


The CYFIRMA Industry Report delivers original cybersecurity insights and telemetry-driven statistics of global industries, covering one sector each week for a quarter. This report focuses on the healthcare industry, presenting key trends and statistics in an engaging infographic format.
Welcome to the CYFIRMA infographic industry report, where we delve into the external threat landscape of the healthcare industry over the past three months. This report provides valuable insights and data-driven statistics, delivering a concise analysis of attack campaigns, phishing telemetry, and ransomware incidents targeting the healthcare industry.
We aim to present an industry-specific overview in a convenient, engaging, and informative format. Leveraging our cutting-edge platform telemetry and the expertise of our analysts, we bring you actionable intelligence to stay ahead in the cybersecurity landscape.
CYFIRMA provides cyber threat intelligence and external threat landscape management platforms, DeCYFIR and DeTCT, which utilize artificial intelligence and machine learning to ingest and process relevant data, complemented by manual CTI research.
For the purpose of these reports, we leverage the following data from our platform. These are data processed by AI and ML automation based on both human research input and automated ingestions.
While this report contains statistics and graphs generated primarily by automation, it undergoes thorough review and enhancement for additional context by CYFIRMA CTI analysts to ensure the highest quality and provide valuable insights.
Healthcare organizations featured in 1 out of the 9 observed campaigns, which is a presence in 11.1% of all campaigns.
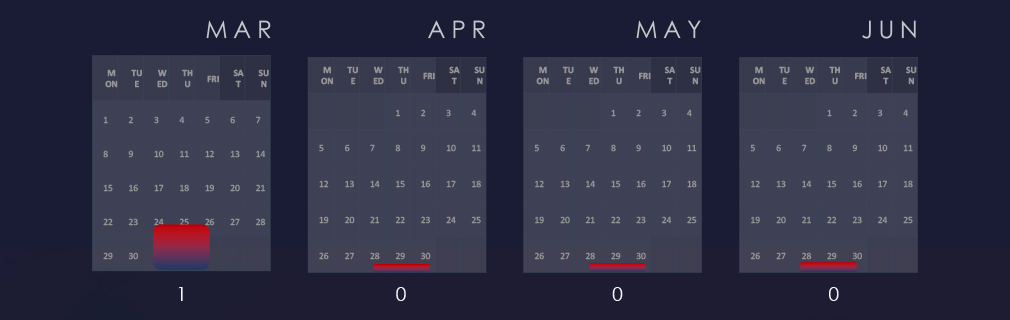
We are observing a generally low detections period. Last observed campaign targeting healthcare sector was in mid-March, specifically biotechnology.

We observed varied mix of TTPs splitting the suspected threat actors. Among others, the presence of Winnti derivate suggests Chinese MISSION2025 (APT41 nexus). However, Korean language was also present, indicating Lazarus Group from DPKR activity.
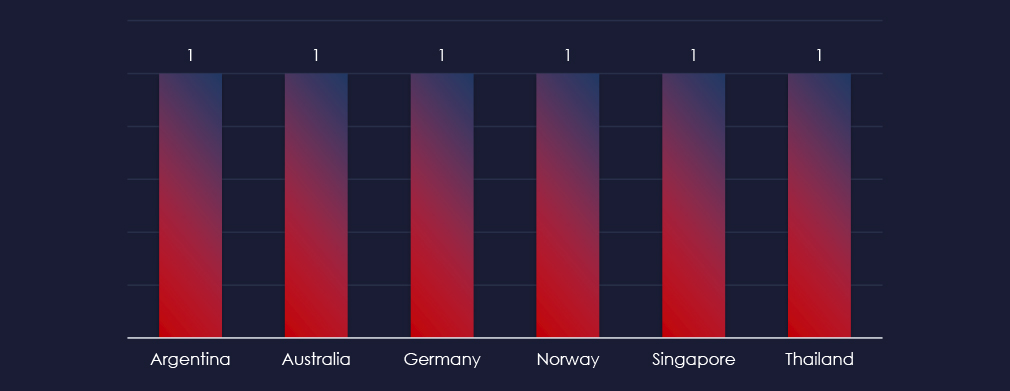
Recorded victims of observed attack campaign span 6 different countries. There does not appear to a be clear geographic pattern. Considering suspected TAs, it is suggesting opportunistic targeting and possibly financial motivation over geopolitical.

