly concentrated in the *USA, which alone accounted for 60% of victims. Qilin led activity with 18 cases, while groups like Worldleaks and Killsec showed disproportionately high shares, indicating healthcare as a priority. Smaller gangs such as Cephalus and Nova exclusively targeted healthcare in many of their incidents. In total, 27 countries recorded victims, though the USA dominates the threat landscape.