Web applications continue to be the most targeted technology across industries.
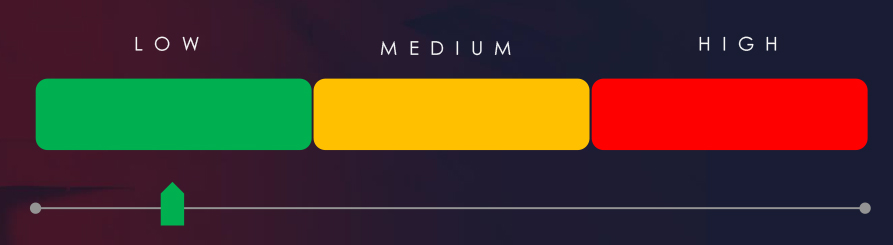
Risk Level Indicator: Low
In the past 90 days, healthcare organizations have not been significantly impacted by advanced persistent threat (APT) campaigns. Just 11.1% of observed APT campaigns targeted the healthcare sector, with 1 out of 9 total campaigns affecting this industry.
Monthly Trends
Since single observed campaign in mid-March with biotechnology victims, we did not observe other campaigns targeting healthcare sectors.
Key Threat Actors
Overlapping TTPs suggest two suspected threat actors. The Chinese MISSION2025 (APT41 nexus) and Lazarus Group from DPKR. Presence of Winnti derived malware links the activity to MISSION2025. However, Korean language used points towards Lazarus Group. Moreover, use of commodity Redline Stealer with no apparent targeting pattern implies opportunistic and financially motivated campaign.
Geographical Impact
The campaigns impacted a total of 6 countries, seemingly randomly spread across continents. This lack of geographic focus suggests opportunism over nation-state strategic focus.
Targeted Technologies
Web applications emerged as the only apparent targeted technology within this campaign.
Over the past 3 months, CYFIRMA’s telemetry detected 75 phishing campaigns themed around healthcare out of a total of 277,041.
The chart below illustrates the global distribution of observed themes. Healthcare accounts only for 0.02% of all captured phishing attempts and therefore is not tracked as a category.
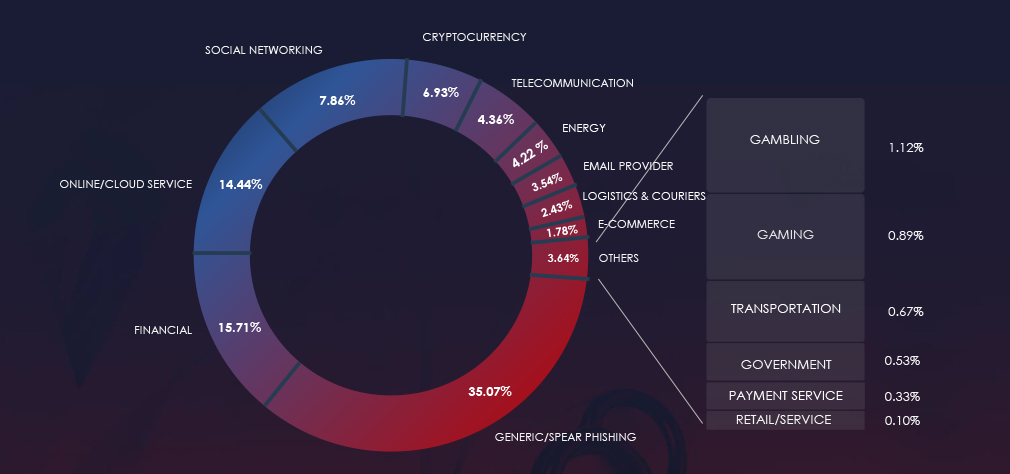
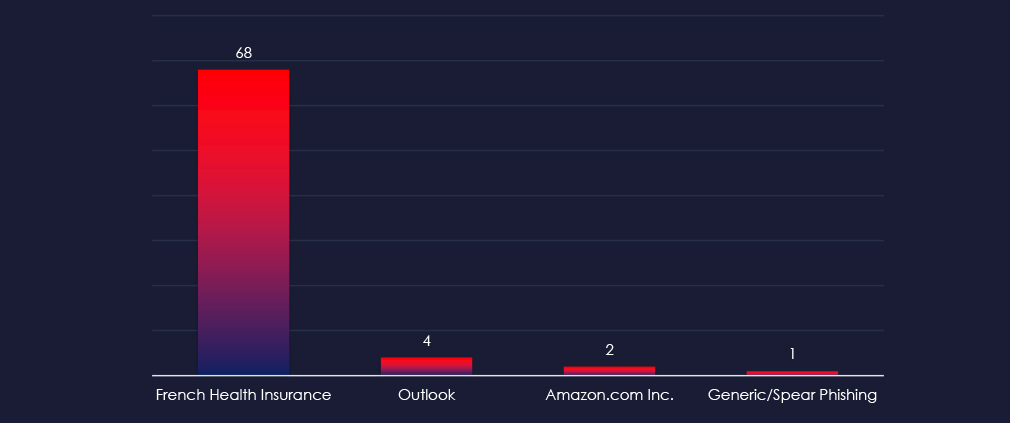
Nearly all healthcare related phishing is impersonating French Health Insurance. The rest is leveraging other brands, just containing healthcare products or services references.
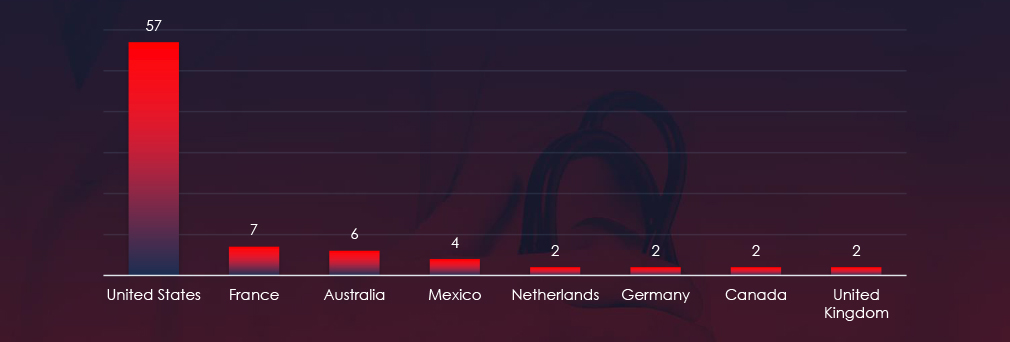
The geographical sources of observed phishing campaigns show that most of healthcare themed phishing comes from the US, despite mostly impersonating a French organization.
Risk Level Indicator: Low
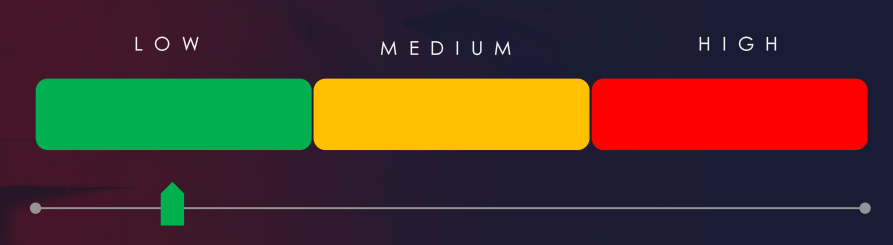
The healthcare warrants low risk factor.
As established in previous healthcare industry reports, it does not present attractive lure for wider “spray and pray” types of phishing campaigns.
The data indicates that French Health Insurance is the sole identified impersonated organization related to healthcare, though it aligns more closely with the financial industry. Additionally, cybercriminals often avoid targeting healthcare organizations due to the significant law enforcement attention such attacks attract. Lastly, some cybercriminals follow ethical guidelines, avoiding attacks that directly harm individuals.
ASN-origin data reveals that the United States is the leading source of phishing emails impersonating healthcare.
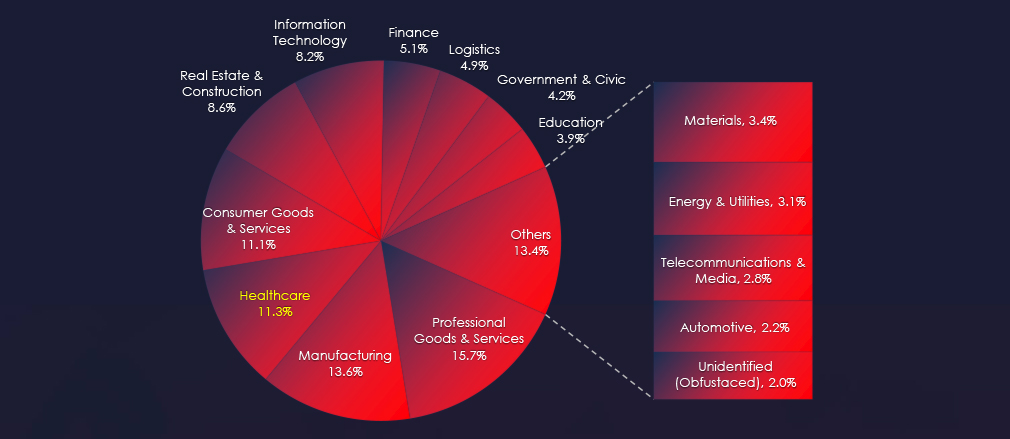
In the past 90 days, CYFIRMA has identified 147 verified ransomware victims in the healthcare industry. This accounts for 11.3% of the overall total of 1,298 ransomware victims during the same period.
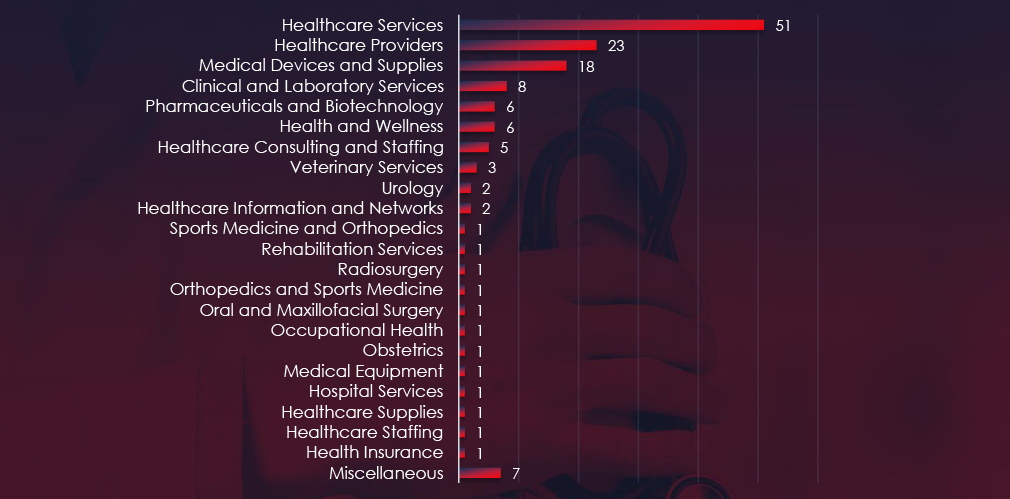
Healthcare Services and Providers are the most frequent victims of ransomware in healthcare industry.
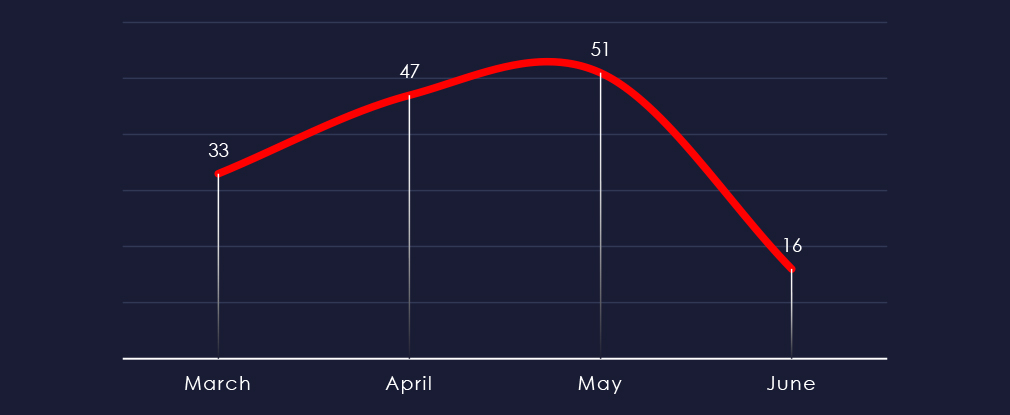
Considering roughly half of March and June, we can see consistent numbers with a mildly growing trend.
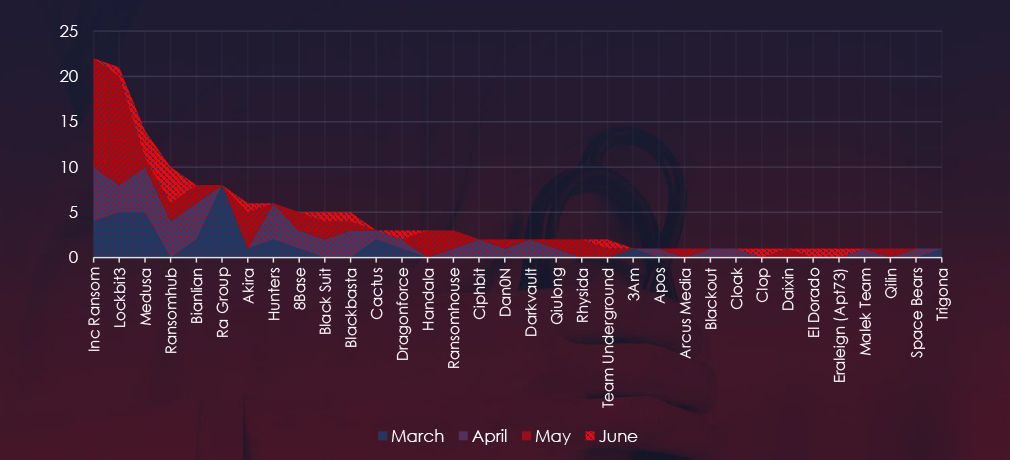
A breakdown of the monthly activity provides insights into which gangs were active each month. For example, LockBit3 came back in May and Inc Ransom “dumped” a lot of victims in one block in May as well. Ra Group and Medusa reported many victims in March.
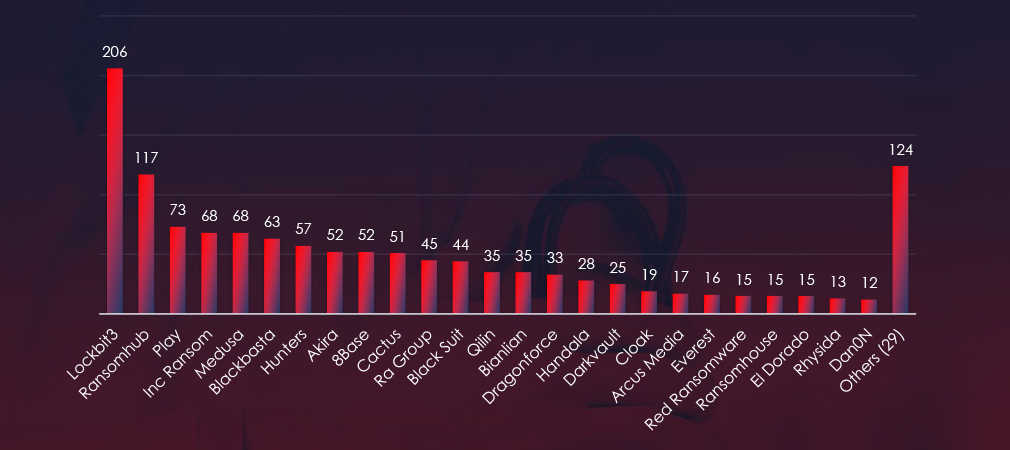
In total 34 out of 54 active groups recorded healthcare organizations victims in the past 90 days. Notable is a high distribution among large number of groups in this period.
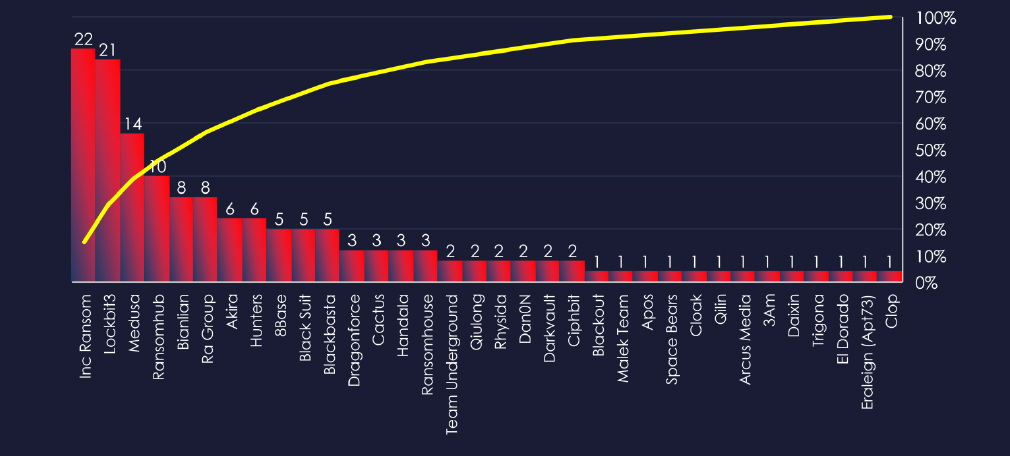
Comparing the healthcare industry to all recorded victims, some gangs stand out with a high percentage of victims in this industry. Highest are Inc Ransom with 22 out of 68 (32.3%) Bianlian with 8 out of 35 (22.8%) and Medusa with 14 out of 68 (20.5%) victims.
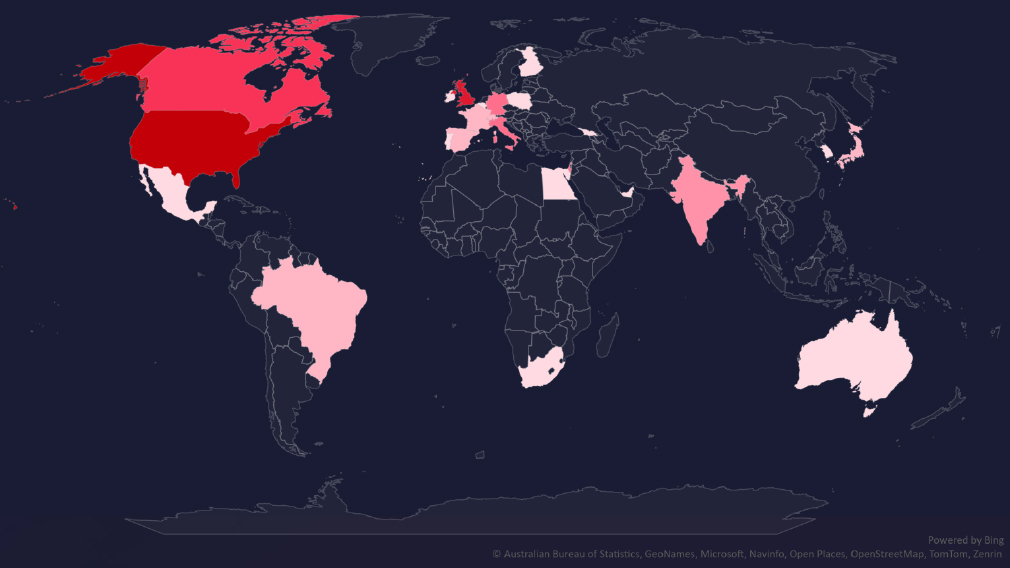
The geographic distribution heatmap underscores the widespread impact of ransomware, highlighting the countries where victims in this industry have been recorded.
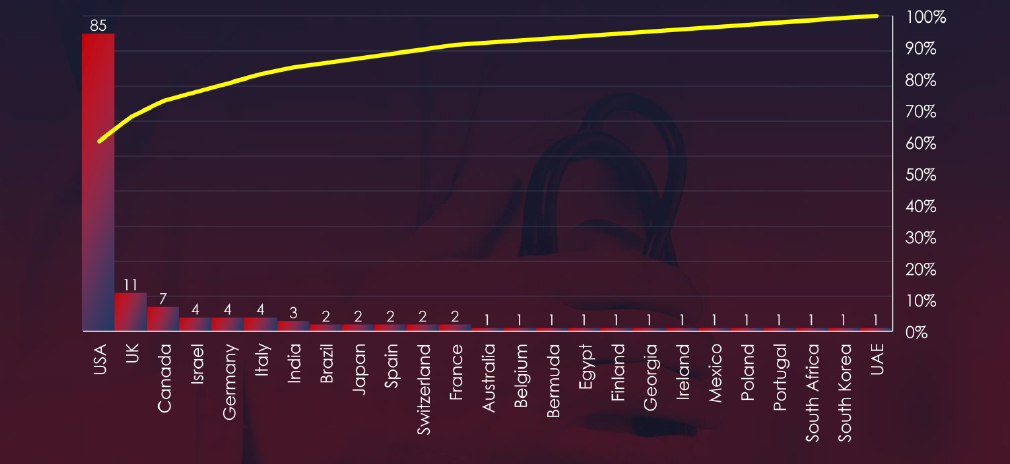
In total 25 countries recorded ransomware victims with the US alone accounting for ~59% of all victims with identified geography.
Risk Level Indicator: High
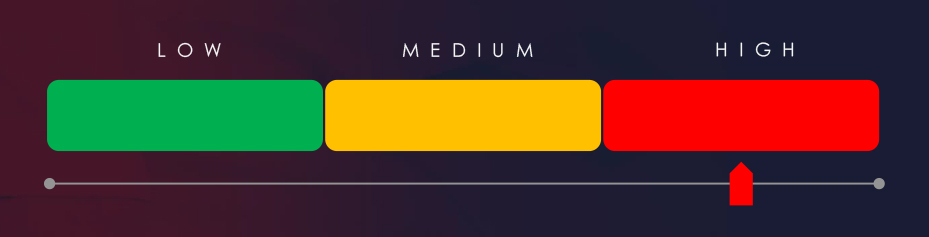
The healthcare industry is the 3rd most frequent victim of ransomware. It faces a significant threat, with attacks affecting a wide range of sub-sectors and a broad geographic distribution. The steady monthly activity, coupled with the involvement of numerous ransomware groups, highlights the pervasive and ongoing risk.
Monthly Activity Trends
Ransomware activity in the healthcare industry has shown consistent and growing numbers of victims each month.
LockBit3 returned in May and Inc Ransom gang recorded most of their victims also in May, contributing to the spike in activity during this month.
Ransomware Gangs
A total of 34 out of 54 active ransomware groups targeted the healthcare industry in the past 90 days:
Inc Ransom: 32.3% of their victims were from the healthcare industry (22 out of 68 victims).
Bianlian: 22.8% of their victims were from the healthcare industry (8 out of 35 victims).
Medusa: 20.5% of their victims were from the healthcare industry (14 out of 68 victims).
The distribution of attacks among many groups indicates no single gang dominated the ransomware landscape in the healthcare sector.
Geographic Distribution
The geographic distribution of ransomware victims in the healthcare industry highlights the widespread nature of these attacks:
59% of all victims with identified geography were located in the US.
In total, 25 countries reported ransomware victims in this industry.
For a comprehensive, up-to-date global ransomware tracking report, please refer to our new monthly “Tracking Ransomware” series here.
In the past 90 days, healthcare organizations have faced low to high risk across monitored categories.
APT campaigns risk in the healthcare sector is low, with only 11.1% of observed APT campaigns targeting this industry. A single campaign in mid-March, likely involving Chinese MISSION2025 (APT41) or Lazarus Group, impacted biotechnology victims across six countries. This campaign primarily targeted web applications and appeared opportunistic rather than strategically focused.
Phishing impersonating the healthcare sector does not attract wide-scale “spray and pray” phishing campaigns, with French Health Insurance being the only notable impersonated organization. Cybercriminals often avoid targeting healthcare due to increased law enforcement scrutiny and ethical considerations. Most phishing emails targeting healthcare organizations originated from the United States.
Ransomware attacks also pose a high risk, ranking healthcare as the third most frequent victim. The industry has experienced consistent and growing numbers of ransomware attacks, with LockBit3 and Inc Ransom gang activities spiking in May. A total of 34 out of 54 active ransomware groups targeted healthcare, with Inc Ransom, Bianlian, and Medusa being the most active. The attacks are widely distributed across 25 countries, with 59% of victims located in the United States.